Phishing-Resistant Authentication for Business Apps
Ensure that only authorized users can access your cloud business applications. Streamline the login process for Entra ID & Okta apps with digital certificates, giving access to those who need it faster. Reduce the risk of phishing attacks, MFA fatigue attacks, and more.
Secure Business Applications & Improve Login Experience - Simultaneously
Digital certificates don’t just improve security - they make accessing necessary resources and applications simple for end-users. Instead of having to remember complex passwords or rely on a password manager, they can use certificate-based authentication to access everything they need, including cloud applications.
- Keep Users Connected: Prevent disconnects due to password resets and other password-related issues.
- Prevent Phishing Attacks: Since passwords aren’t being transmitted over-the-air, the risk of phishing and credential theft are dramatically reduced.
- Support Smart Card Login: Install certificates on smart cards to make application access as simple as plugging in a card.
- Eliminate Password-Sharing: Secure access to critical resources and Azure AD and Intune-managed applications by using digital certificates that can’t be shared.
- Reduce Password Fatigue and Frustration: Save users time and effort that would otherwise be spent on brainstorming new passwords or reusing old, insecure ones.
What Real Customers Have to Say About SecureW2
At SecureW2, we have a laser focus on making products and services that customers love. But don’t take our word for it, check out what some of our customers are saying:
Easily Leverage the Security of Azure Certificate-Based Authentication (CBA)
With Azure AD Certificate-Based Authentication (CBA). organizations can empower their users to passwordlessly log in to any Azure cloud application. It’s a balance between both security and an enhanced end-user experience. Apply the device trust you get from Intune to the way you grant access to your business-critical applications.
- Tie the device trust you get from certificates directly to your Azure applications.
- In-depth visibility and context over who’s accessing your applications.
- Segment which users have access to which applications with granular policies.
- Prevent password mismanagement and theft.
- Provide a smoother experience to your Azure and Intune-managed applications.
Passwordless Application Access with Okta Client Certificate Authentication
With Okta client certificate authentication, administrators can make accessing applications simultaneously simpler and more secure. Enable your end-users to log in to multiple business resources just by using certificate authentication. Create detailed application access policies based on multiple points of data, such as the user’s group, location, email address, and much more.
- Eliminate password-related disconnects from Okta applications.
- Dramatically increase the context administrators get from every connection, including data such as MAC addresses and email addresses.
- Simplify end-users’ ability to access multiple applications at once without the need for a complex password.
- Easy configuration and rapid deployment with a vendor-neutral PKI designed for cloud IDPs like Okta.
We’ve Helped Many Businesses Like Yours
Rapid Zero-Touch Certificate Enrollment for Your Managed Devices
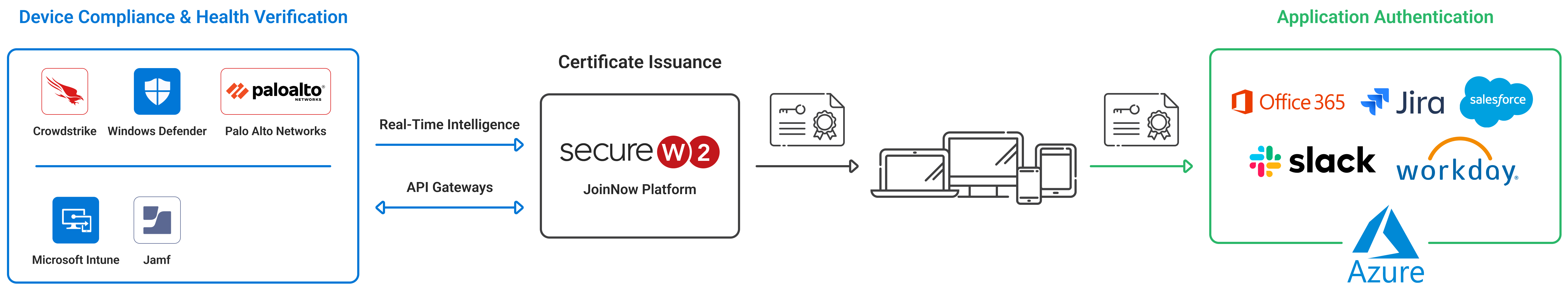
In the past, your network administrators would be right to be concerned about the difficulty of issuing certificates to all your company-managed device. Our Managed Devices Gateway APIs have effectively eliminated that obstacle, enabling zero-touch certificate enrollment for all your managed device with just a few clicks.
- Zero-touch configuration and enrollment for managed company-owned device through our managed device gateway APIs.
- Automate certificate revocation or re-enrollment based on any device/user activity or security event
- Support for all major MDM/EMM platforms such as Jamf, Microsoft Endpoint Manager (Intune), Google Workspace, and more
- Push configuration profiles to IoTs, ensuring all devices are using secure certificate-based authentication.
Top-Rated & Self-Service Certificate Enrollment for Unmanaged Devices & BYODs
Potential misconfiguration can be a huge window for human error - and a liability for your network security. Our JoinNow MultiOS onboarding application takes human error out of the equation by configuring unmanaged devices for your users. Ensure EAP-TLS is configured correctly every time.
- Automatic device 802.1X configuration software compatible with every OS, which includes guided user flow where necessary.
- Configure for device or user certificates.
- Enables easy configuration for server certificate validation.
- From start to finish, configuration takes only a minute or two.
- Support for iOS, Windows, macOS, Android, ChromeOS, Linux, and Kindle.
SSO Certificate FAQs
The ultimate benefit of a private PKI is passwordless, certificate-based authentication based on asymmetric cryptography using a public key and a private key for each certificate. It’s no secret that passwords are a vulnerability, with organizations like Microsoft recommending that you move away from password-based PEAP-MSCHAPv2 to passwordless protocols like EAP-TLS. Digital certificates can be used to secure a range of resources, including your wired & wireless network, VPN, applications, desktop logins, and much more.
Additionally, there are benefits for your end-users. With digital certificates, employees no longer have to deal with frustrating password reset policies and disconnects due to password changes. Successful authentication - and access to the applications they need - is as simple as choosing the correct certificate when they log in.
There are multiple benefits to using certificates for single-sign-on (SSO). Most importantly, the security of your login is enhanced because certificates are significantly more secure than passwords. Passwords are easily stolen through a variety of attacks if they’re transmitted over-the-air, such as Man-in-the-Middle attacks. Certificates also provide device trust, as they can be tied to a device’s compliance status in an MDM such as Intune or Jamf. Because a certificate can be issued through your MDM, you have certainty about the devices accessing your platform.
Certificates grant your administrators greatly enhanced visibility over who’s accessing your business applications. A set of credentials doesn’t tell you anything because anyone can use them. A certificate, on the other hand, can be encoded with numerous attributes from your Identity Provider or MDM, such as username, MAC address, device serial number, user group, and more.
The end-user experience is also improved when you use certificates. Also SSO is already an improvement over having to log into multiple platforms with different passwords, it can be even easier when you don’t need to use passwords at all. Logging in is reduced to a couple of clicks without any need to remember a complex password.
PKI certificates can replace passwords or be used alongside them in MFA in the single-sign on process. This can look a little different depending on what your users are logging into, but with Azure CBA, for example, it means they choose to log into applications with a certificate instead.
The end-user experience is much simpler. When they log into your cloud applications through a browser, they can simply click on the certificate.
We wouldn’t be able to call it PKI as a Service if we didn’t provide you everything you needed to deploy certificates. For endpoint distribution, we have our automatic gateway APIs for managed devices and our self-service onboarding technology for unmanaged devices/BYODs.
When it comes to revocation, our cloud-based PKI can revoke certificates in a few different ways, including manually and through automatic revocation with some MDMs such as Intune. With automatic revocation, our gateway APIs can check within Intune or Jamf to see if a device has been stolen, retired, or rendered non-compliant in any other way. The certificates for these devices are automatically revoked.
You can also set the validity period for a certificate. This gives certificates an expiration date; an expiring certificate can no longer be used to authenticate once it passes that date. Access is declined automatically by Cloud RADIUS.
Our PKI makes renewal simple, too. For managed devices, certificate renewal typically happens on an automatic basis a month or two before the certificate’s expiration. For BYODs, administrators can set a customizable notification email to go out to end-users, encouraging them to re-enroll for a certificate before it expires.
Yes. Our platform can issue a client certificate to smart cards such as Yubikeys to allow for smart card-based single sign-on.
If you’re already using SecureW2’s PKI, setting up Azure AD Certificate-Based Authentication (CBA) can be done in just a few steps. In a nutshell, you’ll begin by exporting your SecureW2 Certificate Authority (CA) to Azure AD/Entra ID, then you’ll create a CBA policy in Azure and issue certificates to the users and devices you want to use the policy.
We have more detailed configurations steps in this Azure AD CBA guide for more information.
Active Directory Certificate Services is Microsoft’s legacy PKI solution that gives organizations the ability to build their own on-premise Public Key Infrastructure. Unfortunately, this often ends up being a costlier venture in terms of finances and time spent. Building a private PKI requires expertise, space for the servers, and regular maintenance. Certificate lifecycle management with Active Directory Certificate Services - from issuance to renewal to building a certificate revocation list - is time-consuming.
It’s important to understand the costs of building a PKI with Active Directory Certificate Services. Aside from taking potentially hundreds of hours to set up initially, there’s a high upfront infrastructure and software cost that can easily exceed $200,000 USD. On top of up-front software and infrastructure costs, Active Directory Certificate Services will have recurring costs in the form of high maintenance.
These costs, unfortunately, are unavoidable. A PKI is a foundational part of security systems. Rushing a configuration, or setting it up with inexperienced professionals is a huge liability. In this writeup by Specter Ops, they identify countless security vulnerabilities organizations will run into if they leave default settings enabled in AD CS. This reason alone is why many organizations choose a managed PKI.
Finally, a PKI service like ours makes it easier to manage on a day-to-day basis. You can generate whatever type of certificate you need, whether it’s a root certificate, a CA certificate, or certificates for user authentication. All of this can be achieved through a single pane of glass, saving you both time and money.
No, CBA isn’t limited to just Azure AD/Entra ID and Okta. It works with both Google and OneLogin, as well. Certificates are pretty broadly supported across different applications.
However, at the time of writing this (September 2024), most of our testing has been with Okta and Azure AD/Entra ID. The passwordless authentication process for web apps works well with both these platforms.
Schedule a Demo
Sign up for a quick demonstration and see how SecureW2 can make your organization simpler, faster, and more secure.
Pricing Information
Our solutions scale to fit you. We have affordable options for organizations of any size. Click here to see our pricing.