Key Points
- CAs issue and validate certificates within a Public Key Infrastructure (PKI), with the Root CA as the central trusted entity establishing chain-of-trust for all certificates.
- Trusted Root Stores, managed by OS and browser providers, contain pre-approved public Root CAs, allowing trusted device interactions. Private CAs, however, require custom configurations for network devices.
- SecureW2’s PKI management solutions simplify CA operations, including integration with SAML/LDAP IdPs and certificate policies based on directory groups, enhancing security and efficiency.
A Certificate Authority (CA) is the entity that handles the certificate distribution for a PKI. Certificate Authorities assist in validating the identities of different websites, individuals, and devices by providing a trusted source for certificates.
Certificate authorities are a key part of a functional PKI and are essential to having a secure network. SecureW2 Cloud PKI service allows you to create CAs and distribute certificates with ease. It’s also cheaper than on-premise alternatives as maintaining a cloud PKI costs ⅓ of the price of an on-prem PKI, see how we helped our customers here.
In order for a PKI to work properly, trust must first be established from an original source or the whole system falls apart. But how exactly can a CA establish trust? In this article, we will explain a core element of this initial trust, the trusted root certificate authority store.
What is a Root Certificate Authority?
Trust is established through a chain (pictured below). You can trace the path from the client’s certificate back to a single root CA. This root CA is where all the trust for a PKI is ultimately derived.
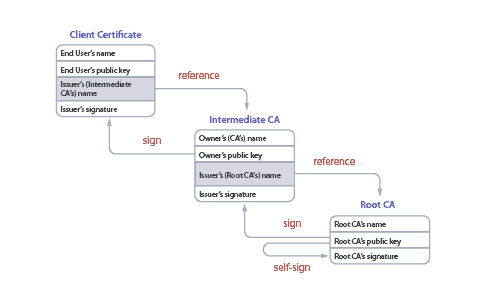
A Root CA is just that – the “root” of the chain of trust. It is a certificate authority that can be used to issue other certificates, which means it is imperative that Root CAs are secure and trusted. If the Root CA were to be compromised, the trust of the chain would be gone, leaving the system obsolete.
Establishing Trust With Trusted Root Certification Authorities Store
In order for a device to get a certificate, it needs to be issued from a trusted source. Root CAs can be established by anyone, so there must be a workaround to establish initial trust.
The most common solution for trust is pre-installed root CAs that come with browsers and applications from their trusted root certification authority stores. Many providers of browsers and operating systems operate their own root store programs; Google, Microsoft, and Apple all have their own, each with stringent guidelines. Other CAs may apply to be accepted into a trusted root certification store using the criteria of that specific program.
What About Private Root Certificate Authorities?
By default, a trusted root certification authority store is configured with a set of public CAs that have met the requirements of the criteria of whatever OS a device is using. If you are using a private CA, it is unlikely to be trusted by any device outside of that network environment.
Managing Your Certificate Authority With SecureW2
The average number of certificates an organization needs to manage grew 43 percent in the 2020 study over the previous year, this highlights how pivotal proper certificate management is for an organization.
SecureW2 offers management systems that you can use to manage and customize any CA, ensuring all your security needs are met. You can adjust your certificate expiration based on user status and automate a notification system that makes sure no certificate expires without you knowing.
SecureW2 allows you to integrate any SAML/LDAP IdP with your CA, which makes it incredibly simple to issue certificates to your organization’s devices. You can create robust policies and create custom certificate templates based on groups already existing in your directory.
SecureW2 comes with a Dynamic Cloud RADIUS that improves certificate management by allowing the RADIUS to communicate directly with the IDP during authentication. This is useful in a situation where a user needs a certificate replaced but you don’t want an interruption in service. The authentication process is unchanged for the user, and it ultimately saves time and effort for both the user and admin.
SecureW2’s certificate solutions are guaranteed to make your network more secure and easier to use. Check out how our PKI can work for your organization on our solutions page here.