Cyberspace is a rapidly evolving world, and in order to keep up with the pace, tech organizations must evolve at a similar speed. The cyber performance enterprise Riverbed recently analyzed Windows 11 readiness in its most recent report and discovered that 34% of currently in-use devices are not capable of operating Windows 11.
That’s alarming, considering the fact that updating your operating system is a must for minimizing the risk of cyber threats. Microsoft recently released a list of guidelines for installing/updating Windows 11 that contains software and hardware requirements for the same.
Here we will discuss a vital cog in the “hardware requirements list” that need to be on your system for installing Windows 11.
What is a TPM (Trusted Platform Module)?
A TPM (Trusted Platform Module) is a cryptoprocessor that enhances the security of any hardware-based system by generating and securely storing cryptographic keys. It is usually located on your system’s hardware (primarily the motherboard), occasionally independent from the memory and the primary CPU.
TPM is the new talk of the town, especially after Microsoft announced the hardware requirements of the recently released Windows 11. Microsoft has officially announced that enabling TPM 2.0 is mandatory for installation or migration to Windows 11.
So, network administrators are now checking their devices to see if they were manufactured with a TPM and whether they are sufficient for an OS upgrade.
How Does a TPM Work?
When appropriately executed, software security is an effective instrument for preventing hackers from accessing a network. However, the software is “elastic”, its code can always be tampered with, allowing trespassers to access private data.
TPMs, on the other hand, are hardware chips with various security safeguards that prevent tampering and malicious software from interfering with their security features.
There are several configuration options for TPM-based keys. One option is to avoid a TPM-based key being used outside the TPM. Since the key cannot be duplicated and used without the TPM, this helps to lessen phishing attempts.
TPM-based keys can also be configured to demand an authorization value.
Types of TPMs
There are basically four kinds of TPMs, according to the Trusted Computing Group (TCG), which regulates TPM guidelines.
- Discrete TPM
- Integrated TPM
- Firmware TPM
- Software TPM
TPMs can be physically included in the primary CPU or operate as software in an exclusive environment called firmware.
Virtual TPMs are a little different. They are entirely code-driven. A virtual TPM is a creative technique to deploy a TPM in a cloud setting. The virtual TPM, an integral part of the cloud-based architecture, gives every virtual machine a unique set of commands, much like a conventional TPM would.
The TCG cautions that due to its vulnerability to manipulation and any potential operating system security flaws, real-time usage of this is not encouraged.
What are the functions of a TPM?
The most widely employed TPM functions include key generation and usage, as well as measures of system security. The boot code that is loaded during a system’s initial configuration, such as the firmware and OS version components, may be examined and saved in the TPM.
TPM also creates, keeps, and restricts the usage of cryptographic keys by utilizing the burnt-in RSA key of the TPM to authenticate platform devices utilizing TPM technology. It also assists in ensuring system security by recording various security metrics.
You can easily deploy or install certificates on devices already using a TPM. Once a device has been configured, you can not export the RSA private key for a certificate linked to the TPM.
You can also use TPM as a substitute for Smart Cards, which lowers the price of production and distribution of smart cards.
Firefox and Chrome web browsers use a TPM for specific, more complex tasks, such as keeping track of websites’ SSL certificates. TPMs are operated by a wide range of consumer electronics outside PCs, including printers and linked home devices.

Does Your Device have TPM 2.0?
The answer is probably “Yes,” for anybody who recently purchased a PC or desktop. Most PCs built in the last decade or so should already be equipped. The upgrade could be trickier for someone who wants to migrate to Windows 11 and has designed or rebuilt their own Windows desktop.
There are a few methods for determining whether your present machine has a TPM.
- Open the Start
- Navigate to the Windows Security
- Click the Device Security
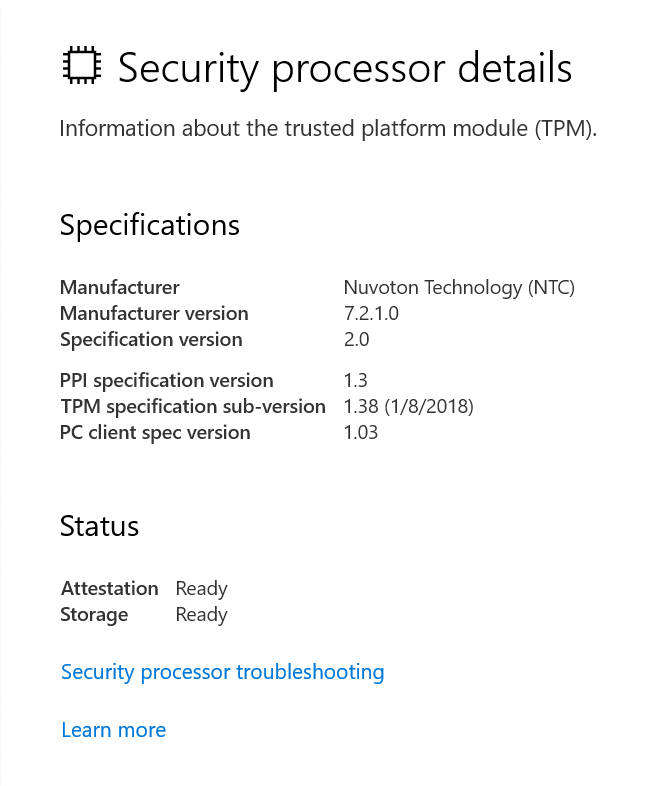
An additional window that displays the presence of a TPM on your device will then appear there. It must display the Security Processor with a little green checkmark next to the icon. You can not install the TPM if that Security processor icon is missing.
If you don’t see anything, you can also type Run by pressing WIN + R into the Start search box, followed by tpm.msc, and press Enter to see if a TPM is installed.
The window for “Trusted Platform Module (TPM) Management on Local Computer” should appear as a result. If the message “Compatible TPM cannot be detected” appears, your machine either lacks a TPM or has a TPM 1.2 chip, but the BIOS has not activated it.
Unfortunately, Windows 11 really requires TPM 2.0 even if TPM 1.2 is enabled in the BIOS.
Why does Microsoft Require a TPM?
We have already discussed that Microsoft has made it mandatory to have TPM 2.0 installed on your system if you want to continue enjoying the services of its latest versions of Windows. Here we want to speculate the motives of Microsoft behind this decision and understand how it might affect your current network infrastructure.
We have observed that Microsoft is serious about going ahead with passwordless network infrastructure for apparent reasons, and TPM can ensure passwordless login to multiple apps, particularly cloud infrastructure.
TPM is basically a smart card, and they’re pushing certificate-based authentication (CBA) for going passwordless in the long run.
In an effort to resemble Apple, Microsoft places a strong emphasis on privacy and security. It upgrades Windows 11 to bridge the security gap between desktop and mobile devices (mobile devices have more in-built security and are generally better protected).
Since less expensive devices (such as cheap laptops) now have native defenses, which usually raises the bar for security in general, this move also focuses on democratizing security and device trust in the network perimeters.
Similar to how preinstalling Windows Defender on Windows changed the dynamic for Windows security in the past, this action of requiring a TPM on your system has the potential to enhance the baseline security of your network infrastructure in the future.
Go Passwordless with SecureW2
We have seen how tech giants like Microsoft and Google are actively implementing measures to minimize dependencies on credentials. On a similar note, SecureW2 has been pursuing the goal of Zero Trust by reducing the dependencies of cyberspace on passwords by offering superior passwordless certificate-based authentication in the cloud.
Some of our products, like Cloud PKI and Cloud RADIUS, have enabled many organizations to go passwordless without any hassle. The great thing about our products is that they can be easily integrated into any operating system or managed device. Set up a free demo with our team to see firsthand how easygoing passwordless can be.