Microsoft Endpoint Manager (Intune) is a stellar MDM that we frequently encounter in managing managed devices, especially when the enterprise size is large, and we need to have centralized control over all the systems within the organization. Intune works really well with almost all the cloud Identity providers, especially Azure, but sometimes, managing Intune could be challenging, especially when you are dealing with 802.1x certificates.
In this case, you might look for reliable onboarding solutions that not only effectively manage your MDM but also smoothly pave the way for secure 802.1x certificates with the help of robust PKI solutions. In this article, we’ll first describe some of the decisions you need to make before configuration (especially regarding network infrastructure), as well as point out the most important options to pay attention to during the lengthy config for Enterprise Wi-Fi Profiles in Intune.
1. Choose ‘Enterprise’ as the Wi-Fi Type
Naturally, in order to configure an Enterprise Wi-Fi profile in Intune, you’ll need to select ‘Enterprise’ as the Wi-Fi type in the first setting. This prepopulates the rest of the profile configuration with settings that are necessary for Enterprise Wi-Fi Profiles. Most importantly, it confirms WPA2-Enterprise as your security protocol, requiring 802.1X authentication (and thus, a RADIUS server).
The alternative setting here is the Wi-Fi type ‘Basic’, which supports WPA-PSK and WPA2-PSK security protocols. These are both username + password forms of credential authentication, which is far too insecure to be considered for an enterprise environment.
2. Configure “Server Trust” aka Server Certificate Validation
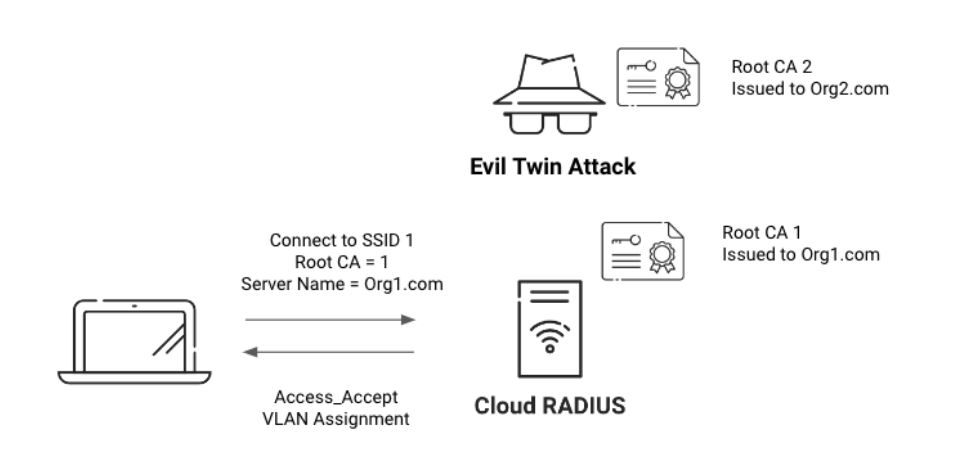
Server Certificate Validation is an optional check during RADIUS authentication in which the client device confirms the identity of the RADIUS server. To do so, the client examines the server certificate installed on the RADIUS server and verifies that it was issued by a trusted Certificate Authority. If it checks out, the client proceeds to send its authentication credentials.
Server certificate validation is arguably the most vital step in the authentication process because it prevents the majority of common over-the-air attacks, such as Man-in-the-Middle attacks. Without server certificate validation, it’s trivial for attackers to spoof a network and harvest credentials from devices that attempt to connect automatically as they come in range.
Despite being relatively simple to configure, server certificate validation is often overlooked in enterprise settings. Click here to read more about how SecureW2 can enable server certificate validation for your organization.
3. Choose Passwordless Authentication (EAP-TLS)
Another extremely significant decision when configuring a network is the authentication protocol you choose. We’ve compared authentication protocols in detail in another blog, so we’ll just cover the highlights here.
EAP-TLS is the EAP type you should choose when configuring an Enterprise Wi-Fi profile on Intune. It’s the only EAP method that doesn’t have decades-old vulnerabilities, such as PEAP-MSCHAPv2 already being cracked or the fact that EAP-TTLS/PAP sends your credentials over the air in cleartext.
However, in order to use EAP-TLS authentication, you must configure a Public Key Infrastructure (PKI) to support the creation, distribution, and revocation of X.509 digital certificates. Certificates are a form of passwordless credential that provide massive benefits to security and user experience when used for authentication in lieu of traditional username and password credentials.
Certificates are effectively impossible to crack due to the asymmetric cryptography used to generate them, which means they can be safely communicated over the air without fear of interception. Certificates are immune to credential theft and over-the-air attacks (like the Man-in-the-Middle attack).
And, unlike passwords, certificates can’t be shared, stolen, or modified. They authenticate automatically and don’t need to be remembered or reset, so they’re beloved by IT and end-users alike. Click here to read more about the benefit of using certificates for passwordless authentication.
4. Use SCEP Profiles (and Configure them Correctly)
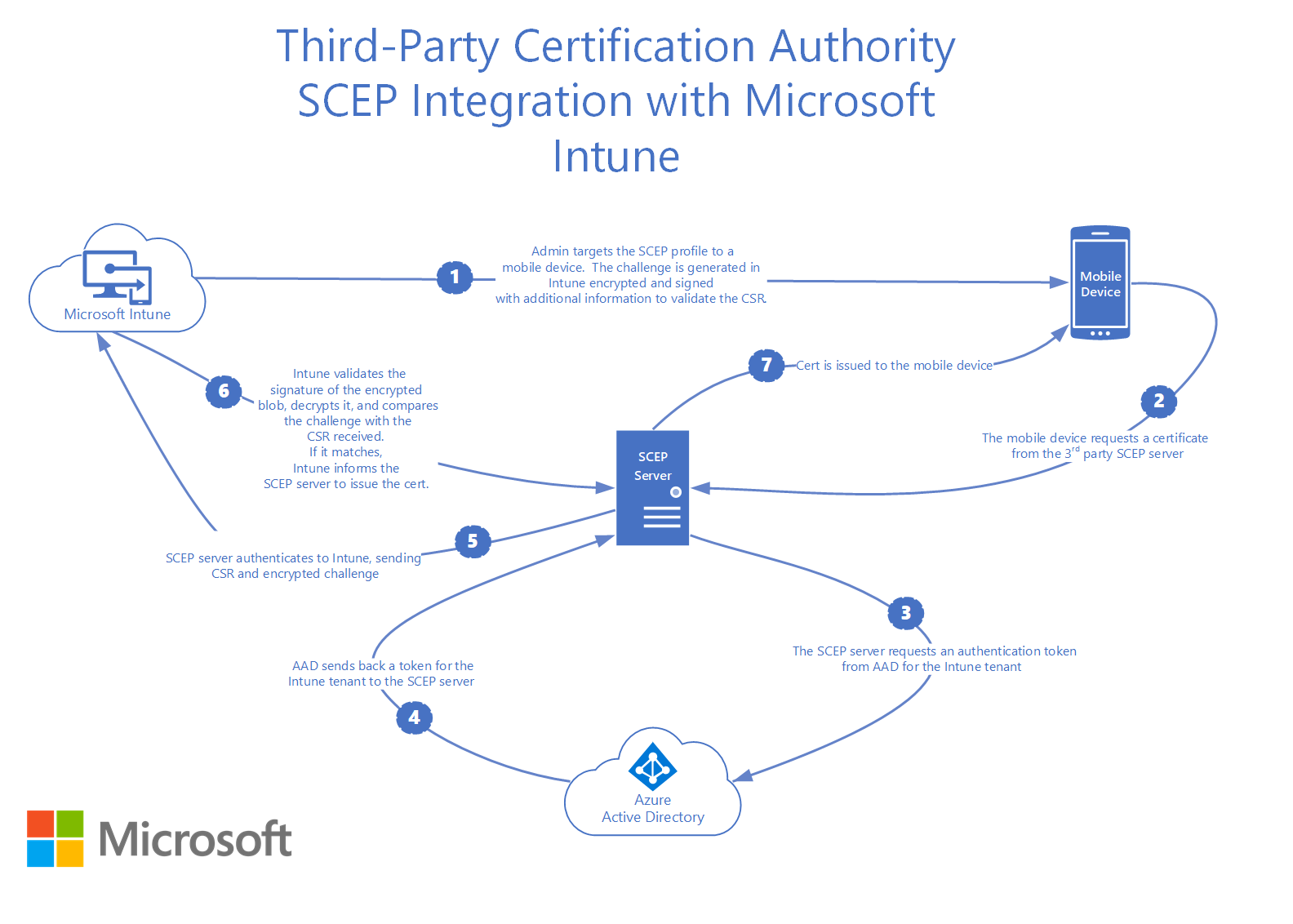
Simple Certificate Enrollment Protocol, commonly abbreviated to SCEP, is a protocol that enrolls devices for digital certificates issued by a PKI. Devices need to be properly configured before they can be issued a certificate, and a SCEP Profile contains the necessary configuration required so devices can auto-enroll themselves for certificates.
That being said, configuring SCEP Profiles is no trivial pursuit, and at the time of writing (August 3rd, 2022) there is an active bug in the way SCEP Profiles interact with Wi-Fi Profiles for iOS devices. If you don’t feel comfortable with Intune SCEP Profiles, or would just like to know some best practices, read our blog on Intune SCEP Profiles to learn what our engineers have figured out after helping hundreds of organizations configure them.
There are also a couple of different ways of implementing SCEP. Luckily, Intune supports a more secure version of SCEP, which basically enables you to do a User/Device lookup before issuing a certificate. Below highlights a diagram of how this is accomplished.
To read how to configure this more secure version of SCEP with SecureW2, click here.
To read some of Microsoft’s own documentation on configuring SCEP, click here.
5. Focus on These Wi-Fi Profile Settings
While there are over 25 configurable settings in an Enterprise Wi-Fi Profile, there is a handful that are critical to configure correctly to ensure your network security is up to snuff. Below are the 5 most important Enterprise Wi-Fi Profile settings we feel Intune (MEM) administrators should know about:
- EAP type
- Server Trust
- Certificate server names
- Root certificates for server validation
- Client Authentication
- Authentication method
- Client certificate for client authentication (Identity certificate)
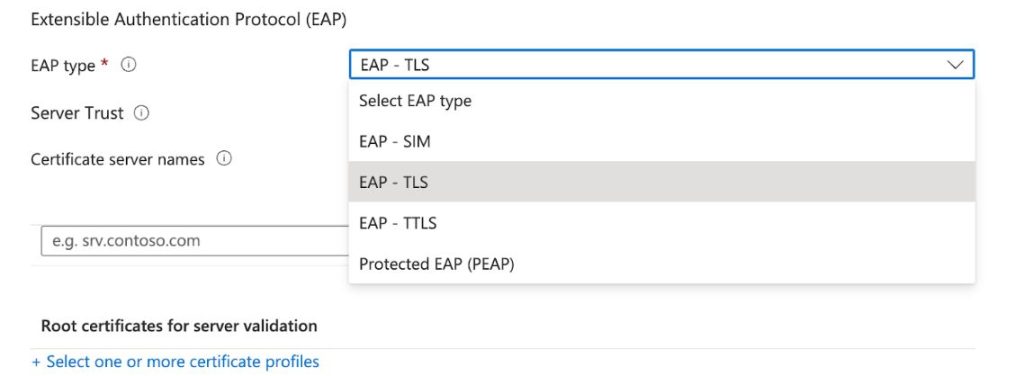
EAP Type
As we previously mentioned in Best Practice #3, EAP-TLS is far and away the most secure EAP protocol that is available. It prevents MITM and over-the-air credential theft from stealing your Azure AD (Microsoft Entra ID) credentials. Selecting EAP-TLS as the EAP type is something we recommend everyone does if they have a Public Key Infrastructure.
Server Trust
Certificate Server Names
Configuring Server Trust, aka Server Certificate Validation, is critical. It prevents devices from accidentally connecting to an Evil Twin Network. In order to tell the device the correct network to connect to, we need to tell them the domain that the Root CA of the server was issued. This is what you need to configure in Certificate Server Names.
Root Certificates for Server Validation
The second half of configuring Server Trust is specifying the Root CA that the RADIUS server should have. In order to do this, you will need to first set up a Trusted Certificate Profile in Intune. Once you have done that, you can select the profile that contains your RADIUS Server Root CA, so your device knows which server is safe to connect to.
Client Authentication
Authentication Method
For the Authentication method, nearly every organization we work with picks a SCEP certificate. We talked about SCEP a bit in Best Practices #4, but it’s basically a protocol that allows devices to securely enroll themselves for certificates without needing end-user interaction. This is the best user experience and makes EAP-TLS a much more attainable security initiative.
Client certificate for client authentication (Identity certificate)
Here you will pick a SCEP Profile. You will need to configure a SCEP Profile before configuring your Wi-Fi Profile, so it will be available to select in this setting.
All Microsoft Endpoint Manager (Intune) Enterprise Wi-Fi Profile Settings Explained!
While the above settings are the most important to configure properly from a security perspective, Wi-Fi profiles allow an awesome amount of customization, and we very regularly help set up the other settings for many organizations.
We interviewed our top Network Engineers who work with Intune on a daily basis to summarize what each Enterprise Wi-Fi Profile setting means from a practical perspective. We hope you find this useful, and if you have any questions at all, please feel free to contact us for help.
Enterprise Wi-Fi Profile Settings for Windows Devices:
Wi-Fi Type: In this field, We can select different Wi-Fi profiles, and for organizational purposes, here we have to select Enterprise. Selecting Basic will just create some small settings for WPA2-PSK.
Network Name: In a Windows device, the Wireless Profile will get exported, and we will receive output in XML format. After the XML gets exported, we will get both the SSID Name and the Connection Name. So we need to enter the reference name for the network. In Microsoft End Point Manager, enter the name of Wi-Fi Name and Connection Name as the same to get SSID.
Connect Automatically when in the range: Whenever the device gets active, Select Yes for enable to connect to this network. It should always be select Yes as an option, because it is first preferred network for managing devices by an MDM. If we select No, the other SSID will take place the role, and we will not take full advantage of the MDM setting
Connect to a more preferred network, If available: If we select Yes as an option, We can create a profile with the idea of the highest preferred MDM. But in the MDM settings, we don’t have a situation to select Yes Unless It has more than one SSID. So, Instead of Yes, we can choose No as an option.
Connect to this network, even when it is not broadcasted its SSID: Based on the device perspective, if the network is not broadcasted to SSID, we can instruct the device to make an attempt on SSID.
Here we should select Yes because it will make a device overwork and also not try to connect any other available SSID. So Instead of Yes, we have to select the Option as No.
Metered Connection Limit: It is a measure of bandwidth that allows to connect the network eventually while connecting to the SSID. This option is needed for the simultaneous configuration on the server to allow the network.
- Unrestricted: It helps to allow the app or service to use all data on the Wi-Fi.
- Fixed: It will allow only a few selected lists of data.
- Variable: This option can be used when the device is in a critical stage.
Authentication Mode: The Authentication mode is a widely used authentication where we can fix user or machine authentication as a default option.
Remember credentials at each logon: This field helps save the user credentials and will use the same credentials for the Wi-Fi Authentication. Here we have to select the Enable option for this field. It will be applicable for PEP Authentication and Credential Based Authentication.
So whenever the user gets login, their SSID credentials automatically get saved. The user can log in with the same SSID credentials frequently with the help of the Single Sign-On option.
Authentication Period: It is a number of seconds for the client to wait after an authentication attempt before failing.
Authentication Retry delay period: The Client user sends the authentication request, and during the request, if the authentication fails, it can be considered in two ways, either from the Client side or the Controller side. The client can able to retry the authentication for a maximum of three attempts which are provided by the controller. If the client tries to reattempt for the fourth time, he will be blacklisted, and the credentials can be considered invalid.
Start Period: It is the EAPOL start message. The Client can click the SSID and as soon as it convey the information to the Controller that the client is trying to do the E-Connection work.
Maximum EAPOL start: The BYOD and SSID get combines and configured along with 802.1 X Authentication. After configuration, the client would get aware of 802.1 x, and he will receive the EAPOL (Extensible Authentication Protocol over LAN) start message.
Minimum Authentication Failure: The client would type the User-ID and Password for authentication, if the radius rejects the credentials, the client can try Maximum attempts to authenticate their device. After accepting the failure, the client cannot receive the E-Transaction for a certain amount of time.
Single Sign-On (SSO): Single Sign-On is a domain joined devices where the user needs to use the Wi-Fi authentication credentials.
Allow Windows to prompt user for additional authentication credentials: The user has to enter the credentials and select Connect. After Connecting the SSID, the user receives another prompt information.
Fast Roaming Settings: When the client uses the 802.1 X, the encryption between the client and SSID becomes unique, and the decryptions will happen individually based on the profiles. When enabling the fast roaming, the client gets moves from SSID A to SSID B, and we have to reset the PMK(Pairwise Master Key) values. Also, the decryption between the SSID-A and SSID-B would happen much quicker.
Enable Pair-Wise Master Key(PMK) caching: Pairwise Master Key is a key that generates PTK for unique cast and GTK for Multicast.
Maximum time a PMK is stored in cache: It helps to maintain a certain amount of time (5-1440 minutes) to store the PMK.
Maximum number a PMK is stored in cache: It can store a certain number of PMK entries within 1- 225 entries.
Enable Pre-Authentication: Pre-Authentication can help to allow the profile to authenticate all access point in the profile before getting connected to the network.
- Select Yes to authenticate all access points in the profile.
- Select No to authenticate a required number of users or device access points.
Maximum Pre-Authentication Attempts: Enter the number of tries from 1-16 attempts.
Extensible Authentication Protocol: Extensible Authentication Protocol is a type of settings that protocol can be used to authenticate directly.
EAP Type: Select EAP-TLS from the drop-down list.
Certificate Server Names: Enter one or more relevant names issued certifications by the trusted certificate authority.
Root Certificate for server validation: Select the trusted root certificate profile that can help authenticate the network connection. It is applicable only to the radius server root CA.
Authentication Method: The client user need to select the relevant authentication method.
- SCEP Certificate: The user must select the SCEP client certificate profile that can be deployed to the device. The device can grant the certificate to the server that gets authenticated to the network connection.
Company Proxy Settings: The Company proxy settings will work after the authentication.
Force Wi-Fi profile to be compliant with the federal information processing standard (FIPS): Select Yes to prove compliance to the FIPS 140-2 standard. It is required to use cryptography-based security systems to protect digital sensitive information. Select No for Non-FIPS compliance.
After the Wi-Fi Settings get configured, Click OK and Click Create. The profile will get created and displayed in the profiles list.
Enterprise Wi-Fi Profile Settings for Android Devices:
Wi-Fi Type: In this field, We can select different Wi-Fi profiles for an organization’s purpose, Select Enterprise.
Network Name: Here, we need to enter the reference name for the network. In the Microsoft End Point Manager, enter the Wi-Fi Name and Connection Name as the same to get SSID.
Connect Automatically: Whenever the device gets active, Select Yes to enable it to connect to this network. Select the No to Disable option to safeguard the devices from automatically connecting to the network.
Hidden Network: Select enable from the available network lists on the device to hide the network. The SSID cannot be broadcasted. To show the network, select disable from the available network list.
EAP Type: Select EAP-TLS from the drop-down list.
Certificate Server Names: Enter one or more relevant names issued certifications by the trusted certificate authority.
Root Certificate for server validation: Select the trusted root certificate profile that can help authenticate the network connection. It is applicable only to the radius server root CA.
After the Wi-Fi Settings get configured, Click OK and Click Create. The profile will get created and displayed in the profiles list.
Enterprise Wi-Fi Profile Settings for iOS and macOS:
Wi-Fi Type: In this field, we can select different Wi-Fi profiles For an organization purpose, select Enterprise.
Network Name: Here, we need to enter the reference name for the network. In Microsoft Endpoint Manager, enter the Wi-Fi Name and Connection Name as the same to get SSID.
Connect Automatically: Whenever the device gets active, Select Yes to enable it to connect to this network. Select the No to Disable option to safeguard the devices from automatically connecting to the network.
Hidden Network: Select enable from the available network lists on the device to hide the network. The SSID cannot be broadcasted. To show the network, select disable from the available network list.
EAP Type: Select EAP-TLS from the drop-down list.
Certificate Server Names: Enter one or more relevant names issued certifications by the trusted certificate authority.
Root Certificate for server validation: Select the trusted root certificate profile that can help authenticate the network connection. It is applicable only to the radius server root CA.
Proxy Settings:
- None: Proxy settings are not get configured.
- Manual: Enter the proxy server address and its port number as an IP address.
- Automatic: Enter the proxy server URL that can configure the file automatically.
Disable MAC address randomization: When the user connects to the network, the devices can present a randomized MAC address that is instead of the physical MAC address. The randomized MAC address can help to provide better security, and it is recommended to maintain privacy.
After the Wi-Fi Settings get configured, Click OK and Click Create. The profile will be created and displayed in the profiles list.
Enable Passwordless Authentication for Intune Enterprise Wi-Fi Profiles
Ultimately, the single most important security best practice you can implement for Microsoft Endpoint Manager (Intune) is to use digital certificates for authentication rather than credentials. When you install certificates on managed devices and enable passwordless auth, you gain a number of benefits that are unavailable with credential-based authentication, such as eliminating the need for password reset policies (or remembering your password at all) and immunity to over-the-air attacks, credential theft, and phishing and so on.
SecureW2 has helped dozens of organizations of all shapes and sizes to enhance their Intune experience. In addition to our SCEP gateway APIs that help enroll all of your Intune-managed devices for certificates, we also have an industry-unique feature that enables the auto-revocation of expired certificates in Intune.
Let our experts help with your enterprise MEM Intune deployment, and rest assured that your organization is protected by best-in-class authentication security. Click here to see our pricing.