Wi-Fi security and availability is imperative for businesses now that online communication is the standard. Many organizations use passwords to authenticate user devices, but that is no longer a viable option as cyber attacks can easily bypass passwords. This has led many organizations to invest in PKI technology to harden their networks with certificate-based authentication.
This has led many organizations to invest in PKI solutions to harden their networks with certificate-based authentication. Cloud Managed PKIs, like SecureW2, outrank on-premise PKIs like AD CS, because they are more scalable and come at a third of the cost. Plus, they are simple to implement if you choose the right PKI solution.
In this article we will discuss what a PKI is, how it works with Wi-Fi, and how you can use it to improve your Wi-Fi Security.
What is a PKI?
Passwords can be lost, stolen, forgotten, and shared around, making any credential-based network vulnerable to over-the-air credential theft. Certificates provide a more secure form of network authentication than passwords because they are encrypted and locked onto devices. With certificates, admins can easily configure devices for 802.1x authentication, which is a common issue as many industry providers don’t natively support it. Public Key Infrastructures (PKI) serve as the foundation for admins to build a certificate-based network.
The definition for a PKI varies between security professionals, but the general consensus is that a PKI is a handful of components that give everything an organization needs to issue, revoke and manage X.509 Digital Certificates. A PKI can be used with a variety of applications (Wi-Fi, VPN, Web Apps, E-Mail) to replace insecure credential-based authentication and securely encrypt the transmission of data.

How Does a PKI Work with Wi-Fi?
At a high level, a PKI works with Wi-Fi by replacing credential-based Wi-Fi authentication with certificate-based authentication. Rather than sending credentials over the air every time users need to authenticate to the network, they are used only once for certificate enrollment and never put at risk for credential theft again.
Wi-Fi authentication is also enhanced through the use of digital certificates because every network connection can be tied back to a user.One of the core functions of a PKI is to encrypt network communications between servers and clients, ensuring only approved users and servers are granted network access, which the easily and often shared credentials fail to do.
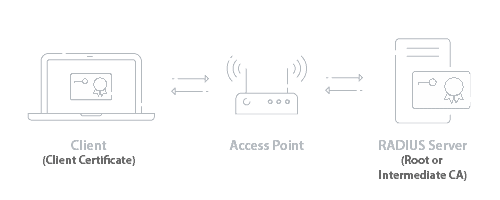
Using a PKI for Wi-Fi authentication requires using the 802.1x standard for network access. There are several protocols within the 802.1x standard. Certificates-based networks enjoy the most secure protocol of 802.1x authentication with EAP-TLS. 802.1x networks possess superior security measures because they have RADIUS servers. RADIUS servers are the bouncers of the network PKI system. Their purpose is to check a device’s client certificate, check the private key against the CA’s public key, credentials and determine if it belongs to’s an active user and grant it network access based on network policies in place.
Certificate Authorities (CA) serve as the central authority for a PKI environment, thus the name. CAs handle all aspects of certificate management, including generating, issuing, and revoking certificates. With PKIs, users and systems are better able to verify the legitimacy of other entities by checking if they have a certificate. PKIs run on a public-private key pairings: a user device generates a public-private key and sends their public key and attributes to the CA. The CA generates a certificate containing the public key and attributes, ultimately signing the certificate with the private key and sending it back to the device, granting it network access.
One of the ways PKIs let the RADIUS server know that a certificate isn’t allowed on the network is through Certificate Revocation Lists (CRL) that are updated by the CA and routinely checked by the RADIUS server. The CRLs contain all the certificates that have been revoked, and are part of the Certificate Authority. In a way, a CRL is the “Do Not Serve” list for a PKI. If a certificate is revoked before expiration, it will show up on the CRL. Everytime a user authenticates against the RADIUS server, it checks the serial number of the client certificate to see if it’s on the CRL as a safety measure.
The end user will never see any of this, and probably never know it’s all going on. Once a device is equipped with a certificate, the device for the most part will just connect. No more password resets, or disconnects, it will just connect. Any end user device not equipped with a certificate will be denied network access. Any server not equipped with a certificate will be ignored by end user devices.

Configuring a PKI for Wi-Fi
In order to configure a PKI for Wi-Fi authentication, you will obviously need a PKI setup. There are a couple options for implementing a PKI: on-premise PKI or Managed PKI.
On-premise PKIs are common because many environments operate with an infrastructure that is designed for an on-premise connection. This is fairly common for Windows environments that run on Active Directory. In this instance, an on-prem PKI would make sense.
However, on-prem PKIs are not a good choice because organizations have to dedicate a massive amount of resources to implement and maintain. Organizations have to pay for training or hiring PKI admins, licensing fees, hardware and software, backup, secure storage, and much more. The IT department will have to set up the entire infrastructure, which can take weeks and eats up company time. Overall, deploying an on-premise PKI means more money spent by the enterprise and an intensified workload for IT admins.
Managed Cloud PKIs are the better option because they do not require any additional hardware to set up, can be implemented in much less time, and is a fraction of an on-prem PKI cost. Since it’s in the cloud, admins can benefit from the versatility of cloud computing services. In fact, we offer a Cloud RADIUS server that comes with our Managed PKI.
Building a PKI from scratch is a grueling task, so instead of that, go with SecureW2’s Managed Cloud PKI that streamlines the implementation process. Below we’ve laid out just how easy it is to deploy a PKI for your network.
Use Our Getting Started Wizard
SecureW2’s PKI services are completely turnkey because all the necessary tools for PKI implementation are set up through our Getting Started wizard. This easy-to-use wizard will set up a Root and Intermediate CA, Base and Delta CRL, RADIUS Server, Network Policies and everything else you need to use a PKI for Wi-FI.
Integrating your Identity Provider with the PKI
SecureW2’s service allows admins to integrate their SAML or LDAP Identity Provider (IDP) in SecureW2’s Management Portal. Now the SecureW2 certificate enrollment clients will use the IDP as a Single-Sign On for certificate enrollment, ensuring only members of the organization are issued certificates.
Here are some links on integrating popular IDPs with SecureW2’s PKI:
PKI + RADIUS Server Integration
Integrating a PKI with a RADIUS server for Wi-Fi authentication requires three things. One is importing the Root and Intermediate CA’s on the RADIUS server. This is already setup on SecureW2’s Cloud RADIUS but must be done with other vendors. You also need to configure your devices for Server Certificate Validation, so they only connect to RADIUS servers that have certificates authorized to your domain. This requires onboarding software, which isn’t offered by all RADIUS server providers, but is included in our RADIUS and PKI licenses for free for this reason. Lastly, they can be configured for Identity Lookup, so that they check the users status in the directory before allowing them network access.
PKI + Access Point Integration
The PKI and the APs don’t actually talk to each other. All that needs to be done here is to create a secure SSID that authenticates via WPA2-Enterprise / 802.1x, and enter in the RADIUS’s IP address and shared secret in the SSID settings.
Configuring Devices for PKI Wi-Fi
In order to configure devices to use certificate-based authentication, two things need to happen. They need to enroll for a certificate, and they need to configure their devices for EAP-TLS 802.1x network authentication using their certificate. Both are no trivial tasks, which is why we create the JoinNow solution.
SecureW2’s JoinNow solution makes it easy for admins to onboard BYODs through our self-service onboarding clients that make it easy to enroll for certificates and 802.1x network access, and our simple certificate auto-enrollment Gateway APIs for managed devices that silently enroll every device for unique client certificates.

The JoinNow solution uses a landing page that any device on the market, deploy a dissolvable client that uses any IdP for SSO certificate enrollment, and then configures the device for network access using the certificate.
SecureW2 gives admins the ability to build Gateway APIs to send out payloads via Mobile Device Management Software so that organizations can configure every managed device for certificate auto-enrollment and secure 802.1x authentication.
Instead of wasting time manually configuring every single device or leaving it up to the end user, admins are able to issue a certificate to every BYOD and managed device. Plus, SecureW2’s Management Portal gives admins full visibility into the certificate enrollment process for great security and efficient troubleshooting.
PKI Wi-Fi Certificate Management
Once the certificate enrollment process is complete and the end device is able to access Wi-Fi, the next part is managing issued certificates. There are three key features admin benefit from by using SecureW2’s Managed Cloud PKI: CRLs, Identity Lookup, and an advanced certificate management GUI.
CRLs allow the RADIUS server to verify active network users. The two types of CRLs are Base and Delta and the difference lies in how often they update. The Base CRL is the standard list, it’s only referred to as Base when the Delta CRL is used.
Base CRLs can take a long time to update, slowing down the authentication process. Admins can configure Delta CRLs which contain all revoked certificates since the last Base CRL update. Since Delta CRLs are much shorter, RADIUS servers can be configured to authenticate against them instead. Admins can even adjust Delta CRL update intervals in the SecureW2 Management Portal.
Identity Lookup makes it easy for admins to search for specific certificates and identify end users. Identity Lookup verifies that an end user is still active by checking if their information is in the IDP. It used to be that only LDAP providers could use Identity Lookup, but SecureW2 expanded it to include SAML providers as well.
Our easy-to-use Certificate Management GUI simplifies all certificate management functions, and is much better than the logs of back in the day. Our GUI has loads of features like automated email notifications when a certificate is about to expire, custom certificate templates, manual revocation, and much more. Having a GUI also makes it straightforward for the Help Desk because all the attributes (MAC address, common name, computer model) are easily searchable.

Secure Wi-Fi and 802.1x Authentication with SecureW2’s Managed Cloud PKI
If your organization runs on password-based authentication, it’s time to switch over to certificates because passwords no longer cut it for Wi-Fi security. PKIs provide the most secure form of Wi-Fi authentication because admins can distribute certificates to every network device. Both BYODs and managed devices can be equipped with a certificate and configured for 802.1x with our onboarding software and gateway APIs.
If you’re thinking about deploying a PKI, avoid the on-prem option which is expensive and labor-intensive. Instead choose SecureW2’s Managed PKI that is completely turnkey, can integrate with any provider, and is much more affordable.



