Easy Certificate-Driven Security with Our Managed Cloud Private CA Service
You don’t need to invest hundreds of hours or tens of thousands of dollars on building your own Public Key Infrastructure (PKI). We provide everything you need to deploy your own cloud private certificate authority in less than an hour. Manage all steps of the certificate lifecycle, from issuance to revocation, from one pane of glass.
Secure Critical Business Resources with Certificates
Certificates deliver so much more identity context to each connection and can be used for a variety of purposes. In one convenient centralized location, our managed cloud PKI solution allows you to create certificates for these types of extended key usage (EKUs):
A Cloud Private Certificate Authority Service that Integrates with Your Environment
In the past, PKIs have been challenging to set up, but the good news is that’s just the past. Our PKI as a service solution brings the best of modern certificate management tools to your cloud environment, automating certificate enrollment and revocation based on real-time data from your Cloud Identity.
- Search for users/devices and easily view all their certificate lifecycles and authentication events in one place for easy troubleshooting and management
- Simple and secure, backed by HSM (Hardware Security)
- Integrate with ease to nearly every device management system or with BYODs/unmanaged devices
- Automate certificate enrollment and revocation to all your managed devices through our API
- Total cost of ownership (TCO) is less than a third of comparable on-premise Active Directory Certificate Services (AD CS) solution.
We’ve Helped Many Businesses Like Yours
Take the Difficulty Out of PKI Maintenance with our Cloud Private CA
Many organizations have given up on passwordless authentication because building an on-premise PKI is difficult. But with our managed PKI solution, enterprises of every size can leverage the security of internal certificates with modern automation technology that ensures every step of the certificate lifecycle is manageable. Enjoy the best of both worlds: simplicity and security.
|
|
Build Your Own PKI | |
|---|---|---|
| Upfront Infrastructure Cost | $0 | $65,216* |
| Upfront Software Cost | $0 | $141,383* |
| Time for Configuration | 2-4 hours with white glove implentation | Hundreds of hours to set up securely** |
| Level of Maintenance required | None | High maintenance with regular manual patches and updates |
| AI & Monitoring | Monitoring & AI-driven anomaly detection | Set your own alarms |
| Training Required | None | Years |
| Support | Team of experts with experienced implementing PKIs for hundreds of organizations | Limited to your team’s experience |
*Costs are in USD, and are based on building an on-premise PKI with Microsoft Active Directory Certificate Services (AD CS).
**This requirement is based on research conducted by Specter Ops.
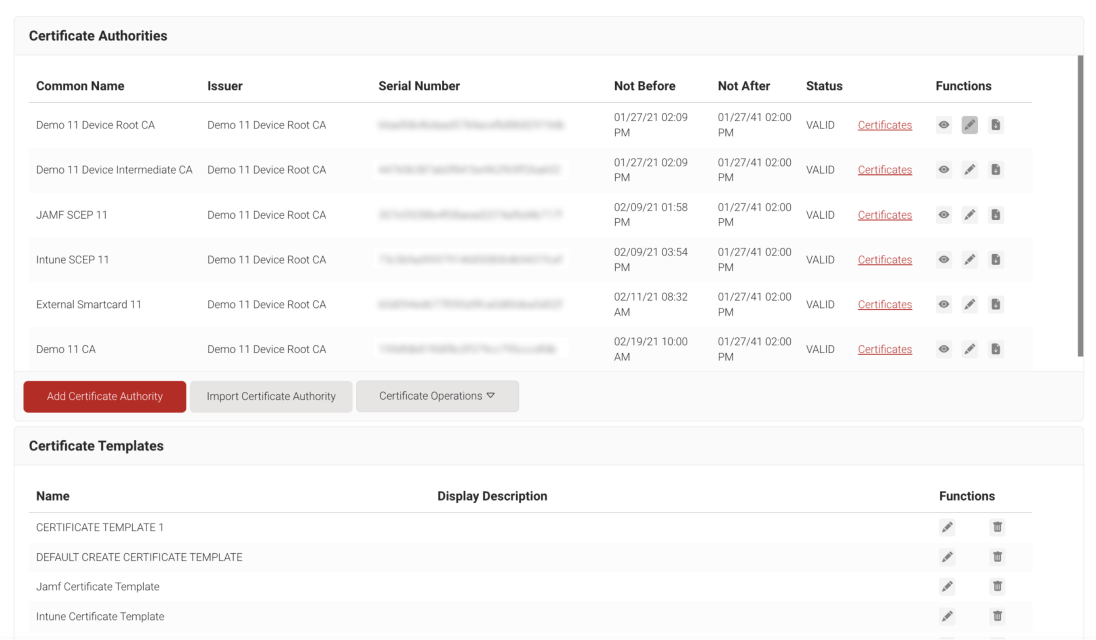
Bolster Network Segmentation with Multiple Private Cloud Certificate Authorities
Our cloud private CA service allows you to create internal certificate authorities quickly and simply. Combined with our innovative policy engine, administrators can increase security segmentation with granular policies based on issuing CA and more. Import external CAs as necessary to leverage our powerful automation platform for any existing PKI your organization has.
- Easily create new certificate authorities in minutes.
- Create policies based on issuing certificate authority.
- Tie different domains and MDMs to unique private CAs, all under your own private PKI.
- Create and export CAs to upload to other systems, such as MDMs.
- Automate the issuance and management of certificates through enrollment policies.
- Import external CAs to the SecureW2 management portal.
Zero-Touch Certificate Enrollment for Managed Devices
Historically, one of the greatest challenges of certificate management has been distributing certificates to all your enterprise’s managed endpoints. That’s no longer the case, thanks to our PKI as a service platform. Our managed device gateway APIs can configure the managed devices on your network for certificate-based authentication with no end-user input.
- Automatically configure and enroll managed company-owned devices through our managed device gateway APIs.
- Connect devices to networks and provide reporting, device analytics, and remote troubleshooting data.
- Push configuration profiles to IoTs, ensuring all devices are using secure certificate-based authentication.
Self-Service Certificate Enrollment for BYODs & Unmanaged Devices
SecureW2’s PKI as a service also provides onboarding technology for BYODs. Potential misconfiguration can be a huge window for human error - and a liability for your network security. Our JoinNow MultiOS onboarding application takes human error out of the equation by configuring unmanaged devices for your users.
- Automatic device 802.1x configuration software compatible with every OS, which includes guided user flow where necessary.
- Configure for device or user certificates.
- Enables easy configuration for server certificate validation.
- From start to finish, configuration takes only a minute or two.
- Support for iOS, Windows, macOS, Android, ChromeOS, Linux, and Kindle.
FAQs
What are the benefits of a Public Key Infrastructure for Organizations?
The ultimate benefit of a private PKI is passwordless, certificate-based authentication. It’s no secret that passwords are a vulnerability, with organizations like Microsoft recommending that you move away from password-based PEAP-MSCHAPv2 to passwordless protocols like EAP-TLS. Digital certificates can be used to secure a range of resources, including your wired & wireless network, VPN, applications, desktop logins, and much more.
Additionally, there are benefits for your end-users. With digital certificates, employees no longer have to deal with frustrating password reset policies and disconnects due to password changes.
Why can’t we just build our own Private CA instead?
Many organizations see the benefits of going passwordless, but think that they can reduce the cost of doing so by building their own PKI and private CA. Unfortunately, this often ends up being a costlier venture in terms of finances and time spent. Building a private CA and PKI requires expertise, space for the servers, and regular maintenance. Additionally, certificate management - from certificate issuance to renewal to revocation - is time-consuming.
Private CA solutions like our JoinNow Connector PKI can save you the resources you would otherwise spend on building and maintaining your own. What’s more, since our PKI is cloud-based, your administrators can access it from anywhere without having to replicate it at every office location.
Does your PKI platform provide both public and private certificate authorities?
Our PKI allows you to create a private certificate authority only. However, you can create as many private certificate authorities as you need. Our customers commonly build a different certificate authority for different groups of people to enable role-based access control, such as having a separate certificate authority for their HR and DevOps teams. This makes managing private certificates for different roles organized and efficient.
We also support importing an external certificate authority. If your organization has its own existing private CA from sources such as Active Directory Certificate Services (AD CS), you can integrate it with our management portal and use our onboarding technologies with it.
What is the purpose of deploying a private CA?
A private CA empowers organizations in certificate issuance for private certificates - or, in other words, certificates that are used internally. Although private certificates can’t be used for external-facing purposes, like code-signing in applications that the public will use, they still greatly enhance the security of your internal resources.
Private certificates enable your administrators to create detailed policies preventing unauthorized devices from accessing your Wi-Fi, VPN, cloud applications, and much more. In order to issue private certificates, however, you first need a private CA.
How does your private CA platform handle certificate lifecycle management phases, such as revocation and renewal?
We wouldn’t be able to call it PKI as a Service if we didn’t provide you everything you needed to manage your private certificates and private CAs. We provide two different technologies to issue certificates. To issue certificates to managed devices, we have our automatic gateway APIs. To issue certificates to unmanaged devices and BYODs, we offer our self-service onboarding technology that empowers end-users to configure their own devices in seconds.
When it comes to revocation, our cloud-based PKI can revoke certificates in a few different ways, including manually and through automatic revocation with some MDMs such as Jamf and Intune. Our private CA service also includes customizable policies you can create, such as non-utilization, which means private certificates that aren’t used for a definable period of time (such as 60 days) are automatically revoked.
What is the passwordless authentication experience like for the end user?
The user experience differs based on whether they are using managed or unmanaged devices/BYODs. For managed devices, the end user will never notice the certificate enrollment process - our private CA service includes gateway APIs that will automatically enroll them for a certificate. For BYODs, you can utilize our self-service onboarding technology, which allows end users to configure their devices for private certificates in a matter of minutes.
After enrollment, certificate-based authentication is mostly the same for either type of end-user. They no longer need to remember a plethora of passwords, reset those passwords regularly, or adhere to complex password requirements.
Can you export the certificate key and use it to authenticate another device?
Public key cryptography requires the use of both a public and private key. While the public key can be sent freely, the private key file must be stored securely, and we take private key storage seriously as a result. The best way to guarantee your private key won’t be removed from your device is to ensure it is stored in the proper key stores and enclaves and set to non-exportable. To increase security further, we recommend that a private key is stored in a device’s Trusted Platform Module (TPM) instead of storing the keys in software.
Which cryptographic algorithms does your Private CA service support?
Our best-in-class PKI supports a range of secure algorithms. Those include RSA 2048 & 4096, as well as SHA-256.