How to Set Up Passwordless WPA2-Enterprise and Tie Azure AD to Network Security
Many organizations today are adopting cloud-based and passwordless network solutions for their networks. Microsoft created Azure AD (Microsoft Entra ID) to help clients move their directories from an on-premise Active Directory (AD) server to the cloud. Unfortunately, Azure AD doesn’t support network authentication natively.
Some have adapted by syncing their Azure AD with an LDAP server, but this solution still uses PEAP-MSCHAPv2 for authentication.
For WiFi and VPN connections, Microsoft recommends move from MSCHAPv2-based (password) connections, to certificate-based authentication such as EAP-TLS.
EAP-TLS (certificate-based authentication) requires a Public Key Infrastructure to enroll and manage certificates to be used for Wi-Fi. That's why our cloud PKI and RADIUS are designed to easily integrate with Azure AD, so organizations can easily use their Azure AD for WPA2-Enterprise. Below we break down the solution into three steps:
- Tie your PKI Infrastructure to Azure AD.
- Tie your RADIUS Infrastructure to Azure AD.
- Tie your Device Management platform to SecureW2 cloud PKI.
How to Configure Managed Devices for 802.1X with Microsoft Endpoint Manager (Intune)
We’ve provided a high-level diagram showing how to use MEM Intune to enroll managed devices for certificates.
- Step 1: Configure your MDM platform with our PKI services to send out configuration profiles directing managed devices to auto-enroll for a certificate nad self-service for 802.1X.
- Step 2: Cloud RADIUS will authenticate the device for Wi-Fi access by directly communicating with your Azure AD.
Now that our devices are configured for certificate-based authentication, without the need for LDAP, we can use Cloud RADIUS to authenticate the user in Azure AD (or any major Cloud IDP for that matter) and authorize access at the time of authentication.
For a more detailed guide, check out how to use SCEP to enroll certificates on Intune devices.
Using Other MDMs for WPA2-Enterprise/802.1X
Azure is closely tied to Intune because they’re both Microsoft products. However, it is possible for other MDMs to be set up to deploy certificates. A common issue arises with Identity Lookup because many MDMs do not allow emails to be input into RFC on certificate templates, which prevents admins from identifying the user.
Our JoinNow suite offers a certificate enrollment Gateway APIs that can be used by any major MDM (Jamf, Airwatch, etc) to auto-enroll devices for certificates. Our industry-unique Identity Lookup integration will allow you to find specific certificates and identify devices.
Below is a detailed guide on how to integrate Azure and AD with SecureW2 to easily deploy certificates for EAP-TLS authentication and manage 802.1x network through the cloud.
Configuring a SAML Azure Application for WPA2-Enterprise
Create SAML Application in Azure
The SAML application is a crucial connection between the IDP and JoinNow MultiOS Management Portal. The application allows a user to enter their credentials, which are the passed to the IDP for verification.
To create a SAML application in Microsoft Azure:
- Log in to the Azure Portal.
- Type “Enterprise applications” in the search box and click Enterprise applications.
- In the main pane, click New application.
- On the Browse Azure AD Gallery page, type “SecureW2 JoinNow Connector”.
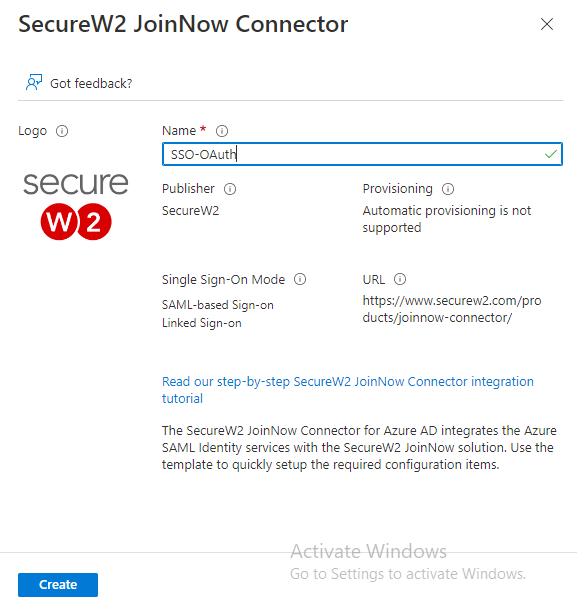
- Select SecureW2 JoinNow Connector and in the pop-up window type a name for the application and click Create.
Create Identity Provider in SecureW2
To create an IDP in SecureW2:
- To create an IDP, log in to the JoinNow MultiOS Management Portal.
- Go to Identity Management > Identity Providers and click Add Identity Provider.
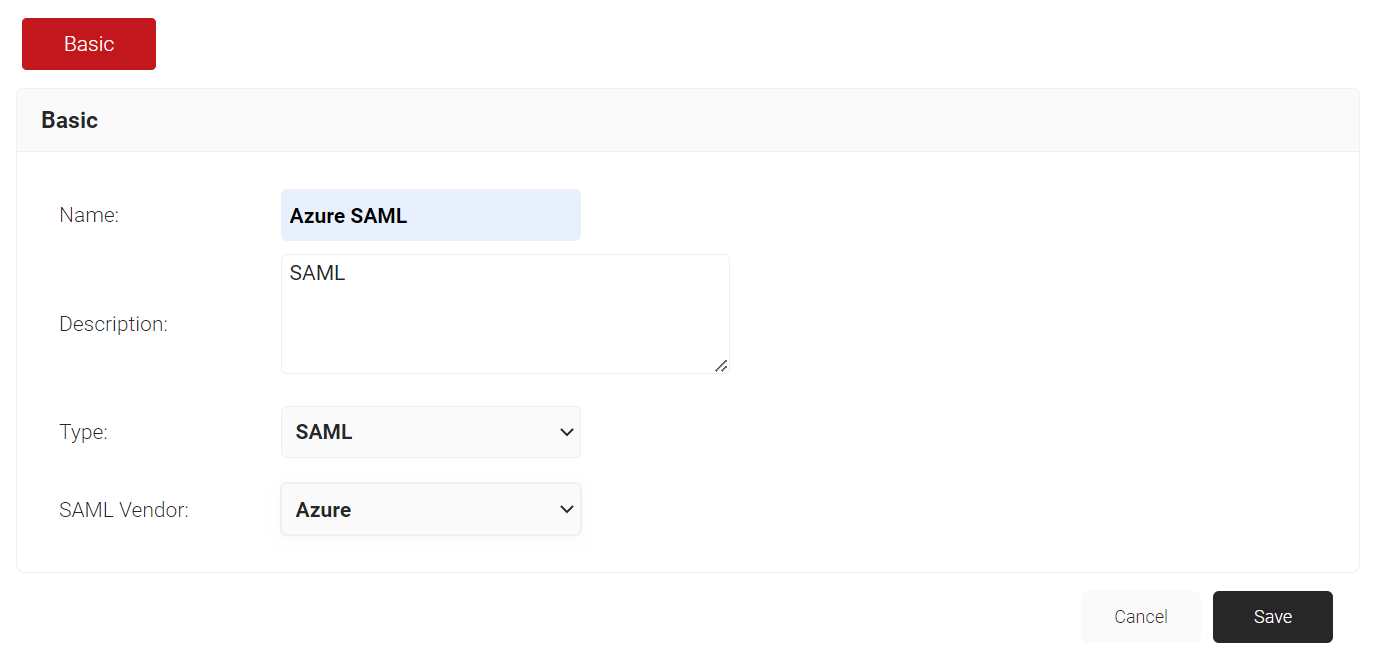
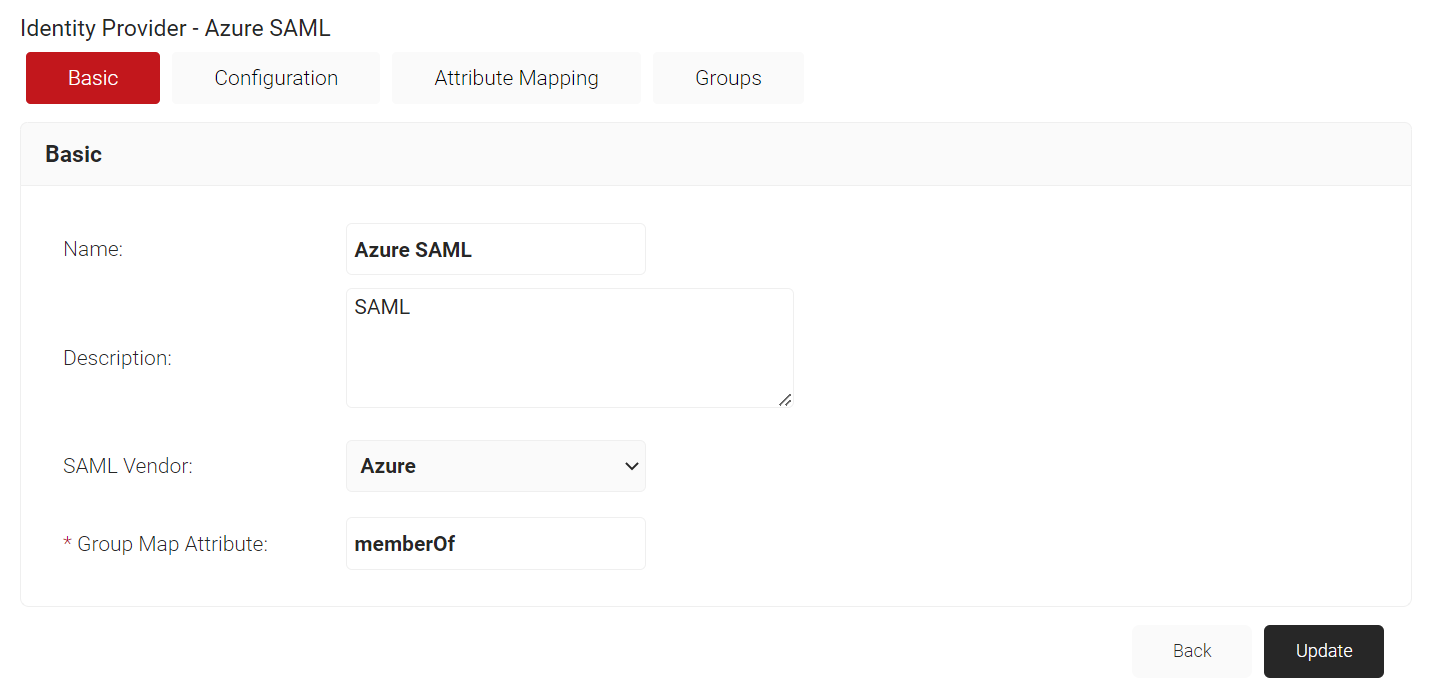
- Under the Basic tab, enter name and description.
- From the Type drop-down list, select SAML.
- From the SAML Vendor drop-down list, select Azure.
- Click Save. The following screen is displayed.
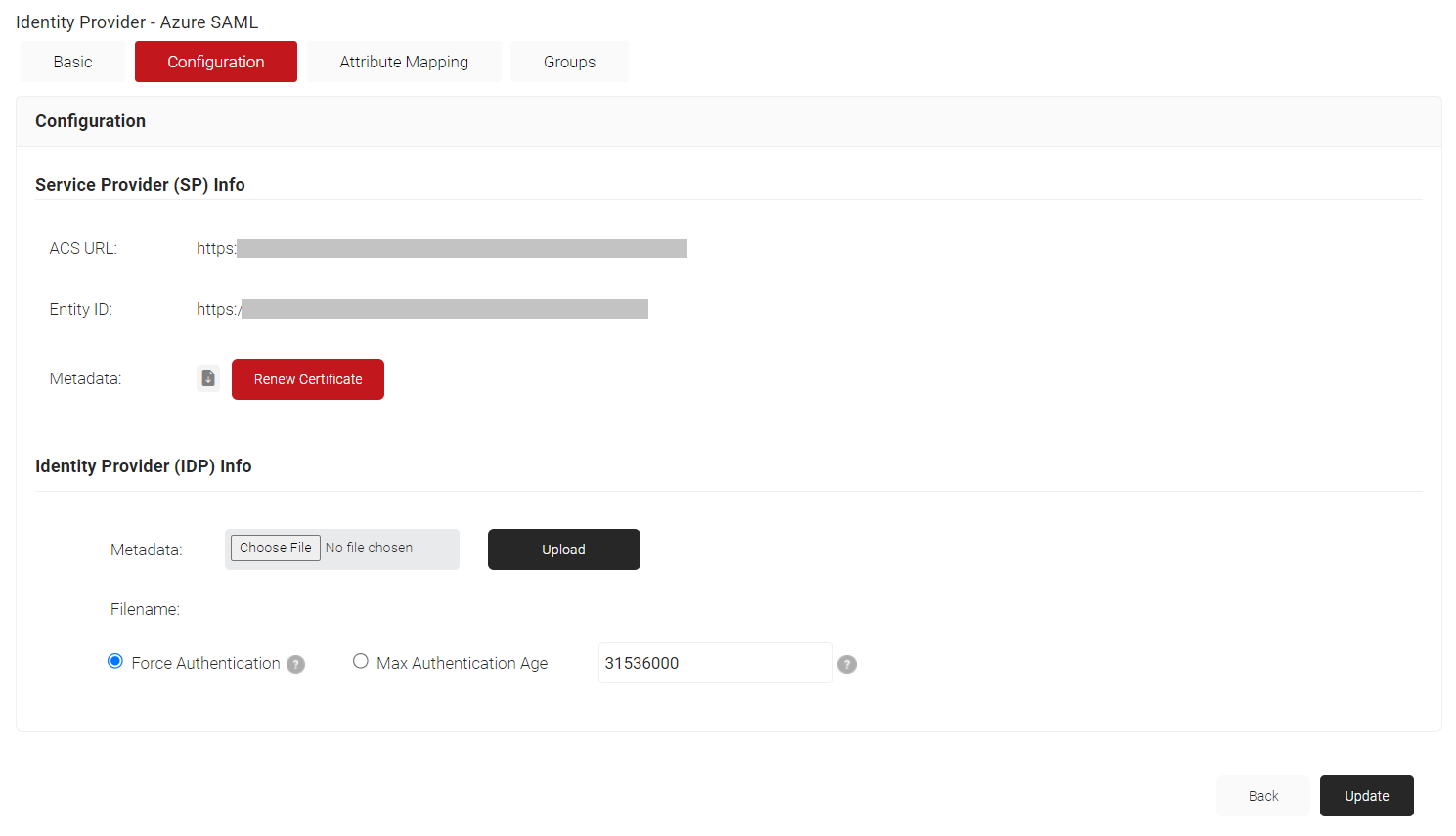
- Click the Configuration tab. Copy the Entity ID and ACS URL to your clipboard and save it in a word/text file. This will be used later while connecting with your SAML application.
Now, SecureW2 Cloud Connector knows how to exchange information with your Azure user database.
Configure Single-Sign-On in Azure
To configure single sign on in Microsoft Azure:
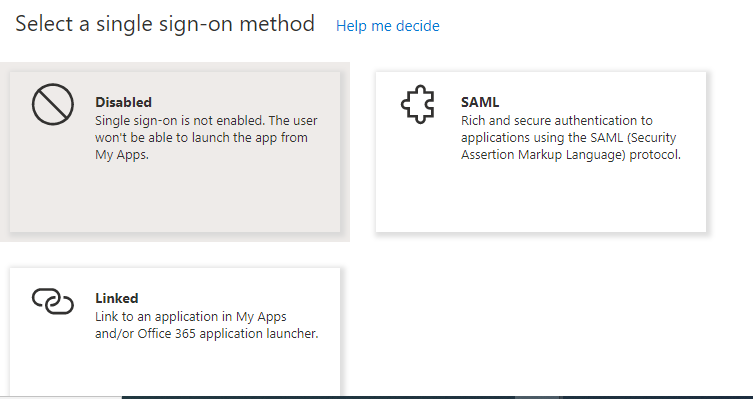
- In the left pane, navigate to Manage > Single sign-on.
- On the Single Sign-on page, select SAML-based Sign-on.
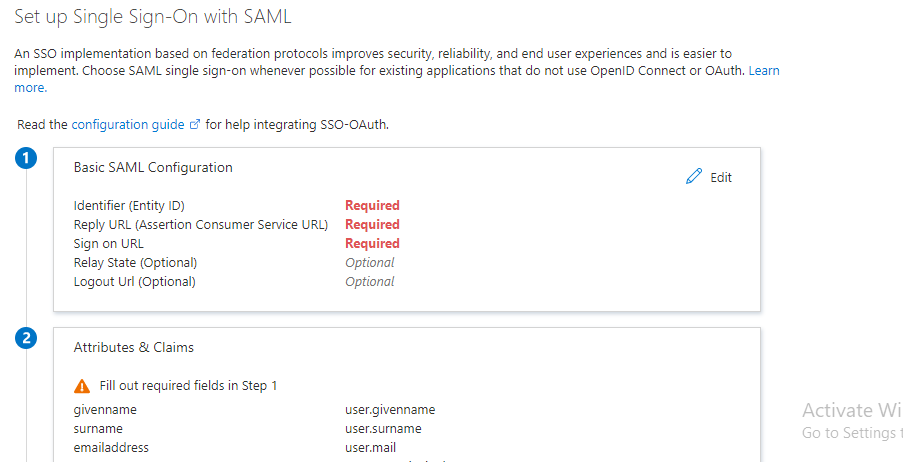
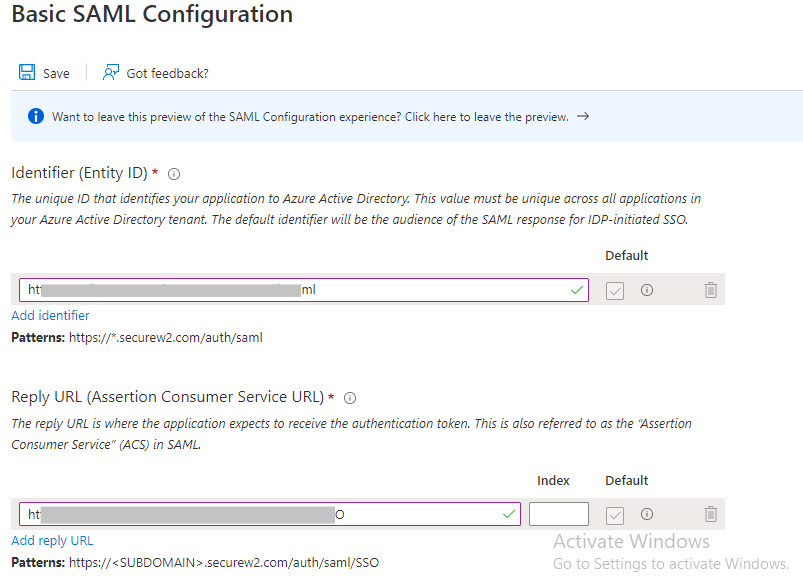
- In the Basic SAML Configuration section, click the Edit button.
- For the Identifier fields, enter the Entity ID and ACS URL values obtained earlier. (See Creating a SAML IDP, step 7)
- For the Sign on URL field, enter the same value as the Reply URL obtained from ACS URL.
- Click Save.
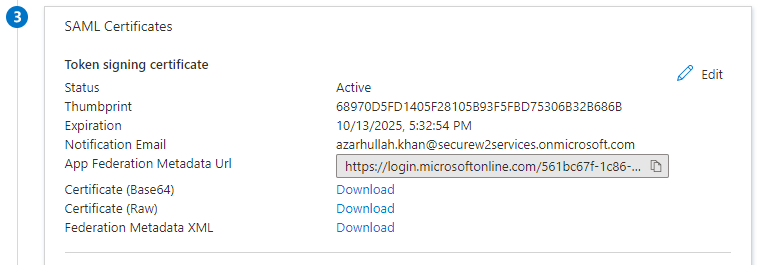
- Under the SAML Signing Certificates section, click the DOWNLOAD button to obtain the Federation Metadata XML file from Azure.
Configure the IDP with Azure Metadata
To upload the Azure metadata to SecureW2:
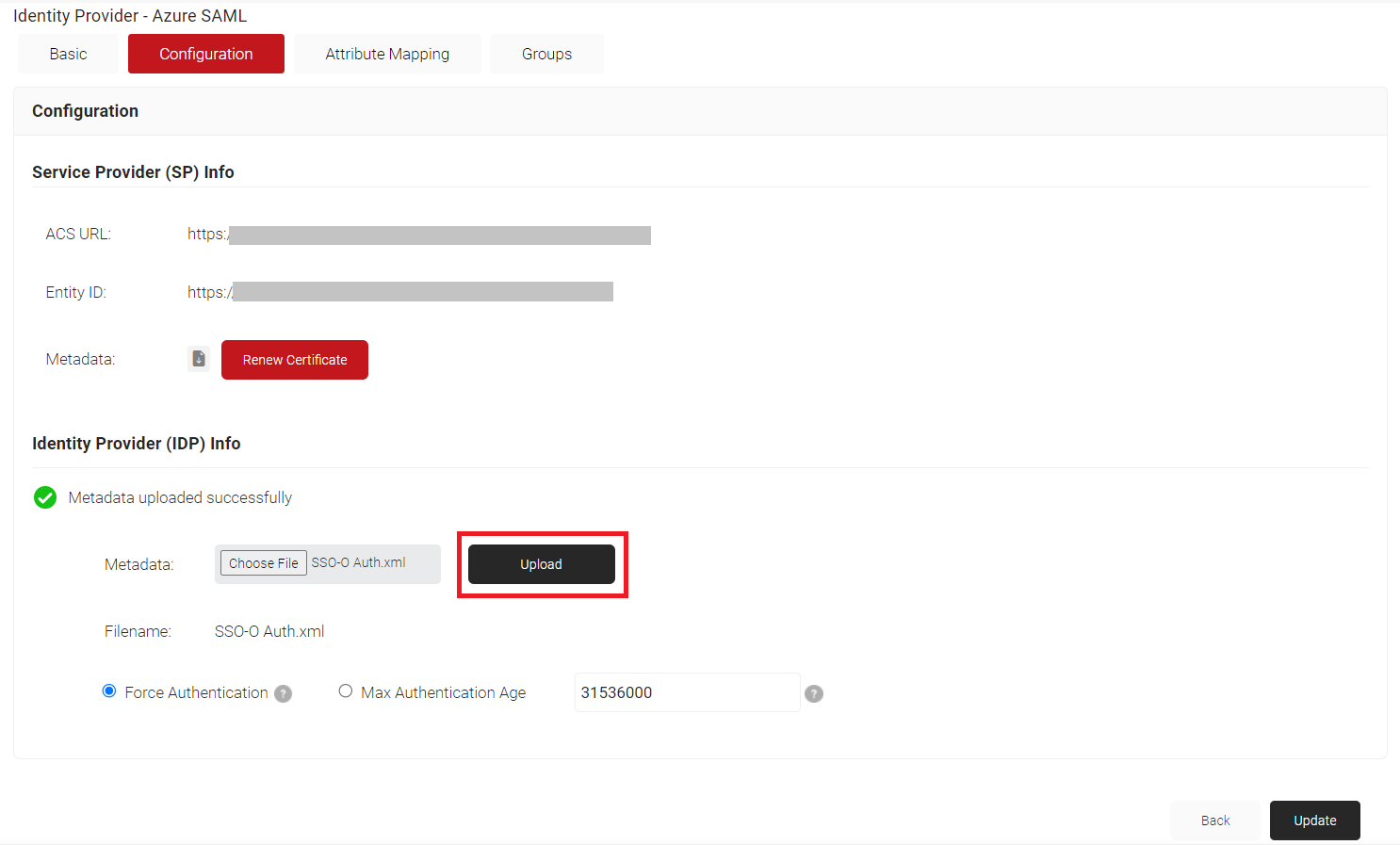
- In the JoinNow MultiOS Management Portal, go to Identity Management > Identity Providers. Click the Edit link of the newly created SAML IDP.
- Click the Configuration tab. In the Identity Provider (IDP) Info section, click Choose File to select the Metadata XML file you downloaded from Azure.
- Click Upload and then click Update.
Integrating Active Directory with the Azure SAML Application
After you’ve configured your SAML Application in Azure and SecureW2, it’s time to assign users to it. You can do this by directly assigning users, if you have them stored in Azure, or you can integrate it with your Active Directory. Below we will show you how to do both.
Add Users to the SAML Application
- From your Microsoft Azure Portal, go to the JoinNow Connector Application, or the SAML application you created in the section “Create a SAML Application in Azure”.
- Navigate to Manage > Users and groups.
- Click Add user/group.
- In the Users and groups pane, use the Select field to search for the user by name or email.
- Select the user, and then click Select.
- In the Add Assignment pane, click Assign.
- For creating group navigate to Manage > Users and groups.
- Type “Groups” in the search box and click Groups.
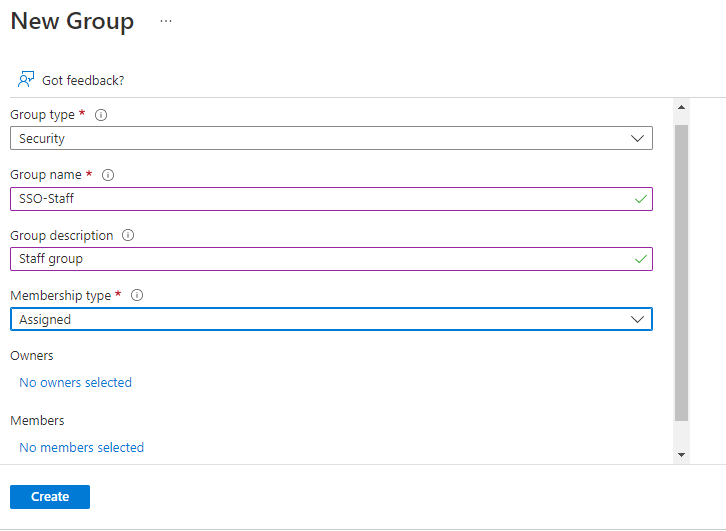
- Click + New group to add a new group. You will be directed to the following screen:
- From the Group Type drop-down list, select Security.
- In the Group name field, type a suitable name for the group.
- In the Group description field, type a description for the group.
- From Membership type drop-down, select Assigned.
- For the Members field, click No members selected.
- In the Add members window, search for one or more members. Click on desired member/members from the list and click Select. The member/members are added to the group.
- Click Create.
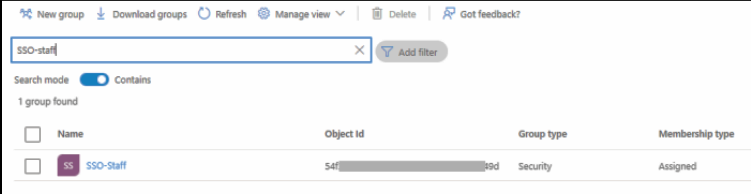
NOTE: Repeat steps 4-9 to create additional groups and add members, as required. - On the displayed screen, search for the group(s) created and copy the Object Id(s) of the group/groups to your clipboard and save it on a word/text to be used later.
Grant SAML Application Access to Active Directory
To allow your SAML application to access Active Directory:
- From your Microsoft Azure Portal, use the search feature to go to App registrations.
- Next to the search field, click the drop-down and select All apps. This displays a list of all available applications.
- Click your application.
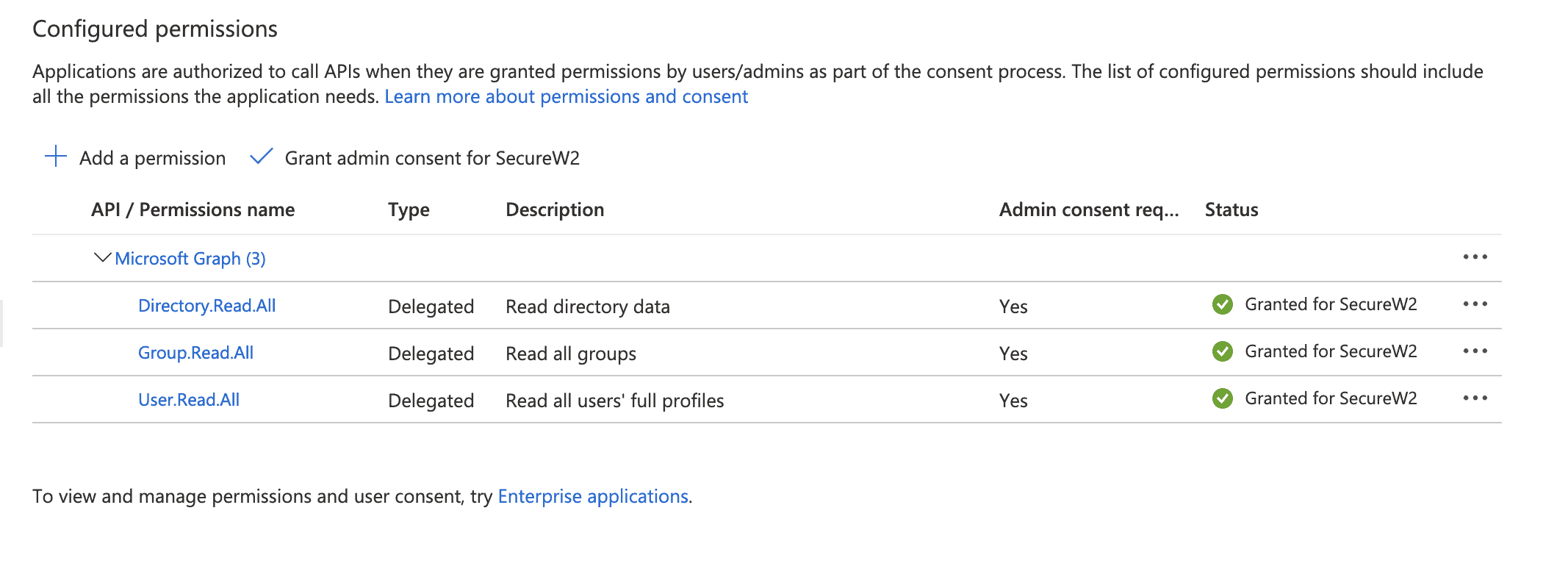
- In the pane that appears for your application, scroll under Manage and click API Permissions.
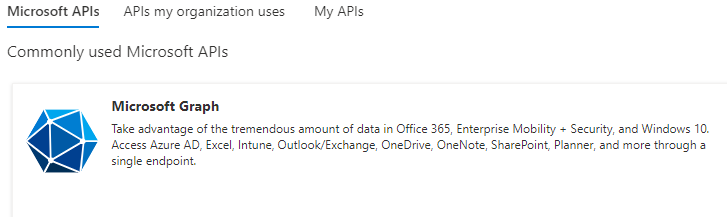
- Under Configured Permission, click Add A Permission.
- In the Request API permissions pane, select Microsoft Graph.
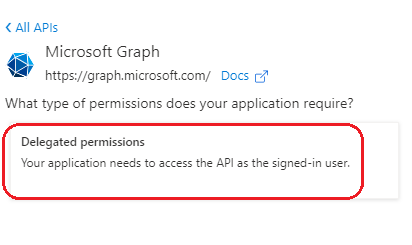
- Click Delegated Permission.
- Select the following permissions:
- Directory.Read.All
- Group.Read.All
- User.Read.All
- Click Add Permissions, the permissions will be added.
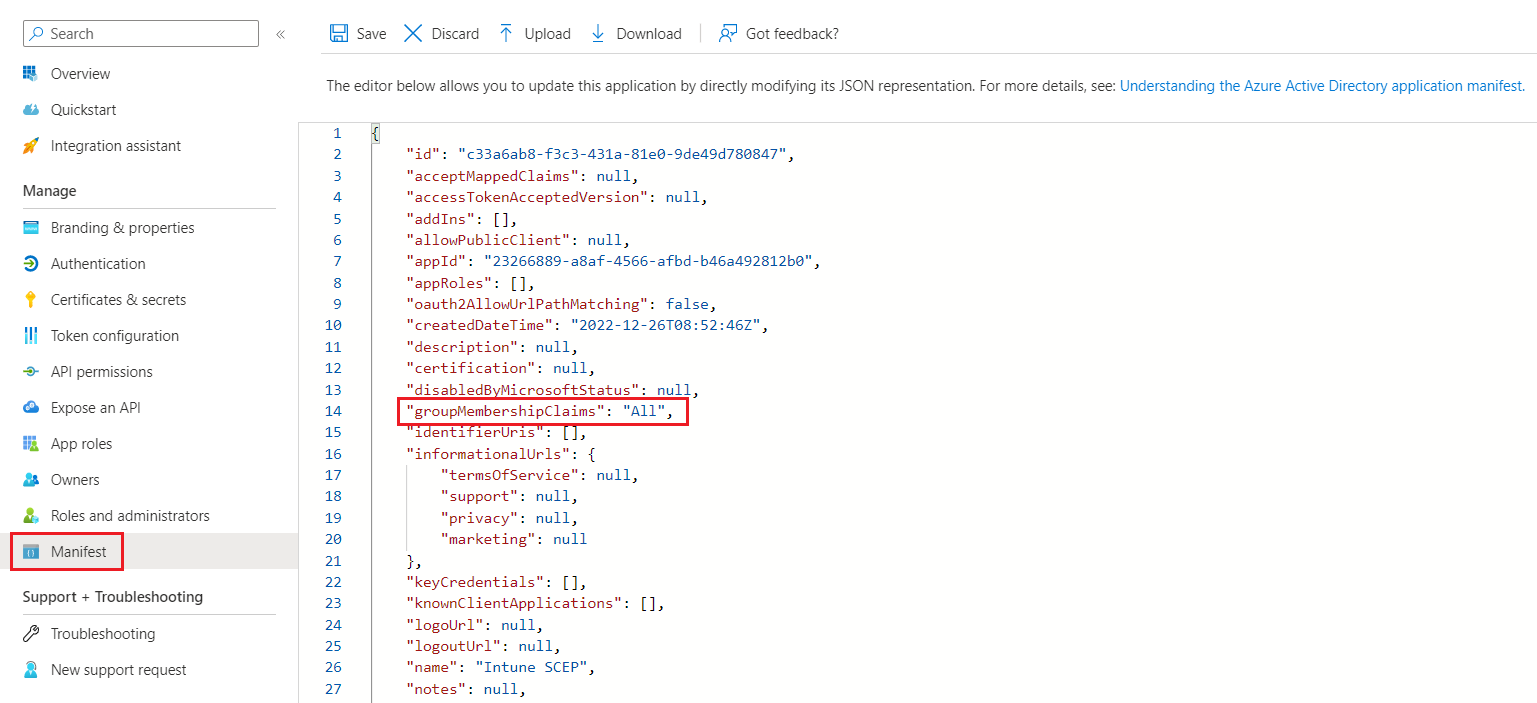
- Click Manifest.
- Change the value of the groupMembershipClaims variable to “All” in the source code.
Configure Attribute Mapping and Policies for 802.1x Certificates
Configure Attribute Mapping in SecureW2
To configure attribute mapping in SecureW2:
- From your JoinNow MultiOS Management Portal, navigate to Identity Management > Identity Providers.
- Click Edit for the IDP you created in the “Create Identity Provider in SecureW2” section.
- Click the Attribute Mapping tab.
- Click Add.
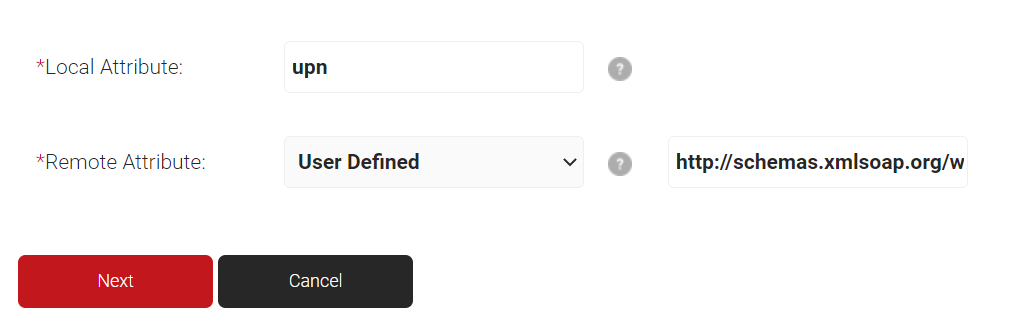
- In the Local Attribute field, enter upn as the name of the variable.
- From the Remote Attribute drop-down list, select User Defined and enter http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name in the field that appears next to the Remote Attribute field.
- Click Next.
- Click Add.
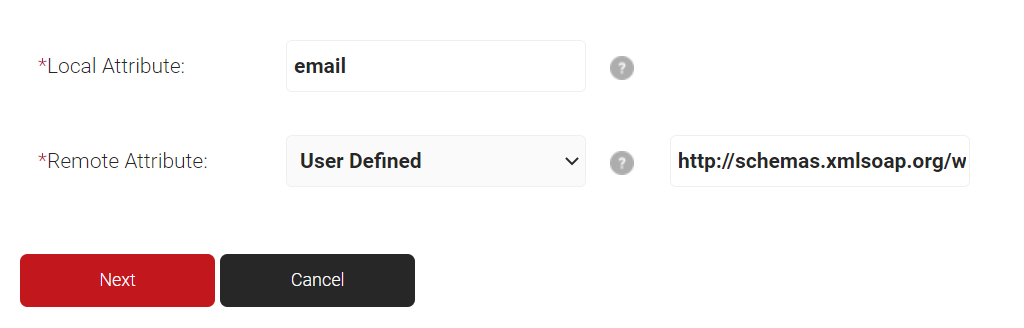
- In the Local Attribute field, enter email as the name of the variable.
- From the Remote Attribute drop-down list, select the User Defined and enter http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress in the field that appears next to the Remote Attribute field.
- Click Next.
- Click Add.
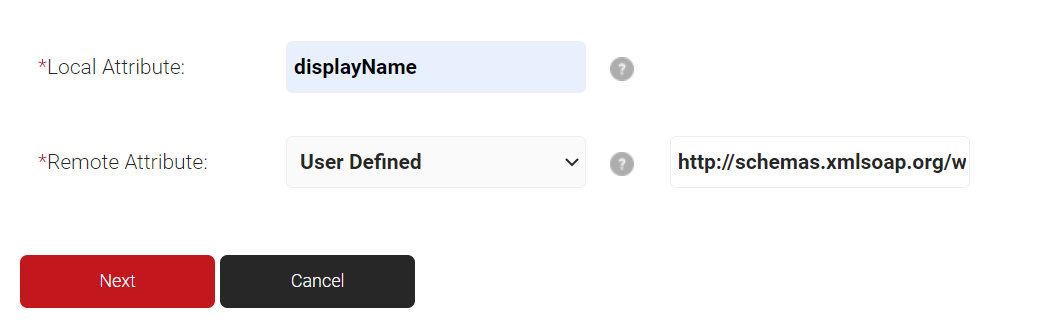
- In the Local Attribute field, enter displayName as the name of the variable.
- From the Remote Attribute drop-down list, select User Defined and enter http://schemas.microsoft.com/identity/claims/displayname in the field that appears next to the Remote Attribute field.
- Click Next.
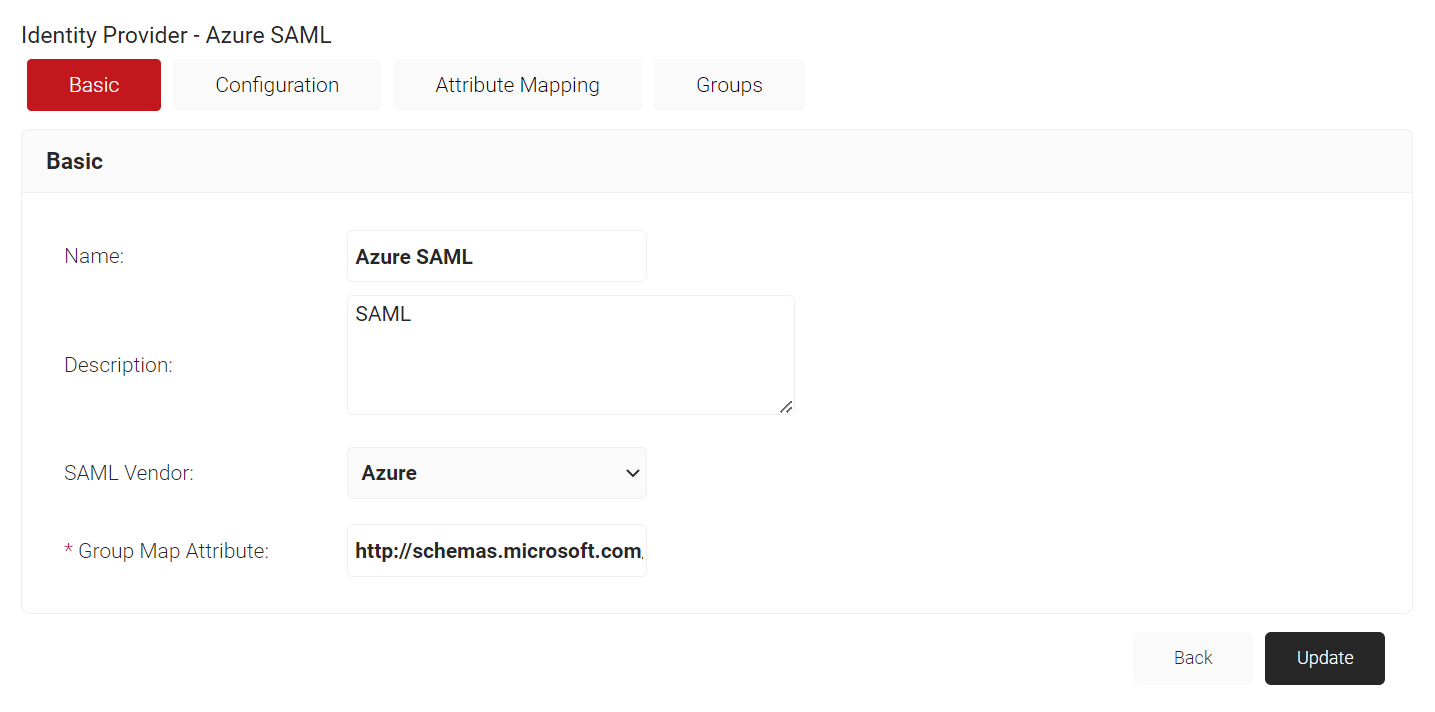
- Select the Basic tab.
- For Group Map Attribute, enter http://schemas.microsoft.com/ws/2008/06/identity/claims/groups.
- Select the Groups tab.
- Click Add.
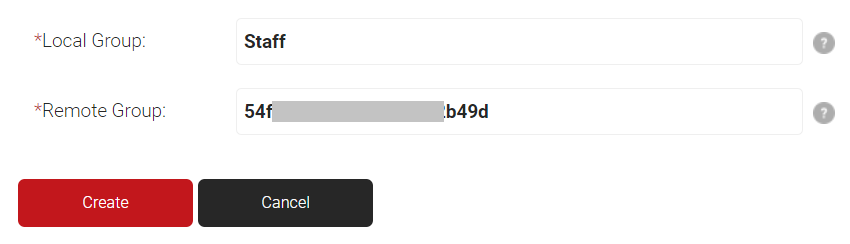
- For Local Group, enter a name.
- In a new browser tab/window, log into your Microsoft Azure Portal and go to Azure Active Directory > Groups > All groups.
- Use the Name field to search for the group.
- Click the group, and then go to Properties.
- For Object ID, copy the value.
- Return to your JoinNow MultiOS Management Portal.
- For Remote Group, paste the Object ID value.
- Click Create.
- Click Update.
Update Authentication Policy in SecureW2
To update authentication policy in SecureW2:
- From your JoinNow MultiOS Management Portal, navigate to Policy Management > Authentication Policies.
- On the Authentication Policies page, click the Edit link against your network profile’s authentication policy.
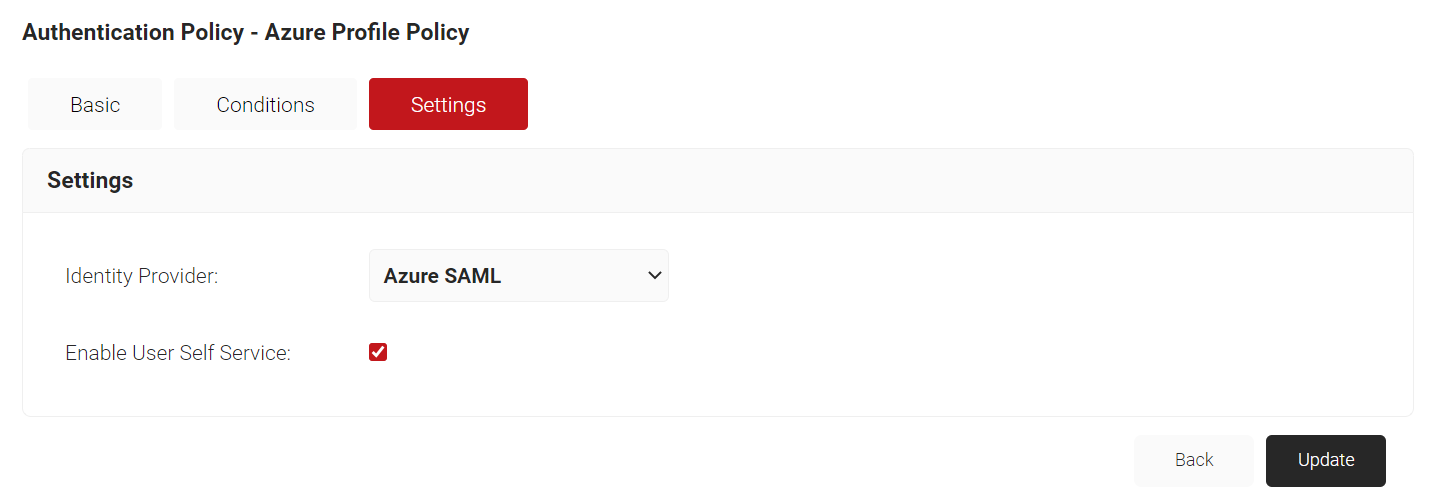
- Click the Settings tab, from the Identity Provider drop-down list, select the Identity Provider that you just created in the Create an Identity Provider in SecureW2 section.
- Check the Enable User Self Service checkbox, if required.
- Click Update.
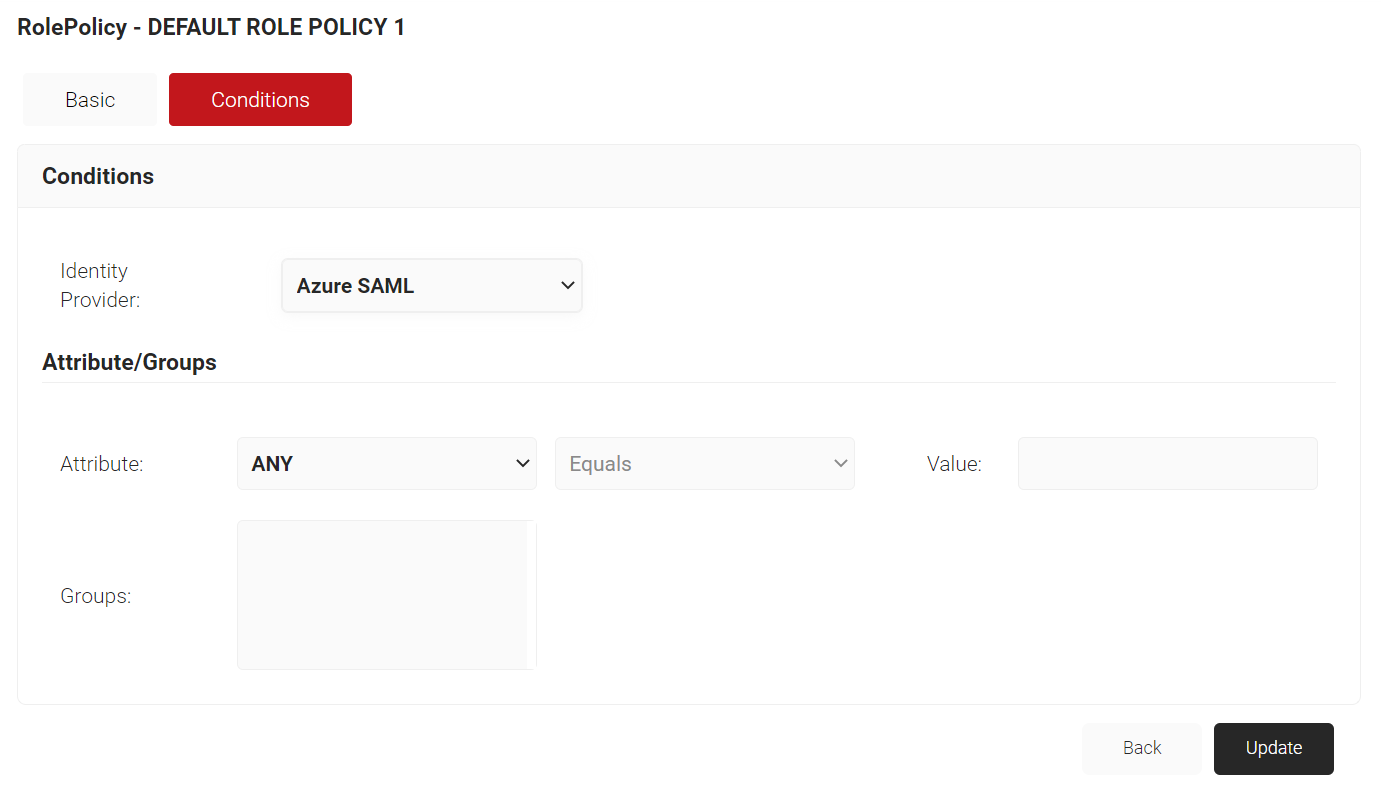
Update User Role Policy in SecureW2
To update user role policy in SecureW2:
- From your JoinNow MultiOS Management Portal, navigate to Policy Management > Roles Policies.
- For DEFAULT ROLE POLICY 1, click Edit.
- Click the Conditions tab.
- From the Identity Provider drop-down list, select the IDP you created in the Create an Identity Provider in SecureW2 section.
- Click Update.
Add User Role Policy in SecureW2
To add user role policy in SecureW2:
- Navigate to Policy Management > Roles Policies.
- Click Add Role.
- On the displayed screen, enter a Name and Description.
- Click Save. You will be directed to the Conditions tab.
- From the Identity Provider drop-down list, select the IDP you created in the Create Identity Provider in SecureW2 section.
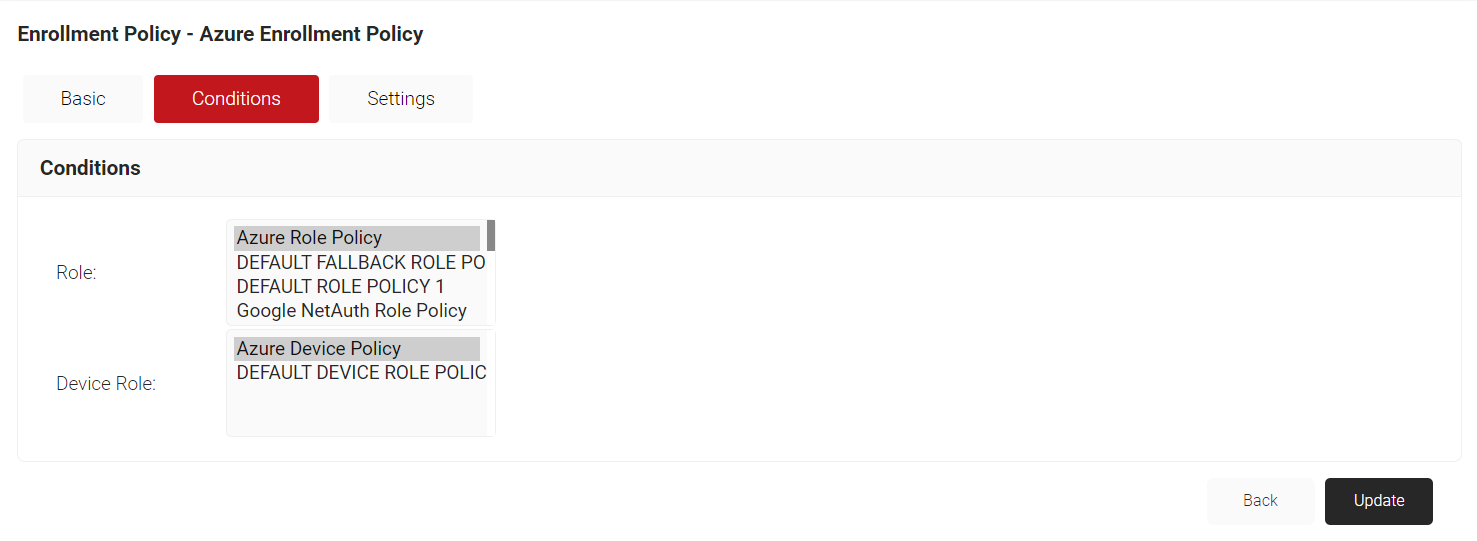
Add Enrollment Policy in SecureW2
To add an enrollment policy in SecureW2:
- Navigate to Policy Management > Enrollment Policies.
- Click Add Enrollment Policy.
- On the displayed screen, enter a Name and Description.
- Click Save. You will be directed to the Conditions tab.
- In the Conditions tab, for the User Role list, select the user role created in the previous section.
- In the Device Role list, select the DEFAULT DEVICE ROLE policy or a newly created policy according to your need.
- Click Update.
Republish Your Network Profile
To republish your network profile:
- Navigate to Device Onboarding > Network Profiles, and for the network profile click Publish or Republish if already published. This might take up to 60 to 90 seconds.
- After publishing successfully, click View.
- Click the JoinNow button. It downloads a Wi-Fi wrapper package.
- Open the downloaded file and enter your Azure credentials when the system prompts.
- The system tries to enroll and connect. Check if enrollment is successful.
NOTE: If you notice any issues with your setup, please write to support@securew2.com
FAQ's:
Why Should I Go Passwordless?
According to a Verizon report, 80% of hacking-related breaches are caused by stolen and reused credentials. Plus, you simply aren't sure who's on your network with a password as anyone can pose as a legitimate user as long as they have the right credentials.
Certificates improve user experience, identity context, and role-based access control (RBAC). You can see who owns the device, who the user is, the device’s OS, when and how the user was last authorized access, and much more. End-users won’t be disconnected from the network due to password reset policies, decreasing the amount of password-related support tickets. Certificates can be encoded with group policy attributes, making it simple for admins to implement secure RBAC practices. Cloud RADIUS can dynamically segment users based on your Azure policies at the time of authentication.
How Do I Enroll Certificates for Unmanaged or BYOD Devices?
You can enroll unmanaged and BYOD devices by setting up our JoinNow MultiOS, a small dissolvable on boarding client that can enroll users for certificates and configure 802.1X settings. Users first go to a custom landing page that detects their operating system and organization, to deploy the right client for their device. Then, users are redirected to their Azure AD login screen to validate their credentials.
Once they have been authorized by Azure AD, a certificate is enrolled on their devices from our PKI, and an 802.1X network profile is installed configuring the device for certificate-based 802.1X.
Do I Need to Manage My Own PKI?
Absolutely not! We understand that setting and managing a PKI can be frustrating work. Our PKI is turnkey and is designed to seamlessly integrate into your Azure infrastructure. No forklift upgrades are required. The best part is that you don’t even need to stick with Active Directory or LDAP.
Do I Still Need On-Premise Infrastructure for Azure AD?
Azure AD can be integrated with SecureW2, so that the entire infrastructure required for 802.1x is in the cloud. Many organizations are pushing for an all-cloud initiative, and SecureW2 enables organizations to move away from their legacy on-premise Active Directory servers to adapt to a modern Azure AD in the cloud. Moving away from on-premise AD, increases security, reduces costs, and allows a wider range of application support because Azure AD supports SAML authentication while on-premise AD requires LDAP which isn’t supported by most modern applications.
Does Azure support Certificate Signing Requests?
Deploying certificates can be difficult with Azure because it does not support Certificate Signing Requests (CSR), which is a security risk. You will either need to create your own CSR, or you can use SecureW2’s Management Portal to seamlessly integrate your CAs and get CA-approved certificates on Azure.
Can I setup a PKI with Azure?
With SecureW2, you can set up your own cloud PKI in just a few hours without needing to overhaul your entire network infrastructure. We do this by integrating a Azure AD SAML application with our PKI, so users can enter their Azure AD credentials to enroll for a certificate.
Can I Integrate AD CS with Azure AD?
Organizations wanting to switch over to cloud environments realize its unnecessary to keep or build Active Directory Certificate Services (AD CS) because it requires Active Directory. Azure is incompatible with AD CS, leaving many stuck with clunky, on-premise hardware.
Luckily, SecureW2 has a solution to configure AD CS certificates for EAP-TLS authentication. Our Management Portal can replace the AD CS backend to better manage certificates and push configuration payloads onto AD-managed devices.
Simplify Passwordless WPA2-Enterprise with Azure AD
Setting up WPA2-Enterprise with Azure is easy when you use SecureW2. Most importantly, it keeps your network and its users secure. SecureW2 is also regarded as one of the most cost effective solutions in its class. Click here to learn about our pricing.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Schedule NowPricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.
Check Pricing