Key Points
- Microsoft NPS centralizes network policies and controls authentication within Windows Server environments, enhancing on-premises network security.
- Integrating NPS with Azure AD presents compatibility issues due to differing on-premises and cloud-based architectures, requiring additional configurations.
- NPS extensions support Azure MFA but come with limitations like complex rule management and security vulnerabilities, complicating integration.
- SecureW2’s Cloud RADIUS streamlines the shift to cloud-based authentication, integrating seamlessly with Azure AD and simplifying certificate management.
In an era dominated by cloud-centric solutions, Microsoft NPS sets out as an on-premise network security tool for Windows Server. Its primary goal is centralizing network regulations, user identities, and authorization protocols. As organizations increasingly use cloud computing, integrating Microsoft NPS with Azure services like Azure AD Connect and Azure AD Sync becomes critical. The NPS extension is essential for extending on-premises NPS infrastructure into the Azure cloud, resulting in a unified ecosystem for safe access control.
Microsoft NPS, as defined, is a policy server that enforces access control based on user accounts identification, device characteristics, and connection settings. It is important for network security because it helps keep privacy policies uniform.
A strong network security posture is bolstered by the seamless authentication and authorization procedures ensured by the interconnection of Azure AD Connect, NPS extension, Microsoft NPS, and Azure AD Sync. However, recognizing several challenges with integrating NPS and Azure AD is important. This article will explore these issues, offering advice and solutions for a smooth deployment.
What Is NPS?
The origins of Network Policy Server (NPS) may be traced back to Microsoft’s dedication to delivering strong and secure networking solutions inside the Windows Server environment. The origins of NPS may be traced back to older versions of the Windows Server operating system when the necessity for a centralized system to control network policy became obvious. Microsoft recognized the need to reduce authentication and authorization operations to improve network security and efficiency.
Organizations that used Active Directory for 802.1X authentication often used NPS concurrently. It is commonly accomplished using EAP methods, such as PEAP-MSCHAPv2 or EAP-TLS, because they can be configured using server certificates. NPS was originally intended to integrate AD with network add-ons, such as VPN, much easier.
How NPS Safeguard Networks?
Centralized authentication guarantees that all users and devices are validated before access to network resources, increasing security. Conversely, authorization establishes the resources that authenticated entities are allowed to utilize.
These are the key tasks that an NPS server oversees to keep a safe and effective network environment.
Users Authentication: NPS ensures that only those with legitimate credentials may access the network by authenticating users and devices making connection attempts. Secure network access points, including dial-up connections, wireless networks, and VPNs, depend on this authentication procedure.
Authorization Management: Following authentication, NPS applies preset policies to decide which resources the users or devices may access. Enforcing safety protocols and guaranteeing that users may only access network locations that correspond to their function and clearance are made possible by this role.
Transitioning to Cloud-Centric Azure AD (Azure Active Directory)
When adopting a cloud-centric identity and access management system, organizations frequently struggle to integrate cloud-based solutions like Azure AD with on-premises components like Microsoft Network Policy Server (NPS). The fundamental incompatibility results from the difficulty of NPS, built on an on-premises 802.1X security approach, integrating with Azure AD’s cloud-based architecture. Many companies use NPS extensions for Azure Multi-Factor Authentication (MFA) after realizing the necessity for a connecting link.
This road is not without complications, though. There are peculiarities in the integration process that need to be carefully considered. Managing the interplay between cloud-centric setup and on-premises components is the problem. A successful transition requires finding the ideal mix between adopting a cloud-first infrastructure and setting up an on-premise, self-managed RADIUS server like Microsoft NPS.
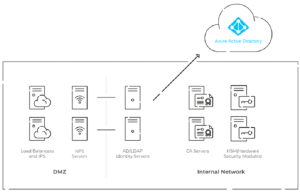
This is how on-premises NPS with cloud-facing architecture looks like –
The Challenges With NPS
NPS’s main issue is that it is generally an on-premises RADIUS solution. Organizations that want to manage cloud-based resources undoubtedly need additional network add-ons and a reliable IT department with some spare time. Organizations face this significant issue when they want to move their AD to the cloud and use Azure while still supporting 802.1x. This doesn’t even mention the extreme cost of building physical servers. The services that organizations need to pay with on-premise servers include, but are not limited to:
⦁ Software acquisition
⦁ Licensing fees
⦁ Scalability for users’ growth
⦁ Hardware infrastructure
⦁ Creation and management of group policies
⦁ Certificate Revocation Lists administration
⦁ Certificate lifecycle management
⦁ Personnel training
Spending hundreds and thousands of dollars for an on-prem NPS server is not out of the question.
To operate NPS in a cloud environment, you must use it as a RADIUS proxy and combine it with a cloud-based RADIUS solution. A user would first send their authentication to the Cloud RADIUS, and then the request would be forwarded to NPS for final authentication. This is an inefficient solution because it requires unnecessary steps for the same level of authentication.
Another issue with NPS is that Microsoft’s products tend to integrate smoothly with other Microsoft products. NPS isn’t your solution if your environment has devices with several operating systems.
Challenges and Drawbacks of On-premise Setups
The main issue with Microsoft Network Policy Server (NPS) is that it is an on-premises solution, which might cause problems for businesses moving to the cloud. This change necessitates more network expansions and a skilled IT staff and presents challenges for moving Active Directory to the cloud while maintaining 802.1x compliance. The difficulty is compounded by the financial expense of setting up a physical server, including hardware infrastructure charges, software licensing, software procurement, and scalability issues. Ongoing tasks, including staff training, certificate lifecycle management, group policy formulation, and administration of Certificate Revocation Lists, also increase the complexity of on-premises NPS.
A RADIUS proxy must be set up to operate NPS in a cloud environment. This causes inefficiencies since user authentication must go via Cloud RADIUS before it can be finalized and reach NPS. This complicated procedure adds pointless steps and reduces authentication efficiency. Furthermore, the substantial expenses linked to setting up and managing NPS servers on-site cast doubt on the viability of such expenditures. The inability of NPS to integrate seamlessly with various environments—particularly those with devices that run various operating systems—highlights the necessity for organizations to look into other options.
Vulnerabilities Associated With NPS and Azure AD Integration
Integrating cloud services like Azure Active Directory (Azure AD) with an on-premises environment poses security problems due to the fundamental differences in authentication methods and architecture. Azure AD’s cloud-based architecture and Microsoft Network Policy Server (NPS), initially intended for on-premise implementation, are incompatible.
Attempting authorization and authentication across two different systems might lead to a potentially fragmented security environment, like having several sets of keys to open a vault. The necessity for safe data transmission between on-premises AD and cloud-based systems, protocol incompatibilities, and attribute mapping problems are common problems.
Businesses frequently use complex infrastructure solutions to overcome these obstacles and bridge the gap between cloud-based and on-premises systems. Specific technologies and protocols must be implemented to provide dependable data flow between NPS and Azure AD.
Furthermore, to adjust to the changing nature of cloud environments, organizations must always be alert in implementing updated security measures. Organizations that rely only on traditional on-premises AD technology run the risk of experiencing new security vulnerabilities. A strong security posture in today’s hybrid IT environments requires a proactive security strategy and a thorough grasp of the challenges of combining on-premise and cloud-based systems.
Azure NPS Extension and Azure AD Integrations
Role of NPS Extension in the Transition
NPS extensions are critical for organizations transitioning from the on-premise world of Microsoft Network Policy Server (NPS) to the cloud-based world of Azure Active Directory (Azure AD). These extensions are essential add-ons that improve compatibility, bridge the gap between NPS and Azure AD, and enable NPS to interact with Azure AD easily according to various regulations.
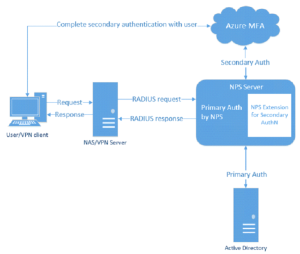
Technical Challenges in Integration
The technological complexities of combining Azure Active Directory (Azure AD) with NPS extensions provide complicated hurdles beyond surface-level understanding. Given that NPS is dependent on Active Directory and cannot communicate directly with Azure AD, it is important to thoroughly comprehend how compatible NPS and Azure AD are. Common concerns include handling complex rule sets inside NPS, guaranteeing connectivity across various devices, and resolving device identification issues. You’ll need technical know-how, proactive monitoring, and preventative measures to navigate these obstacles properly.
Limitations of NPS Extensions
NPS extensions have disadvantages, even though they aim to make the transition easier. Authentication failures can cause user accounts access issues, resulting in delays and possibly compatibility concerns. Specific difficulties include problems with RADIUS attribute flow, which necessitate extra scripts and administrative work. Text-based MFA-based authentication techniques could have problems, and allowing multiple MFA techniques might put networks at risk for security flaws like MITM attacks. It becomes essential for administrators navigating the integration process to weigh the advantages of NPS enhancements against these restrictions.
SecureW2’s Cloud RADIUS Solution for Seamless Transition
There are several obstacles to overcome when moving from on-premises infrastructure to the cloud, especially when integrating Microsoft Network Policy Server (NPS) with Azure Active Directory (Azure AD). A grasp of compatibility issues and the fine balance between security and ease are essential to navigating the complexity between legacy infrastructure and cloud-centric solutions.
In the face of these difficulties, SecureW2’s Cloud RADIUS is a reliable solution for businesses negotiating this complex environment. SecureW2’s Cloud RADIUS solves the security and compatibility issues related to integrating NPS and Azure AD by providing a complete and safe solution. Its increased security features and ability to seamlessly bridge on-premise and cloud-based systems are invaluable for facilitating a safe and seamless transfer.
SecureW2’s Azure RADIUS Solution replaces NPS for Azure AD by easily transferring AD infrastructure to the cloud. CloudRADIUS offers easy-to-use certificate onboarding and integrates with AD CS to supply server and client certificates. JoinNow onboarding software and a turnkey PKI solution are included in SecureW2’s toolset, which streamlines certificate deployment. JoinNow enables users to easily configure certificates on any device, eliminating IT support issues.
Contact us to explore how SecureW2 can empower your organization’s journey to cloud-based identity management.