How to Issue AD CS Certificates for EAP-TLS Network Authentication
Enrolling ADCS Certificates and Installing them on BYOD Devices
With SecureW2’s #1 Rated Onboarding Client, organizations can easily install certificates and configure certificate-based WPA2-Enterprise Wi-Fi settings on any BYOD device. With solutions for every Operating System, all you need to do is direct users to the SecureW2 Landing Page and their OS will be detected, with the appropriate Onboarding Client deployed to their device. From there, they go through a one-time configuration. They enter in their credentials, and the client will enroll them for a unique client certificate and configure their device to use that certificate for secure network access.
Configure the Landing Page and Onboarding Clients
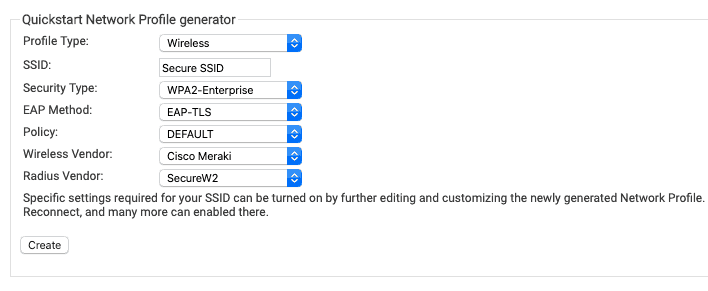
The first step in integrating ADCS with SecureW2, is using our Getting Started Wizard. This will configure default settings for everything you need for WPA2-Enterprise Certificate-Based Authentication.
- Navigate to Device Onboarding → Getting Started
- Configure the appropriate settings on the Wizard like the Image below. Make sure the SSID name matches the SSID we will configure later for certificate authentication.
- After the Wizard finishes running, navigate to Device Onboarding → Network Profiles
- Click View on the newly generated Network Profile and you will be redirected to your new Landing Page
Now that we’ve got our Landing Page and Onboarding Clients, we need to configure them to generate certificate with our ADCS Root CA. After that, we will configure network settings, go over methods of distributing the Landing Page, and you will be all set to get certificates on your BYOD devices.
Import your ADCS Certificate to SecureW2
Start by downloading your Root CA from ADCS. Once you’ve done that, we can import them into SecureW2.
- Navigate to Device Onboarding → Network Profiles and click Edit on your Network Profile.
- Under the Certificates tab, select Add/Remove Certificate
- Under the Private Certificate option, click Choose File and select your ADCS Root CA
- Click Upload
- Click Update
- Under the Network Settings tab, click Edit on your Network Setting. Here we need to configure Server Certificate Validation is setup on our devices with our ADCS CA
- Under the Server Certificate tab, ensure that Enable Server Certificate Validation is checked
- Under Specify CA Certificates check Trust on your ADCS Root CA and uncheck Trust on the CA included by default (GeoTrust)
- Ensure that the Connect to these server names setting is configured for the organization that your CA belongs to.
- Click Update
- Now you can Delete the CA that is included in the Network Profile by default (GeoTrust)
- Update your settings.
- Click Republish on your Network Profile to push your recently configure settings.
Now your Onboarding Clients will enroll devices for a client certificate issued by your ADCS Root CA and you can test them accordingly. Now all that’s left is to configure your Access Points and RADIUS Server for certificate-based authentication and direct the SecureW2 landing page to your users.
Direct Users to the Landing Page
There are several ways to get users to the SecureW2 landing page. We typically recommend configuring an ‘Onboarding SSID’, Open SSID that is restricted to SecureW2 resources and redirects to our Landing Page, and getting users to configure their devices at home or using mobile data. For more information on creating Onboarding SSIDs, visit our Wi-Fi integrations page for integration guides for the major networking vendors.
Using AD CS to Issue Certificates to Managed Devices
Our powerful certificate enrollment gateway will enable any MDM you choose (Jamf, Airwatch, Intune, GPO, Google Workspace, etc.) to push configuration payloads to your managed devices for automatic self-enrollment of certificates. For more info on supported systems, check out our managed device solutions page.
Below is an example that illustrates the ease with which you can use Jamf and SCEP to issue your AD CS certificates to all of your managed devices in just a few minutes.
Configure SCEP Gateway API in SecureW2
- Use our Getting Started Wizard to generate a shared secret key and an access token.
- Following the prompts, use the shared secret and the token to create a new SCEP URL. This URL will later be pushed to your devices to enable auto-enrollment for certificates.
- The last step is to create your Enrollment Policies. These can differ based on the needs of an organization, but most users will choose a setup similar to the one pictured below.
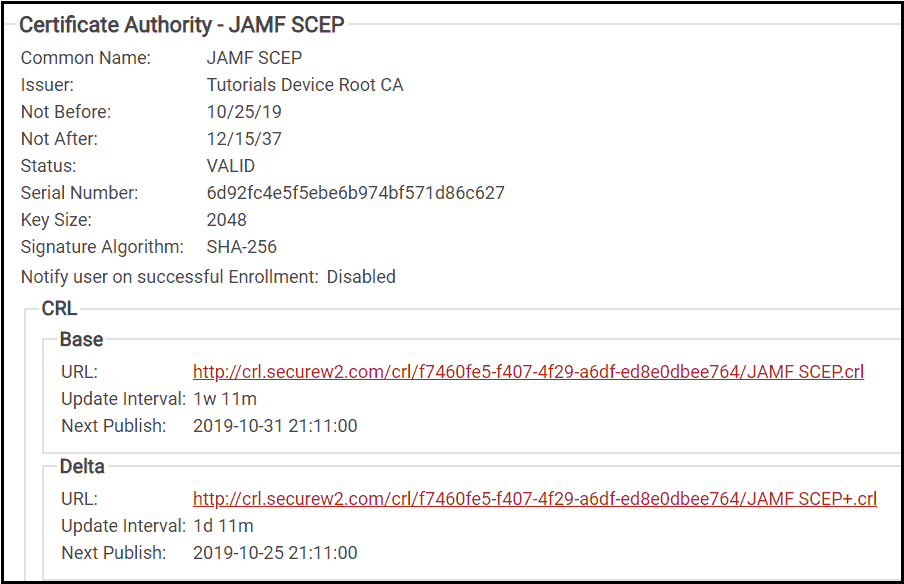
Configure Certificate Template for SCEP Gateway
- Insert the SCEP URL you previously created. It contains all the necessary instructions for your MDMs to configure themselves to request client certificates from SecureW2.The screenshot below is an example of a typical config for Jamf-managed devices.
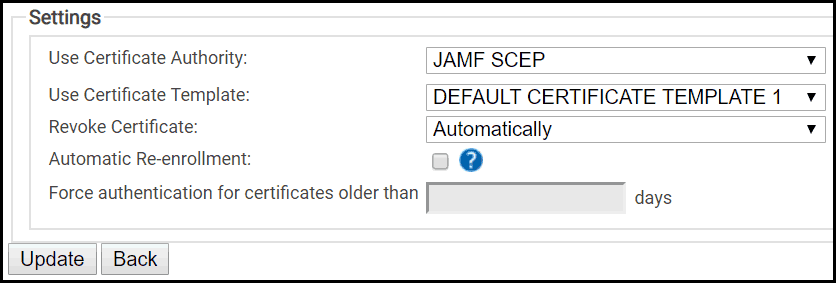
Push the Payload to Your MDM
- Now that your configuration profile (the ‘payload’ of network settings) is properly set up, you can push it to your devices through the recently configured SCEP Gateway.
Create an SSID for AD CS Certificate-Based Authentication
Now that we’ve configured SecureW2 to enroll our devices for certificates and configure them for certificate-based Wi-Fi, we need to create an SSID to use with our certificates.
Creating the SSID is quite easy, as all we need to do is make sure the name of the SSID matches the name on our Network Profile (you can change this later in the Network Settings), and the SSID points to a configured RADIUS Server. For more information about this, visit our Wi-Fi integrations page for detailed integration guides for all the Wi-Fi vendors.
Configuring the RADIUS Server is where most of the work comes in, but even this isn’t overly complex. If you choose to use the SecureW2 RADIUS Server, there is zero work involved after you enter the RADIUS details.
Configure the RADIUS Server
In a nutshell, configuring your existing RADIUS Server for certificate-based authentication takes 3 steps.
- Importing the ADCS Root CA to your RADIUS Server trust list
- Configuring the RADIUS Server to use the SecureW2 CRL
- And Identity Lookup if supported by your RADIUS Server. (Identity Lookup is supported by SecureW2’s RADIUS Server.)
- Configuring any authentication policies, like segmenting your network into VLANs
For more information about this, you can visit our RADIUS Integrations Page where we have detailed guides on how to integrate the SecureW2 PKI with all the major RADIUS servers. We also offer white-glove support on deployments, so head on over to our Free Demo page and see for yourself how SecureW2 can revolutionize your network security.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Schedule NowPricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.
Check Pricing