How to Set Up LDAP For Certificate-Based WPA2-Enterprise
Utilizing certificate-based authentication provides stronger security, easier authentication, and an improved user experience when compared to credential-based authentication – but only when it is supported by an efficient onboarding method. Integrating LDAP as your IDP with SecureW2’s certificate onboarding solutions allows users to provision their devices with certificates in only a few steps.
By connecting LDAP with effective certificate onboarding, your network can accurately distribute certificates to network users and ensure that no unapproved users can gain access. Since certificates from SecureW2 cannot be removed or transferred from the device, only those with valid LDAP credentials will be able to receive a certificate.
The following demonstrates the steps involved to configure the integration:
- Configure the Identity Provider
- Begin by configuring the attribute mapping of the IDP. Here you will customize the fields that are populated by the attributes of your network users and will be used to define different user groups within your network.
- Configure the Network Policies
- Nearly all organizations have different user groups that require varying levels of access to networks, servers, data, etc. By onboarding with SecureW2, you can automatically separate users into groups by configuring their attributes to identify and segment users. For example, a university would configure the onboarding software to segment users based on their status as a student or a professor.
NOTE: You will perform all of these procedures in the SecureW2 Management Portal.
Configure the Identity Provider
To configure the identity provider (IDP):
- From your SecureW2 Management Portal, go to Identity Management > Identity Providers
- Click Add Identity Provider
- For Name, enter a name
- Click the Type dropdown and select LDAP
- Click Save
- Select the Connections tab and click Add Connection
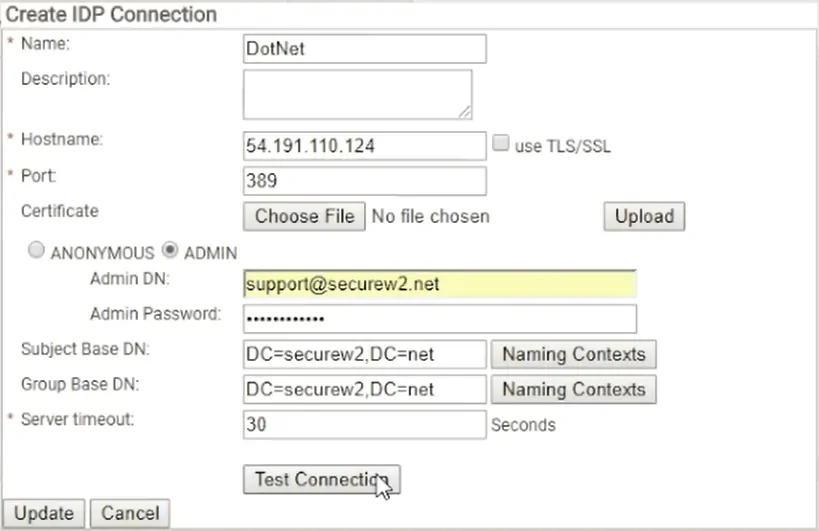
- For Name, enter a name
- For Hostname, enter ‘54.191.110.124‘
- For Port, enter ‘389‘
- For Admin DN, enter ‘support.securew2.com‘
- For Admin Password, enter the password
- For Subject Base DN, enter ‘DC=securew2,DC=net‘
- For Group Base DN, enter ‘DC=securew2,DC=net‘
- For Server timeout, enter ‘30‘
- Click Test Connection
- After the connection is successfully tested, click Update
- Select the Basic tab
- For Subject Name Attribute, enter:
- ‘sAMAccountName‘ (users log in with only their username), or ‘userPrincipalNames‘ (users log in with their username and realm)
- Click Update
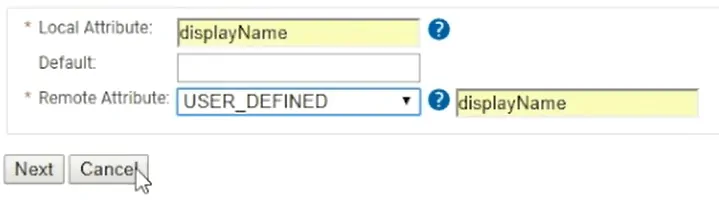
- Select the Attribute Mapping tab and click Add
- For Local Attribute, enter ‘displayName‘
- Click the Remote Attribute dropdown and select USER_DEFINED
- In the field that appears, enter ‘displayName‘
- Click Next -> Add
- For Local Attribute, enter ‘upn‘
- Click the Remote Attribute dropdown and select USER_DEFINED
- In the field that appears, enter ‘upn‘
- Click Next -> Add
- For Local Attribute, enter ‘email‘
- Click the Remote Attribute dropdown and select USER_DEFINED
- In the field that appears, enter ‘email‘
- Click Next
- Select the Groups tab and click Add
- For Local Group, enter a name
- For Remote Group, enter ‘CN=SECUREW2-STAFF,CN=Users,DC=securew2,DC=net‘
- NOTE: The value for Remote Group is case sensitive
- Click Next -> Update
- To ensure that everything is working properly, select the Connections tab and test the connection again
Configure LDAP IDP Profile Policy
To configure the profile policy:
- From your SecureW2 Management Portal, go to Policy Management > Profile
- Click Add Profile Policy
- For Name, enter a name
- Click Save
- Select the Conditions tab
- Click the Profile dropdown and select the profile you created in the previous section
- Select the Settings tab
- Click the Identity Provider dropdown and select the IDP you created in the previous section
- Click Update
Configure LDAP IDP User Role Policy
To configure the user role policy:
- From your SecureW2 Management Portal, go to Policy Management > User Roles
- Click Add Role
- For Name, enter a name
- Click Save
- Select the Conditions tab
- Click the Identity Provider dropdown and select the IDP you created in the section “Configure the Identity Provider”
- Click Update
Configure the Enrollment Policy
To configure the enrollment policy:
- From your SecureW2 Management Portal, go to Policy Management > Enrollment
- Click Add Enrollment Policy
- For Name, enter a name
- Click Save
- Select the Conditions tab
- In the User Role list, select the user role you created in the previous section
- In the Device Role list, select DEFAULT DEVICE ROLE POLICY 1
- Click Update
SecureW2 offers a cost-effective solution to streamline device onboarding and strengthen network security. Head over to our pricing page to learn more.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Schedule NowPricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.
Check Pricing