Imagine conducting important business online without identifying the person you’re interacting with. It would be like handing sensitive documents to a stranger on the street; every login would be risky. Fortunately, the internet establishes protocols to build trust in the digital world, with one of the most important being the Public Key Infrastructure (PKI) certificate.
A PKI certificate is like a driver’s license in that it is a digital ID. It confirms the identity of an entity (person, device, or service) online, allowing you to communicate securely and verify that you’re dealing with the correct person. According to BuiltWith, “There are over 292 million SSL certificates on the Internet as of 19th December 2023. That’s an increase of 40 million in just two years”. This staggering figure highlights the growing importance of PKI certificates in securing online interactions.
Figure 1: SSL usage distribution on the entire internet (source: BuiltWith)
In this blog post, we’ll take a closer look at PKI certificates, explaining what digital certificates are, why they matter, and how you can obtain them easily to safeguard your online activities.
What are Public Key Infrastructure Certificates?
PKI certificates rely on a complex cryptographic system, but it’s easy to understand the basic concept. Consider a specialized lock featuring two distinct keys: the public and private keys. A public key is accessible to all, and a private key is known only to you. While the private key is required to decrypt a message, it is possible to encrypt data using the public key. This is public key cryptography at its core, which serves as the basis for PKI.
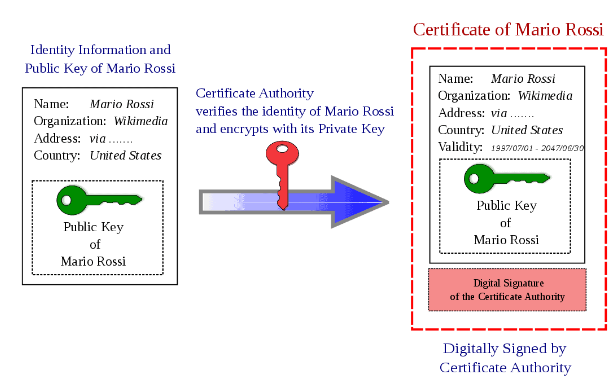
A PKI certificate acts like a digital certificate of ownership for your public key. It’s an electronic document that a trusted entity, a Certificate Authority (CA), issues and binds your public key to your identity. This certificate comprises details such as the holder’s name, organization (if applicable), and the duration of the key’s validity. The CA serves as a verifier, attesting to the public keys and the authenticity of the entity holding the certificate.
Figure 2: Certificate Authority
Why Do I Need a Digital Certificate?
A digital certificate is an underrated asset in online security. It operates quietly to protect your digital activities. It provides the following benefits to you:
Secure Communication (Encryption)
A PKI or a digital certificate enables the use of encryption, a process that scrambles or encrypts data into an unreadable format. This ensures that even if someone checks in on your conversation, they can’t decipher the information.
Assigned with legitimate SSL/TLS certificates, websites establish secure connections, as denoted by the padlock icon within the address bar of your browser. This safeguards the transmission of sensitive data, including login credentials and financial information.
User/Device Authentication Using Digital Certificates
Digital certificates authenticate the identity of users and devices that are attempting to access a network or online resource. This measure serves against unauthorized access and safeguards against malicious entities.
Data Integrity (Digital Signatures)
PKI certificates can digitally sign both documents and emails. This guarantees the integrity of the data during transmission and enables the recipient to authenticate the sender’s identity.
It is important to ensure that data is correct, especially regarding private documents like contracts or financial agreements.
How to Get a PKI Certificate
There are two primary methods for obtaining a PKI certificate, each suited for different needs:
Purchasing from a Certificate Authority (CA)
The most common strategy for ensuring the security of websites and applications is through this approach. Known CAs, such as DigiCert, Comodo, or Sectigo, provide different types of PKI certificates based on your specific needs. SSL certificates are commonly used to encrypt website traffic while signing code certificates are used to authenticate software downloads.
Pros
- Easy and convenient: CAs offer streamlined purchasing processes.
- Wide variety of certificates available: Choose the right certificate type for your needs.
- Cost-effectiveness: Cost-effective for basic website security.
Cons
- Limited control: You rely on the CA for issuance and management.
- Potential renewal costs: Certificates have expiration dates requiring renewal fees.
Issuing from Your Own Self-Built PKI
Optionally, some organizations choose to construct their own Public Key Infrastructure by utilizing resources such as Microsoft’s Active Directory Certificate Services (AD CS).
While offering greater control, building your own PKI requires significant resources and expertise. This process requires hardware, the physical space to store that additional hardware, and the ability to maintain it regularly. Here is an overview of the advantages and disadvantages of this option:
Pros:
- Maximum Control: You have complete control over PKI issuance, management, and security policies.
Cons:
- High Cost: Getting and keeping your SSL certificates up to date requires a lot of money to be spent on hardware, software, and people with PKI expertise.
- Management Complexity: It’s hard and takes a lot of time to manage PKI certificates, including enrollment, issuance, renewal, and revocation, which is complex and time-consuming. This is particularly true without automated solutions.
- Scalability Challenges: Scaling a PKI that you built to fit a growing business’s needs can be hard and require a lot of resources.
- Geographical Limitations: If your business has more than one location, you might have to duplicate your PKI infrastructure at each location, which will make things more complicated and additional costs.
Issuing Certificates with a Managed PKI Service
Managed PKI services provide a cloud-based solution for issuing and managing PKI certificates within your organization. Managed PKI services like SecureW2 offer a cloud-based solution that streamlines issuing and managing PKI certificates within your organization. It makes it easier than ever to secure your digital environment.
The SecureW2 PKI eliminates the need to replicate the infrastructure at different office locations. Additionally, it does not require building from scratch, which ensures swift deployment and reduces costs. This approach simplifies the process compared to building your own PKI infrastructure and offers various features.
Pros
- Increased control over issuance and managing certificates.
- Scalability to accommodate growing security needs.
- Managed PKI services simplify deployment and management.
Cons
- Requires technical expertise for initial setup (managed PKI services can help).
- It may involve higher initial costs than purchasing from a CA for basic needs.
How Does Certificate Issuance Work with SecureW2’s Managed PKI?
Imagine a world where requesting and obtaining PKI certificates is a seamless process. SecureW2’s managed PKI service makes this a reality. We simplify certificate issuance in two different ways, depending on whether you are issuing certificates to a company-owned, managed device or an unmanaged device/BYOD.
We offer our managed device gateways for devices managed by MDMs such as Intune. Using the Simple Certificate Enrollment Protocol (SCEP), these gateways integrate with your MDM platform and automatically issue certificates to all endpoints. With Intune and Jamf Pro, we can even automatically revoke certificates based on the groups you create in your MDM.
With BYODs, we offer a simple onboarding application called JoinNow MultiOS. All end-users must do is navigate to your customized onboarding landing page and run the application. It empowers them to configure their own devices and request certificates in usually less than a minute.
By automating workflows and offering user-friendly onboarding solutions, SecureW2 removes the complexity associated with traditional PKI management. This allows your IT team to focus on more strategic initiatives while ensuring a strong foundation of trust within your organization’s digital environment.
Certificate Issuance FAQs
Where can I get a PKI certificate?
You can acquire them from a CA or through your own PKI, either by using a managed service or building it yourself.
How do you Create a PKI Certificate?
Certificates can be issued via public CAs (like Sectigo, Digicert, etc) or private ones.
Public CA
- Generate a key pair (public & private) on your device.
- Submit a Certificate Signing Request (CSR) with your public key to the CA.
- CA validates your information and issues a certificate linking your public key to your verified identity.
Private PKI
Similar steps, but with internal validation instead of a public CA.
- Enroll (managed service) or request a certificate (self-built PKI).
- Internal validation of your identity or device.
- PKI infrastructure issues the certificate.
Managed PKI services simplify creation compared to self-built options.
How much does a PKI certificate cost?
The costs for certificates can differ based on factors such as the type of certificate, the chosen CA, and the specific plan you choose for managed PKI services.
Who issues PKI certificates?
Certificate Authorities (CAs), which are trusted entities, issue the majority of PKI certificates. Organizations can create their own PKI to internally issue certificates, which can be facilitated by a managed PKI service. A chain of trust is established from each layer in the PKI, with root certificates at the core.
What is a PKI certificate?
A PKI certificate is a digital document used to verify electronic communications’ authenticity and integrity. It contains information such as the owner’s identity, a public key, and a digital signature, which are used to ensure secure and trusted communication over networks.
How do I get my PKI certificate?
The method depends on where you obtain it. Through a CA, you typically purchase and download it. A managed PKI service often automates the process upon user enrollment.
Why do I need a PKI certificate?
PKI certificates offer several benefits: secure communication (encryption), user/device authentication, and data integrity (digital signatures). They create a foundation of trust online.
What is PKI and certificate management?
PKI is a system for issuing and managing PKI certificates. Management involves tasks like enrollment, renewal, and revocation.
What is PKI certificate authentication?
The authentication of Public Key Infrastructure certificates involves the verification of a PKI certificate’s validity by the issuing Certificate Authority (CA). This verifies the identity of the entity to which the certificate belongs.
SecureW2: A Managed PKI Platform that it Easy to Issue Digital Certificates
Public key certificates offer secure communication, which is critical for online security. Each entity must thoroughly understand the procedure involved in obtaining these digital credentials.
Implementing a managed PKI service, such as SecureW2, offers multiple benefits, including a streamlined issuance procedure, reduced administrative workload, enhanced scalability, and an improved security posture. BYOD compatibility and MDM integration facilitate the integration of a wide range of device ecosystems, whereas our intuitive platform automates certificate enrollment and streamlines the onboarding procedure.
By utilizing SecureW2, users can effectively manage the financial implications of internal PKI certificates and identify a solution compatible with their organizational budget. SecureW2 is dedicated to providing the necessary knowledge and resources to establish a reliable and safe digital environment. Start establishing secure interactions, and contact SecureW2 to learn more!



