Ensuring the security and integrity of a business’s data and network infrastructure is of utmost importance, and thus safeguarding the local network is imperative. The Wi-Fi network serves as the primary access point to the internet and cloud-based applications and services, necessitating the need to prioritize data protection regardless of its physical storage location on the device.
In the event that one’s Wi-Fi network lacks adequate security measures, it may be susceptible to hacking, thereby resulting in unauthorized entry into cloud-based data. It is imperative to bear in mind that upholding cybersecurity is not a singular event but rather a continuous undertaking, ideally encompassing the subsequent measures, such as:
- a regular evaluation of your network security rules;
- the updating of software and firmware; and
- the education of employees on best practices.
The expansion of cloud computing is accompanied by a parallel rise in security vulnerabilities. Many companies place a strong emphasis on safeguarding their tangible resources, yet frequently neglect to secure their local area networks (LANs). It is imperative for customers to exercise greater vigilance with regard to their data being stored on cloud-based services, such as Google Drive or Office 365. However, the integrity of an organization’s data may be jeopardized despite its storage in the cloud.
This article will discuss several Layer 2 attacks and their countermeasures in the context of networks protected solely by a pre-shared key (PSK).
PSK Networks and Why They’re Vulnerable
With the shift to cloud-based services, in-network storage is becoming rarer. Instead of storing shared information on a local area network, companies are increasingly turning to the cloud. In addition, modern programs can operate without antiquated hardware or server room.
The likelihood of adopting Google Drive or Office 365 for file storage exists even if you are still using Microsoft Office. Your company’s network stores next to nothing in terms of data. What is the big issue if a hacker breaks your PSK and gains access?
In the cloud, all the good stuff is hidden behind another firewall. While these assets are adequately protected, a hacker who obtains access to your network may do extensive harm very rapidly. Such a situation renders your network vulnerable to a string of attacks, including the following types:
- Over-the-Air (OTA), especially Man-In-The-Middle (MITM)
- Brute force attacks using free security tools like Aircrack-ng
- Simple dictionary
- A multitude of Layer 2 attacks
- VPN+Firewall on PSK creates more attack vectors
- Password theft/loss
- Phishing
Pre-shared keys (PSKs) pose a security concern when used as the initial line of defense. By checking the wireless settings of a connected Windows device, an attacker who has previously acquired access to your network may see the PSK in plain text.
A PSK has several problems, not the least of which is its insecure cryptographic foundations. Vulnerabilities associated with humans are equally numerous and more apparent to the average person. A dissatisfied worker might leak a PSK, but even a happy worker poses a danger if they lose track of a laptop or smartphone linked to the network.
One such prominent human vector of attack is phishing efforts that lead to compromised computers. Let’s discuss several types of Layer 2 attacks on networks in detail.
What Are Layer 2 Attacks?
Switches may be found in the data connection layer, which is known as Layer 2. Its primary function is to ensure that frames are formed correctly. Also, it is a collective term for technology located below Open Systems Interconnection model (OSI) layers 3 and 4.
Layer 2 attacks focus on network equipment operations and exploit vulnerabilities in hardware switches, routers, and ports exposed by unsecured administrative settings or insufficient access control mechanisms in company operating systems. These cyber-threats attack the devices, making prevention impossible without preemptive steps.
Possible Layer 2 attacks on your network include:
1. Address Resolution Protocol (ARP) Attacks
A hacker may execute an ARP attack by imitating a device and routing communications to oneself to get access to user data rather than the intended destination. Hosts on a network need to know each other’s IP and MAC address to transmit and receive data from each other’s devices.
By masquerading as Host B, the hacker can access the network. To trick Host A into thinking he is Host B, he sends a message in which he pretends to be the latter. As a result, the attacker will get communications meant for Host B from Host A. The hacker is now acting as a Man-in-the-Middle (MITM) and serving as Host A’s and Host B’s first point of contact. These are primarily used in very sophisticated cyberattacks and espionage.
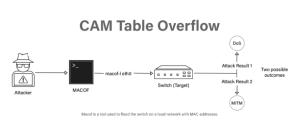
2. Content Addressable Memory (CAM) Table Overflow Attacks
A CAM Overflow Attack involves a hacker connecting to one or more switch ports and running code that spoofs out the ports with thousands of MAC addresses. After the switch’s CAM database is full, no space for additional MAC addresses is left. As a result, it crashes, causing a deluge of brand-new host connections to overwhelm the switch’s infrastructure. Using a CAM attack, an attacker may turn a switch into a hub and perform man-in-the-middle assaults or eavesdrop on conversations between hosts.
3. Spanning Tree Protocol (STP) Attacks
When used in a switched network, Spanning Tree Protocol (STP) helps to minimize broadcast traffic storms by ensuring that bridging loops are not created. First, a root switch is selected based on the lowest configured priority in an STP network. Then, it identifies additional controls and picks the root bridge. After establishing the root bridge, the network anatomy is constructed based on its connectedness.
An STP attack occurs when a hacker or attacker forges the structural root bridge. They have to broadcast a new configuration to force the STP to recalculate. Every time a root bridge is changed, an STP recalculation may cause an interruption.
4. Spoofing Media Access Control (MAC)

Network attacks may be carried out using MAC spoofing by exploiting flaws in the MAC authentication bypass scheme. As a result, it is often recognized as one of the first attacks in cyber history. While a device’s MAC address is only a (usually temporary) serial number identifying a computer, it may be easily spoofed or altered without any difficulty. MAC spoofing involves the attacker establishing illegal access points or impersonating an access point to steal user credentials.
In the event that a device unintentionally shares its network with an unauthorized individual, there is a possibility that the individual may gain unauthorized access to the entire network. Mitigation of such attacks can be achieved through the implementation of measures such as port blocking, firewall establishment, and utilization of advanced authentication methods, including multi-factor authentication (MFA) and digital certificates.
5. Switch Spoofing
Like a local area network, a switch typically waits for approved users or devices to connect. In contrast, a spoofing attack involves a hacker setting up a computer to masquerade to be a switch. The attack simulates a trunk connection to the controller using the Inter Link switch (ISL) or 802.1Q in conjunction with the Dynamic Trunking Protocol (DTP).
Switch spoofing can occur during interface negotiation with a trunk. Connecting a rogue switch to a switch port is another method of conducting a switch spoofing attack. The most straightforward technique to avoid a basic switch-spoofing attack is disabling DTP and manually activating trunking on the needed ports.
6. Double Tagging

Another kind of VLAN-hopping attack, known as a Double-Tagging VLAN attack, is accomplished when the attacker establishes a connection to the native VLAN of the trunk port. As many switches support 802.1Q tagging and removal, this attack often only travels in one way. An attacker modifies the first packet by adding new VLAN tags to the existing framework. The outer tag represents the victim’s VLAN, while the inner tag represents his original VLAN.
The intruder’s computer must use the same VLAN as the trunk. Therefore, only switch ports with native VLANs are vulnerable to a double-tagging attack.
7. Cisco Discovery Protocol (CDP) Reconnaissance
Cisco Discovery Protocol (CDP) is a proprietary protocol that Cisco devices may use to auto-configure a network and find other Cisco devices. Auto-configuration streamlines the onboarding process. Yet, information from devices that CDP is broadcasting across its network can be readily sniffed out by attackers.
A CDP is not authenticated, allowing an attacker to create and transmit forged packets through his linked CDP device. If a hacker gets into your router through Telnet or SNMP, they can use CDP data to figure out the Layer 2 and Layer 3 topology of an organization’s network.
The most effective technique to prevent a CDP attack is deactivating it on any device that may not require it.
8. Dynamic Host Configuration Protocol (DHCP) Spoofing
In DHCP spoofing, a hacker assumes the identity of another user (a DHCP server). DHCP is a commonly used protocol that supplies users with information and other data. Therefore, any loss of DHCP management might endanger the entire network.
A hacker orchestrates a DHCP spoofing attack on a network by installing a malicious DHCP server. When a client accesses a network and requests an address, the quickest DHCP server receives the initial request. If the malicious server answers to a user first, it may easily assign an address and take control of the gateway device it selects. Unfortunately, there are no infallible solutions for preventing DHCP spoofing.
The Benefits of Protecting Your Local Network With Certificates
Hackers need to be stopped from entering your local network in the first place if you want to avoid Layer 2 attacks. This is the most effective technique to stop such attacks from happening. That means using a more secure authentication method than a pre-shared key, and certificates are an excellent alternative.
Digital certificates offer a few significant benefits when used to secure your local network:
- Secure authentication
- Faster authentication
- Better end-user experience
Secure Authentication
Certificates use public-private key encryption to encrypt all data transferred across a network using EAP-TLS, which is considered to be the most secure of all protocols. A rising number of certificates improve web security by linking user identities to their devices. This is especially important now that more people than ever are bring your own devices (BYOD) into the network.
Faster Authentication
Certificates eliminate the need to remember several passwords and credentials to access a network, which results in a significant savings of both time and effort. Not having to manually enter a password every time you log in to a network also streamlines the process of getting access.
But reducing the end-user’s interactions isn’t the only way certificate-based authentication is faster. Fewer packets must be transmitted during certificate-based authentication than traditional credential-based authentication, further streamlining the login process.
Better End-User Experience
Using certificates improves the overall experience for the end-user in multiple ways. The first difference is fewer manual interactions — end-users no longer need to type out their passwords whenever they need to log in, saving them time.
Another improvement is the lack of password-related disconnects. We’ve all had the experience of losing access to a resource — whether it’s an application or a website — when our password expires after a few months. Unfortunately, many organizations set up a similar standard for their Wi-Fi network, disconnecting hundreds or even thousands of users when passwords expire. This is no longer the case with certificates, as end-users can have credentials set to renew before they expire automatically.
Prevent Layer 2 Vulnerabilities Using Digital Certificates
The transition from conventional WPA-PSK to Certificate-Based WPA2-Enterprise with 802.1X authentication may appear cumbersome, but it is not. Implementing the EAP-TLS network authentication protocol on your network can assist in converting PSK to digital certificates and aid in configuring the certificate enrollment of the device.
Today, digital certificates are robust, secure, and automated. With SecureW2’s turnkey solution, you can easily upgrade your infrastructure. We have custom solutions for organizations of any size. Choose the appropriate option by clicking here.