Public Key Infrastructure (PKI) keeps data secure, authenticates identities, and ensures end-to-end encryption. It plays a vital role in securing digital communications and involves a set of roles, policies, hardware, software, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates. Essentially, PKI helps safeguard data and ensure secure communications.
Managing PKI in-house can be daunting, requiring significant resources and expertise. PKI-as-a-Service (PKIaaS) offers a solution to this. PKIaaS is a cloud-based solution that simplifies the complexity by offering PKI functionalities as a service, eliminating the need for on-premises infrastructure. PKIaaS is a game-changer, making robust security accessible even to organizations that lack extensive IT departments.
This article defines what PKIaaS is, how it works, its core components, and the benefits it offers. The article aims to arm you with the knowledge to understand and appreciate why adopting PKIaaS could be one of the best decisions for your organization.
What is PKI-as-a-Service (PKIaaS)?
PKI-as-a-Service (PKIaaS) is a cloud-based solution that delivers full Public Key Infrastructure (PKI) functionalities, eliminating the necessity for on-premises infrastructure. This service encompasses seamless key generation, certificate management, and automation processes, all hosted on secure cloud environments. By relying on PKIaaS, organizations can ensure robust cryptographic security and streamlined management, benefiting from scalability, cost-efficiency, and enhanced compliance with security protocols.
How PKIaaS Differs from On-premise PKI
PKI-as-a-Service (PKIaaS) offers several distinct advantages over traditional on-premise PKI, primarily through its cloud-based architecture and managed service model. PKIaaS differentiates itself in these ways:
- Infrastructure Management: On-premise PKI requires significant hardware and software installations and ongoing maintenance, whereas PKIaaS leverages cloud infrastructure, eliminating the need for physical equipment and reducing maintenance overhead.
- Scalability: Traditional PKI systems are often rigid, requiring substantial effort to scale. PKIaaS, hosted in the cloud, offers seamless scalability, allowing organizations to adjust to fluctuating demands easily.
- Deployment Speed: Setting up an on-premise PKI can be time-consuming, often spanning weeks or months. PKIaaS, thanks to pre-configured cloud environments, enables rapid deployment, often within hours.
- Cost Structure: On-premise PKI typically involves substantial upfront and ongoing hardware, software, and personnel costs. PKIaaS operates on a subscription model, spreading costs over time and eliminating the need for large capital investments.
- Management Complexity: Managing PKI in-house requires specialized expertise and constant oversight. PKIaaS offloads this burden to the service provider, simplifying management and ensuring that best practices in security and compliance are continuously followed.
Core Components of PKIaaS
PKIaaS encompasses several core components essential for robust cryptographic security and streamlined security management solutions. These include:
| Cloud Hosting | PKIaaS leverages cloud infrastructure to host the PKI, eliminating the need for physical hardware and ensuring high availability, redundancy, and disaster recovery. This also facilitates rapid scaling and resource optimization. |
| Automation | Automation in PKIaaS covers key generation, digital certificate issuance, renewal, and revocation. These automated processes drastically reduce the risk of human error and ensure timely updates, maintaining the integrity and security of digital signatures and encrypted communications. |
| Managed Services | PKIaaS offers managed services, including setup, ongoing maintenance, and support. These services ensure private keys, digital certificates, and cryptographic algorithms are properly configured and maintained, providing end-to-end encryption and secure communications. |
| Security Protocols | Robust security protocols are foundational to PKIaaS. It incorporates asymmetric cryptography, ensuring that public and private keys facilitate secure key exchange and data encryption. Advanced security measures protect against man-in-the-middle attacks and unauthorized access. |
| Certificate Management | Efficient certificate management is crucial. PKIaaS manages the lifecycle of digital certificates, ensuring proper issuance by trusted certificate authorities, and automated renewal and revocation of certificates to maintain a secure connection and prevent vulnerabilities. |
| Authentication and Authorization | PKIaaS provides robust authentication mechanisms, utilizing certificates to verify identities during communication sessions and granting appropriate access based on predefined security policies. |
How PKIaaS Works
PKIaaS works by encompassing the following:
Public Key Cryptography
At the heart of PKIaaS lies public key cryptography, which ensures secure key exchange and encryption. This cryptographic technique employs a pair of public and private keys.
Public Key
The public key is openly distributed and used to encrypt data. Though freely accessible, it is a crucial part of the asymmetric encryption. It transforms plain text into an encrypted format that can only be deciphered by the matching private key. This ensures that even if the encrypted data is intercepted, unauthorized entities cannot read it.
Private Key
The private key is closely guarded and never shared. It works in tandem with the public key to decrypt information encrypted by the public key. The security of the entire system hinges on keeping the private key confidential. Only the private key holder can decrypt the messages and data, ensuring robust security.
Importance of the Public and Private Keys for Data Integrity and Confidentiality
Public and private keys are essential for maintaining data integrity and confidentiality. When encrypted using a public key, only the corresponding private key can decrypt data. This guarantees that the data remains intact and unaltered during transmission, preventing attacks. Digital signatures’ integrity is similarly maintained, providing proof of data authenticity and origin.
Certificate Lifecycle Management
PKIaaS streamlines certificate lifecycle management, automating the digital certificate issuance, renewal, and revocation process. Trusted certificate authorities oversee the issuance of certificates, ensuring their validity and trustworthiness. Automated renewal prevents expired certificates from compromising security, and revocation ensures compromised or invalid certificates are promptly invalidated. This full lifecycle management ensures continuous security compliance and minimal operational disruption.
Authentication and Authorization
Authentication and authorization are pivotal aspects of PKIaaS. PKIaaS ensures that entities are authenticated before accessing sensitive data or systems. This authentication process verifies the identity of users and devices, ensuring that only authorized entities have access. Additionally, PKIaaS enforces authorization policies, granting access rights based on predefined security rules. This combination of robust authentication and precise authorization fortifies overall security, ensuring secure communications and data integrity across all interactions.
Why Businesses are Ditching On-premise PKI Over PKI-as-a-Service
Businesses are increasingly transitioning from on-premise PKI to PKI-as-a-Service due to the numerous advantages that PKIaaS provides. Some key benefits driving this shift include:
Cost Efficiency
Traditional PKI systems demand significant capital investment in hardware security modules, software, and specialized personnel for management. PKIaaS operates on a subscription-based model, spreading costs over time and eliminating hefty upfront expenses. This makes robust PKI accessible to businesses of all sizes.
Scalability
On-premise PKI solutions are often rigid and require substantial effort to scale. PKIaaS leverages cloud infrastructure, providing seamless scalability that allows businesses to adapt quickly to growing or fluctuating demands. This elasticity ensures enterprises can scale their cryptographic key infrastructure without overcommitting resources.
Enhanced Security
PKIaaS providers adhere to strict security protocols, ensuring optimal cryptographic keys and digital signature protection. Features such as automatic key generation, certificate issuance, and renewal offer stronger security measures. Asymmetric encryption used in PKIaaS ensures that only the matching private key can decrypt messages encrypted with the public key, safeguarding data integrity.
Simplified Management
Managing an on-premise PKI system requires constant oversight and specialized expertise. PKIaaS simplifies this by providing managed services where the service provider takes care of all operational tasks, including key management, certificate authority functions, and compliance with industry standards. This offloading allows IT departments to focus on core business functions.
Rapid Deployment and Integration
Thanks to preconfigured cloud environments, PKIaaS offers near-instant deployment compared to the time-consuming setup of on-premise systems. Furthermore, PKIaaS integrates smoothly with existing infrastructure, supporting various out-of-the-box applications and devices. This flexibility ensures businesses can quickly enhance their security posture without extensive modifications.
Enhance Your Security Posture with SecureW2’s Managed PKI
Transitioning from traditional on-premise PKI to a managed PKI solution can drastically enhance your organization’s security posture. SecureW2’s JoinNow Connector PKI offers a comprehensive managed PKI solution that seamlessly integrates with existing infrastructure to deliver robust functionalities.
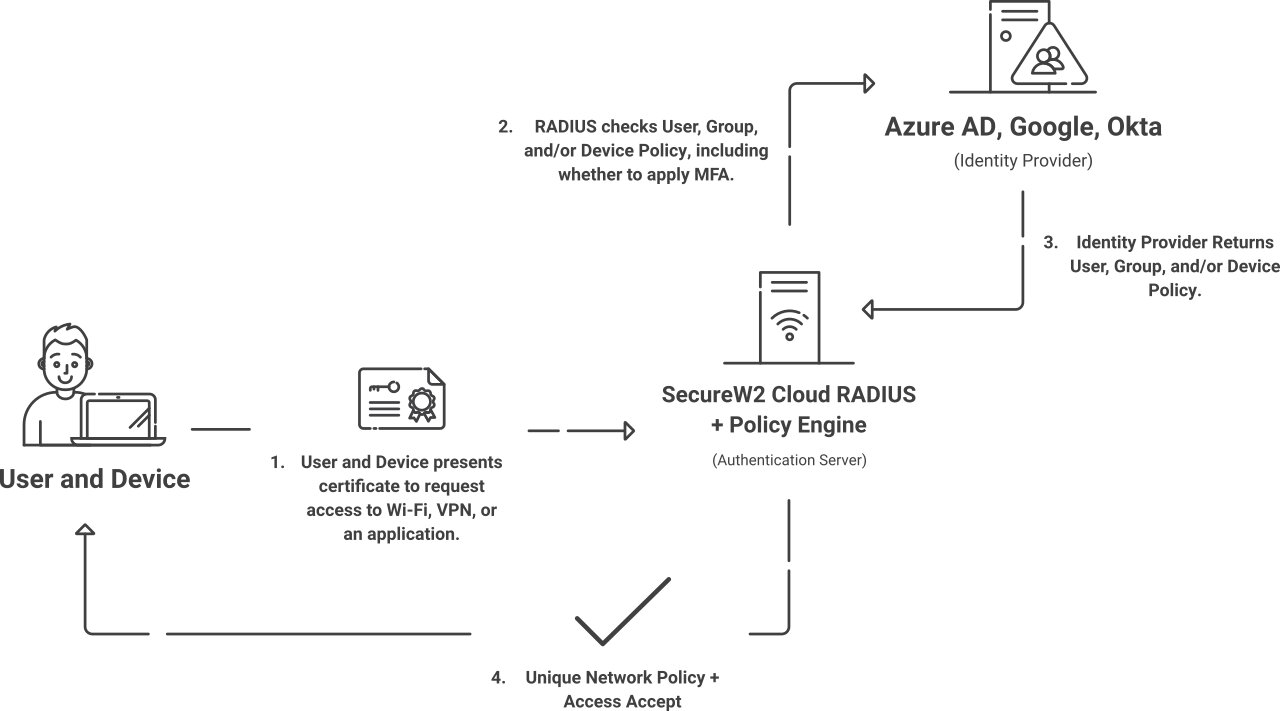
SecureW2’s managed PKI solutions are designed with scalability, security, and simplicity. By leveraging SecureW2’s cloud-based services, including Cloud RADIUS, organizations can streamline certificate management, automate the issuance of digital certificates, and enhance secure communications through advanced public key encryption. This combination simplifies the onboarding process for users and devices and significantly reduces operational costs by eliminating the need for on-premise hardware security modules and specialized personnel.
Our Cloud RADIUS enables secure authentication and authorization, ensuring only authorized users can access sensitive data and resources. With features like automatic key generation, digital signatures, and certificate authority functions, our PKI solutions provide an added layer of security that protects against man-in-the-middle attacks and unauthorized access. By choosing SecureW2, businesses can enjoy peace of mind from a highly secure and efficient public key infrastructure tailored to meet the demands of modern digital environments.
Ready to upgrade your security infrastructure? Explore the benefits of SecureW2’s JoinNow Connector PKI and Cloud RADIUS to see how a managed PKI solution can transform your organization’s approach to security, simplify management, and save costs. Request a free demo today to learn more and take the first step towards a more secure, streamlined future.
