Protecting and encrypting communications online is vitally important as there are countless attempts made daily to intercept them for nefarious purposes. From securing a bank transaction to protecting an authentication attempt, people communicate highly sensitive information online, and if it’s not protected, the results can be disastrous. Read here how a Fortune 100 took security into its own hands and transitioned to a more secure authentication method.
For years, the method for encrypting communications has been SSL (Secure Socket Layer) and TLS (Transport Layer Security). Below, we will discuss how these encryption protocols work and how they are being outfitted to combat modern threats.
Transition from SSL to Transport Layer Security (TLS)
While it is possible to perform a network connection and communicate without encryption, it’s a risky action. The connection would be open to eavesdropping or even theft. If you’re communicating an email login with an unsecured website, that log-in could potentially be viewed and used for unauthorized access.
SSL was created in 1995 to combat this type of theft and secure network connections. This first generation was updated in 1999 and renamed to TLS with improvements in security and communication protection. While SSL is not supported today by modern processes, the acronym has become a synonym with TLS and is still used.
SSL and TLS are protocols used to establish authenticated and encrypted links between computers, websites, servers, and more. To establish this link, they use an encryption protocol that ensures no outsiders can read the messages transferred between the two parties. In order to establish this link, they bind identities to cryptographic key pairs via certificates.
There are two main encryption types used to authenticate with keys: asymmetric and symmetric encryption. With symmetric encryption, both parties use a single shared key to encrypt and decrypt communications. This is a highly efficient method that can be quickly processed because it involves only one key. But using one key is less secure when compared to asymmetric encryption.
Asymmetric encryption occurs when both parties hold one key in a key pair. In this situation, the private key is held by the server and is secured from prying eyes while the public key is distributed freely to clients. When authenticating, the public key encrypts a message that is sent to the server and can only be decrypted by the private key. Without the private key, the message is unreadable. This method is more secure than symmetric encryption but is more resource intensive.
Each key is bound to a TLS certificate that contains identifying information about the holder. TLS certificates are signed by a Certificate Authority (CA) before being imprinted with identifying information and distributed to a user device or server or other tech. As a result, when a certificate is sent to be authenticated, the receiver can quickly see that the certificate is signed by a trusted CA and move forward with the authentication. The subsequent process that establishes trust is known as the TLS handshake.
The TLS Handshake
The TLS handshake is a series of communications between two entities that establishes trust before allowing regular network communication. This process occurs during situations such as opening an HTTPS website or authenticating to a RADIUS server. While the process does involve several steps, there are 4 main actions that are completed and accomplished.
Hello Messages: The client and server exchange a sequence of “hello” messages to establish the secure connection’s parameters at the start of the handshake.
Key Exchange: In the next step, the parties exchange encryption keys, and the server’s certificate is displayed. In cases of mutual authentication, the client can additionally present its certificate.
- Specify the version of TLS that will be used
- Decide which cipher suite will be used during communication
- Authenticate the identity of the server and client
- Generate session keys to encrypt communications during the subsequent session
The entire process is incredibly fast in real-time and establishes a secure connection between the two parties. This process is vitally important and should be the benchmark before communicating any sensitive information. For example, you should be sure that any website you’re using has undergone a TLS handshake before gaining access.
SSL vs. TLS in Email Security
Email exchanges can also be secured using TLS or SSL. However, TLS is more widely utilized because of its advanced capabilities, which increases security. Additionally, a TLS client and an SSL server are able to communicate since TLS and SSL are backward-compatible.
HTTPS Encryption
When you access a website and see HTTPS at the front of the URL, your computer has successfully completed the TLS handshake with the current website. HTTPS is a protocol used to send data between a website and the web browser used by the client. It uses asymmetric key encryption to ensure each party can be properly identified.
If it is an HTTP website, it is considered unsecured and is risky to use, especially if any of the communications contain sensitive information. HTTPS is quickly becoming the standard for online communications and is heavily favored by search engines like Google.
TLS Certificate Authentication
TLS certificates contain identifying information about the user that is presented as a form of ID when authenticating. A use case that many organizations are beginning to favor is the use of certificates instead of credential-based authentication. When compared, certificates outperform credentials in every important metric, such as speed of authentication, user experience, and overall security.
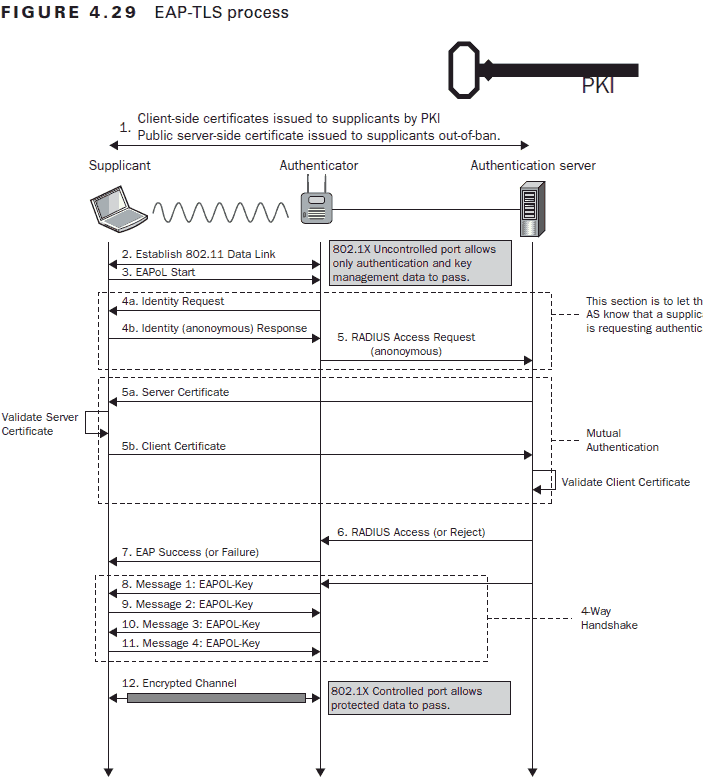
EAP-TLS authentication is considered the most secure network authentication method and is commonly used on certificate-based networks. It generates an end-to-end encryption tunnel that establishes the identity of the server, the user, and the device. If you’re looking for stronger security and a more efficient network experience, adding certificates as an authentication factor can be revolutionary.
TLS and SecureW2
SecureW2’s JoinNow Connector, a Cloud PKI solution, opens up new possibilities for SSL setup and ensures the highest level of security for network authentication. It provides a single platform for certificate production and maintenance, making the smooth administration of SSL certificates easier. This implies that organizations may do away with the requirement for costly infrastructure, as well as the hassle of managing or maintaining their SSL operations. There are no extra fees associated with storing all of the keys in HSM.
For the end user, the JoinNow onboarding solution is the most efficient certificate provisioning experience available. All the user must do is enter their IDP credentials, and they are quickly configured for EAP-TLS and issued a certificate. Our management portal provides numerous tracking and visibility tools to give you an accurate picture of who is on the network and what device they are using.
If your organization isn’t utilizing TLS, it could be at greater risk for outside attacks and accidental exposure. Check out SecureW2’s pricing page to see if our certificate solutions can provide TLS security for your organization.