Accessing Wi-Fi networks easily and remotely has become a critical interaction point between organizations and their remotely located users. The captive portal is at the center of this process. It is a doorway that not only gives people access to the internet but also gives organizations the power to connect and filter out suspicious SSIDs to secure the device.
Imagine you’re at a busy cafe, ready to get to work with a cup of coffee in hand. When you join the cafe’s Wi-Fi, a window pops up asking for your passwords or agreement to the terms before giving you access to the internet. This Pop-up is what a captive portal is all about. It is an entry point that stands between you and the Wi-Fi network.
Captive portals are often ignored, but they give businesses a chance to increase brand interaction, improve network security, and meet legal requirements. This article explains the best practices for captive portals that safeguard users and businesses while onboarding.
Introduction to WiFi Onboarding and Captive Portals
Wi-Fi onboarding refers to incorporating new users into a network, facilitating seamless access and utilization of Wi-Fi services. A captive portal refers to a webpage that individuals visit before gaining access to the internet, usually necessitating identification or acceptance of terms and conditions. The initial contact establishes a secure connection, which is crucial for effectively managing network access.
Many organizations create custom landing pages in their captive portals using tools such as JoinNow MultiOS, like in the examples pictured below. Custom landing pages ensure users know they’re in the right place, provide branding opportunities, and can communicate the next steps to the users.
Risks of Inadequate Onboarding
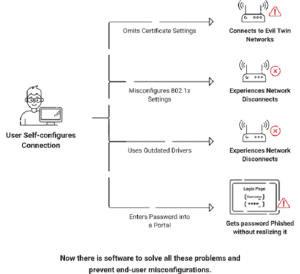
Inadequate onboarding procedures present various potential risks that can adversely affect the user’s experience and the network’s security. One notable concern is security vulnerabilities Onboarding provides a crucial chance to set up and secure devices. Without adequate onboarding technology, hacked devices might enter the network and spread malware. User connections to malicious or “evil twin” access points can be reduced by addressing server certificate checking during onboarding.
Another threat that should be considered is the possibility of user dissatisfaction. Complicated onboarding procedures or inadequate communication might result in user discontentment, generating frustration that could result in higher support inquiries. An uninterrupted onboarding process accompanied by effective communication is crucial in mitigating such challenges and fostering favorable user perceptions.
Moreover, poor onboarding procedures contribute to an increased risk of network misuse. The absence of adequate authentication increases the probability of unauthorized access, potentially resulting in the improper utilization or exploitation of network resources. Effective communication throughout the onboarding process is a proactive strategy to mitigate the potential for unauthorized access and its related risks.
Organizations can augment network security, user contentment, and overall network efficacy by comprehending and mitigating these risks through efficient onboarding and captive portal approaches.
Onboarding Differences in Managed vs. Unmanaged Devices
Knowing the differences between how Wi-fi onboarding works in managed devices and unmanaged devices and BYODs is paramount. IT managers usually have more say over adding new users in a managed device setting. They can set up devices with policies, digital certificates, and settings before they join the network through their Mobile Device Management (MDM) platform. If you’re configuring managed devices for certificate-based authentication, you can use your MDM to push digital certificates to devices through the simple certificate enrollment protocol (SCEP). This controlled method makes the onboarding process go more smoothly and requires less user input.
However, a different onboarding plan is needed for devices that are not managed, like personal smartphones and computers. It’s important to communicate clearly and directly so that users can follow the steps needed for identification and network access.
By understanding and handling the differences between managed and unmanaged devices, organizations can adapt their onboarding methods to various situations, ensuring Wi-Fi is safe and easy to use.
Best Practices for Wi-Fi Onboarding with Captive Portals
1. Clear and Concise Communication
Effective Wi-Fi onboarding captive portals rely on clear and concise information. This practice accommodates those proficient in technology and assists others less knowledgeable about technology throughout the self-enrollment process.
Graphics are very important for helping users through the Wi-Fi onboarding process. The style should make people feel like they are in the right place and show them what to do next. Visual elements like buttons, icons, and others should prioritize clear information and avoid misunderstandings as much as possible.
The captive portal should provide information about how users can get help if they encounter problems or mistakes during setup. Making it clear who to call for assistance helps users deal with problems quickly, which can reduce stress.
2. Use CNA Breakout Technology
A CNA or Captive Network Assistant is a feature of several standard operating systems meant to streamline and secure the process of onboarding guest Wi-Fi networks. A limited browser pops up whenever the user connects to an open SSID. The following OSs have a native CNA:
⦁ Android
⦁ iOS,
⦁ macOS
The strongest security measure of a CNA also makes it unsuitable for onboarding users to Wi-Fi. A CNA doesn’t allow anything to be downloaded and installed on the secure device; that’s great for preventing spoofed SSIDs from installing malware on unsuspecting devices. However, it prevents us from downloading the configuration payload for automatic onboarding to secure Wi-Fi.
Working around CNAs isn’t very simple, unfortunately. Even if the user exits the CNA browser and opens a new browser window, it won’t redirect them to the captive portal you set up. They would have to try to navigate to an HTTP address specifically – and all of the typical sites a user might try to access are almost certainly HTTPS. It’s worse on Android – disconnecting from the CNA completely disconnects you from the limited internet.
The only proper solution to onboarding mobile devices and macOS to Wi-Fi is SecureW2’s industry-first CNA Breakout solution. The solution detects the user is in the CNA-limited browser. It presents instructions to the user alongside a button automatically opening the Captive Portal in a full, non-CNA browser. For more information about CNA Breakout, contact our specialists here.
SecureW2’s JoinNow MultiOS changes how safe Wi-Fi onboarding works when a Captive Network Assistant (CNA) is present. JoinNow MultiOS optimizes the process for different operating systems when it comes across a CNA, such as public Wi-Fi networks. It streamlines the onboarding process by working in the background and automatically fills in login details or certificates so that users don’t have to interact with the captive portal themselves. This ensures the onboarding process is smooth and uniform across all devices and meets strict security standards.
3. Use Hidden SSIDs for Simple Onboarding
The first step in automatic onboarding is always getting the users to connect to your SSID. Depending on the location, though, they might be bombarded with 10 or 20 potential SSIDs when they open their network settings. That can be overwhelming, especially for users who don’t know what to look for.
You can hide all of the SSIDs you control besides the onboarding SSID. This won’t affect your existing network users – they can find and connect to the hidden SSIDs with no issues. The new users to be onboarded will only see the onboarding SSID, eliminating confusion about which network they need to connect to.
4. Onboarding Network Segmentation with VLAN
Most organizations already use VLANs to segment classes of users and implement Group Policies. It’s an easy way to restrict access to specific resources and enable permissions to others with broad strokes.
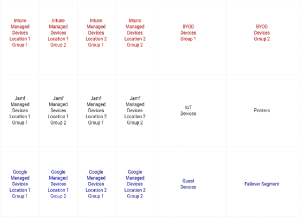
Also, having your onboarding SSID on a separate physical or virtual network is a good security practice. Onboarding is a complicated process, so there are a lot of potential nooks and crannies a bad actor might exploit. It’s better to play it safe and keep your primary network safe by keeping it separate from the onboarding network. SecureW2’s Onboarding software can roll onboarding into user segmentation, automatically sorting newly onboarded users based on attributes from your directory. Appropriate network privileges will be assigned automatically, ensuring a smooth and safe onboarding experience.
Network Segmentation
Incorporating network policies into VLAN structures accomplishes two goals. First, it creates a dynamic setting where users can access resources suited to their roles. This makes sure that resources are used efficiently. Second, this way of breaking up the network protects it from potential threats by limiting attempts to get in without permission to certain segments. Combined with our onboarding solution, this approach speeds up the onboarding process and helps build a resilient network framework that protects data and meets legal standards.
VLAN segmentation is very helpful in various settings such as schools, universities, corporations, and so on because it lets the network segmentation meet many different needs. For example, imagine a school where students, teachers, the administration, and guests had separate VLANs. This setup solves problems like network congestion during class hours, increased security by separating sensitive administrative data into segments, better bandwidth allocation for educational resources, and a separate VLAN for guest access. This makes network management easier, safer, and more efficient.
Strategic Investment in Crafting a Reliable ACL
Creating a well-structured Access Control List (ACL) or whitelist is often ignored when setting up a captive Wi-Fi onboarding site. Developing a complete ACL may be time-consuming, but its importance cannot be emphasized. An Access Control List (ACL) is an important filter that lets only authorized devices and people into your network while stopping possible threats. However, building an ACL that can’t be broken takes careful planning and testing to ensure it works and is complete.
What you enter in your ACL is critical to keeping your network safe and working well. It’s the line between secure connections and things that could go wrong. So, it’s essential to put in the time to make a complete list of many attributes, such as device IDs, IP addresses, users, and so on. But it’s important to remember that designing a reliable ACL is only the first step. It is also essential to do thorough testing to catch any mistakes or holes that could accidentally give entry to unauthorized entities. During this testing process, you have to be patient and pay close attention to every detail because any unexpected opening could be used by online threats to get in.
To assess the efficacy of your ACL, you may use various testing methods, including simulation, auditing, and logging. The simulation entails establishing controlled situations to evaluate the ACL’s reaction to various access attempts. Auditing thoroughly examines the ACL’s setup and configuration to guarantee compliance with security criteria. Logging records and analyses of network events make spotting abnormalities or unauthorized access attempts easier. SecureW2’s Cloud RADIUS event logs are an excellent example, offering real-time visibility into authentication events, facilitating the detection of anomalies, and enhancing the ACL validation process.
SecureW2’s onboarding products are a great example of how to onboard Wi-Fi because our unique ACL backs them safely. We have spent years improving and assembling a reliable ACL, using our deep industry knowledge and hands-on experience. This careful work ensures that the resources in the ACL are complete and up-to-date. Our hard work makes it easier to set up ACLs and makes networks safer by making a list of approved entities. This level of dedication shows how important it is to put time and knowledge into building an ACL that acts as an impenetrable line of defense to protect your Wi-Fi network and the privacy of your users.
Easy Wi-Fi Onboarding With SecureW2 JoinNow
A good onboarding process is simple, secure, and streamlined. The user should hardly be aware they’re being onboarded, and IT should be hardly involved. A well-configured Wi-Fi captive portal can head off many of the issues commonly encountered in the onboarding process, so getting this first step right is critical. It establishes a foundation for the user’s future network experience and the security of your network.
JoinNow MultiOS stands out as the finest self-service onboarding software, known for its easy setup. Misconfigurations no longer happen, which gives network managers a great deal of peace of mind. From unmanaged devices to bring-your-own-devices (BYODs), this software simplifies the process for end users with just a few clicks and ensures that every setup is correct. It works with the most popular operating systems and offers guided user flows where they are needed to make things easier. It can simultaneously set up unique network accounts and request certificates, allowing safe authentication without a password.
In a world where network security and speed are the most important, SecureW2’s JoinNow MultiOS has proven the best option. It can make onboarding easy, safe, and focused on the user. This makes it possible for users to be more productive and for the network to be more secure. Contact us to learn more.