Organizations worldwide are making the transition to cloud-based network solutions. To ease the transition, Microsoft created Entra to aid clients in moving their directories from on-premise Active Directory (AD) to the cloud. However, Entra is limited compared to AD in terms of support for RADIUS-backed WPA2-Enterprise Wi-Fi. AD is an on-premise solution, and Microsoft Entra ID doesn’t offer an integrated and managed RADIUS solution.
If you plan to migrate to the cloud, you could face challenges that require you to retain your AD-domain hardware.. Luckily, there are many different methods you can use to implement a RADIUS-backed Entra system. SecureW2’s RADIUS solution for Entra ID is entirely cloud-based, verifies Entra ID identity at the moment of authentication, and is straightforward to set up according to our customers.
Entra ID RADIUS Authentication Services
Since Entra ID does not have native RADIUS server functionality, network administrators need to use several methods to secure their on-prem wireless Internet access, including:
Entra ID with Network Policy Extension (NPS)
A standard method configures Microsoft Entra Multifactor Authentication with an NPS extension for RADIUS authentication. However, configuring this service can be time-consuming and requires ongoing maintenance and management. It also only supports RADIUS authentication and MFA. In addition, this method can only work via a password authentication protocol (PAP), which is far less secure than its 802.1x certificate counterpart.
Entra ID With FreeRADIUS
Another solution for adding RADIUS capability to Entra ID is implementing and configuring a virtual FreeRADIUS server. To do this, network administrators need to secure LDAP for a managed domain in Entra ID DS and create a VM to host FreeRADIUS in the same virtual network as AD DS. Unfortunately, this process is also quite time-consuming, and any missed step can lead to an unsecured network.
This method may be a suitable solution if you have the technical skills and resources. However, most organizations don’t have the time to create a suitable FreeRADIUS solution.
Entra RADIUS Server With SecureW2
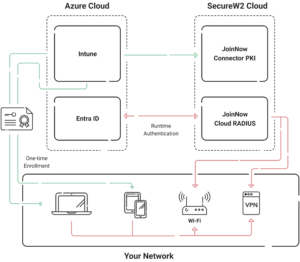
Using Microsoft Entra as your SAML provider, you can easily set up a WPA2-Enterprise network equipped with Cloud RADIUS using SecureW2.
Our JoinNow Connector fully integrates your Entra system for WPA2-Enterprise, allowing you to safely and effortlessly use certificate-based security for Entra and AD devices.
How Entra ID Integrates with Cloud RADIUS to Provide Secure Network Access
Entra ID ensures that only authorized users can access an organization’s network resources. Organizations that integrate Entra ID with a Cloud RADIUS solution can increase network security and enforce strong authentication standards.
This is how the integration works:
Identity and Authentication Integration:
Entra ID serves as a directory, maintaining user IDs and providing important information for authentication. Cloud RADIUS implements certificate-based authentication by dynamically referencing this directory with each login.
- When a person or device seeks to connect, Cloud RADIUS confirms their identification by comparing the digital certificate’s validity to real-time information in Entra ID.
- This real-time look-up guarantees that existing access regulations are enforced, even if modifications (such as revoking rights or altering roles) were made after the certificate was issued.
SecureW2 streamlines this by providing an easy-to-deploy RADIUS solution that removes manual processes, resulting in a quick and secure integration.
Passwordless Security:
One of the key benefits of combining Entra ID with Cloud RADIUS is the transition to passwordless authentication. By employing certificates instead of passwords, the integration significantly reduces problems such as phishing and credential theft.
SecureW2’s platform automates certificate issuance and lifecycle management while ensuring ongoing compliance, allowing organizations to retain strong security with minimum administrative work.
Seamless User Experience:
SecureW2’s Cloud RADIUS solution improves the user experience by making authentication safe and straightforward. Users get a quick, password-free connection, while administrators benefit from simplified implementation and maintenance.
Organizations can maintain a seamless, secure network for employees, contractors, and BYOD users by utilizing SecureW2’s sophisticated capabilities, such as dynamic policy enforcement and certificate automation.
Best Practices for Entra ID RADIUS Integration
Integrating Entra ID with a Cloud RADIUS server can help transform your network security—these best practices, paired with SecureW2’s expertise, will help you with a seamless deployment:
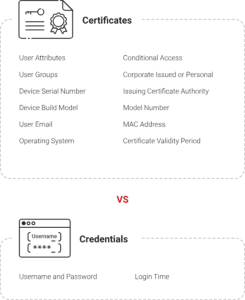
1. Prioritize EAP-TLS for Certificate-based Authentication
The EAP-TLS protocol is considered the gold standard for secure network authentication. Unlike password-based methods, it uses digital certificates to authenticate users and devices, removing the possibility of credential theft. SecureW2’s Cloud RADIUS is designed to handle EAP-TLS natively, simplifying certificate issuing and integration while providing a secure, smooth user experience.
2. Automate Certification Provisioning and Lifecycle Management
Manually managing certificates is time-consuming and can be prone to errors. SecureW2’s Cloud RADIUS automates this whole process, from issue to renewal, saving time and lowering administrative costs. Administrators may use advanced monitoring tools to track certificate status, ensuring that devices are always compliant and authorized. This mechanism improves security by preventing expired or incorrectly set certificates from interrupting access.
3. Enforce Conditional Access Policies
Dynamic, real-time access control is critical to current network security. Integrating Entra ID with SecureW2’s Cloud RADIUS allows you to impose fine-grained conditional access controls based on user roles, group memberships, and device compliance. This guarantees that only authorized people and devices may connect, and it automatically adapts to user or device status changes.
4. Use MDM for Comprehensive Device Management
A strong Mobile Device Management (MDM) policy guarantees that only compliant devices—corporate-issued or BYOD—can connect to your network. SecureW2 integrates seamlessly with top MDM systems, such as Jamf and Intune, to enforce device-level policies and simplify security for IoT and corporate devices.
5. Thoroughly Test Before Deployment
Testing your RADIUS configuration before full-scale deployment enables a seamless transition and minimizes interruptions, particularly for remote users. Test the setup with a small group to discover any possible problems. The SecureW2 professional support staff is accessible throughout the testing phase, providing specialized help to evaluate setups and ensure error-free deployment. This proactive strategy minimizes downtime and optimizes the onboarding process for a larger-scale implementation.
FAQs
- What’s the difference between Entra ID and Azure AD?
Microsoft Entra ID is the new name for Azure Active Directory (Azure AD), reflecting its evolution as part of Microsoft’s Entra product family. While the functionality of Entra ID remains the same as Azure AD, it emphasizes modern identity management, including advanced passwordless authentication methods like certificate-based solutions.
Entra ID is designed for cloud-native architectures, making it ideal for organizations with remote or hybrid workforces. SecureW2 seamlessly integrates with Microsoft Entra ID, enabling secure and efficient network access while leveraging features like certificate-based authentication for a passwordless experience.
- How do you set up RADIUS with Entra ID?
To setup RADIUS using Entra ID:
- Set up a Cloud RADIUS solution (such as SecureW2) that works with Entra ID.
- Ensure that Entra ID is configured to issue authentication certificates.
- Set up RADIUS to use EAP-TLS for certificate-based authentication.
- To regulate who has access to the network, use Entra ID’s conditional access and network policies. SecureW2 automates the whole process, making all setups simple and secure.
- Will Entra ID work with Cloud RADIUS?
Yes, Entra ID fully integrates with Cloud RADIUS. Organizations may benefit from Entra ID’s identity management capabilities and Cloud RADIUS’ passwordless authentication by connecting both technologies, resulting in a safe and efficient network access solution. SecureW2’s Cloud RADIUS service is designed to work seamlessly with Entra ID, making settings more straightforward and more secure.
- What are the advantages of using Cloud RADIUS with Entra ID?
Using Cloud RADIUS with Entra ID has several benefits, including:
- Password-based vulnerabilities were eliminated.
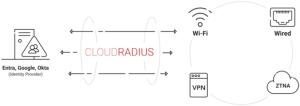
- Integrates well with cloud environments like Azure, Google, and Okta.
- Enhanced security with certificate-based authentication (EAP-TLS).
- Support for secure BYOD and remote working practices.
- Certificate and network access controls may now be managed more easily. SecureW2’s Cloud RADIUS solution streamlines setup while ensuring consistent security across all devices and network access points.
- Is the Entra ID necessary for safe RADIUS authentication?
No, Entra ID is not required for any RADIUS setting. However, it is strongly recommended for organizations that wish to adopt passwordless authentication solutions while maintaining adequate security, particularly in cloud-first or hybrid settings. Entra ID improves RADIUS by offering seamless identity management and contemporary authentication mechanisms like EAP-TLS. The SecureW2 platform makes deploying and operating Entra ID and Cloud RADIUS easy for optimal security.
- What are some common errors when configuring RADIUS with Entra ID?
Numerous common challenges could arise when integrating Entra ID with a Cloud RADIUS server. The following are essential areas to monitor and troubleshoot:
Certificate Validation Errors
Certificates are required for the authentication procedure, and poorly issued or expired certificates might prevent users from accessing the network. Ensure that certificates are valid, appropriately configured, and renewed before expiration.
Solution: Use SecureW2’s automated certificate lifecycle management to speed up certificate issuance and renewal, lowering the likelihood of certificate-related errors.
Conditional Access Policy Errors
Incorrectly configured conditional access policies in Entra ID might unintentionally prevent users from authenticating. Check that policies meet your organization’s authentication and access needs.
Solution: SecureW2 allows for easy monitoring and modification of conditional access policies, ensuring they match your network’s security standards.
MDM Integration Issues
Devices not registered in the organization’s MDM system may have limited network access, particularly BYOD.
Solution: SecureW2 interfaces with MDM systems to ensure device compliance, allowing only authorized and secure devices to access the network.
Misconfigurations in Network Access Control (NAC) settings
Misaligned NAC rules or network settings might cause access issues, preventing users from connecting correctly.
Solution: SecureW2 has thorough diagnostics and reporting tools to discover and fix NAC misconfigurations swiftly.
Authentication Log Errors
Authentication logs can indicate mistakes associated with unsuccessful attempts, assisting in the diagnosis and resolution of issues. Without adequate monitoring, determining the underlying reason might be difficult.
Solution: SecureW2 provides full reporting and log inspection capabilities, allowing administrators to identify and rectify authentication issues quickly.
- Can Entra ID be used as a Wi-Fi SSO?
Yes! SecureW2’s onboarding clients use Entra as a Wi-Fi SSO, except the credentials aren’t used for Wi-Fi authentication. Instead, they are used to enroll for a Wi-Fi certificate, which is then used for authentication. This provides a high level of flexibility and stronger overall cybersecurity. It’s the best defense against over-the-air credential theft.
- Can I Use My Existing PEAP-MSCHAPv2?
SecureW2 can set up a RADIUS server that can service PEAP-MSCHAPv2 and EAP-TLS protocols while ensuring that devices are properly configured for either protocol with the MultiOS Device Onboarding platform.
The most common setup among organizations supporting both protocols is keeping one Secure SSID and configuring the RADIUS server to support both protocols. A properly configured RADIUS server will respond to a PEAP-MSCHAPv2 or EAP-TLS request appropriately, allowing devices using different protocols to connect seamlessly to one SSID.
Simplify Secure Access with SecureW2’s Cloud RADIUS
Integrating Entra ID with Cloud RADIUS guarantees your organization’s network access is safe and passwordless. Organizations may improve security, ease device management, and eliminate weaknesses in old password-based systems by deploying modern authentication techniques such as EAP-TLS. SecureW2’s Cloud RADIUS solution makes this connection easier by automating certificate provisioning, providing extensive lifecycle management, and working seamlessly with Entra ID. With SecureW2, your organization obtains a comprehensive, secure network access solution that expands seamlessly.
Are you ready to safeguard your network with the best?
Contact SecureW2 today to begin integrating Cloud RADIUS and Entra ID!