The essence of Transport Layer Security (TLS) requires understanding two key concepts: encryption and authentication. While encryption ensures that the data transmitted between your browser and the web server is unreadable to anyone else, authentication verifies the identity of the parties involved in the communication. Together, they ensure that the data remains confidential and reaches the intended recipient without being intercepted or tampered with by malicious actors.
TLS ensures privacy and data integrity between two communicating applications. It is a cornerstone of secure internet browsing. But how does it work, especially when it comes to authentication? This article is a guide to TLS authentication, exploring its workings, setup, and why it’s crucial for your online security.
What is TLS Authentication?
TLS Authentication forms the basis of secure digital communications, employing a protocol designed to authenticate the identities of communicating entities over a network. At its core, TLS Authentication leverages asymmetric cryptography, utilizing public and private keys within digital certificates issued by trusted Certificate Authorities (CAs).
This mechanism ensures that only the intended recipient can decrypt the transmitted data, providing a robust layer of security against unauthorized access and identity spoofing. TLS Authentication facilitates encryption and verifies the legitimacy of the server (server authentication) and, optionally, the client (client authentication), thus ensuring data integrity and confidentiality.
How Does TLS Authentication Enhance Security?
TLS Authentication enhances security through a multifaceted approach involving identity verification, data encryption, and integrity checks. TLS authentication requires one or both parties to prove their identity using TLS certificates. These digital certificates, issued by trusted Certificate Authorities (CAs), are akin to digital passports, assuring that the entity you’re communicating with is indeed who they claim to be. This process helps to thwart a range of cyber threats, including man-in-the-middle attacks, where attackers impersonate a legitimate entity to intercept or manipulate the data.
TLS vs SSL
It’s important to note that TLS is the successor to Secure Sockets Layer (SSL). Although the terms are often used interchangeably, SSL is an older protocol with vulnerabilities that have been addressed in TLS. For all intents and purposes, TLS has replaced SSL, offering stronger security protocols and encryption methods.
How TLS Authentication Works
TLS Authentication operates on a foundation of public key infrastructure (PKI) principles to secure communications between a client and a server across a network. The process begins when a client initiates a connection request to a server protected by TLS.
Here’s a breakdown of the process:
- Certificate Presentation: The server responds by presenting its TLS certificate to the client. This certificate contains the server’s public key and is signed by a trusted Certificate Authority (CA), ensuring its authenticity.
- Certificate Validation: Upon receipt, the client validates the server’s certificate by verifying the digital signature with the CA’s public key. This step confirms that the certificate is indeed issued by a recognized authority and that it has not been tampered with.
- Key Exchange: After validating the server certificate, the client uses its public key to encrypt a pre-master secret and sends it to the server. Only the server, with its corresponding private key, can decrypt this message, ensuring both parties have a shared secret.
- Secure Symmetric Encryption: Using the shared secret, the client and the server derive symmetric encryption keys. Subsequent communication is encrypted with this symmetric key, facilitating a secure and private session.
The protocol further encapsulates mechanisms for client authentication, should the server require. In such instances, the client must also present a digital certificate, verified through a similar scrutiny process performed by the server. This mutual authentication fortifies the security landscape by guaranteeing both parties’ authenticity.
After authentication, a secure encrypted channel is established, leveraging the agreed-upon symmetric key. Henceforth, all transmitted data is encrypted, preserving confidentiality and integrity. This secure conduit ensures that sensitive information remains protected from interception and tampering, showcasing the pivotal role of TLS server authentication in contemporary digital communication frameworks.
The TLS Handshake Process
The TLS handshake is a critical phase in the authentication process, where the client and server exchange the necessary information to establish a secure connection. This includes the server’s certificate, the chosen encryption method, and the symmetric key for encryption. Following a successful TLS handshake, both parties can communicate securely, knowing that their data is encrypted and interacting with a verified entity.
How to Set up TLS Authentication
Setting up TLS Authentication requires meticulous attention to detail to ensure secure communication between clients and servers. The initial phase involves creating or procuring digital certificates from a trusted CA. These certificates are pivotal as they are used to establish the server’s authenticity (and, optionally, the client) in the TLS handshake process. The process involves steps including:
- Obtain Digital Certificates: Secure a server certificate for your server and client certificates for clients if mutual authentication is required. It’s crucial these certificates are issued by a CA that participants in the communication trust.
- Install Server Certificate: Install the server certificate on your server. This involves importing the certificate into your server certificate store and configuring your server software (e.g., web server, email server) to use this certificate for TLS communications.
- Configure Certificate Validation: Ensure your server and clients are configured to validate certificates during the TLS handshake. This means setting up a list of trusted CAs in the client’s software and, if using mutual TLS, on the server.
Configuring TLS Authentication on the Authentication Server
Configuring TLS Authentication on authentication servers is a nuanced procedure that requires proper setup to facilitate secure connections. Authentication servers, which validate user or device credentials before granting access to network resources, play a crucial role in the TLS authentication ecosystem.
Here’s how to configure TLS server authentications:
- Server Certificate Installation: First, ensure a valid server certificate is installed. This certificate should be from a CA trusted by the client devices that will connect to it.
- Enable TLS on the Server: Configure the authentication server’s software to enable TLS for incoming connections. This usually involves editing the server’s configuration files or settings to specify the TLS use and point to the server certificate and its corresponding private key.
- Client Certificate Request Configuration: If client certificate authentication is used, configure the server to request a certificate from clients during the TLS handshake. This implies that the server must have access to a list or store of trusted CA certificates, which it uses to validate the client certificates.
- Testing and Validation: After configuration, conduct thorough testing to ensure the server can authenticate clients using TLS successfully. This may involve using client software configured with client certificates and attempting to access the server to validate that the connection is established and secured as expected.
What is TLS Client Authentication?
TLS client authentication is an authentication mechanism where the server verifies the client’s identity through a TLS certificate, mirroring the client’s process to verify the server. This adds an extra layer of security by ensuring mutual authentication. To enable TLS client authentication:
- Configure the server to request a TLS certificate from the client during the handshake.
- The client must have a valid TLS certificate issued by a trusted CA.
- The server validates the client’s TLS certificate against the trusted CAs.
Configuring Client-Side for TLS Authentication
On the client side, ensuring readiness for TLS authentication involves a few critical steps:
- Obtain a client TLS certificate from a trusted CA.
- Install the client certificate on the device that will be used for the connection.
- Configure the client’s software to present the TLS certificate during the TLS handshake process.
What is Extensible Authentication Protocol-TLS?
EAP-TLS, which stands for EAP-Transport Layer Security, is recognized for its robust authentication framework, particularly in wireless networks and point-to-point (PPP) connections. Unlike simpler methods that may rely on less secure password-based mechanisms, EAP-TLS employs a certificate-based approach, leveraging the strengths of TLS to ensure mutual authentication between the client device and the server.
The process mandates that the client and the server present and validate certificates:
- Certificate Requirements: Both the client and the server must have a digital certificate issued by a trusted Certificate Authority (CA). This requirement ensures that both parties can authenticate securely, significantly reducing the risk of impersonation or man-in-the-middle attacks.
- Mutual Authentication: EAP-TLS is distinguished by its use of mutual authentication. Unlike methods that only authenticate the client to the server, EAP-TLS also requires the server to authenticate itself to the client, offering an enhanced security posture.
- Encryption and Security: Leveraging the underlying TLS protocol, EAP-TLS ensures that the authentication process is encrypted, protecting credentials and other sensitive data exchanged during the process.
EAP Authentication vs TLS Authentication
Both EAP and TLS Authentication address network security from different angles. EAP serves as a framework allowing for the use of various authentication methods, including TLS, within diverse network environments. Conversely, TLS Authentication specifically refers to using TLS protocols to authenticate and secure communications between two parties. EAP can incorporate TLS as one of its authentication ways, highlighting EAP’s flexibility in adapting to different security requirements, while TLS focuses on establishing encrypted, authenticated connections.
How Does EAP-TLS Compare With Other EAP Methods?
When compared to other EAP authentication methods, EAP-TLS stands out because it uses certificate-based mutual authentication, offering a higher security level than methods relying on shared secrets or passwords. This is in stark contrast to methods like EAP-PEAP (Protected EAP) and EAP-TTLS (Tunneled Transport Layer Security), which encapsulate a second authentication transaction within a protected TLS tunnel, offering the user or client-side authentication post-establishment of a secure tunnel.
| Security | EAP-TLS is considered one of the most secure EAP methods because it avoids the vulnerabilities associated with shared secrets and password-based methods. The certificate-based approach mitigates risks such as brute force attacks and credential theft. |
| Deployment Complexity | The major contrast between EAP-TLS and other methods lies in its deployment complexity. EAP-TLS requires the distribution and management of certificates for both clients and servers, which can be a significant administrative burden, especially in large-scale environments. Other methods like EAP-PEAP and EAP-TTLS, while still secure, offer simpler client-side management since they do not require client-side certificates for the initial authentication phase, reducing overhead. |
| Compatibility and Flexibility | EAP-TLS is widely supported across different platforms and devices, offering a high degree of compatibility. However, its strict certificate requirement may limit its application in decentralized device management scenarios. In contrast, EAP-PEAP and EAP-TTLS provide greater flexibility in environments with diverse devices and less stringent control over client configurations. |
| Performance and Efficiency | The direct and secure communication channel EAP-TLS establishes typically results in a more efficient authentication process. However, the initial setup and certificate verification process can introduce delays compared to simpler, password-based methods. This is a trade-off between enhanced security and speed of connection. |
Microsoft EAP and TLS Authentication
Microsoft EAP is a proprietary extension of the standard EAP authentication framework designed to integrate with Microsoft’s network services. Tailored to support the authentication needs of Windows-based networks, it facilitates secure network access control by using various authentication methods, including certificates and passwords. Microsoft EAP is crucial in securing wired and wireless network infrastructures within the Microsoft ecosystem.
Microsoft’s implementation of EAP integrates seamlessly with TLS Authentication, offering robust security features for network access and communication. This integration is particularly evident in environments such as Windows servers and clients, where security and authentication are pivotal.
Through its support for EAP-TLS, Microsoft EAP leverages certificate-based authentication, ensuring a secure and encrypted channel for client-server communications. This approach enhances the security posture of Microsoft-based networks and aligns with industry standards for secure access and data integrity.
Integrating TLS Authentication with Microsoft EAP
Integrating TLS Authentication within Microsoft EAP involves configuring the EAP-TLS protocol as the preferred authentication method in the network policy server (NPS) settings. This process entails deploying a Public Key Infrastructure (PKI) to issue and manage the necessary digital certificates for servers and clients.
By setting EAP-TLS as the authentication method, administrators ensure that the client and server authenticate each other using certificates, thereby enforcing a higher security level. This setup is crucial for environments that demand stringent access controls and secure data transmission, which are characteristic of corporate and enterprise networks.
Configuring Microsoft EAP to utilize TLS Authentication requires careful setup within the Network Policy Server. This configuration process includes:
- Defining a new network policy that specifies the use of EAP-TLS for client authentication.
- Ensuring that the NPS has a server certificate issued by a trusted CA enables it to establish TLS connections securely.
- Configuring client machines to trust the CA and possess client certificates for authentication.
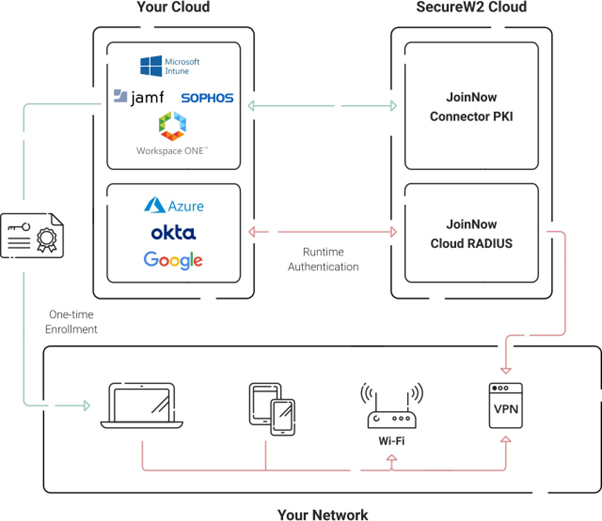
Enhancing Your WiFi Security with SecureW2’s PKI Solutions
SecureW2 offers an innovative, powerful suite of tools designed to streamline the deployment and management of certificate-based authentication, which lies at the heart of TLS and EAP-TLS protocols. Certificate-based authentication replaces traditional, less secure methods such as passwords, offering a more streamlined user experience and significantly enhanced security.
This approach, leveraging Public Key Infrastructure (PKI), ensures that each entity in the network—whether a server, client device, or user—is authenticated using a unique digital certificate, drastically reducing the risk of credential theft or impersonation attacks.
SecureW2’s PKI solutions are designed to integrate seamlessly into existing network infrastructures, simplifying the complex process of certificate enrollment, management, and revocation. With features like automated certificate enrollment and easy-to-manage PKI settings, SecureW2 empowers organizations to bolster their network security without adding undue administrative burden, ensuring that sensitive communications remain secure while maintaining a frictionless user experience.
Schedule a free demo to see if our certificate solutions can provide TLS security for your organization.