As the internet continues its trend toward ubiquity, the dangers of lackluster network security have become increasingly apparent. With 10 million attacks targeting usernames and passwords occur every day it’s no wonder why so many companies are making the much-needed transition from pre-shared key (PSK) authentication to 802.1x authentication using certificates. However, historically this was only possible through the use of expensive on-premise servers, making it difficult for companies to transition to WPA2-Enterprise network security.
If you are viewing the article, then that must mean that you are currently using Okta or plan on using it. We will be discussing how to set up RADIUS authentication with Okta and use your Okta directory to enroll for certificates.
Okta can also be used with Personal Identity Verification (PIV) cards for tighter security and is compatible with certificates, easing the user experience with fewer credentials to remember and tighter security for your network. Check out how we helped a customer integrate SecureW2 with their Okta environment here.
How RADIUS Authentication Works at a High Level
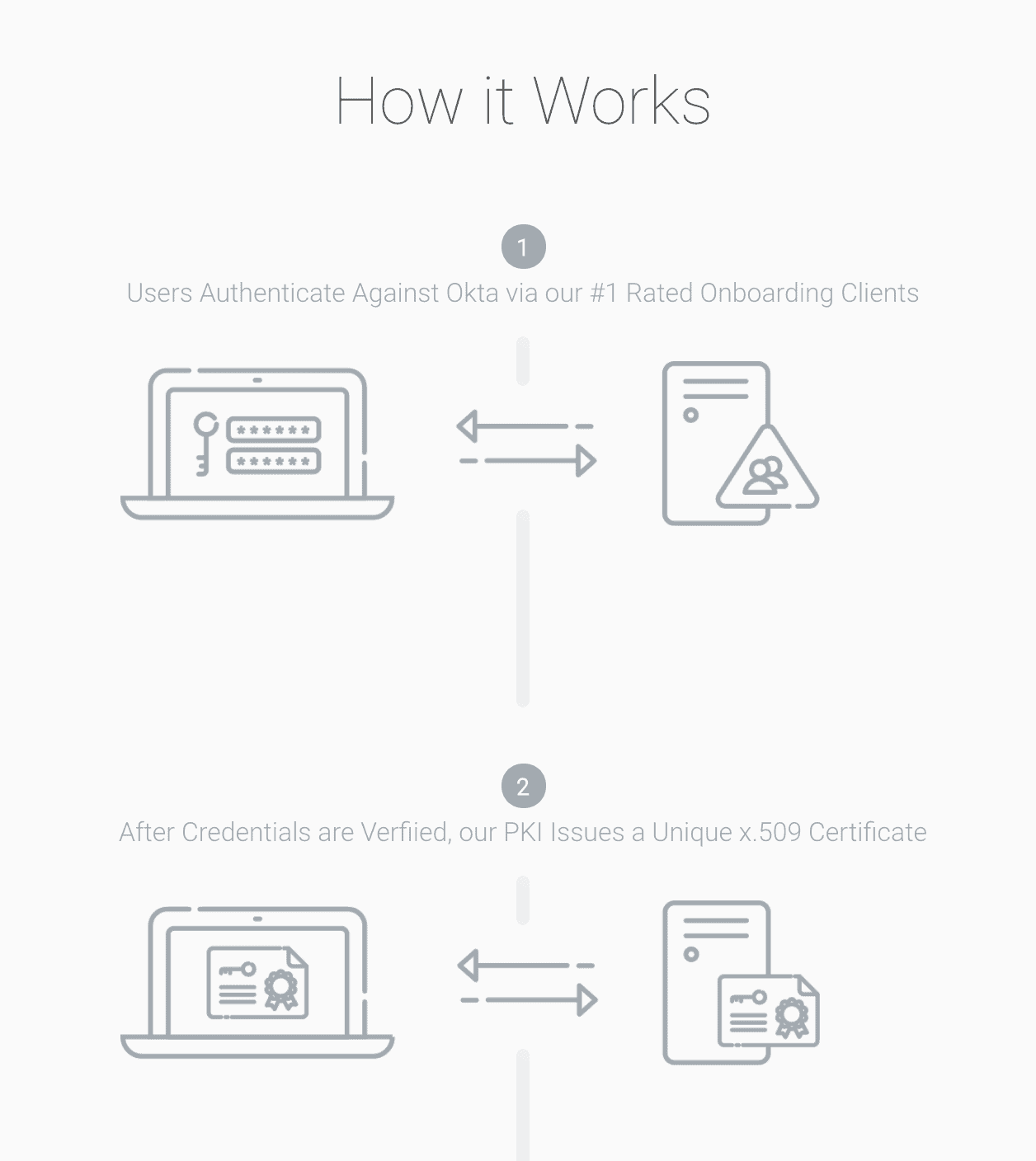
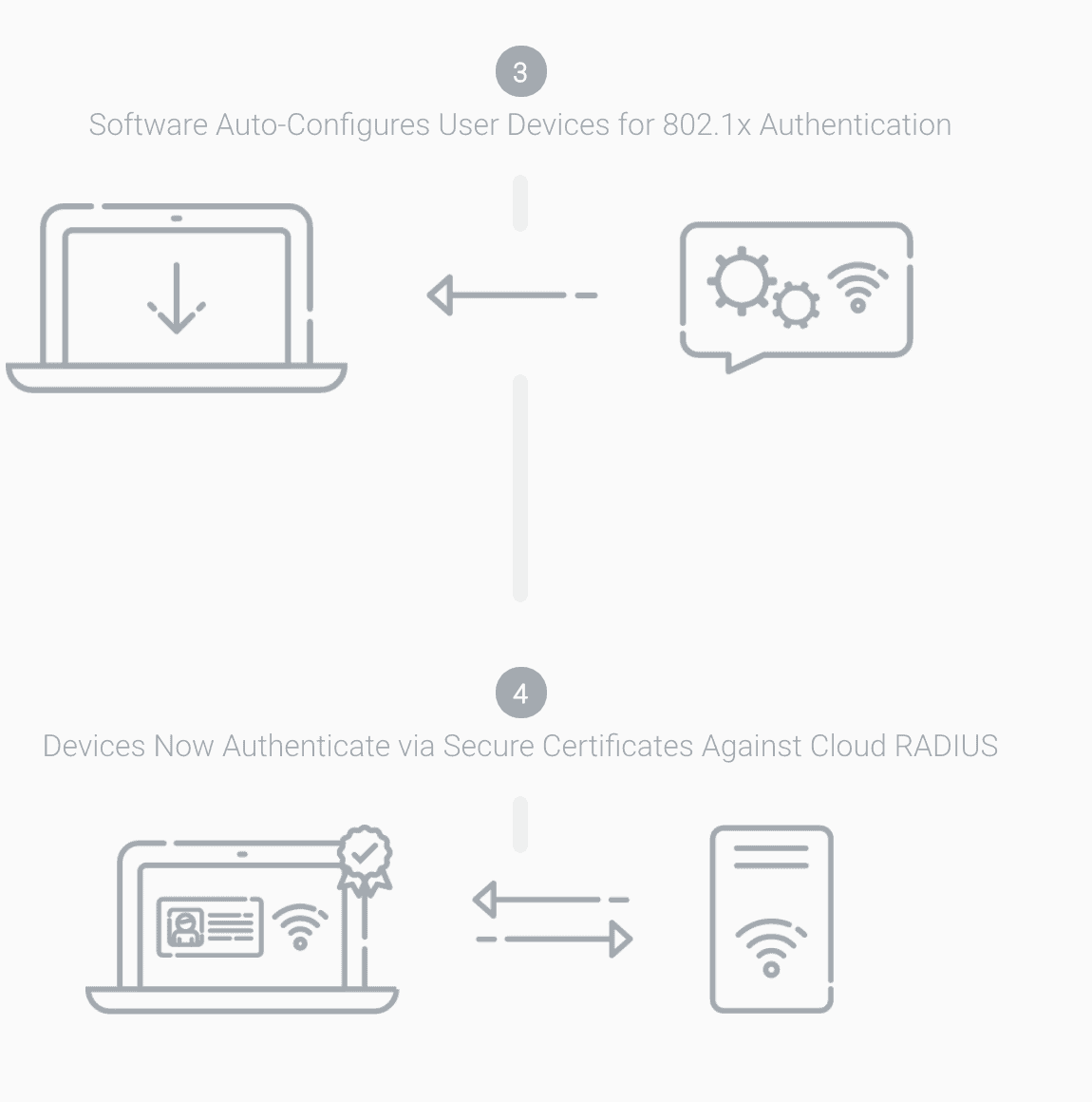
Can I Use Okta With FreeRADIUS?
Yes, you can authenticate Okta users using FreeRADIUS. If a user is valid in Okta and they present the correct authentication materials, they will be authenticated for network access.
Unfortunately, organizations are quick to jump to insecure credential-based authentication with FreeRADIUS because it’s easier to set up than alternatives. But the fact of the matter is that passwords are far more trouble than they are worth. They can be hacked, lost, or stolen and rely heavily on the user, which is the weakest link in the cybersecurity chain.
The best alternative comes from certificates, which utilize public-key cryptography so they cannot be replicated by outside attackers and are protected by EAP-TLS which eliminates the threat of over-the-air attacks.
While it is possible to configure Okta to populate your certificates with user information and authenticate them via FreeRADIUS, there are more efficient solutions. It’s difficult to distribute certificates for this configuration and will be an intensive, ongoing management process for any IT team.
The best alternative comes from SecureW2.
Create an Identity Provider in SecureW2
An IDP connects with SecureW2’s onboarding software and confirms the identity of a user. In the future, when a user provides their certificate, their identity is compared against the IDP to confirm they are an approved network user and are authenticated by the RADIUS.
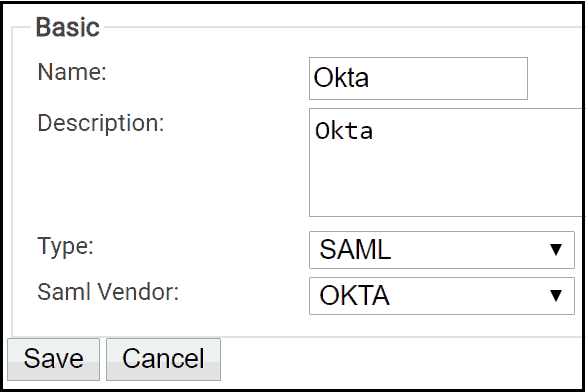
To create an IDP in SecureW2:
- From your SecureW2 Management Portal, go to Identity Management > Identity Providers.
- Click Add Identity Provider.
- For Name, enter a name.
- For Description, enter a description.
- Click the Type dropdown and select SAML.
- Click the Saml Vendor dropdown and select Okta.
- Click Save.
How To Use Okta for RADIUS Authentication
By combining Okta identity management and SecureW2’s EAP-TLS certificate solutions, network users can be easily equipped with certificates for RADIUS authentication.
Furthermore, SecureW2 has the industry’s only solution to allow user lookup in cloud directories like Okta. Our Dynamic Cloud RADIUS can make runtime-level policy decisions by referencing user attributes stored in Okta rather than relying on the information stored in a static certificate. Not only does this add an extra layer of authentication protection, it reduces the reliance on extensive certificate management.
Create a SAML Application in Okta
- From your Okta dashboard, go to the Dashboard page.
- Under Shortcuts, click Add Applications.
- Click Create New App.
- In the Create a New Application Integration prompt:
- Click the Platform dropdown and select Web.
- For Sign on method, select the radio button for SAML 2.0.
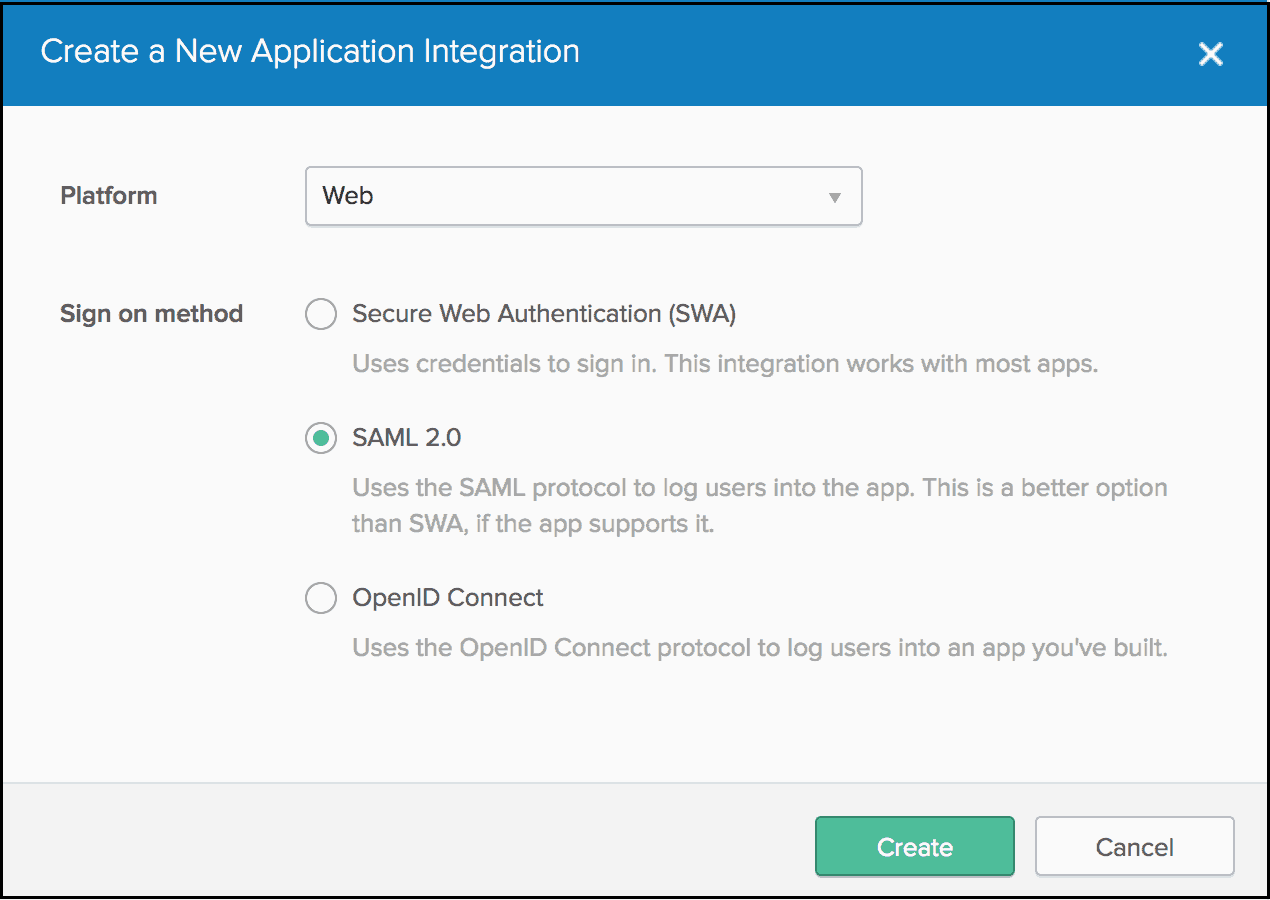
- Click Create.
- On the 1 General Settings step, for App name, enter a name.
- Click Next.
- In a new browser tab/window, log in to your SecureW2 Management Portal and go to Identity Management > Identity Providers.
- Click Edit for the IDP you created in the section “Create an Identity Provider in SecureW2”.
- Select the Configuration tab.
- Copy and paste as follows:
- From SecureW2, copy the information for ACS URL and EntityId, and
- Paste respectively into Okta (2 Configure SAML step) for Single sign on URL and Audience URI (SP Entity ID).
- Click Next.
- On the 3 Feedback step, for Are you a customer or partner? select the appropriate radio button.
- Click Finish.
Configuring RADIUS Authentication for Okta Users
Now, you need to enter in the RADIUS information. For this guide, we are using a Meraki Access Point to show how Cloud RADIUS integrates with an access point. However, Cloud RADIUS is vendor-neutral and works with any Enterprise AP vendor.
- Under Wireless, select Access control
- Under Network access change it from the default value of Open (no encryption) to WPA2 Enterprise with “my RADIUS server”
- For the WPA encryption mode, select WPA2 only
- In the Splash page section, leave it set to None (direct access)
You can find the details about your Cloud RADIUS when you go to AAA Management and AAA Configuration. Here you will see a Primary IP Address, Secondary IP Address, Port Number, and a Shared Secret.
- Copy the Cloud RADIUS information and paste it back into your Access Point Provider under RADIUS Servers, click the green link to Add a server
- Enter in the Primary IP Address, Port Number, Shared Secret respectively
- You will need to perform the same steps for the Secondary IP Address by entering the Secondary IP Address, Port Number, Shared Secret
- Scroll down and click Save changes
Enrolling BYODs for Okta
SecureW2 automates the device onboarding process for end-users with our #1 rated 802.1x onboarding clients (as shown in the section ‘How it Works’), eliminating the risk of user misconfiguration and MITM credential theft.
The SecureW2 solution redirects users to the Okta Single-Sign-On where they enter their credentials, and then SecureW2 enrolls their device for a certificate and configures it for 802.1x.
Now, organizations no longer have to be tied up managing outdated hardware, like their on-premise Active Directory servers. Devices only need to be authenticated once and are set until the certificate expires.
Enrolling Managed Devices for Okta
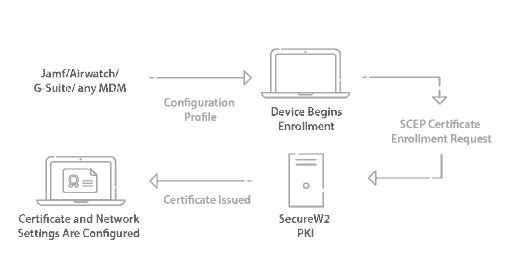
For managed devices, many organizations with Okta use Microsoft’s MDM, Intune. SecureW2 integrates with Intune through our Gateway APIs. You can use the gateway to push policies and configuration settings onto Intune devices so they can auto-enroll themselves for 802.1x digital certificates automatically, and IT admins don’t need to lift a finger to get managed devices configured for 802.1x.
RADIUS Authentication with Okta and SecureW2
Using SecureW2, your organization can have a top of a line, RADIUS-backed network fully functional in a matter of hours. Paired with a variety of useful certificate management features available through our Cloud Managed PKI Service, employing Public Key Cryptography on your network has never been easier. Plus an amazing support team that’s ready to assist you with any help you may need. We easily work with all cloud-based SAML providers to eliminate any headaches usually associated with integration. Check out our Okta Solutions page to see how we can boost your network security.



