The Network Access Server (NAS) is the frontline of authentication – it’s the first server that fields network authentication requests before they pass through to the RADIUS.
The NAS Identifier (NAS-ID) is a feature that allows the RADIUS server to confirm information about the sender of the authentication request. It’s typically used to set up role-based access, automatic VLAN sorting, or some other form of policy enforcement
How Does NAS-ID Work?
A NAS-ID is generated by a controller or access point (AP) and used to set the NAS-Identifier attribute of RADIUS packets, indicating to the RADIUS server which AP sent the request. The RADIUS server must be preconfigured to receive and verify the identity of the access point, though not all RADIUS servers have the capability.
Note that WLAN profiles and VLAN interfaces can also be configured to generate a NAS-ID for use with RADIUS.
Once the RADIUS is connected to the client via NAS-ID, it can make policy decisions based on optional, customizable NAS-ID attributes assigned to a given group or segment.
How to Configure Custom Policies with NAS-ID
The following is a brief walkthrough of the steps needed to create user segmentation policies in the SecureW2 Management Portal with custom attributes. It assumes that you’ve already bound the controller or AP to the RADIUS via the NAS.
- Select the Network Policies tab from the sidebar of the management portal.
- Click “Create new policy”
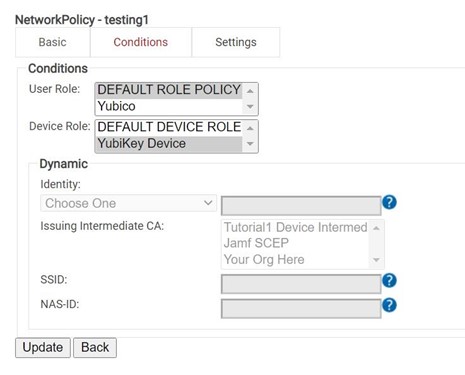
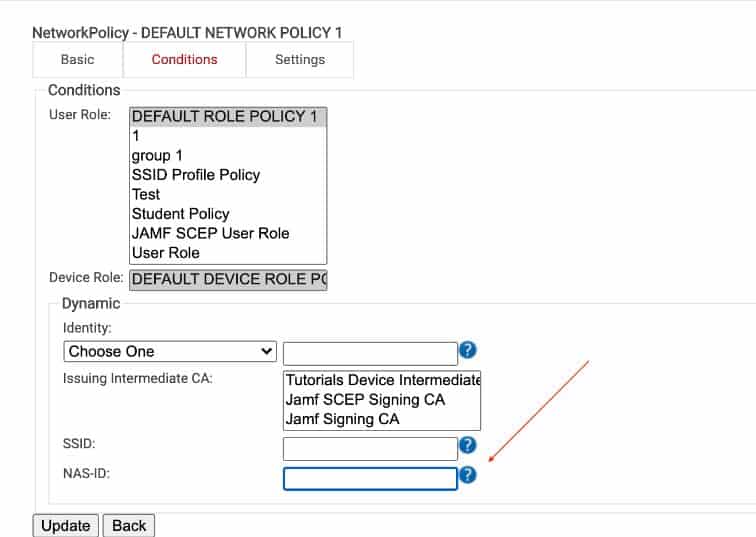
- Choose which conditions activate the network policy.
- Role conditions can be as basic as traditional user or device roles, or you can use our advanced dynamic roles for fine-grain policy decisions.
- Copy the NAS-ID from the AP to the appropriate field.
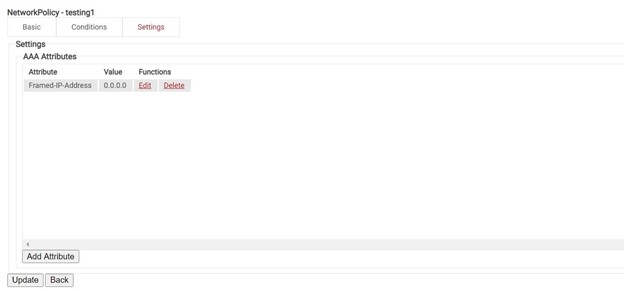
- NAS-ID attributes can be configured with predetermined values in the Settings
Dynamic Cloud RADIUS Policy Enforcement with NAS-ID
SecureW2’s Cloud RADIUS makes great use of NAS-ID to offer unprecedented control over your network authentication. By combining it with our proprietary Dynamic Policy Engine and EAP-TLS certificate-based authentication, our Cloud RADIUS can make runtime-level policy decisions based on attributes stored in the user directory.
This process hugely enhances the security of the network by adding redundant authorization checks (both CRL and IdP) without impacting user experience or even authentication speed. Attributes can be stored in an easily-editable and dynamic user directory rather than on static digital certificates that need to be revoked and reissued to reflect role or permission changes.
The best part is that all of this is easily manageable from our robust single pane management interface. All our products are vendor neutral and can integrate with your existing network infrastructure to deploy more cheaply and quickly.
We have affordable options for organizations of all sizes. Click here to see our prices.