Key Points
- RADIUS is a protocol for centralized Authentication, Authorization, and Accounting (AAA).
- It supports password-based authentication but is more secure with certificate-driven methods like EAP-TLS.
- Cloud RADIUS is a managed RADIUS service designed to enable passwordless EAP-TLS authentication for organizations, improving security and scalability.
The Internet has been one of our most transformative and fast-evolving technologies. According to Satista.com, the internet user base increased from 413 million in 2000 to nearly 4.9 billion in 2022.
Using an SSID and a shared password was the most frequent technique of connecting users to workplace networks for a long time. However, the prevalence of data breaches due to weak identification and access control, the growth in geographically dispersed users, and the proliferation of technology platforms used by enterprises make sharing passwords and accounts particularly problematic.
The coronavirus pandemic has worsened pre-existing remote work trends, raising new cybersecurity concerns. Security Magazine says there are over 2,200 attacks daily. Several systems for authenticating and authorizing users have been developed and used to ensure the security of two-way data flow. Here’s where RADIUS proves to be helpful!
This article provides an in-depth analysis of RADIUS, encompassing its definition, operational mechanism, historical background, and current and prospective implications in the domain of network security.
What is a RADIUS Protocol?
RADIUS, short for Remote Authentication Dial-in User Service, is a widely used network security protocol based on a client/server model. RADIUS aims to offer a centralized place for user authentication, where users or customers from diverse locations may request network access and services.
The RADIUS system has gained widespread adoption among network service providers owing to its user-friendliness, effectiveness, and capacity for expansion. Consequently, it has emerged as a prevailing industry standard and is poised to attain IETF standardization.
The RADIUS protocol is employed by various entities such as Internet Service Providers (ISPs), cellular network providers, and corporate and educational networks, and serves three fundamental purposes.
- Authentication – matches user credentials to verify identity
- Authorization – determines user permissions
- Accounting – tracks user network resource-use
The RADIUS authentication protocols are of utmost importance in the 802.1X architecture, where point-to-point protocol and Extensible Authentication Protocol (EAP) are utilized.
The RADIUS server is the pinnacle of network security, and 802.1X is a port-based authentication protocol that permits access to networks via RADIUS. Even if your users log in over public or shared Wi-Fi, the adoption of the RADIUS protocol for authentication will ensure that they cannot access your networks without being securely authenticated first.
History of RADIUS
Although RADIUS was designed during a different era of computing, it’s proven to be versatile and adaptable to meet today’s challenges. Let’s examine a chronology of RADIUS’ evolution during the past decades.
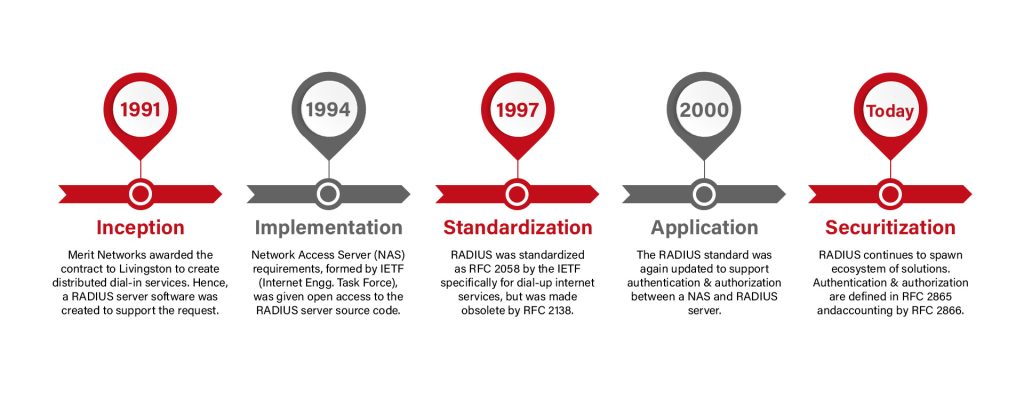
The Livingston Corporation developed the RADIUS protocol to allow the Merit Computer Network to provide dial-up service to tens of thousands of users without configuring each user on each dial-up server.
The first implementation served as the primary source for the Merit AAA/RADIUS server after being heavily changed to operate as both a client and a server for the protocol and to make judgments regarding how to route authentication requests depending on various protocol-carried information. The protocol was so beneficial that it was standardized as a series of Internet Requests for Comments (RFCs).
Components of RADIUS
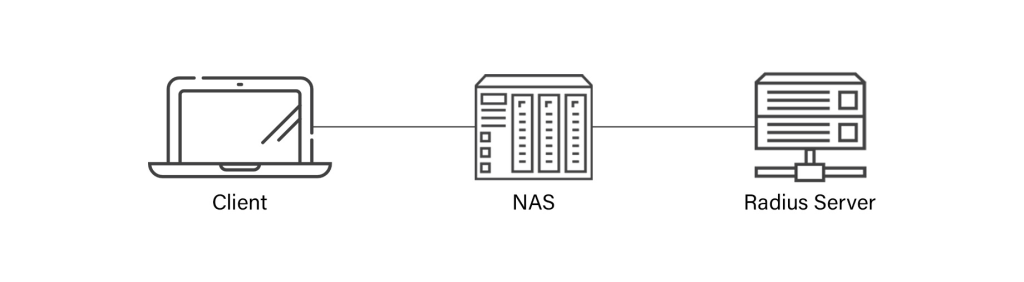
RADIUS consists of 3 main components:
- RADIUS Client/RADIUS Supplicant: a lightweight software that validates credentials by sending them to the RADIUS server.
- Network Access Server (NAS): a gateway between the user outside and the network.
- RADIUS Server: the server that validates credentials. It can also conduct time tracking and assess connection details.
How Does RADIUS Server Authentication Work?
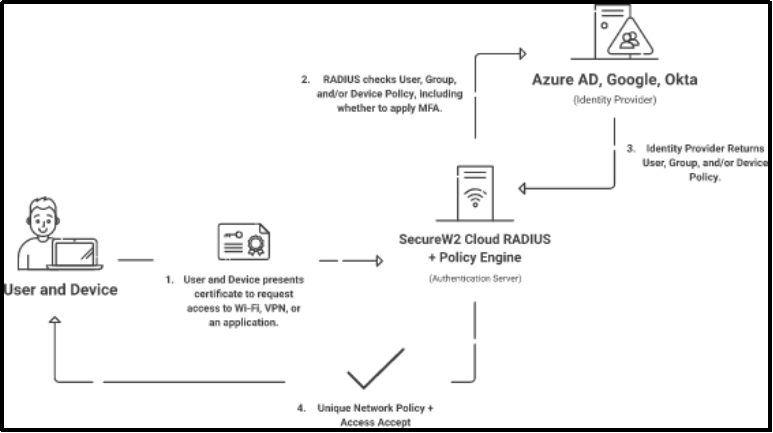
The flowchart presented earlier illustrates that the 802.1X authentication mechanism utilizes a client/server model that comprises four distinct elements, namely a client, an access device, an authentication server, and an identity provider. RADIUS facilitates user authentication by allowing them to establish a connection with a RADIUS server through the use of their credentials or certificates. Subsequently, the server verifies the authenticity of these credentials by cross-referencing them with its user database.
802.1X opens network ports and authorizes access to network resources if the credentials match. Authentication and Authorization can occur concurrently: the RADIUS validates the user (authenticate) and examines whatever network policies have been given to the user (authorize).
X.509 digital certificates or credentials may be utilized for RADIUS server authentication to validate users or devices instead of using usernames and passwords. Depending on which approach is employed, the actual RADIUS authentication procedure differs slightly.
Role of RADIUS in Network Security
RADIUS is the de facto standard for dial-up, DSL, wireless, and mobile networks today, and it is the most common implementation used to enable 802.1X access control management.
The key benefits of a RADIUS server’s centralized AAA capabilities are increased security and efficiency. RADIUS servers enable the system and each individual user to maintain their privacy and security.
Because of RADIUS’ flexibility and adaptability, network defenses may be improved further by adopting current security processes such as multi-factor authentication (MFA), TLS, and VPNs to encrypt payloads.
On-Prem and Cloud RADIUS Server
The integration of cloud-based RADIUS servers involves the utilization of a cloud-based directory service, whereas on-premises RADIUS servers are implemented within the confines of the local infrastructure. Cloud-based RADIUS servers provide a viable substitute for on-premises RADIUS servers, delivering a convenient authentication solution that is devoid of the related administrative burden.
The utilization of a managed cloud RADIUS that employs certificate-based authentication is an effective approach to data security management, as it effectively mitigates significant security risks such as phishing and hacking, while concurrently enhancing the efficiency and security of the authentication process. It is imperative that we consider enhancing our digital security measures to establish a resilient security framework that can effectively safeguard our enterprise against potential cyber threats, irrespective of its size.
RADIUS Authentication Protocols for Wi-Fi
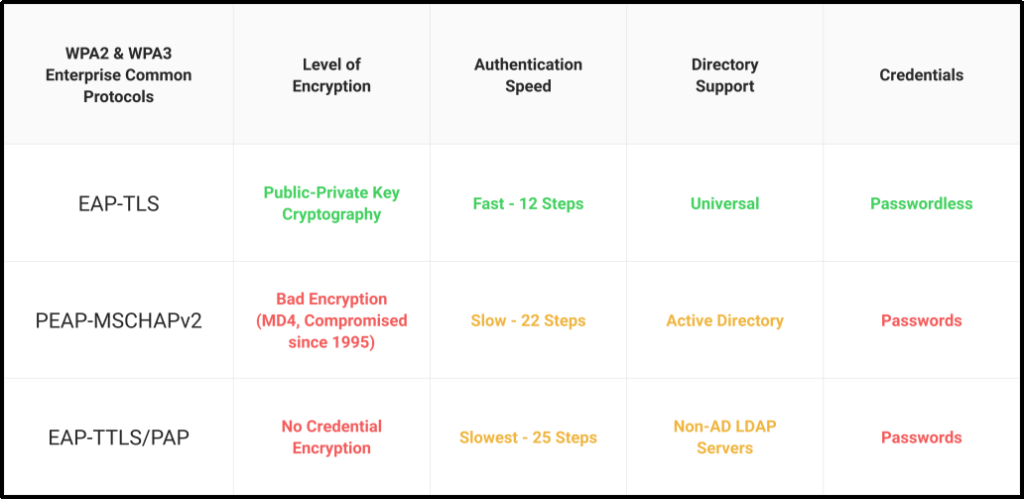
Let’s take a look at the different protocols used in credential-based and certificate-based authentication:
PEAP-MSCHAPv2
The user is required to provide their credentials when using PEAP-MSCHAPv2; these credentials are then transmitted to the RADIUS Server, which validates the credentials and authenticates the user before allowing them access to the network.
EAP-TTLS-PAP
For many years, EAP-TTLS-PAP has been a system standard for WPA2-Enterprise Wi-Fi authentication. It is a credential-based protocol that was developed to make the setup more accessible by needing only the server to be authorized, with client authentication optional.
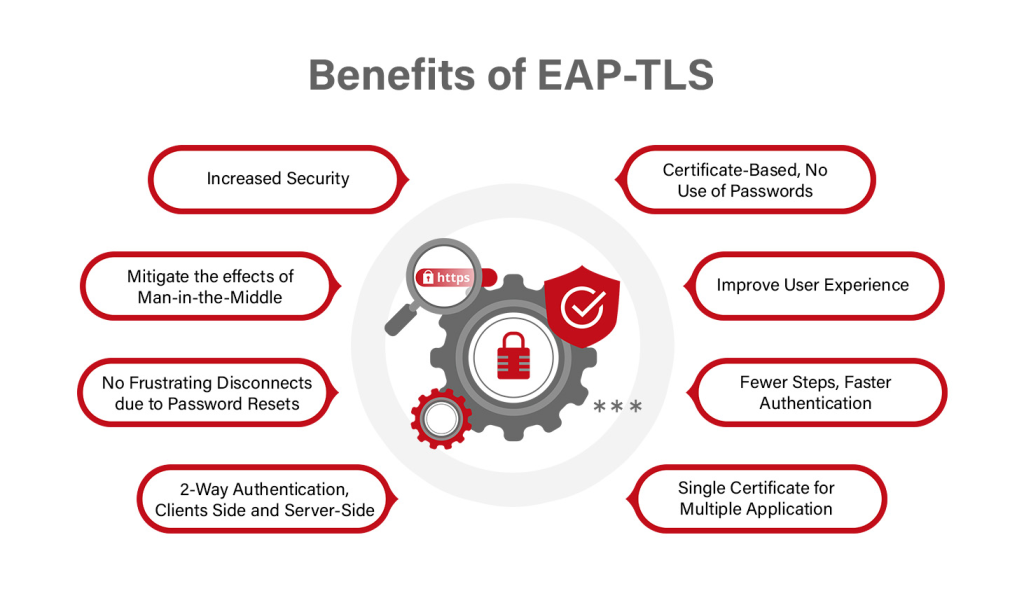
EAP-TLS
EAP-TLS is purely certificate-based and does not utilize any passwords. Our RADIUS servers must have CA certificates from which all client certificates are obtained. Each client that wants to connect must be set up with a certificate (and corresponding key) that will be presented at connection time. Client authentication is performed since the client certificate contains the user’s email address, so validating the owner.
Which Authentication Protocol is Most Secure With RADIUS?
For the EAP-TLS system to work, both the server and the client must use digital certificates to make a link. Because of this, it is generally agreed that, along with RADIUS, it is the most safe system. In order for the digital certificate to be considered valid, it must be signed by a Certificate Authority (CA) that both the client and the server respect.
Let us further examine why EAP-TLS is a winner here.
The future of RADIUS
Authentication services have plenty to offer in every industry, from healthcare to the military. It is the future of login security and will be essential in minimizing ransomware attacks.
Diameter, a protocol conceived not long after the RADIUS working group was established, was at first meant to be a spruced-up version of RADIUS. This improved protocol is now an IETF Standard RFC (3588); its name, Diameter, means “twice as efficient as RADIUS”.
According to a study, “cloud computing can be worth $68.5 billion by 2025” implying that “cloud is the future”. Businesses using the cloud are finding it easier to process huge volumes of data, facilitate global deployment, adopt dynamic ways of working, and be more innovative.
SecureW2’s CloudRADIUS is a 100% passwordless solution, designed to ensure your organization is never susceptible to credential theft of cloud identities. It has built-in redundancy, which means a high-traffic event will not stymie the authentication process.
With the rise in remote work, cloud-based and password-free network solutions are being used by a growing number of companies in today’s business landscape. It is crucial for businesses to reinforce a strong cybersecurity culture.
SecureW2’s CloudRADIUS
Overall, CloudRADIUS is focused on efficiency, since it benefits from a lack of hardware and related expenditures over time.
Furthermore, integrating with Securew2 provides you with additional customization possibilities via our numerous revolutionary features like Azure MFA authentication, Intune auto revocation, Windows Hello for Business login, and many more. Aside from not requiring extensive preparations, CloudRADIUS is immune to on-site threats like outages and robbers. Since it is stored on the cloud and features built-in redundancy, it can serve your business just fine without being installed at each of its locations. Look no further if you’re ready to take the initial step toward protecting your business click here to inquire about pricing.
