Integrating a RADIUS server with your network security infrastructure is a wise decision. RADIUS or AAA (Authentication, Authorization, and Accounting) servers guard your network against unauthorized access by verifying individual devices, granting them different levels of authorization, and keeping activity logs. You can read more here about how one of our customers benefited from using our Cloud RADIUS solution to improve the safety of their network.
This doesn’t mean that a RADIUS server is the only answer you’ll ever need, though. Protocols like RadSec seek to make RADIUS protocol security even stronger by protecting RADIUS communication with transport layer security (TLS). We’ll be taking a closer look at what a RadSec server is, how it works, and how it benefits you here.
What is the RadSec Protocol?
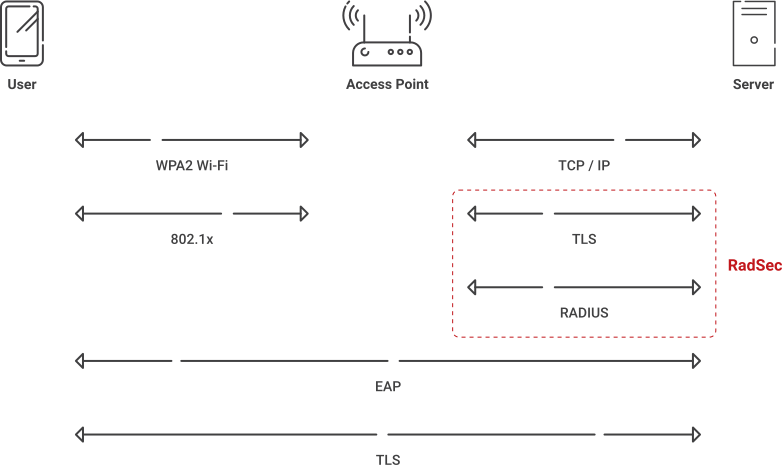
RadSec, also known as RADIUS over TLS, is an 802.11x protocol for transporting RADIUS packets through TCP (Transmission Control Protocol) and TLS (Transport Layer Security), which themselves are protocols.
RADIUS has historically relied on the MD5 message digest algorithm to create a 128-bit hash value for security, but that has had known vulnerabilities for many years. While that weakness could be overlooked by compensating with strong security in other network layers, the increase in network roaming has necessitated strict security on the transport layer, so MD5 is no longer sufficient. Basically, RadSec seeks to ensure secure communication between the RadSec client and the RadSec server by using an encrypted TLS tunnel.
What is RadSec used for?
RadSec is a feature supported by some RADIUS servers. Because RadSec forms an encrypted TLS tunnel between the client and server, it’s even more secure than your standard RADIUS. It can be used by any organization using RADIUS servers, but is commonly used in situations where employees are expected to roam between networks, such as businesses with multiple locations.
How Does RadSec Work?
The simple explanation of RadSec is that it allows you to transfer RADIUS packets through public networks while still enjoying end-to-end security through the transport layer using TLS.
This configuration is particularly useful because it allows dynamic establishment of connection. Normally, when a network connects to peers it must either use an IP address and shared secret to identify them, but RadSec can do it securely and on the fly because both servers are equipped with x.509 digital certificates and an enterprise PKI.
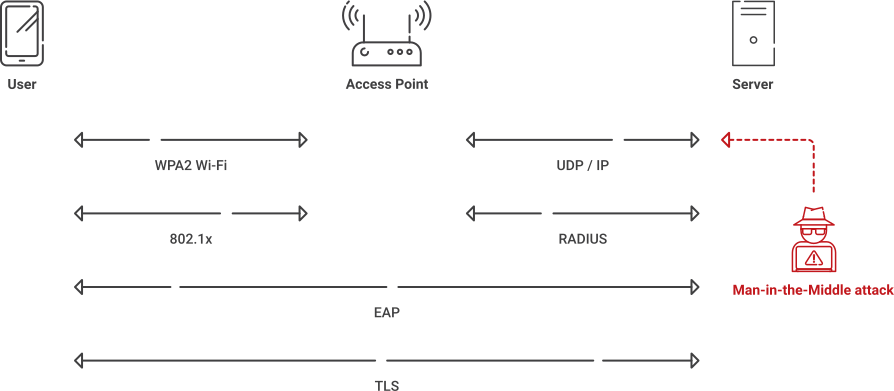
RADIUS Over UDP
RADIUS over TLS (RadSec)
What is a RadSec Server?
A common practice is to name a server after the protocol it uses. Thus, servers that use the RADIUS protocol are often called RADIUS servers, while servers that use the less secure LDAP protocol are often called LDAP servers.
As we mentioned previously, the RadSec protocol can be used to heighten RADIUS security, especially in a roaming environment. A RADIUS server that utilizes the RadSec protocol can be referred to as a RadSec server if you want to get technical. Of course, you can still call a Radsec Server a RADIUS server at the end of the day, as well.
What is a RadSec Server Certificate?
RadSec, also known as RADIUS-over-TLS, increases the security of a RADIUS server by protecting communication between it and its clients with a TLS tunnel. However, some cyber attacks are capable of directing devices to the wrong servers, preventing them from connecting through your TLS tunnel in the first place. The solution to this problem is a RadSec server certificate, which can be validated by clients.
Server certificate validation prevents devices from connecting to the wrong server and exposing themselves to potentially hostile networks. When server certificate validation is configured, the server will show its certificate to any devices connecting to it in order to prove its identity. Assuming both the device and certificate trust the same Certificate Authority that issued the server’s certificate, each user can be certain they are interacting with the right server, ensuring secure communication with trusted networks.
A RadSec server certificate is simply a digital certificate equipped by a RadSec server. When an access point (AP) interacts with the server, it’s able to verify that the server is trusted through the certificate. This setup can protect users from man-in-the-middle attacks or other cyber-attack methods that make use of false APs. It also protects users from connecting to untrusted networks.
This setup also has its privacy advantages. Because it ensures users and devices are connecting to the correct server, third parties are protected along the way from having their traffic intercepted and analyzed.
What is RadSec Proxy?
RadSec proxy can refer to a couple of things. The first is a RADIUS proxy available online that was created with the ability to support TLS(RadSec) on top of the standard RADIUS UDP. Because it was designed for simple configuration, it can be an easy addition to your network. The second definition could be any RADIUS proxy that supports RadSec.
Can you make RadSec Proxy Servers?
Yes! RadSec operates like RADIUS in most every way, including the ability to make and use proxy servers. Just as you can make a RADIUS proxy, you can also make a RadSec proxy server. This is particularly helpful if you want to make local RADIUS servers for specific access points.
Furthermore, it’s possible to customize your RadSec proxy server to a form TLS connection instead instead of the default TCP connection. If you would like to see more information about this process, we’ve found a guide that shows how to configure RADIUS to RadSec, but it only works for on-premise systems.
Does a RadSec Proxy Use GRE Tunnels?
GRE stands for Generic Routing Encapsulation. Put simply, a GRE tunnel can be used to wrap packets that use one routing protocol inside the packets of another protocol – sort of like a nesting doll. The end result is something that functions similarly to a VPN by connecting two separate networks over the internet. However, GRE tunneling isn’t used for the same security purposes that a VPN is often used for.
It’s also possible to tunnel GRE over TLS or IPSec. Like using a VPN, you would typically do this for the sake of increased security.
At this point in time, RadSec servers and proxies generally don’t use GRE tunnels. There currently isn’t a lot of firmware that supports RadSec, so many manufacturers have looked for alternatives, such as RADIUS over IPSec. Furthermore, there are some other RadSec alternatives that do use GRE tunneling.
Benefits of RadSec
Utilizing digital certificates in the TCP/IP RADIUS streams adds several layers of security hard to achieve otherwise.
- Normal RADIUS requests are sent in plaintext. Such a request is vulnerable to cyber attacks that intercept communication, like MITM attacks. RadSec encrypts the transmission packets, so zero information can be sniffed or intercepted.
- Even if the RADIUS requests were intercepted, it would be impossible to tamper with them without the recipient being aware because of the intrinsic mutual authentication between the client and server. You are always certain of the identity of both parties.
- Random packet loss is trackable, so data won’t go missing without anyone being aware of it.
RadSec Use Cases
Who is RadSec for? It’s commonly implemented in one field: roaming environments. When a device transitions between mobile or cellular data to a local Wi-Fi hotspot, it either has to disconnect and reconnect to the internet, or be “handed off” by the networks.
The hand-off situations, also known as device offloading, are becoming increasingly common. Between Passpoint and OpenRoaming, we can expect seamless, automated roaming for mobile devices to become the norm within the next few years. However, there is vulnerability any time you switch networks as it’s an opportunity for a man-in-the-middle attack. RadSec can eliminate the vulnerability by facilitating the switch on the transport layer (one of the key features of OpenRoaming).
Eduroam-RadSec Use
Perhaps the most widely used implementation of RadSec is eduroam – a roaming service that allows students and staff to easily access the internet while visiting member institutions. The users can safely access the internet without the hassle of sign-ins or onboarding, thanks in part to RadSec.
While it’s mostly used in roaming scenarios today, everyone could potentially benefit from RadSec. The historical hassle of deploying TLS is what has kept it from being widespread, but SecureW2’s TLS solution is plug-and-play with your existing infrastructure.
Does Microsoft NPS Use RadSec?
After some searching, we were unable to find any official documentation stating that Microsoft’s NPS uses RadSec. Our conclusion, then, is that it does not appear to support RadSec infrastructure right now. That being said, there isn’t really a need for it to support RadSec currently, either.
NPS is typically used in tandem with Active Directory in on-premise infrastructures. Given that RadSec is most useful in OpenRoaming, it doesn’t make sense at this point in time for on-premise hardware to support it.
This doesn’t mean, however, that it’s totally impossible to use Active Directory in an OpenRoaming environment. Active Directory technically can be used as an OpenRoaming backend, but there isn’t much of a demand for its use this way.
Easily Deploy RadSec with SecureW2
Security is an ever-evolving pursuit. Considering the future is equally as important as protecting your network in the present. Even if you don’t have the infrastructure to support RadSec today, it’s entirely possible that you’ll want to make the move to RadSec in the future.
The good news is that SecureW2’s low-cost solutions can help. We have a turnkey cloud PKI that you can use to move to secure passwordless authentication backed by digital certificates. You can check out our pricing or contact us to learn more about our RadSec capabilities.