What is S/MIME?
S/MIME stands for “Secure/Multipurpose Internet Mail Extensions”. It’s an IETF standard for public key encryption, as well as for creating a digital signature for MIME data.
In essence, S/MIME uses a PKI to enroll an email client for certificates (sometimes more than one). It can use those certificates in a variety of tasks, from authentication and encryption to prevent malicious actors from interfering with your communication.
It’s true that few emails are sent without some sort of encryption nowadays, but standard email encryption (usually SMTP over TLS, or STARTTLS) isn’t really comparable to the rigor intrinsic to S/MIME, which uses public key cryptography for end-to-end email encryption.
S/MIME Use Cases
This messaging standard inherently supports many functions that enhance and secure emails. It can be used to:
- Create digital signatures (also known as “non-repudiation of origin”)
- Ensure message privacy
- Encrypt messages
- Authenticate to the web client
- Ensure “message integrity” (to confirm the message hasn’t been altered)
The most obvious implementation of S/MIME is as a stronger form of email encryption, but when used to its full extent, it provides critical services that go beyond simple encryption and help protect you from social engineering attacks too.
Why is S/MIME Important?
If you’re not enamored by the mere idea of using ultra-secure certificates anywhere that will support them, we’ll give you a couple reasons why you actually do need S/MIME protecting your emails.
S/MIME Prevents Phishing Attacks
A very common method of phishing is to send fraudulent emails that trick the recipient into performing a task, usually to send money or pass on credentials.
A new type of phishing called “whaling” is becoming more common. In this attack, the hacker targets a senior employee – one who has access to financial resources – and impersonates their superior. Usually, the hacker is able to spoof the email address of the CEO or similar and requests the victim to buy large gift cards and reply with the code.
Training employees to detect and avoid phishing attacks is very difficult. Instructing them to potentially ignore emails that appear to be from their boss is even more challenging – and might cause them to dismiss important communiques.
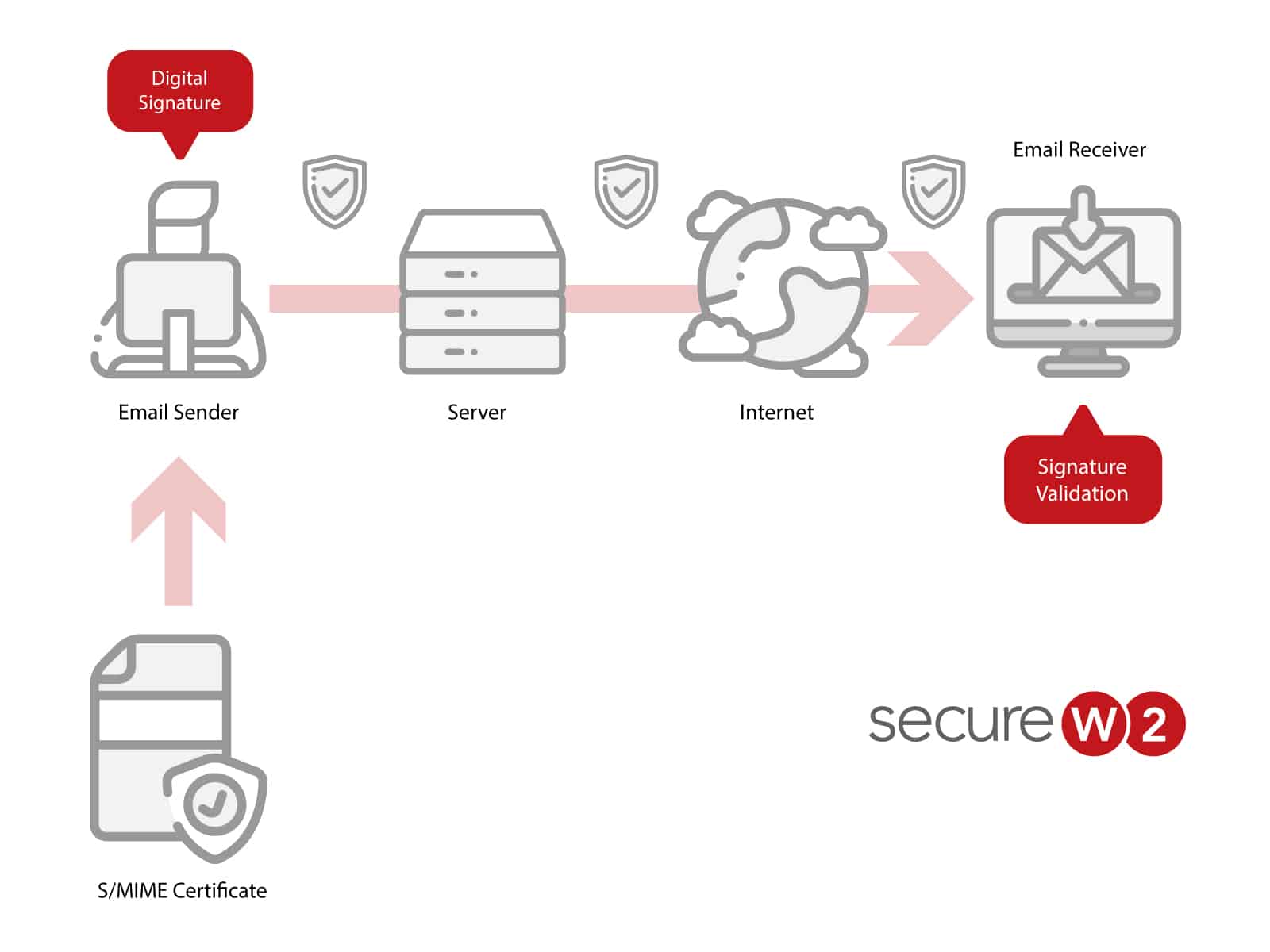
S/MIME prevents email phishing scams better than any other defense hands down.
S/MIME Enables Secure Communication
Money isn’t the only valuable thing your organization produces, however.
Information is just as valuable, and we send critical information through email every day. Passwords, product specs, the Krabby Patty Formula – we often don’t even realize we’re discussing things that should be kept secret.
The same certificate that lets us know for certain the identity of the sender can also be used to enable end-to-end encryption for emails within your network. Since the email was encrypted at the beginning and only decrypted at the receiver’s end, you can be assured that your email’s contents were not seen by anyone… including your organization’s firewall.
That can be particularly dangerous in other scenarios in which you aren’t certain of the sender’s true identity, but since S/MIME solves that problem, you can be reasonably sure no one in your organization is emailing you trojans.
In the same vein, no one can intercept and alter emails, thanks to S/MIME’s inherent preservation of email integrity.
S/MIME Configuration Guide for Intune
You may be surprised to find that S/MIME is easy to configure yourself – as long as your organization uses a managed PKI service like SecureW2. Here’s a stepy-by-step guiding to enabling S/MIME via Intune and SecureW2:
- Log in to the SecureW2 Management Portal.
- Navigate to PKI Management –> Certificate Authorities.
- In the Certificate Templates section, please Edit the Intune Certificate Template.
- Now, scroll to the Extended Key Usage section and select/enable Email Protection along with Client Authentication.
- Finally, click on Update for the changes to take effect.
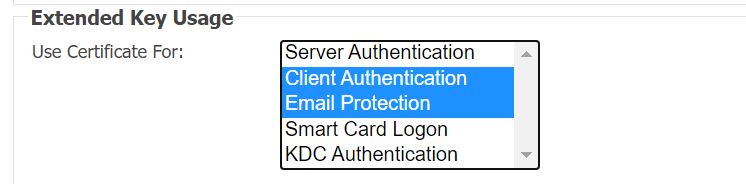 After this, the devices that are managed by Intune will issue certificates that can be used for mail encryption and signing.
After this, the devices that are managed by Intune will issue certificates that can be used for mail encryption and signing.
NOTE: The SecureW2 PKI Root and Intermediate certificate should be available/imported in the end clients so that the chain is complete for S/MIME to work as expected.
Use S/MIME to Protect Your Organization’s Communications
Given the rise of phishing attacks, being able to verify the identity of email senders is critical to maintaining a strong security perimeter. Considering the additional security advantages, implementing S/MIME is a no-brainer.
Note that since S/MIME uses certificates to secure emails, it requires a Public Key Infrastructure (PKI) to provision them. If you already have a PKI, S/MIME is easy to set up. If you don’t yet have PKI, SecureW2 is one of the industry’s leading providers of Managed Cloud PKI.
We have affordable options for organizations of all sizes. Check out our pricing form here.