Encryption is the systematic process of converting plain, readable information, or data, into an unreadable format to prevent unauthorized access. This process is achieved by implementing a set of rules known as an encryption algorithm, using an encryption key. This transformed information can then only be accessed, or decrypted, by someone who possesses the corresponding decryption key.
This dual-key mechanism forms the backbone of many encryption techniques, including the RSA encryption algorithm. Encryption aids in protecting confidentiality and maintaining the integrity of sensitive data, effectively reducing the risk of data breaches and cyber attacks.
Types of Encryption
Encryption methods can be broadly classified into two categories: Symmetric and Asymmetric Encryption. Symmetric encryption, or single-key encryption, uses the same key for both encryption and decryption processes. This method is simple and fast but suffers from the issue of key distribution – both parties need to have the same key, and transferring this key securely can be challenging. On the other hand, asymmetric encryption, or dual-key encryption, overcomes this hurdle by using a key pair – a public key for encryption and a matching private key for decryption.
Asymmetric Encryption
Asymmetric encryption, also known as public key cryptography or public key encryption, is a type of encryption where two different keys, which are mathematically linked, are used. One of these, known as the public key, is made freely available to anyone who needs it. The other key, called the private key, is kept confidential by the owner and is never shared. In this dual-key system, a message that is encrypted using public keys can only be decrypted using the corresponding private keys, and vice versa.
Components of Asymmetric Encryption
A significant component of asymmetric encryption is the key pair consisting of the public and private keys. The public key is made publicly available and utilized for the encryption process, while the private one remains with the user and is employed for decryption. It’s essential to note that these keys are intrinsically linked mathematically; even though the public key is openly distributed, it’s not feasible to use it in determining the corresponding private key. This ‘one-way’ nature of the key pair ensures the security and integrity of the encrypted data.
Applications and Use Cases of Asymmetric Encryption
The practical applications of this encryption are diverse and wide-ranging. Serving as a cornerstone in various digital security protocols, it is widely utilized across numerous fields, such as online banking and secure email services to ensure the confidentiality and integrity of the exchanged data. E-commerce platforms also make significant use of this encryption for secure payments, ensuring that customer’s confidential information is kept secure. Virtual Private Networks (VPNs) also leverage asymmetric encryption to establish secure connections for remote access to a private network.
RSA Encryption
RSA encryption, a type of public key cryptography, is one of the encryption algorithms that employ asymmetric encryption. Introduced in 1977, RSA was named after its inventors—Ron Rivest, Adi Shamir, and Leonard Adleman. Pioneering the field, it was the first of its kind to be able to serve both purposes of encrypting data for confidentiality and creating digital signatures for integrity and non-repudiation.
RSA is founded on the concept of number theory and relies heavily on the computational difficulty of factoring large prime numbers. An RSA key pair, composed of a public and private key, is central to this method of encryption. In the RSA encryption process, the public key is used to encrypt the plaintext data into an unreadable ciphertext. This public key encryption is designed so that only the corresponding private key from the RSA key pair can decrypt the ciphertext back into the original plaintext.
In public key cryptography, RSA stands out for its strength and reliability. The public key used in the encryption process is shared publicly without compromising the security of the private one due to the complex mathematical relationship between the two. The RSA key pair thus provides a very secure method for data encryption and decryption, which is why it is widely used in various fields such as e-commerce, online banking, email encryption, and more.
The unique approach of this encryption, utilizing the public key for encryption and the private key for decryption, ensures the integrity and confidentiality of data. The RSA key pair plays an integral role in public key infrastructure (PKI), driving secure communication and data exchanges across digital networks.
Role of RSA in Public Key Infrastructure (PKI)
RSA plays an integral role in a Public Key Infrastructure (PKI), where it is used for generating digital certificates that certify the ownership of a public key. It enables users and systems to both securely exchange data and verify the authenticity of those involved in the data exchange, thereby bolstering the security of the entire communication system.
How Does RSA Encryption Work?
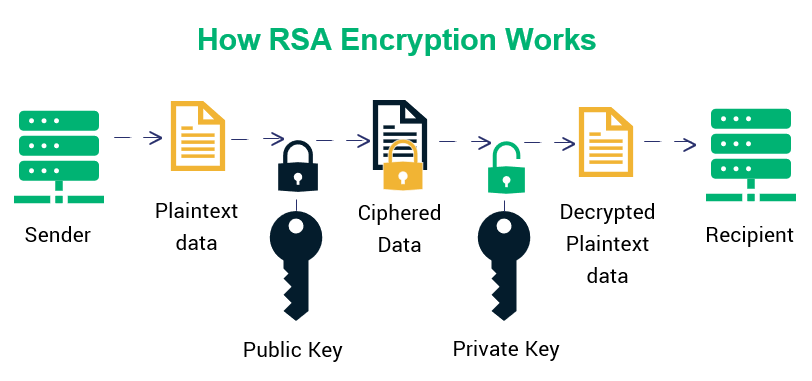
Encryption is achieved through the generation of a pair of RSA keys – a public key for encryption and a private one for decryption. The strength of the RSA algorithm lies in the difficulty of factoring large numbers—a problem that is easy to perform in one direction (multiplication) but hard in the other (factorization). Here’s a simplified overview of how it works:
Step 1: Choose Two Large Prime Numbers
The process begins with the generation of two large prime numbers randomly and independently of each other. These numbers are kept secret. They are multiplied together to create a third number, which is used as the modulus for encryption and decryption.
Step 2: Public and Private Keys Generation
The next step is the generation of public and private keys. The public key is created by choosing an integer, known as “e”. An important requirement of this integer “e” is that it must not be a divisor of (p-1) or (q-1), where p and q are the prime numbers selected in the first step. The selection of “e” is critical because it is used in the encryption process. The pair of numbers (e, n), where n is the product of the prime numbers p and q, constitutes the public key. This public key is made publicly available so that anyone can use it to encrypt a message.
The private key, on the other hand, is generated using an inverse function over the numbers e and (p-1)(q-1) to compute the value of “d”. The pair of numbers (d, n) make up the private key. Only the recipient has this key to decrypt the message.
Step 3: Encryption
The sender encrypts their message by raising it to the power of e (from the public key), and then taking the modulus of n (also from the public key). This results in the ciphertext.
Step 4: Decryption
The recipient then decrypts the cipher text by raising it to the power of d and again taking the modulus of n. The resulting number is then divided by the product of the prime numbers, with the remainder being the original numerical message. This number is then converted back into its original plaintext format, effectively completing the decryption process and allowing the recipient to read the original message.
The security of RSA relies on the fact that while it is easy to multiply two large prime numbers together to create a third number, it is extremely difficult to go the other way, that is, to factorize the third number back into its two prime number components.
Strength and Security of RSA Encryption
The security of this encryption relies heavily on the difficulty of factoring the large composite number formed by the product of two prime numbers – a widely recognized difficult computational problem. It’s easy to multiply two prime numbers together to get another number, but it’s very hard to reverse the process by factoring the resulting number back into its original primes. This property makes the encryption highly secure. While the public key – the product of the two primes – is distributed and known to everyone, knowing this number doesn’t help in figuring out what the original prime numbers were. This asymmetry is what gives RSA its security.
The strength of RSA lies in the fact that it is a deterministic encryption algorithm, meaning that a given input will always produce the same output. This makes it particularly effective and reliable for secure data transmission. The difficulty in reversing the encryption without the private key ensures that even if someone intercepts the encrypted message, they won’t be able to decrypt it.
Additionally, the RSA private key is never transmitted or revealed to anyone. This ensures a level of ongoing protection, as the key is only known to its rightful owner. Even if the public key is known, it is computationally infeasible to determine the private key, hence keeping the communication secure.
Can RSA Be Cracked?
While breaking the RSA algorithm is theoretically possible, doing so is practically infeasible due to the sheer computational power required. In essence, cracking this encryption would mean successfully factoring the product of two large prime numbers, a task which remains computationally challenging even for today’s fastest supercomputers. The larger the prime numbers used in the RSA algorithm, the more secure the encryption, making it practically uncrackable.
Factors Affecting the Security of RSA
Several factors affect the security of this encryption, including key length, the quality of key generation, and the security of key storage. For better security, a minimum key length is required. Shorter RSA key lengths are less complex and can be decrypted more swiftly, presenting a potential vulnerability for cyber attacks. Therefore, using a larger key length is recommended as it exponentially increases the difficulty of cracking the encryption, providing a higher level of security. However, a balance must be found as larger key lengths also require more computational resources, which could reduce system performance. Ideally, it is recommended to use a minimum key length of 2048 bits.
The quality of key generation is critical in ensuring the randomness of the RSA keys, which further enhances security. Lastly, the safe storage of private keys is vital to maintaining the system’s overall security. If an unauthorized individual gains access to an RSA private key, they can decrypt any message encrypted with the corresponding public key.
Side-channel attacks also pose a threat to the security of RSA. These attacks exploit the physical implementation of the system such as power consumption, electromagnetic leaks or timing information, bypassing the mathematical properties of RSA encryption. Effective countermeasures against side-channel attacks are crucial for maintaining the overall security of the system.
Can you Decrypt RSA?
Yes, decrypting RSA-encrypted messages is possible, but it requires the appropriate private key. Anyone who possesses the corresponding private key can decrypt an RSA-encrypted message. It’s this principle that allows secure communication, as the sender can use the recipient’s public key to encrypt the message, and only the recipient’s private key can decrypt it.
Tools for Decrypting RSA
There are several tools available online to decrypt RSA-encrypted messages, though these typically require possession of the appropriate private key. These tools are primarily used to test the security of the RSA algorithm or for educational purposes wherein students can learn about the workings of RSA.
Risks and Challenges in RSA Decryption
The main risk associated with this encryption and decryption arises if the private key somehow lands in the wrong hands. Since the private key is what allows for decryption, unauthorized access could lead to unintended data exposure. Additionally, as RSA relies on the difficulty of factoring large numbers, rapid advances in computing, especially Quantum Computing, could potentially pose challenges for this encryption in the future.
How RSA Compares with Other Encryption Algorithms: RSA vs AES
Comparing RSA and AES (Advanced Encryption Standard) isn’t straightforward since they serve different purposes and have unique strengths. AES is a symmetric encryption algorithm and is faster, making it ideal for encrypting large volumes of sensitive data. On the other hand, RSA is an asymmetric encryption algorithm that stands out for its robust security, making it perfect for securely exchanging keys and creating digital signatures. While AES is characterized by its speed, RSA is marked by its security, and the choice between the two often depends on the specific requirements of a situation or system.
Is RSA Still Being Used Today?
Despite advancements in encryption algorithms, RSA continues to be a dominant method for secure online communication and digital signature authentication. Its widespread use can be attributed to its robust security, ease of use, and extensive validation over the years. Furthermore, RSA is an integral part of many standardized communication protocols in use today.
RSA Use Cases
RSA encryption finds its application in numerous fields and use cases, including:
- Secure Email Systems: RSA is often used in secure email systems like Pretty Good Privacy (PGP) and Secure/Multipurpose Internet Mail Extensions (S/MIME). It helps to encrypt the content of an email so that only the intended recipient with a correct key can decrypt and read it.
- SSL/TLS for Web Security: RSA is a critical part of the SSL/TLS protocol, which is used to secure communications on the internet. It ensures that data transmitted over networks, such as credit card information or personal details, is secure and safe from hackers.
- VPN Connections: RSA is also used in Virtual Private Network (VPN) connections to secure data transmission over untrusted networks. It is typically used during the initial key exchange process.
- Digital Signatures: RSA is used to create digital signatures in various software, ensuring the authenticity and integrity of data. It proves that the data comes from a specific sender and has not been altered during transmission.
- Secure File Transfer: In file transfer protocol systems, like SSH File Transfer Protocol (SFTP), RSA helps in the secure exchange of files. It ensures that the files transferred between systems remain confidential and are not tampered with.
RSA Encryption Online: Secure Communication over the Internet
In an online context, RSA encryption plays a significant role in ensuring secure communication over the internet. By encrypting data before it is transmitted and then decrypting it upon receipt with the appropriate private key, RSA prevents unauthorized access, ensuring the confidentiality and integrity of data.
Enhance Your Security with RSA Encryption and SecureW2’s Cloud-based PKI
So, how can your organization leverage the security of RSA encryption? The simplest way is to utilize a managed cloud PKI, such as SecureW2’s JoinNow Connector PKI. Our PKI utilizes several secure algorithms including SHA-256 and, of course, RSA.
Getting digital certificates to all your endpoints is important, too. That’s why our passwordless platform also the entire certificate lifecycle, including generation, distribution, and revocation. We have a self-service onboarding application for unmanaged devices, and automatic certificate enrollment for managed devices through gateway APIs.
For businesses, this combination can significantly minimize the risk of costly data breaches, protect sensitive information, and ensure non-stop business continuity. Simultaneously, it lifts the operational efficiency by simplifying network security management. In essence, coupling RSA with SecureW2’s Cloud-based PKI empowers businesses to leverage advanced encryption capabilities while enjoying the convenience, flexibility, and security of a cloud-based solution. Schedule a free demo today and see SecureW2’s offerings in action.



