Hackers acquired the personal data of over 37 million T-Mobile users, including names, dates of birth, Social Security numbers, and driver’s license information, in a recent incident that featured a password breach. The breach is regarded as one of the largest in US history, illustrating the persistent vulnerabilities of password-based security measures in the face of more sophisticated cyber attackers.
Password-based authentication paired with multi-factor authentication (MFA) has long been regarded as the gold standard for safe login in cybersecurity. However, the emergence of MFA fatigue attacks and other security flaws has encouraged many to seek other options. Azure AD CBA is one potential approach that allows enterprises to reduce MFA while simultaneously increasing user experience and security securely.
In this article, we will understand how we can easily eliminate these flaws of MFA using Azure AD CBA.
Security Concerns with Passwords Along with MFA
The biggest concern with passwords, along with MFA, is that this combination can be really tiresome and frustrating for users. Having to enter a password and a one-time code every time you log in can be time-consuming and frustrating, leading to MFA fatigue, where users get frustrated with the process and are more likely to try to find ways around it.
Additionally, password-based authentication is inherently vulnerable to a variety of attacks, including brute force attacks, dictionary attacks, and credential stuffing attacks. While MFA can help mitigate these attacks, it is not foolproof, and attackers can still use phishing and social engineering techniques to trick people into handing over their passwords.
That’s where Azure AD CBA (Certificate-Based Authentication) comes in, but before we discuss that, let’s dive deeper into MFA Fatigue attacks and ways to mitigate them.
MFA Fatigue Attacks
As we know, MFA is a security mechanism that adds an extra layer of protection to user accounts by requiring two or more forms of authentication, such as a password and a verification code sent to a user’s mobile device. While MFA is a powerful tool for securing accounts, it is not immune to attacks. One such attack is MFA fatigue.
MFA fatigue refers to a user’s tendency to lose faith in the security provided by MFA and become less vigilant in verifying their identity, resulting in a weakened security posture. Attackers can take advantage of this complacency by duping users into providing their MFA credentials, such as a verification code, via phishing, social engineering, or other means. This is really harmful because MFA is frequently seen as an impregnable security mechanism, causing users to relax their guard.
There are a few ways to avoid MFA fatigue attacks. To begin, users must be educated on the dangers of complacency and the importance of remaining alert when verifying their identity. Regular security awareness training can help users stay informed about the latest risks and best practices.
Secondly, users should be encouraged to employ more tricky MFA methods, such as hardware tokens as well as biometric authentication. These methods provide an additional layer of protection that is more difficult for attackers to bypass.
Also, companies should build fraud detection methods to identify and avoid MFA fatigue attacks. Monitoring user behavior and account activity to detect anomalies that may indicate a compromised account is one of these mechanisms.
Lastly, users should avoid duplicating passwords across numerous accounts and constantly change their passwords to lessen the possibility of their accounts being hijacked. A compromised account can be the first step toward a successful MFA fatigue attack.
Azure AD CBA
Azure AD CBA (certificate-based authentication) is a security feature provided by Microsoft in the Azure Active Directory that uses real-time authentication and access policies to protect your organization’s resources.
Azure AD CBA provides a powerful alternative to passwords along with MFA. With CBA, users are issued a digital certificate that is used to authenticate them to the network or application. This eliminates the need for passwords and one-time codes, streamlining the authentication process and making it more user-friendly.
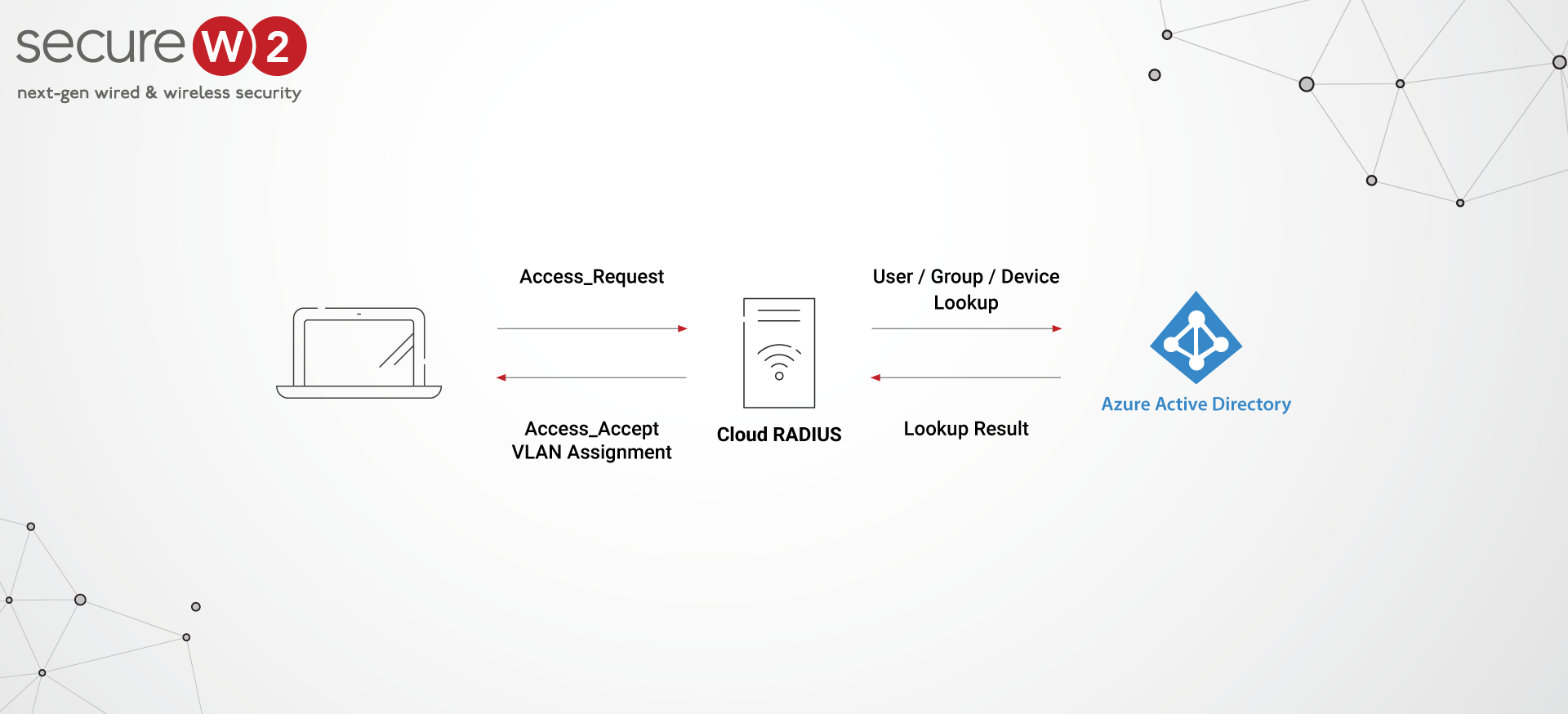
In addition, CBA eliminates the risk of MFA fatigue attacks. Users are significantly less likely to try to circumvent the authentication procedure now that a one-time code is no longer required. This means that the network or application is more secure overall.
Advantages of Azure AD CBA
Azure AD CBA contributes to passwordless authentication by letting users sign in to their personal Microsoft account without entering a password by utilizing safe means such as biometrics or security keys. CBA monitors the user’s authentication status continuously and imposes access controls depending on their risk profile and the sensitivity of the resource they’re attempting to access.
Here are some added advantages an Azure AD CBA brings to the table while ensuring a smooth shift from MFA.
Stronger Security
Stronger security is one of the key advantages of certificate-based authentication. Certificates are significantly more difficult to steal or compromise than passwords, making them a more secure authentication alternative. Certificates are also harder to guess or brute force, lowering the danger of credential-stuffing attacks and other types of password-based attacks.
In addition, certificates can be easily revoked if they are lost or stolen, ensuring that unauthorized users cannot use them. This eliminates the risk of attackers gaining access to sensitive data or systems through stolen credentials.
Greater Convenience
Another key benefit of certificate-based authentication is greater convenience. The authentication process is streamlined and made more user-friendly with certificates because users do not need to remember complicated passwords or enter one-time codes. This reduces the likelihood of MFA fatigue attacks and other forms of user mistakes that harm security.
Improved User Experience
Certificate-based authentication also provides a better user experience. Users may use certificates to authenticate to systems and apps without memorizing complex passwords or going through time-consuming MFA processes. This can increase productivity and decrease frustration, resulting in a better work environment.
Using Azure Identities with Azure AD CBA
Fortunately, it is easy to use your Azure identities with Azure AD CBA. Azure AD CBA supports several types of certificates, including user, device, and service certificates. You can generate these certificates in Azure or import them from your existing certificate authority.
Once you set up your certificates, you can roll out Azure AD CBA to your users. They will be able to authenticate to your network or application seamlessly without the need for passwords or MFA. This can improve security, convenience, and user experience, making it a win-win for everyone.
In short, certificate-based authentication offers several key benefits over passwords and MFA. With stronger security, greater convenience, and improved user experience, certificates are a powerful tool for securing authentication. By using your Azure identities with Azure AD CBA, you can roll out certificate-based authentication to your users and eliminate the need for MFA or passwords. This can improve security, reduce frustration, and increase productivity, making it a smart choice for any organization.
Native Integration of SecureW2 With Azure AD CBA
SecureW2 can integrate natively with Microsoft to give secure and simplified access to Microsoft services such as Office 365 and Azure Active Directory. Users may access Microsoft services through a single sign-on (SSO) experience, eliminating the need for numerous identities and passwords.
The native integration between SecureW2 and Microsoft allows organizations to take advantage of Microsoft services while ensuring the security of their network and data. This can help organizations reduce the risk of security breaches and minimize the impact of potential security threats. Admins can configure SecureW2 to use multiple authentication techniques such as PEAP-MSCHAPv2, EAP-TLS, and EAP-TTLS/PAP. to enable secure access to Microsoft services
By leveraging SecureW2’s certificate-based authentication and access policies, organizations can significantly reduce the risk of password-related security incidents, such as phishing, credential stuffing, and MFA fatigue attacks. If you’d want to see how SecureW2 might appear in your network, we’d be pleased to show you. Set up a free demo with our team to experience how simple passwordless can be.