Key Points
- Android 13 now requires server certificate validation, pushing organizations to replace weak password-based protocols with secure EAP-TLS authentication.
- Google’s Remote Key Provisioning strengthens device trust, using short-lived certificates and eliminating risks tied to factory key provisioning.
- Cloud PKI and onboarding tools simplify Android BYOD enrollment, reducing setup complexity while improving security and user experience.
Integrating the capabilities of two leading operating systems, Android and Windows, have been a dream for most tech-savvy enthusiasts across the globe. Microsoft is going to offer this upgrade by offering smooth integration of Windows 11 and Android 13, along with some other leading operating systems.
Since many employees are using their smartphones as a BYOD devices for working remotely, it becomes imperative to have a broader understanding of Android 13 in order to keep on top of your organization’s security. In this article, we will discuss the latest features of Android 13 and the means to integrate it with the server certificate for better security.
Understanding Server Certificate Validation
Server certificate validation is a WPA2-Enterprise security feature that requires devices to confirm a server’s legitimacy before attempting to log in to a network. By examining the CA (Certificate Authority) that certifies the RADIUS server and ensuring that it is trusted, devices may affirm the server’s legitimacy.
A “root store,” or pre-installed list of trusted CAs, is present on 802.1X capable devices (and also web browsers). The device and RADIUS must both trust the same CA that issued the server validation certificate for server certificate authentication to work.
Web server certificates and RADIUS server certificates are the two most used kinds of server certificates. Their shared trait is using a certificate chain of trust to identify the parties involved. Both parties can share information securely thanks to the certificate chain of trust.
Public certificate authorities are the default group of trustworthy certificate authorities in most root stores. If your server certificate is utilized appropriately and is signed by a public CA, the client devices won’t see any SSL issues.
However, you can also utilize server certificates issued by private certificate authorities, though typically only for internal applications. Some operating systems will throw an error message If you attempt to install a private certificate, for example, iOS will display a warning (certificate not recognizable).
As an administrator, you must ensure that every device trusts the issuing CA to shield consumers from connection errors.
Does Android 13 Require Server Certificate Validation?
Yes, Android 13 requires Server Certificate Validation to configure a WPA2-Enterprise network connection.
Android compels organizations to adopt the more secure certificate-based authentication protocol (EAP-TLS) or, at the very least, appropriately configure their managed supplicants for correctly configured server certificate validation.
Previously, it was a common practice for organizations to instruct their users to select the “Do not validate” option while manually configuring the network on BYOD devices. Often these instructions were available in public-facing documents. Hackers interpret this as a request to put up a counterfeit access point with a spoofed SSID in order to harvest real user credentials.
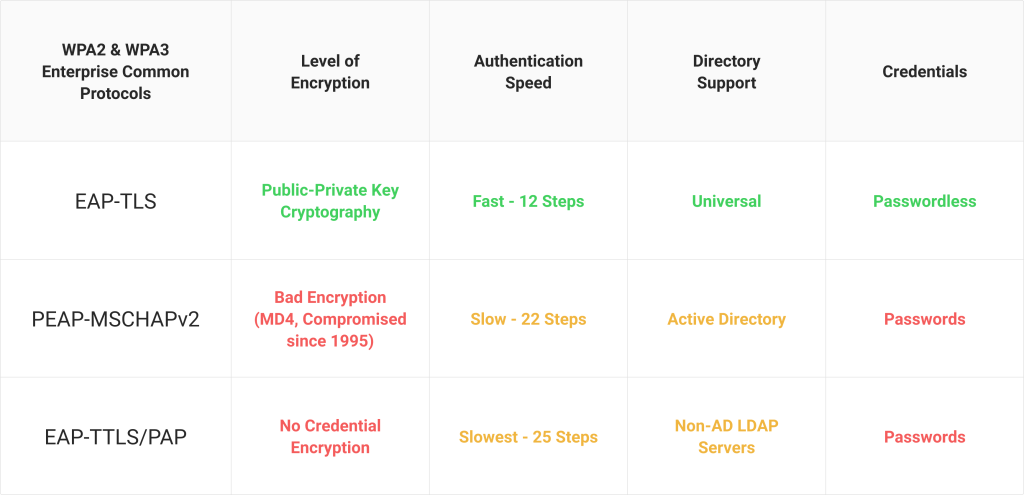 Server certificate validation would still be required even if firms weren’t aggressively disclosing their network vulnerabilities. Most businesses employing WPA2-Enterprise networks continue to use antiquated authentication protocols like PEAP-MSCHAPv2 and EAP-TTLS/PAP that require passwords for authentication. They perceive that digital certificates and EAP-TLS authentication are too cumbersome to implement, which might be the reason for this hesitance.
Server certificate validation would still be required even if firms weren’t aggressively disclosing their network vulnerabilities. Most businesses employing WPA2-Enterprise networks continue to use antiquated authentication protocols like PEAP-MSCHAPv2 and EAP-TTLS/PAP that require passwords for authentication. They perceive that digital certificates and EAP-TLS authentication are too cumbersome to implement, which might be the reason for this hesitance.
That hasn’t been the situation for a while, thanks to the turnkey solutions from managed PKI providers like SecureW2 that provide everything a business needs for certificate-based authentication. We can leverage and connect with your current infrastructure to deploy certificate authentication quickly and effectively.
Google Remote Key Provisioning in Android 13
Since Android 8.0, attestation as a feature has been essential. With each new version, the need for device trust has become more critical for several functions and services, including SafetyNet, Identity Credential, and many third-party components. Android has been reviewing its attestation architecture in light of this to strengthen its trust chain’s security and improve the capacity to restore device trust in the case of security flaws.
Starting with Android 12.0, Android has begun providing the choice to switch from in-factory private key provisioning to a hybrid of in-factory public key extraction and over-the-air certificate provisioning using short-lived certificates. Android 13.0 is making this plan mandatory. This new scheme is known as Remote Key Provisioning.
How Does Remote Key Provisioning Work?
In Remote Key Provisioning, device manufacturers no longer give attestation private keys directly to devices in the manufacturing, alleviating the burden of managing secrets in the factory for attestation.
Each device generates a unique, static key pair, and the OEM extracts the public part of this keypair in their factory. The basis of trust for eventual provisioning is established by uploading these public keys to Google servers. The secure environment where the private key is created is the only place it ever leaves.
A device digitally generates a certificate signing request for keys it has issued, signing it with the private key that matches the public key retrieved in the factory. In order to sign the public keys and return the certificate chains, backend servers first validate the request. These certificate chains are subsequently kept in Keystore, where they will be allocated to applications whenever an attestation request is made.
When the current supply of keys runs out, or the certificates expire, this flow will continue on a routine basis. The approach protects anonymity by giving each application a unique attestation key and frequently rotating the keys themselves. This means even Google can not connect attestation keys to the specific device that made the request.
Enabling Server Certificate Validation on Android 13
The necessity for Android 13 Server Certificate Validation is somewhat complex in nature because there isn’t any simple fix. Google is making it evident that public key cryptography is necessary for safe Android surfing and is gradually becoming a standard for secure network authentication.
To cater to this, organizations running their own WPA2-Enterprise networks must provide their end users with quality technical documentation and hire extra staff at the IT helpdesk to assist whenever users erroneously configure their devices. Or, if that’s not your cup of tea, employ a device onboarding solution that enables end users to configure server certificate validation themselves.
With the proper onboarding solution, you can completely upgrade your network to EAP-TLS certificate-based authentication and benefit from its much-improved security and user experience.
Best Certificate Authentication For Android
Digital certificates are not complex, despite the prevalent belief to the contrary. On-premises implementation indeed used to be challenging and expensive, but cloud PKIs have effectively overcome such obstacles. Building PKIs now is less costly than it was ten years ago, and cloud-based alternatives are even less expensive.
There has never been any doubt that certificates offer far greater security than credentials. In contrast to the widely used EAP-TTLS/PAP protocol, which delivers credentials in cleartext, the public-private cryptography principles that underpin x.509 digital certificates enable a network that is essentially impervious to both over-the-air attacks and phishing.
Additionally, the improved security and lower cost should maintain the user experience in this particular instance. Due to the automated nature of certificate authentication, it is far more user-friendly than credential-based auth. The network handshake automatically displays the certificates stored on a device without user intervention, and there is no need to remember (or reset) passwords.
Enrolling Android Devices For Server Certificate Validation
Enrolling Android devices for server certificate validation by integrating a comprehensive PKI solution is better than paying high license fees to a public CA. Managed devices are simple to set up and enroll in, but since the majority of Android devices on a network are BYOD, the end user must be involved.
Fortunately, you can deploy a customizable configuration client with a reliable self-enrollment wizard from our BYOD onboarding solution, which helps the end user through the Android configuration process. Since our support team has done most of the complex work, setting up our Advanced BYOD Onboarding Service is incredibly simple.
The general setup instructions are shown below.
- Create an open SSID on your wireless AP or controller.
- Establish a redirect to the SecureW2 Advanced Onboarding Service home page.
- Connect your WLC to the cloud RADIUS server.
- Upload the shared secret, port number, and cloud RADIUS IP address.
 Organizations must select a redirect URL for their captive portal and link it to a RADIUS server. The Advanced Onboarding setup might be trickier when setting up and configuring a RADIUS server. However, SecureW2 products already include a world-class Cloud RADIUS server, significantly simplifying the procedure.
Organizations must select a redirect URL for their captive portal and link it to a RADIUS server. The Advanced Onboarding setup might be trickier when setting up and configuring a RADIUS server. However, SecureW2 products already include a world-class Cloud RADIUS server, significantly simplifying the procedure.
Simplify Server Certificate Validation with Android 13
Server Certificate Validation is the need of the hour, especially when you seriously want to upgrade your network security and avoid authentication failure. However, device misconfiguration is an equally risky vector of attack. Configuration should never be left to end-users for this reason, so a reliable onboarding solution is a necessity for this requirement.
You can easily configure server certificate validation for all Android devices with SecureW2’s JoinNow Connector and Cloud RADIUS; there’s no need to shell out exorbitant amounts of money for public CA licensing. With the help of our BYOD onboarding solution, you can push a configurable configuration client with a secure self-enrollment wizard that walks the user through the complex process of configuring Android.
You can book a call with us or check out our pricing page to see if SecureW2’s onboarding solutions fit the authentication needs of your organization.