Organizations are always looking for a new strategy to increase the convenience of using their network without compromising security. As a result, many have sought out cloud solutions. Read here how a SecureW2 client transitioned to cloud-based networking and improved the user experience and overall security.
Cloud-hosted LDAP has gained popularity as a replacement for traditional LDAP and allows organizations to benefit from the use of LDAP in a remote setting. There are both advantages and disadvantages anyone should consider before making the move to cloud-hosted LDAP.
Why Use Cloud-Hosted LDAP
The most visible benefit of any cloud-based technology is the ability to ditch on-premise hardware. An on-prem setup requires things like physical security, high setup and maintenance costs, involved updating processes, and more. A cloud solution bypasses so many of these costs, since you don’t need to worry about physical setup, security, or maintenance. .
A cloud-hosted LDAP solution is often provided by organizations with an LDAP-as-a-service model. They’re able to streamline an otherwise time-consuming configuration process and have an organization ready to authenticate rapidly.
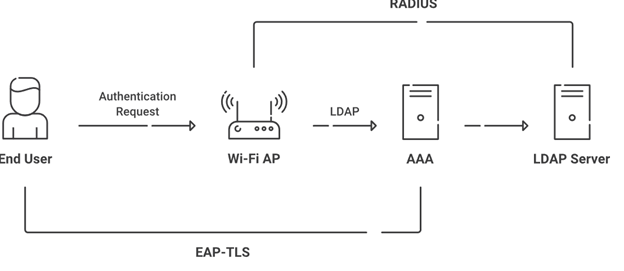
Cloud-hosted LDAP can authenticate a wider variety of applications compared to traditional LDAP, especially cloud-based applications. Additionally, the ease of authentication enables LDAP-based user groups and the ability to implement Zero Trust policies to ensure that users only access the resources they need.
A key problem many organizations experience when dealing with authentication is redundancy and load balancing issues. If an organization experiences a high volume of authentication requests, the server may become overloaded and cause an authentication slowdown. The solution is a redundancy server that would take on the excess authentication logs, but with an on-premise setup, this means another server with all its additional costs. A cloud-based solution can simply utilize another cloud server.
An LDAP Vulnerability
One of the reasons LDAP has seen much updating in recent years is its vulnerability to various attacks. If an attacker is able to bypass authentication security, they can gain network access and do untold damage or steal valuable data.
A specific instance involved LDAP affecting IBM software. The attack allowed a remote user that was authenticated by LDAP to escalate their privileges and perform actions that should not have been available to them. This attack is known as an LDAP Injection.
Injection attacks are not a new phenomenon. The attack requires someone to type malicious code into a user input field. When the code is activated, the attacker can gain unauthorized access, perform data theft, hijack a user’s session, or edit a website or other materials. If an application is not properly sanitized and the code disabled, the attacker may be able to change their permissions and perform even more damage.
Another more common issue that many LDAP users face is the overall weakness of credential-based authentication. Credentials are easily stolen through various attacks like Brute Force or Dictionary attacks. But it doesn’t take a sophisticated mind to steal passwords. Various phishing methods have been found to be highly effective. Even without obvious malicious interference, an approved user may simply lose their password or give it unknowingly to an unreliable person. If even one person doesn’t live up to password best practices, the entire network could be left at risk.
An LDAP Solution From SecureW2
While using Cloud-Hosted LDAP is a step up from traditional LDAP, most organizations still require a wider range of authentication capabilities. SAML-based apps, RADIUS server authentication, and secure VPN are common authentication needs that are not fully covered with LDAP. Luckily, SecureW2 provides authentication security for every situation.
SecureW2 authentication software can easily integrate with any network infrastructure and greatly increase an organization’s authentication spectrum. Our software has the capability to authenticate RADIUS requests, LDAP and SAML apps, remote authentication requests, and more.
Perhaps the greatest benefit organizations experience from SecureW2 is the use of certificate-based authentication instead of credentials. Certificates simply outclass credentials in every metric. They’re far more secure than traditional credentials thanks to public key cryptography and they cannot be stolen or reproduced by attackers. Furthermore, they’re automatically authenticated when in range of the network, and they provide a better user experience.
The process of setting up a certificate-based network is fast and easy with SecureW2, and users can self-configure their devices in seconds and be provisioned with a certificate that lasts for years; no password reset policies needed! Additionally, certificates create inherent device trust because they are tied to the identity of both the user and the device. As a result, organizations can implement Zero Trust policies because each user and device is always accurately authenticated.
The transition to cloud-based networking has created huge leaps forward in security and convenience, and Cloud-Hosted LDAP is no exception. If your organization is looking to upgrade their LDAP protocol without sacrificing usability, SecureW2’s authentication solutions can be key to securing every aspect of your network. Check out our pricing page to see if our LDAP solutions can upgrade your network.