Organisations all over the world trust the WPA2-Enterprise standard to make their Wi-Fi network security strong. Together, this standard and the 802.1X protocol make sure that each user has a unique set of credentials or a specialised certificate to access wireless networks. To secure your network even more, you can tie network access to policies and information from your Identity Provider (IDP), which is exactly where SAML comes in.
SAML is the foundation of single sign-on (SSO) identity, and is the protocol used by many cloud IDPs today to communicate with other systems. In an 802.1X network using certificate-based EAP-TLS for authentication, SAML provides the means interface with the IDP during the certificate enrollment phase for BYODs and confirm the identities of users. All these standards and protocols come together to build the foundation for a significantly more secure WPA2-Enterprise network.
This article goes beyond marketing to talk about setup in the real world. We break down SAML and WPA2-Enterprise properties, making the connection between theory and practice. By the end, you will understand the concepts and how to implement them effectively. Let’s look at how to use SAML for WPA2-Enterprise Authentication step by step.
Configuring Identity Provider, SAML Application, Attribute Mapping and Policies in SecureW2
- Create an Identity Provider (IDP) in SecureW2
- An IDP is required in order to connect to the database and verify the network users.
- The SecureW2 management portal allows the admin to enter key information about the IDP.
- After entering in the IDP information, the SAML information will need to be entered in to the portal.
- Create a SAML Application in SAML Provider’s Console
- The SAML application serves as the medium for end users to enter their credentials, get verified by the IDP, and start the certificate enrollment process.
- Create the SAML application by creating a custom app, then the IDP metadata can be downloaded.
- The metadata can be uploaded on the SecureW2 management portal and an ACS URL and Entityid will be created and copied into the custom app.
- Configure Attribute Mapping
- Attribute mapping allows the admins to categorize end users based on how much access is granted to them.
- These attributes can be added and adjusted on the custom app and encoded on to the certificates.
- SecureW2 can encode the attributes onto certificates in the management portal.
- Configure Policies in SecureW2
- Two policies need to be configured:
- Authentication policy – how the end user is authenticated
- User Role policy – the access that is granted to the end user
- Both of these policies can be configured in the management portal.
- Two policies need to be configured:
Creating a SAML Application for WPA2-Enterprise Authentication
SecureW2’s Device Onboarding Solution works with any Identity Provider to securely authenticate users and configure their devices to access their organization’s WPA2-Enterprise Wi-Fi network.
The SAML application works as the interfacing mechanism. When a user enters their credentials in the SecureW2 application to configure their device for Wi-Fi, SecureW2 uses the SAML Protocol to communicate with the Identity Provider. Now SecureW2 can check if a user’s credentials are valid to authenticate them for secure connection over Wi-Fi.
NOTE: Make sure that your SecureW2 account with Cloud Connector subscription is active.
To configure SAML authentication with major SAML providers and SecureW2:
- Create an Identity Provider in SecureW2
- Create a SAML Application in SAML Provider’s Console
- Configure Attribute Mapping
- Configure Policies in SecureW2
Create a SAML Identity Provider in SecureW2
Creating an IDP within SecureW2 is your first step towards constructing a smooth link between our platform and your identity provider’s user database. This critical stage allows for not only the verification of user credentials but also the issue of digital certificates, which helps to build trust and security in your authentication procedures.
An identity provider (IDP) is the system that proves the identity of a user/device. Creating an IDP in SecureW2 tells the Cloud Connector system how to connect to your provider’s user database, verify user credentials, and issue digital certificates. To create an identity provider in SecureW2:
- From your SecureW2 Management Portal, go to Identity Management > Identity Providers.
- Click Add Identity Provider.
- In the form, enter the name and description of the IDP.
- Click the Type dropdown and select SAML.
- Click the Saml Vendor dropdown and select your SAML provider.
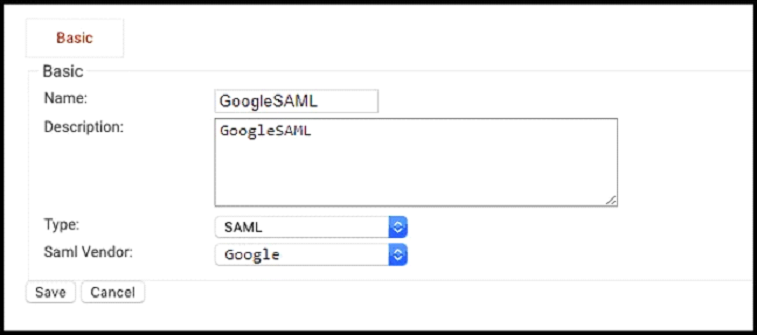
- Click Save to finish creating the IDP.
Now, SecureW2 Cloud Connector knows how to exchange information with your provider’s user database.
Create a SAML Application in SAML Provider’s Console
Your SAML application is a crucial connection between your IDP and SecureW2. Your SAML application allows a user to enter their credentials, which are then passed to your IDP for verification. Your IDP verifies the user’s identity and then sends attributes to your SAML application, which then passes the attributes to SecureW2 for certificate issuance. SAML plays a key role during certificate enrollment for BYODs; the user enters their credentials for your IDP prior to being issued a certificate, and SAML helps verify their identity in your database.
As an example, here’s how to create a SAML application in Google:
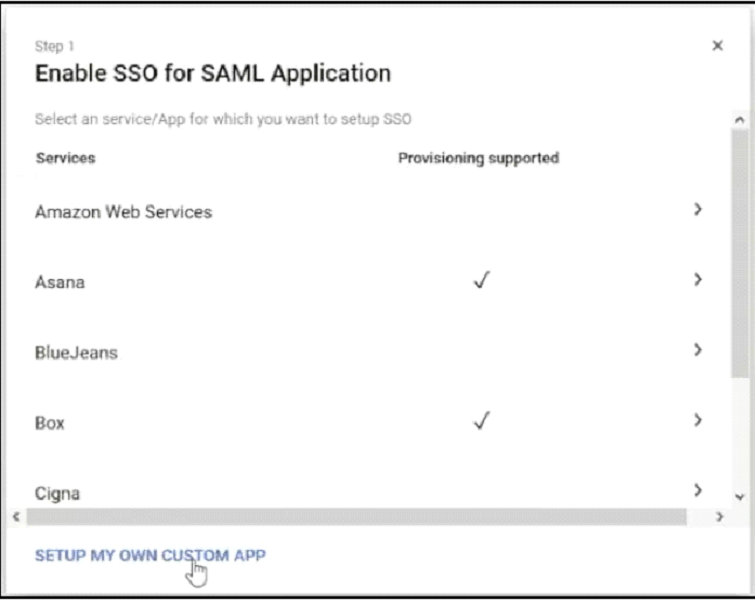
- From your Google Admin Console, click Apps, and then click SAML apps.
- At the bottom right of the screen, mouse over the yellow circle and click Enable SSO for a SAML Application.
- Click SETUP MY OWN CUSTOM APP.
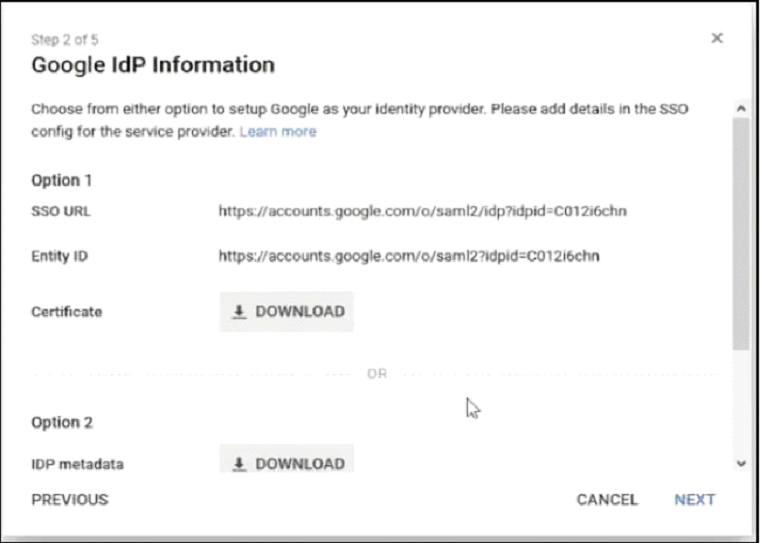
- Under Option 2, for IDP metadata, click DOWNLOAD. Save the metadata file (.XML) to your computer.
- From your SecureW2 Management Portal, go to Identity Management > Identity Providers.
- Cick Edit for the IDP you created (GoogleSAML).
- Select the Configuration tab.
- Under Identity Provider (IDP) Info, for Metadata, click Choose File.
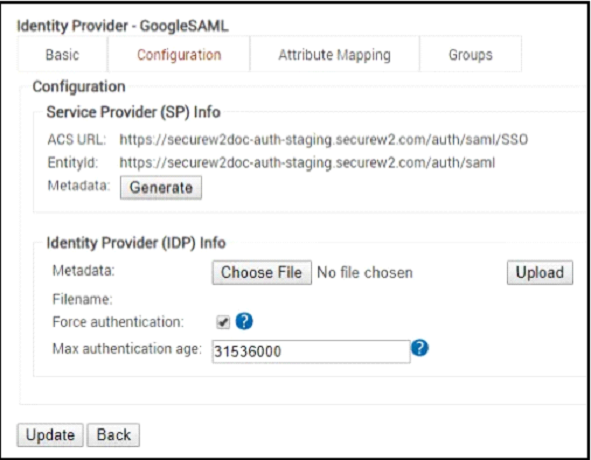
- In the prompt that appears, select the metadata file you saved to your computer. Click Upload.
- Click Update.
- Copy the ACS URL and EntityId to your clipboard or somewhere handy.
- Return to your Google SAML App setup.
- On the Basic information for your Custom App page, enter the Application Name and Description.
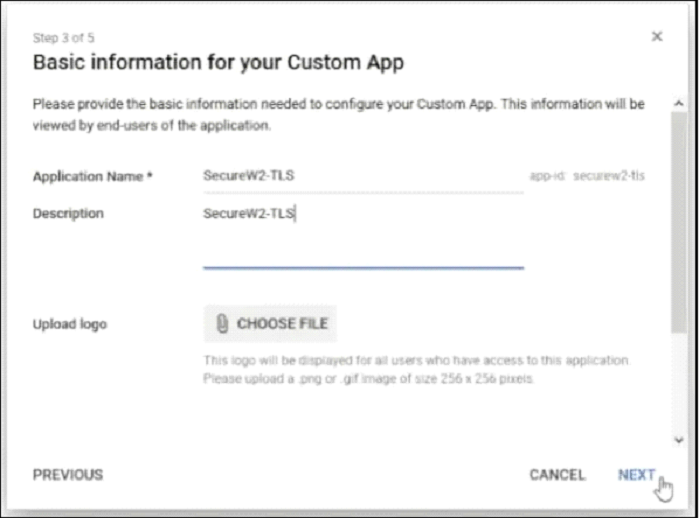
- Click Next.
- On the Service Provider Details page, paste the ACS URL and the Entity ID.
- Check the box for Signed Response, and then click Next.
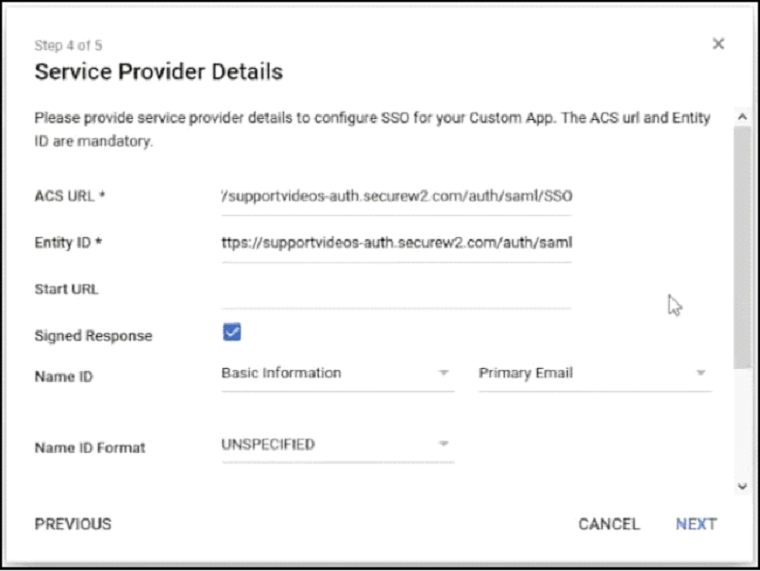
- On the Attribute Mapping page, click Finish.
Configure Attribute Mapping
Attribute mapping lays out the attributes that are returned by your IDP and used to gain access for users in an 802.1X network. Using a SAML app and IDP by University ABC in the example below demonstrates how attribute mapping may be utilized to distinguish between student and faculty users, providing them access to the relevant areas of the course assignment portal. Attribute mapping links the user’s identity, responsibilities, and the services they may access, guaranteeing a personalized and secure user experience.
Once your IDP identifies a user, it sends attributes to your SAML application, which then sends the attributes to SecureW2. SecureW2 encodes these attributes onto the certificate it issues. Attributes contain information about the user themselves, as well as which wireless network resources they can access.
Here’s an example:
University ABC employs a SAML app, which is a landing page where student and faculty users can enter their credentials to sign into the course assignment portal.
The university also employs an IDP. When authenticating users, the X attribute indicates whether the user is a student or faculty member. Student users get access to view the course assignment portal, while faculty users get access to manage assignments on the course assignment portal.
When John Doe, a student at the university, enters his credentials into the landing page, the IDP returns the X_student attribute. This attribute is encoded onto the certificate that SecureW2 assigns to John during certificate enrollment, granting him access to view the course assignment portal.
When Dana Smith, a professor at the university, enters her credentials into the landing page, the IDP returns the X_faculty attribute. This attribute is encoded onto the certificate that SecureW2 assigns to Dana, granting her access to manage assignments on the course assignment portal. To set up SAML authentication, you need to configure attribute mapping in your SAML provider’s console, as well as in SecureW2.
Configure Attribute Mapping in Your SAML Provider
Attribute mapping in your SAML provider is vital in enabling the smooth exchange of user attributes between your identity provider and SecureW2. This procedure guarantees that critical user information is safely and precisely delivered, enabling SecureW2 to incorporate these features in its certificates for EAP-TLS authentication.
To map attributes in your SAML provider (we’ll use Google as an example):
- From your Google Admin Console, scroll to Attribute Mapping and click ADD NEW MAPPING. This allows you to configure the attributes that will be encoded onto the certificate.
- For Enter the application attribute, enter ‘name’.
- Click the Select category dropdown and select Basic Information.
- Click the Select user field dropdown and select First Name.
- Click Save.
- Click ADD NEW MAPPING.
- For Enter the application attribute, enter ‘email’.
- Click the Select category dropdown and select Basic Information.
- Click the Select user field dropdown and select Primary Email.
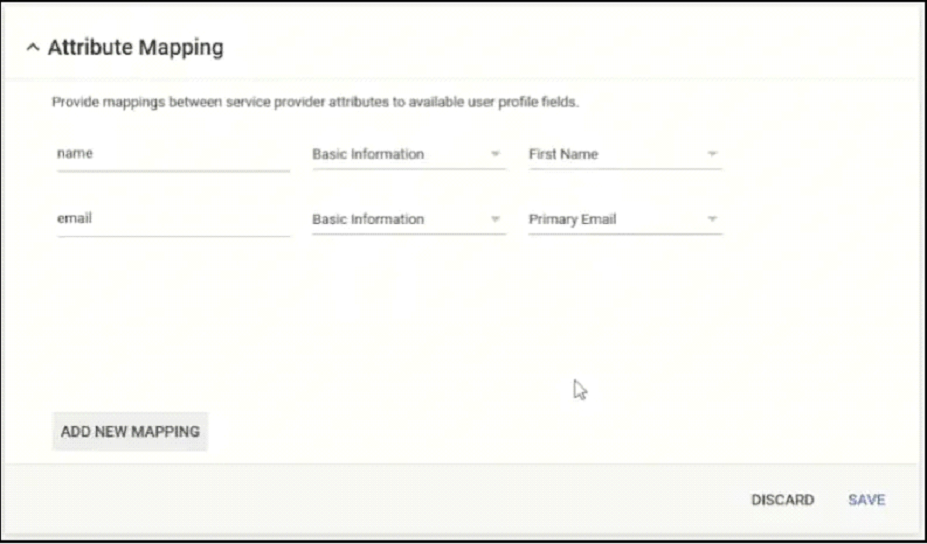
- Click SAVE.
Configure Attribute Mapping in SecureW2
Now, set SecureW2 to receive attributes from your IDP and securely encode them into certificates for policy usage. This configuration allows you to create user or device certificates with customized features suited to your needs for 802.1X network authentication and more. Follow these steps to map the attributes that SecureW2 gets from your IDP and change the certificate template to appropriately utilize these attributes.
Now you need to configure SecureW2 to receive the attributes sent from your IDP, so they can be encoded onto the certificate and used for policies. These steps will show you how to map the attributes SecureW2 receives from your IDP, and how to edit the certificate template to use these attributes.
- From your SecureW2 Management Portal, go to Identity Management > Identity Providers.
- For the IDP you created (GoogleSAML), click Edit.
- Select the Attribute Mapping tab.
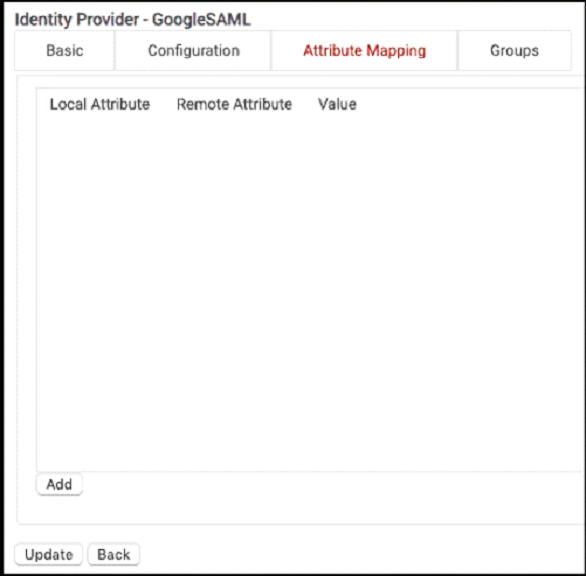
- Click Add.
- For Local Attribute, enter ‘email’ as the name of the variable.
- Click the Remote Attribute dropdown and select USER_DEFINED. Enter ‘email’ in the field that appears, and then click Next.
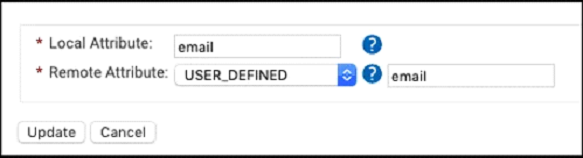
- Click Add.
- For Local Attribute, enter ‘displayName’ as the name of the variable.
- Click the Remote Attribute dropdown and select USER_DEFINED. Enter ‘name’ in the field that appears, and then click Next.

- Below the table, click Update.
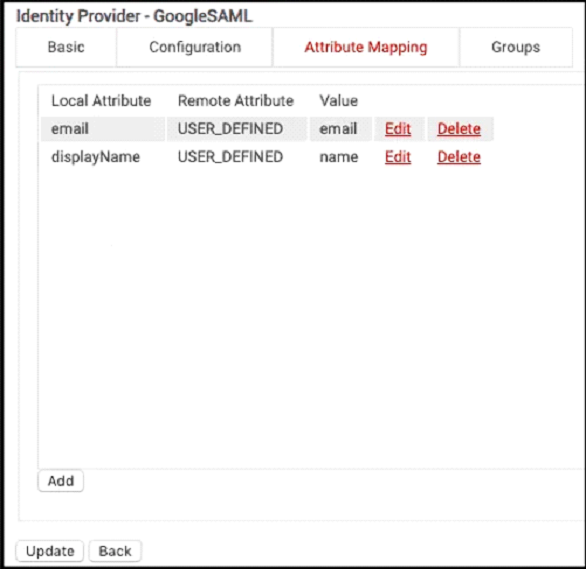
Now that you’ve configured SecureW2 to receive the attributes, you need to make sure the attributes are encoded onto the certificates that are issued to users. Here’s how:
- From your SecureW2 Management Portal, go to Public Key Infrastructure Management > Certificate Authorities.
- For DEFAULT CERTIFICATE TEMPLATE 1, click Edit.
- In the Basic section, the ‘displayName’ variable is encoded as Subject.
- In the SAN section, the ‘email’ variable is encoded as RFC822.
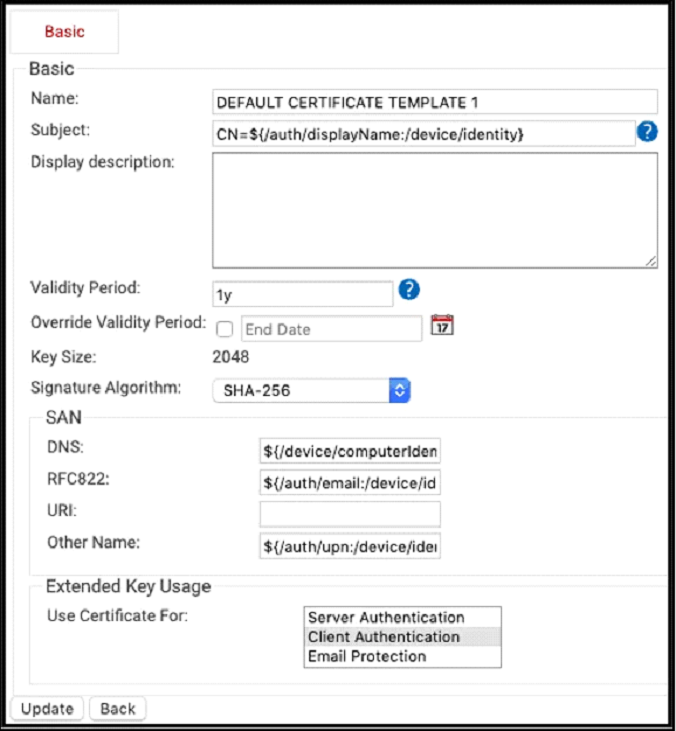
- Click Update.
The certificate template now includes the attributes and will use these attributes when certificates are issued.
Configure Policies in SecureW2
SecureW2 issues digital certificates based on the policy configuration you set up in the SecureW2 Management Portal. There are two policies that you need to configure: the Authentication policy, and the User Role policy.
To configure policies in SecureW2:
- From your SecureW2 Management Portal, go to Device Onboarding > Getting Started.
- For SSID, enter your SSID name.
- Click the Security Type dropdown and select WPA2-Enterprise.
- Click the EAP authentication Method dropdown and select EAP-Transport Layer Security.
- For the Policy dropdown, leave DEFAULT selected.
- Click Create. It takes 60-90 seconds to complete the process.
- Go to Policy Management > Authentication.
- For your network profile’s authentication policy, click Edit.
- Select the Conditions tab and make sure your wireless network profile is selected.
- Select the Settings tab and make sure the selected IDP is the one you created (GoogleSAML).
- Click Update.
- Go to Policy Management > User Roles.
- For Default Role Policy, click Edit.
- Select the Conditions tab. Click the Identity Provider dropdown and select the IDP you created (GoogleSAML).
- Click Update.
Easily Leverage SAML for Enhanced WPA2-Enterprise Authentication with SecureW2
This guide has laid out the steps you need to take to use the power of SAML and SecureW2’s advanced solutions to make WPA2-Enterprise Authentication more secure with EAP-TLS and accessible to organizations of all sizes. With this setup in place, organizations enjoy identity-rich context for each user and network connectivity, thanks to certificate-driven security and a RADIUS server for authentication.
SecureW2 is at the center of this setup. Major SAML-based Identity Providers like Azure AD, Google, and Okta work well with our Public Key Infrastructure and RADIUS. This integration makes it easy for businesses to use their current IDP rules on their Wi-Fi networks, giving them more control over who can access their networks. Also, our certificate-based authentication makes WPA2-Enterprise networks even more secure by replacing passwords with individualized certificates. With our easy-to-use onboarding tools like JoinNow MultiOS and our managed device gateways, getting Wi-Fi login certificates on all user devices is easy.
Unlock the full potential of SecureW2 and enjoy enhanced safety, speed, and user satisfaction. Contact us today for a free demo.