Simplifying WPA2-Enterprise and 802.1X
WPA2-Enterprise has been around since 2004 and is still considered the gold standard for wireless network security, delivering over-the-air encryption and a high level of security. In conjunction with the effective authentication protocol known as 802.1X, users have been successfully authorized and authenticated for secure network access for many years.
But in that time, WPA2-Enterprise hasn't gotten any easier to manually configure. Regardless of whether you are deploying a wireless network for the first time or a seasoned expert, there are always unique challenges ready to give you a headache. Our Cloud RADIUS server is a turnkey solution for organizations of all sizes. What follows is a comprehensive guide on every aspect of WPA2-Enterprise network authentication via the 802.1X protocol.
WPA2-PSK and WPA2-Enterprise: What's the Difference?
WPA2-PSK
WPA2-PSK (Wi-Fi Protected Access 2 Pre-Shared Key) is a type of network that is protected by a single password shared between all users. It's generally accepted that a single password to access Wi-Fi is safe, but only as much as you trust those using it. Otherwise, it's trivial for someone who has obtained the password through nefarious means to infiltrate the network. This is why WPA2-PSK is often considered insecure.
There are only a few situations in which WPA2-PSK should be deployed:
- The network has just a few devices, all of which are trusted. This could be a home or small office.
- As a way to restrict casual users from joining an open network when unable to deploy a captive portal. This could be a coffee shop or guest network.
- As an alternative network for devices not compatible with 802.1x. An example being game consoles in a student dorm.
WPA3-PSK
To improve the effectiveness of PSK, updates to WPA3-PSK offer greater protection by improving the authentication process. A strategy to do this uses Simultaneous Authentication of Equals (SAE) to make brute-force dictionary attacks far more difficult for a hacker. This protocol requires interaction from the user on each authentication attempt, causing a significant slowdown for those attempting to brute-force through the authentication process.
WPA2-Enterprise
Deploying WPA2-Enterprise requires a RADIUS server, which handles the task of authenticating network users access. The actual authentication process is based on the 802.1x policy and comes in several different systems labelled EAP. Because each device is authenticated before it connects, a personal, encrypted tunnel is effectively created between the device and the network.
The WPA2 (Enterprise) RADIUS combination affords networks the highest level of cybersecurity, especially when X.509 digital certificates are used for authentication. WPA2 Enterprise requires an 802.1X authentication server anyway, so it's only logical to implement the best possible authentication security during configuration.
WPA3-Enterprise
A significant improvement that WPA3-Enterprise offers is a requirement for server certificate validation to be configured to confirm the identity of the server to which the device is connecting.
Interested in learning more about WPA3? Get the details about the changes WPA3 is poised to bring in this article.
Key Takeaways
- WPA2-PSK is the simplest form of authentication security and it shouldn't be used outside of
protecting
home Wi-Fi networks. - WPA2-Enterprise requires networking infrastructure and somewhat complex configuration, but it's
significantly more secure. - WPA3 is still in the preliminary stages and for now WPA2-Enterprise is the gold standard for wireless
security.
Deploying WPA2-Enterprise and 802.1x
An 802.1X RADIUS server for WiFi authentication is a necessary component of enterprise network security. Remote Authentication Dial In User Service (RADIUS) secures WiFi by requiring a unique login for each user, as well as recording event logs and applying authorization policies.
There are just a few components that are needed to make 802.1x work. Realistically, if you already have access points and some spare server space, you possess all the hardware needed to make secure wireless happen. Sometimes you don't even need the server: some access points come with built-in software that can operate 802.1x (though only for the smallest of small deployments). Regardless of whether you purchase professional solutions or build one yourself from open source tools, the quality and ease of 802.1x is entirely a function of design.
Key Takeaways
- The best way to deploy the gold standard of wireless security (WPA2-Enterprise with 802.1X) is a
passwordless solution that leverages digital certificates. - Tie your Cloud Identity to network security by deploying WPA2-enterprise for Wi-Fi and VPN
authentication.
The Components of 802.1x
Client / Supplicant
In order for a device to participate in the 802.1x authentication, it must have a piece of software called a supplicant installed in the network stack. The supplicant is necessary as it will participate in the initial negotiation of the EAP transaction with the switch or controller and package up the user credentials in a manner compliant with 802.1x. If a client does not have a supplicant, the EAP frames sent from the switch or controller will be ignored and the switch will not be able to authenticate.
Fortunately, almost all devices we might expect to connect to a wireless network have a supplicant built-in. SecureW2 provides a 802.1x supplicant for devices that don't have one natively.
Thankfully, the vast majority of device manufacturers have built-in support for 802.1x. The most common exceptions to this might be consumer gear, such as game consoles, entertainment devices or some printers. Generally speaking, these devices should be less than 10% of the devices on your network and are best treated as the exception rather than the focus.
Key Takeaways
- The client contains the user's credentials and connects with the switch/controller so the
authentication
process can initiate.
Switch / Access Point / Controller
The switch or wireless controller plays an important role in the 802.1x transaction by acting as a ‘broker' in the exchange. Until a successful authentication, the client does not have network connectivity, and the only communication is between the client and the switch in the 802.1x exchange. The switch/controller initiates the exchange by sending an EAPOL-Start packet to the client when the client connects to the network. The client's responses are forwarded to the correct RADIUS server based on the configuration in the Wireless Security Settings. When the authentication is complete, the switch/controller makes a decision whether to authorize the device for network access based on the user's status and possibly the attributes contained in the Access_Accept packet sent from the RADIUS server.
If the RADIUS server sends an Access_Accept packet as a result of an authentication, it may contain certain attributes which provide the switch information on how to connect the device on the network. Common attributes will specify which VLAN to assign a user, or possibly a set of ACLs (Access Control List) the user should be given once connected. This is commonly called ‘User Based Policy Assignment', as the RADIUS server is making the decision based on user credentials. Common use cases would be to push guest users to a ‘Guest VLAN' and employees to an ‘Employee VLAN'.
Key Takeaways
- These components facilitate communication between the end-user device and the RADIUS server.
- They can be configured with low-security authentication protocols like WPA-PSK that do not require a
RADIUS. - The switch is where you configure the network to use 802.1x instead of WPA2-PSK.
RADIUS Server
RADIUS is an acronym for Remote Authentication Dial In User Service. It's sometimes called an AAA server, which is an intialism for Authentication, Authorization, and Accounting. RADIUS is a WiFi security necessity - it replaces a single preshared key with unique credentials per user or device.
The on-premise or Cloud RADIUS server acts as the “security guard” of the network; as users connect to the network, the RADIUS authenticates their identity and authorizes them for network use. A user becomes authorized for network access after enrolling for a certificate from the PKI (Private Key Infrastructure) or confirming their credentials. Each time the user connects, the RADIUS confirms they have the correct certificate or credentials and prevents any unapproved users from accessing the network. A key security mechanism to employ when using a RADIUS is server certificate validation. This guarantees that the user only connects to the network they intend to by configuring their device to confirm the identity of the RADIUS by checking the server certificate. If the certificate is not the one which the device is looking for, it will not send a certificate or credentials for authentication.
RADIUS servers can also be used to authenticate users from a different organization. Solutions like Eduroam have RADIUS servers work as proxies (such as RADSEC) so that if a student visits a neighboring university, the RADIUS server can authenticate their status at their home university and grant them secure network access at the university they are currently visiting.
Key Takeaways
- RADIUS Servers serve as a “security guard” of the network by authenticating clients, authorizing
client
access, and monitoring client activity. - RADIUS servers take attributes from the client and determine their appropriate level of access.
Identity Store
The Identity Store refers to the entity in which usernames and passwords are stored. In most cases, this is Active Directory, or potentially an LDAP server. Almost any RADIUS server can connect to your AD or LDAP to validate users. There are a few caveats when LDAP is used, specifically around how the passwords are hashed in the LDAP server. If your passwords are not stored in cleartext or an NTLM hash, you will need to choose your EAP methods carefully as certain methods, such as EAP-PEAP, may not be compatible. This is not an issue caused by RADIUS servers, but rather from the password hash.
SecureW2 can help you set up SAML to authenticate users, on any Identity Provider, for Wi-Fi access. Here are guides to integrating with some popular products.
To set up SAML authentication within Google Workspace, click here.
Configuring WPA2-Enterprise with Okta, click here.
For a guide on SAML Authentication using Shibboleth, click here.
To configure WPA2-Enterprise with ADFS, click here.
Developing a robust WPA2-Enterprise network requires additional tasks, like setting up a PKI or CA (Certificate Authority), to seamlessly distribute certificates to users. But contrary to what you might think, you can make any of these upgrades without buying new hardware or making changes to the infrastructure. For example, rolling out guest access or changing the authentication method can be accomplished without additional infrastructure. Recently, many institutions have been switching EAP methods from PEAP to EAP-TLS after seeing noticeable improvement in connection time and roaming ability or switching from a physical RADIUS server to a Cloud RADIUS solution. Improving the functionality of wireless networks can be gained without changing a single piece of hardware.
Key Takeaways
- 802.1x only includes four major components: client, switch, RADIUS server, and directory
- 802.1x requires a directory so the RADIUS can identify each end user and what level of access
they are allowed. - Although it consists of just a few components, 802.1x is incredibly complex to enable and you could
risk
misconfiguration when leaving setup to the end user. - The best practice is to integrate an onboarding application that allows devices to self-service with
802.1x settings.
WPA2-Enterprise Protocols
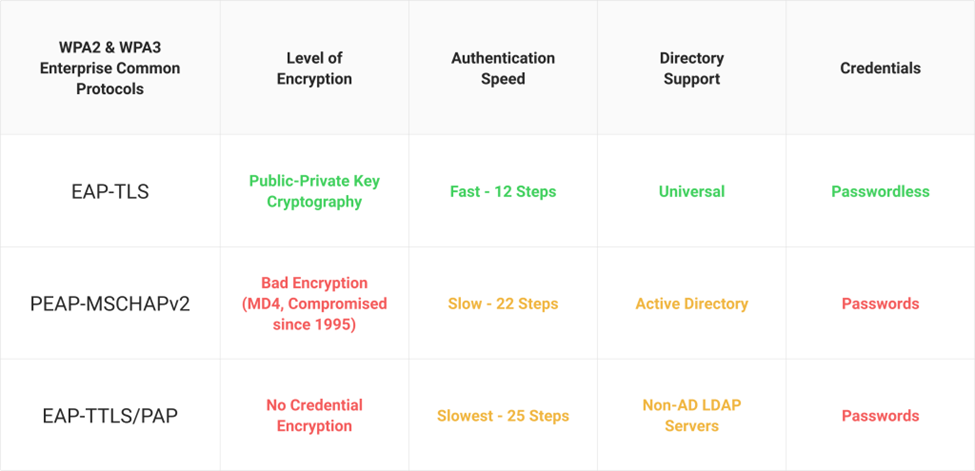
What follows is a brief summary of the primary WPA2-Enterprise Authentication Protocols. If you'd like a more in-depth compare-and-contrast, read the full-length article.
EAP-TLS
EAP-TLS is a certificate-based protocol that is is widely considered one of the most secure EAP standards because it eliminates the risk of over-the-air credential theft. It's also the protocol that provides the best user experience, as it eliminates password-related disconnects due to password-change policies. In the past, there was a misconception that certificate-based authentication was difficult to setup and/or manage, but now EAP-TLS is regarded by many to actually be easier to setup and manage than the other protocols.
Want to learn more about the advantages of EAP-TLS and how SecureW2 can help your implement it in your own network? Click the link!
EAP-TTLS/PAP
EAP-TTLS/PAP is a credential-based protocol that was created for an easier setup because it only requires the server to be authenticated, while user authentication is optional. TTLS creates a “tunnel” between the client and the server and gives you multiple choices for authentication.
But TTLS includes many vulnerabilities. The configuration process can be difficult for inexperienced network users, and a single misconfigured device can result in significant loss to the organization. The protocol allows credentials to be sent over the air in Cleartext, which can be vulnerable to cyber attacks like Man-In-The-Middle and easily repurposed to accomplish the hacker's goals.
If you'd like to know more about the vulnerabilities of TTLS-PAP, read the full article here.
PEAP-MSCHAPv2
PEAP-MSCHAPv2 is a credential-based protocol that was designed by Microsoft for Active Directory environments. Although it's one of the most popular methods for WPA2-Enterprise authentication, PEAP-MSCHAPv2 does not require the configuration of server-certificate validation, leaving devices vulnerable to Over-the-Air credential theft. Device misconfiguration, when left to end-users, is relatively common which is why most organizations rely on Onboarding Software to configure devices for PEAP-MSCHAPv2. Read how this top university converted from PEAP-MSCHAPv2 to EAP-TLS authentication to provide more stable authentication to network users.
For more information on PEAP MSCHAPv2, read this article.
Key Takeaways
- WPA2-Enteprise protocols can either be credential-based (EAP-TTLS/PAP and PEAP-MSCHAPv2) or
certificate-based (EAP-TLS) - EAP-TLS is a certificate-based authentication protocol that is recommended by industry titans like
Microsoft and NIST. - Security professionals advise against using credential-based auth protocol like TTLS/PAP and MSCHAPv2
and instead integrating passwordless auth protocols.
802.1x Authentication Methods
Before users can be authenticated for network access day-to-day, they must be onboarded to the secure network. Onboarding is the process of reviewing and approving users so they can connect to the secure network using a form of identification, such as username/password or certificates. This process often becomes a significant burden because it requires users to get their devices configured for the network. For regular network users, the process can prove to be too difficult because it requires high-level IT knowledge to understand the steps. For example, universities at the beginning of an academic year experience this when onboarding hundreds or even thousands of student's devices and results in long lines of support tickets. Onboarding clients offer an easy-to-use alternative that enables end users to easily self-configure their devices in a few steps, saving users and IT admins a ton of time and money.
Password-Based Authentication
The vast majority of authentication methods rely on a username/password. It's the easiest to deploy since most institutions already have some sort of credentials set up, but the network is susceptible to all of the problems of passwords without an onboarding system (see below).
For password-based authentication, there are basically 2 options: PEAP-MSCHAPv2 and EAP-TTLS/PAP. They both function similarly, but TTLS is not supported by any Microsoft OS before Windows 8 without using a third-party 802.1x supplicant, such as our Enterprise Client. At this point, most institutions have deployed or made the switch to PEAP. However, you can't deploy PEAP without either using Active Directory (a proprietary Microsoft service) or leaving your passwords unencrypted.
Key Takeaways
- Over 80% of data breaches can be traced back to lost and stolen passwords. C onsider moving towards
certificate-based authentication.
Token-Based Authentication
Historically, tokens were physical devices in the form of key fobs or dongles that would be distributed to users. They generated numbers in sync with a server to add additional validation to a connection. Even though you can carry them around and utilize advanced features like fingerprint scanners or as USB plug-ins, dongles do have downsides. They can be expensive and are known to occasionally lose connection to the servers.
Physical tokens are still in use, but their popularity is waning as smartphones have made them redundant. What was once loaded onto a fob you can now put into an app. In addition, there are other methods for two-factor authentication outside of the EAP method itself, such as text or email confirmations to validate a device.
Key Takeaways
- There is no standard structure for an access token; it can theoretically contain anything and the
client
would have no way of knowing. - A bad actor can easily inject a leaked or stolen access token and impersonate the resource server when
the client accepts access tokens.
Certificate-Based Authentication
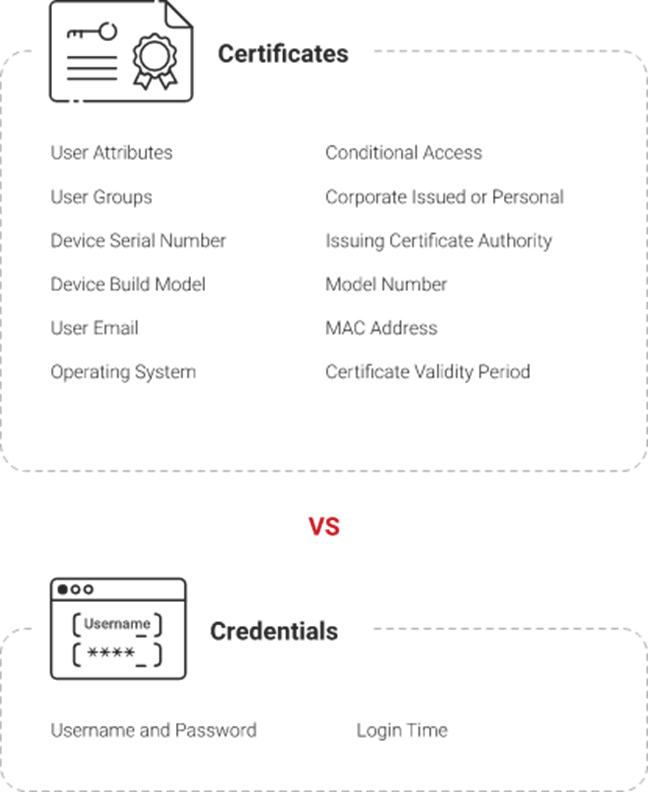
Certificates have long been a mainstay of authentication in general, but are not typically deployed in BYOD settings since certificates require users to install them on their own devices. However, once a certificate is installed, they are amazingly convenient: they are not affected by password change policies, is far safer than usernames/passwords, and devices are authenticated faster.
SecureW2's PKI services, combined with the JoinNow onboarding client, create a turnkey solution for certificate-based Wi-Fi authentication. An effective PKI provides all the necessary infrastructure to implement a certificate-based network and maintains the security and distribution of all network certificates.. Organizations can now seamlessly distribute certificates to devices and manage them with ease using our powerful certificate management features.
Key Takeaways
- 802.1x is used to secure end users to an enterprise network and its applications through Wi-Fi or VPN.
- An ideal 802.1x deployment method is a passwordless onboarding service that automates 802.1x
configuration rather than relying on end-users to configure. - Digital certificates are a passwordless solution because they can be programmed to guide the end user
through the onboarding process.
WPA2-Enterprise Challenges
In our experience, we've found that the average WPA2-Enterprise network suffers from a combination of these 4 problems:
Drawback #1: Device variation
When IEEE created the 802.1x protocol in 2001, there were few devices that could use wireless access and network management was much simpler. Since then, the number of device manufacturers has exploded with the rise of mobile computing. To give some perspective, there are more flavors of Android today than there were entire operating systems in 2001.
Support for 802.1x is inconsistent across devices, even between devices of the same OS. Each device has unique characteristics that can make them behave unpredictably. This problem is made worse by unique drivers and software installed on the device.
Drawback #2: MITM and delivering certificates
While WPA2 offers a very secure connection, you also have to be sure that the users will only connect to the secure network. A secure connection is meaningless if the user unknowingly connected to a honeypot or imposter signal. Institutions often sweep for and detect rogue access points, including Man-in-the-Middle attacks, but users can still be vulnerable off-site. A person with a laptop can attempt to quietly gather user credentials at a bus stop, coffee shop, or anywhere devices might pass through and try to auto-connect.
Even if the server has a certificate properly configured, there's no guarantee that users won't connect to a rogue SSID and accept any certificates presented to them. The best practice is to install the public key on the user's device to automatically verify the certificates presented by the server.
Drawback #3: The Password change problem
Networks with passwords that expire on a regular basis face an additional burden with WPA2-Enterprise. Each device will lose connectivity until reconfigured. This was less of an issue when the average user had only one device, but in today's BYOD environment, each user is likely to have multiple devices that all require a secure network connection. Depending on how password changes are enacted or the users' abilities to manage passwords, this can be a burden on helpdesks.
It's even worse on networks that have unexpected password changes due to data breaches or security vulnerabilities. In addition to having to roll out new credentials site-wide, IT has to deal with an influx of helpdesk tickets related to Wi-Fi.
Drawback #4: Changing user expectation
By far the most difficult part of completing a WPA2-Enterprise network setup is training the users. Users today have incredibly high expectations for ease of use. They also have more options than ever to work around official access. If the network is too hard to use, they'll use data. If the certificate is bad, they will ignore it. If they can't access something they want, they will use a proxy.
For WPA2-Enterprise to be effective, you need to make it as easy as possible for network users to navigate without sacrificing security.
Before you get started on your WPA2-Enterprise network, check out our primer on the most common mistakes people make when setting up WPA2-Enterprise.
Key Takeaways
- WPA2-Enterprise isn't without its challenges ; the main vulnerabilities in WPA2-Enterprise can be
traced
to stolen credentials and misconfigured clients. - These issues can be addressed by tying network security with your Cloud Identity using certificates.
Simplifying WPA2-Enterprise with JoinNow
A properly configured WPA2-Enterprise network utilizing 802.1x authentication is a powerful tool for protecting the safety of network users and securing valuable data; but by no means is this the end of network considerations you need to make. Many components contribute to the security and usability of the network as a complete system. If just the authentication method is secure while the configuration of managed devices is left to the average network user, there is a serious risk to the integrity of the network. SecureW2 recognizes that every facet of the wireless network must work in unison for iron-clad security, so we've provided some turnkey concepts that every network administrator needs to consider in their network planning.
Key Takeaways
- Streamline WPA2-Enterprise implementation with a Managed PKI service that is designed to easily
integrate into your existing architecture. - The JoinNow Connector leverages digital certificate and allows organizations to implement Zero Trust
initiatives.
Efficiency Through Onboarding

One of the greatest challenges for network administrators is efficiently and accurately onboarding users to the secure network. If left to their own devices, many users will misconfigure. Configuring for a WPA2-Enterprise network with 802.1x authentication is not a simple process and involves several steps that a person unfamiliar with IT concepts would not understand. If users are not connecting to the secure SSID and are not properly set up for WPA2-Enterprise, the security benefits admins expect will be lost. For those that want the advantages that come with certificate-based networks, many opt to deploy an onboarding client that will automatically configure users devices.
Onboarding clients, such as those offered by SecureW2, eliminate the confusion for users by prompting them with only a few, simple steps designed to be completed by K-12 age students and up. The result is a properly configured WPA2-Enterprise network with 802.1x authentication that has successfully onboarded all network users to the secure network.
Want more info on the advantages of a streamlined and secure Bring Your Own Device (BYOD) Onboarding software? Check out this informative piece on onboarding!
Key Takeaways
- The best PKI solution provides self-service software for BYOD and unmanaged devices that automatically
administers 802.1x settings.
Certificate-Hardened WPA2-Enterprise
A PKI enables organizations to use x.509 certificates and distribute them to network users. It consists of an HSM (Hardware Security Module), CAs, client, public and private keys, and a CRL (Certificate Revocation List). An effective PKI significantly bolsters network security, allowing organizations to eliminate password-related issues with certificate-based authentication. Once the PKI is configured, network users can begin enrolling for certificates. This is a challenging task to complete, but organizations that have used an onboarding client have had the most success distributing certificates. SecureW2 is able to provide all the tools needed for a successful PKI deployment and efficient distribution of certificates. After equipping their devices with a certificate, users are ready to be authenticated for the wireless network. Beyond secure wireless authentication, certificates can be used for VPN, Web application authentication, SSL Inspection security, and much more.
Key Takeaways
- Our JoinNow Connector PKI supplies a robust framework for passwordless security to strongly
authenticate
devices, networks, and apps.
WPA2-Enterprise Managed Device Configuration
Enterprises with managed devices often lack a unified method of getting devices configured for certificate-driven security. Allowing users to self-configure often results in many misconfigured devices, and leaving the task to IT can be mountainous. Configuring dozens, or sometimes even hundreds, of devices manually for a secure WPA2-Enterprise network is often considered too labor-intensive to be worthwhile. SecureW2's advanced SCEP and WSTEP gateways provide a means to auto-enroll managed devices with no end user interaction. In one fell swoop, these gateways allow an IT department to configure managed devices from any major vendor for certificate-driven network security.
Key Takeaways
- Use your device management platforms (including IoT) and MDM / EMM platforms via JoinNow's APIs to
distribute and manage certificates.
RADIUS Servers and Policy Driven Access Control
The RADIUS server plays a critical role in the network, authenticating every device when they connect to the network. SecureW2's JoinNow solution comes built-in with a world-class Cloud RADIUS server, providing powerful, policy-driven 802.1x authentication. Backed by AWS, it delivers high availability, consistent and quality connections, and requires no physical installation. The server can be easily configured and customized to fit any organizations' requirements, with no forklift upgrades of existing infrastructure required. Once fully integrated, the certificate-based network is ready to begin authenticating network users.
SecureW2 also offers an industry-first technology we call Dynamic Cloud RADIUS that allows the RADIUS to directly reference the directory – even cloud directories like Google, Azure, and Okta. Instead of making policy decisions based on static certificates, the RADIUS makes runtime-level policy decisions based on user attributes stored in the directory.
Dynamic RADIUS is an enhanced RADIUS with better security and easier user management. Want to know more? Talk to one of our experts to see if your WPA2-Enterprise network can benefit from Dynamic RADIUS.
The keys to a successful RADIUS deployment are availability, consistency, and speed. SecureW2's Cloud RADIUS equips organizations with the tools they need to make the secure network easy to connect to and always available so users are consistently protected from outside threats.
Ready to take the next step in improving user experience and hardening your network security? The transition process is easier than you think. Click here if you'd like to get in touch with one of our experts.
Key Takeaways
- Certificate security requires high-performance authentication - you need to implement a cloud-native
RADIUS designed for passwordless and cloud identity-driven security.
FAQs
What is a WPA2-Enterprise Network?
The core difference between a WPA2-Enterprise Wi-Fi network and the type of Wi-Fi network you use at home is the method you use to authenticate. In a standard home Wi-Fi network, which uses WPA2-PSK, you enter a single password to gain access. This password is the same for all connected devices.
A WPA2-Enterprise network requires all devices to log into the Wi-Fi with unique credentials. This means that everyone either has their own username and password or they have their own digital certificate. It’s beneficial for a few reasons: it allows administrators more visibility over who’s connected to the network and can prevent the spread of compromise. If one set of credentials is stolen, it’s easier to disconnect the associated device and deactivate those credentials than to disconnect all devices when the single password used in a PSK network is compromised. Without WPA2-Enterprise, organizations that offer network connectivity to large groups of users, like universities, are helpless to cease and desist letters when users illegally download copyrighted material, since they cannot associate network connections to users/devices.
What is Required for a WPA2-Enterprise Network?
A WPA2-Enterprise network typically needs a directory that contains all the individual user credentials for access and some way of authenticating those credentials or certificates as users and devices connect. One of the main differences between a WPA2-PSK network and a WPA2-Enterprise network is the use of an authentication server, also known as a RADIUS server.
Authentication servers are compatible with a number of authentication protocols. We personally recommend the Extensible Authentication Protocol with TLS, which is certificate-based authentication for wireless networks. Wired and wireless networks can be secured more rigorously with digital certificates, as they cannot be stolen or transferred.
Can a Router Be a RADIUS Server?
A router cannot be used as a RADIUS server. In order to achieve its core function of authenticating other devices on your network, a RADIUS needs to be its own separate machine dedicated to authentication specifically.
How Do I Set Up a RADIUS Server as a WiFi hotspot?
RADIUS servers cannot be used as Wi-Fi hotspots. By definition, a RADIUS server is its own separate device whose function is to authenticate users and devices when they access your network. The RADIUS server is not itself an access point - it simply tells the access point to grant network access to authorized users.
How Do I Set Up a Wireless RADIUS Server?
Setting up a wireless RADIUS server can vary depending on the APs you’re using and, of course, your RADIUS provider. With Cloud RADIUS, however, it’s relatively simple and can be completed in several easy steps:
- Create a RADIUS profile in your wireless controller.
- Navigate to AAA management, then AAA configuration in the SecureW2 Management Portal.
- Note the Primary IP Address, Port, and Shared Secret.
- Input this information into the RADIUS profile you created.
- Save the new RADIUS profile.
You can learn more about configuring RADIUS with an AP in one of our integration guides.
How Does Wi-Fi RADIUS Authentication Work?
RADIUS can be described as a virtual bouncer at a virtual gate. When a user attempts to access your network, the RADIUS server checks that their credentials or certificates are valid by comparing them to a directory or Certificate Revocation List.
What is the Benefit of RADIUS?
The main benefit to RADIUS is that it makes it possible for users to each use their own set of credentials to access the Wi-Fi or VPN, as opposed to sharing credentials. Individual credentials increase security, and if they’re stolen, the breach can be stopped by changing or revoking the single set of stolen credentials rather than all of them.
How Do I Set Up WPA2-Enterprise at Home?
In most home environments, WPA2-PSK (Wi-Fi access based on a single password) is sufficient. However, it is possible to set up WPA2-Enterprise at home if you have the expertise and are willing to invest more time, hardware, and maintenance into it.
You’ll need to establish a directory to keep user credentials in. For enterprise settings, this is almost always an Identity Provider such as Azure AD or Google. Some devices may even allow you to enter in a few sets of credentials if you don’t want a separate database.
Additionally, you’ll need to establish a RADIUS server to authenticate all access requests and an access point that supports this type of authentication. You can find access points with RADIUS built into them, or use something sufficient for home use like pfSense or Microsoft NPS.
Keep in mind that this isn’t strictly necessary in the majority of home settings where Wi-Fi is used primarily for recreational purposes.
How Do I Connect to WPA2-Enterprise Wi-Fi?
From an end user’s perspective, connecting to the WPA2-Enterprise Wi-Fi network is mostly the same as connecting to Wi-Fi at home. They choose the network they want to connect to and enter a password or, if certificates are being used, authenticate automatically with certificates. The authentication server responds with an ACCESS_ACCEPT or ACCESS_REJECT message based on the status of these credentials or certificates.
In an enterprise environment, connecting to WPA2-Enterprise Wi-Fi is often done automatically through an MDM (like Intune, Jamf, or Google). MDMs can send Network Profiles, which are essentially scripts that automatically configure a device for the necessary settings for WPA2-Enterprise, so end users don’t have to configure anything they just open their laptop at work and they are connected.
How Can Certificates Be Used for Wi-Fi Authentication?
With the right setup, certificates can completely replace passwords in Wi-Fi authentication. They allow administrators to leverage the information from their Identity Provider and apply that to their Wi-Fi access. Certificates can contain detailed information about each user and device which is retrieved from the Identity Provider at the time the user enrolls for a certificate.
Once they have a certificate, they present the certificate to the RADIUS server when they connect to Wi-Fi instead of entering a password. The RADIUS then checks if the certificate is expired. With Cloud RADIUS, the authentication is taken a step further and the Identity Provider is checked in real-time during the authentication process to ensure the user exists in the IDP.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Schedule NowPricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.
Check Pricing