Internet of Things (IoT) devices are a necessary evil for almost all industries including but not limited to the healthcare sector, hospitality industry, and manufacturing facilities. These devices are embedded with software and other technologies that are used in most industries because of their utility for data collection to understand different trends like customer behavior, or product usage to name a few.
Common IoT Use Cases
- Smart Appliances for Smart Homes to monitor temperature, lights, and other smart appliances
- HealthCare Sector Medical IoT devices include devices that help monitor the blood sugar and heart rate of a patient, bedside monitors
- Hospitality Industry IoT devices include smart home IoT devices as well as kitchen appliances
- Smart Cities use IoT devices to monitor and collect information like usage of electricity, temperature, and air quality
- Fitness Trackers used mostly for healthcare and fitness are used to track fitness level and physical activity
- Smart Vehicles use IoT devices to monitor car maintenance and pay tolls electronically
- IoT devices in Manufacturing Industry are used to monitor equipment for compliance, safety, and productivity
Common IoT Attacks
Many IoT devices do not support 802.1X configuration because they are equipped with computers that have a very narrow function. But since they need to access the organization’s network to function, they leave the network vulnerable. These devices are usually not accounted for as a fundamental part of the infrastructure, and so their security is usually not given priority. This often leaves an organization’s network vulnerable to cyber-attacks because they become easy gateways for hackers since these devices are still not designed with great cryptography and most IoT devices have unsafe password management making them the weakest link in the network. Here are some of the common security threats IoT devices are faced with.
Privilege Escalation
IoT devices are the perfect target of privilege escalation attacks because of their vulnerability which we discussed above. Hackers can take advantage of the vulnerabilities to plant bugs and escalate their access level to penetrate the network of an entire organization leaving it crippled.
Man-in-the-Middle (MITM) Attack
By exploiting the gaps in the cyber security of IoT devices, a hacker can access sensitive information that would otherwise be encrypted. By modifying the packets in the communication of the IoT devices with their respective networks, an attacker can escalate the attack and gain access to the network to do major damage or even control the network.
Eavesdropping
An eavesdropping attack, also known as snooping or sniffing, is when a hacker gains access to an unsecured transmission between a device or its network, and IoT devices are potentially the perfect host for such attacks.
Brute-force password attacks
IoT devices have the most unsafe password management as their passwords are often easy to crack and never changed making brute-force password attacks or dictionary attacks (that exploit bad password management or easy-to-crack passwords) fairly easy.
HIPPA journal in one of its articles states that 82% of Healthcare Organizations Have Experienced a Cyberattack on Their IoT Devices. An article in Forbes lists IoT attacks as a hot category for cyber attacks. Cyber attacks on IoT devices are becoming fairly common and it is time we start looking at minimizing the threat they pose to network security.
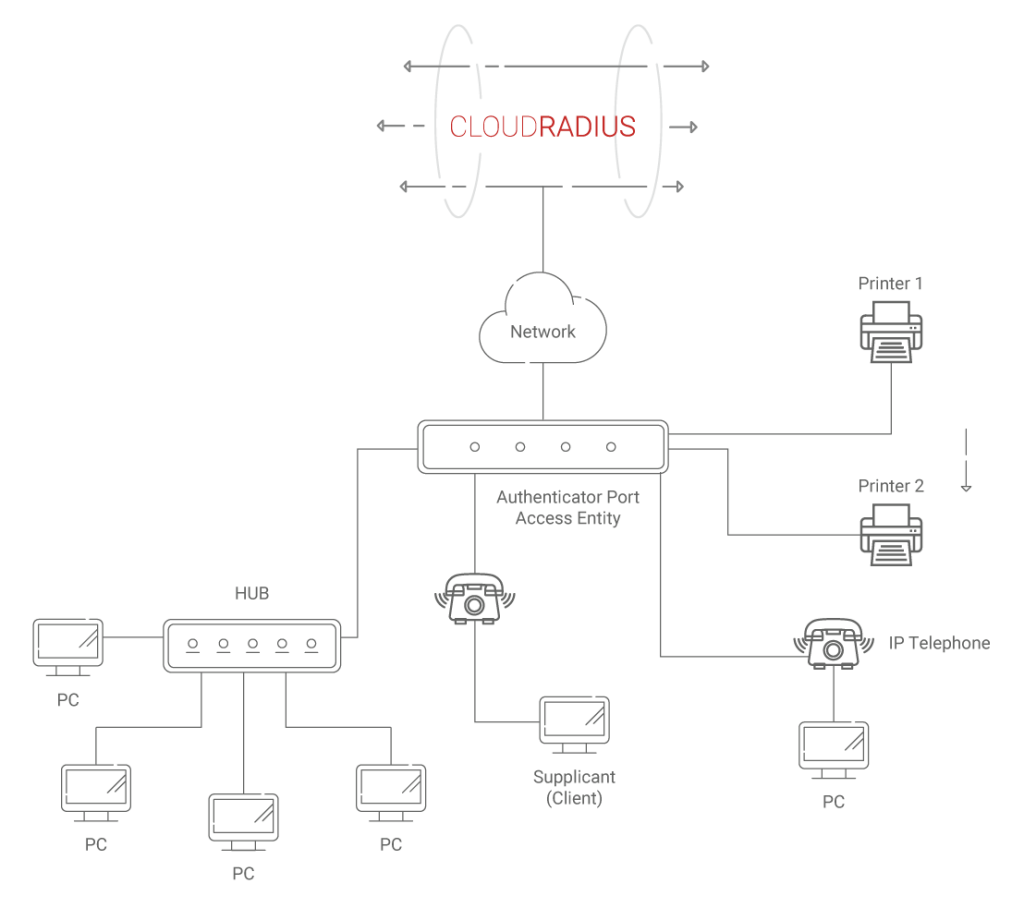
RADIUS Authentication or MAC Auth Bypass for IoT
Remote Authentication Dial-In User Service (RADIUS), also referred to as an AAA (Authentication, Authorization, and Accounting) server is an authentication server that decides if a user/machine trying to connect to a network should be provided access. RADIUS decides this by verifying the credentials or certificates of the user or machine that support 802.1X and checking the level of access a user has by referring to the Identity Provider (IDP) like Azure AD, Google, or Okta.
MAC authentication bypass (MAB) uses the Media Access Control Address (MAC address), also known as a hardware ID number, to identify, authenticate, and determine the level of access of a device. RADIUS MAC authentication bypass can help minimize security risks faced with IoT devices to a considerable extent. Though not as safe as 802.1X, with MAB, you can now get better visibility over the IoT devices and control the level of access they have to a network.
How RADIUS MAC Auth Bypass Works
At a high level, this is how RADIUS MAC Auth Bypass works:
- Switch submits 3 EAPoL identity requests every 30 seconds after the third time out, the switch indicates that the device does not have a supplicant and so initiates MAC auth bypass to authenticate the device.
- MAC auth bypass will refer MAC address database to identify if a particular MAC address is authorized to access the network by sending accepting a single packet from an interface to identify a MAC address origin.
- Once the source is identified, the packet is discarded and the switch creates a RADIUS access-request-message.
- The RADIUS server then receives the access-request message and performs MAC authentication by validating the address to check if the MAC address matches with the list of MAC addresses that are authorized to access the network.
Enabling MAB for Minimizing IoT Attacks
The primary benefit of using MAC auth bypass in conjunction with a dynamic cloud RADIUS is that MAB can be implemented with both dynamic access list and VLAN assignments just like with 802.1X. Though not as secure as the latter, MAB helps get better visibility over the devices in the network, that otherwise go unmanaged and leave the entire network vulnerable to cyber attacks.
MAC Auth Bypass For Healthcare Sector
The Health Insurance Portability and Accountability Act (HIPAA) passed in 1996 has been instrumental in shaping how patients’ data is handled and who has access. With digitalization, HIPPA’s purview is not limited to just the physical documentation of these records but has extended to how the records are stored and accessed over the cloud. It becomes very important from a HIPPA standpoint to ensure there is clear visibility as to who has accessed a patient’s data and if they have the required access level. By securing your network with a managed cloud RADIUS server that operates in accordance with 802.1X, you can prevent unauthorized access to your network and be HIPPA compliant.
But what about the devices that do not support 802.1X? MAC auth bypass can help you with these devices as you can now have better visibility over these machines. Let’s see how MAC auth bypass helps you be HIPPA compliant with devices that do not support 802.1X:
Unique Credentials for Network Access
HIPAA requires that each user have unique credentials. MAC auth bypass allows each device its own set of credentials in the sense that it uses the unique MAC address of a device to identify and authorize it for network access. With MAB, there is better visibility as to when and what device is accessing patient information.
Device Authentication
MAC auth bypass authenticates a device by looking up at the MAC address and matching it to the list of authorized MAC address list. With a managed cloud RADIUS, a device will be provided access only after matching the MAC address with the list of approved MAC addresses so only a device that has been authenticated can access the network.
Identity-Based Dynamic Authorization
MAB is compatible with all dynamic authorization techniques that work with 802.1X authentication. With a dynamic Cloud RADIUS, you can dynamically segment devices at the moment of authentication. For example, a device can be dynamically approved for a particular VLAN based on not just its MAC address, but also its geographical location or the time of the request.
This helps in ensuring that the authorized device only has access to the necessary data and applications, a critical tenet of Zero Trust Network Architecture. For example, a printer at the billing office will be able to access the Insurance coverage information only whereas, a bedside monitor can be provided with access to medical reports of the patient.
Better Network Visibility of Devices that don’t support 802.1X
Mac Authentication Bypass enhances network visibility by linking authentication events to unmanaged devices, providing valuable context about the event and positively identifying the device in question. This is especially useful for security audits and compliance requirements (such as HIPPA for the healthcare sector), network usage statistics, and network forensics as the devices that otherwise go untracked are now monitored. MAB also acts as a Layer 2 controller that allows you to control network access.
Protect IoT Devices with RADIUS MAC Auth Bypass
IoT devices have become an integral part of our lives as well as most industries and their value in making our lives easier cannot be negated. Especially in the healthcare sector, IoT devices have taken a special place in adding value to patient care. But keeping in mind the security threats they pose to a company’s network, it’s time to consider alleviating the risks.
MAC Auth Bypass helps complete an organization’s security audit or data usage report with better accuracy as it gives visibility over devices like printers, IP phones (Internet Protocol phones), and medical equipment on your network, that otherwise would not get registered. Also, it helps you be HIPPA compliant with the devices that would otherwise have been very difficult to track. Here’s how our services have helped our customers from the healthcare industry to get their network secured.
SecureW2 has affordable options for organizations of all sizes. When you’re ready to protect ALL of your endpoints, IoT devices included, submit a pricing request here.



