
How to Set up Device Identification in Defender for Cloud Apps
Want better visibility and control on all devices in your network for efficient device management? Try Defender Device Management with us.
Read More
Want better visibility and control on all devices in your network for efficient device management? Try Defender Device Management with us.
Read More
There are thousands of deployed instances of Windows RADIUS Server across the world, but users still debate its capabilities to keep their large networks intact and secure, giving rise to questions like: “Is a Windows RADIUS Server sufficient for my ...
Read More
Microsoft has many policy management tools to secure client devices in an organizational environment. Microsoft Group Policy and Intune Profiles are commonly used solutions in different environments, catering to different devices. While Group Policy works for devices in a Windows ...
Read More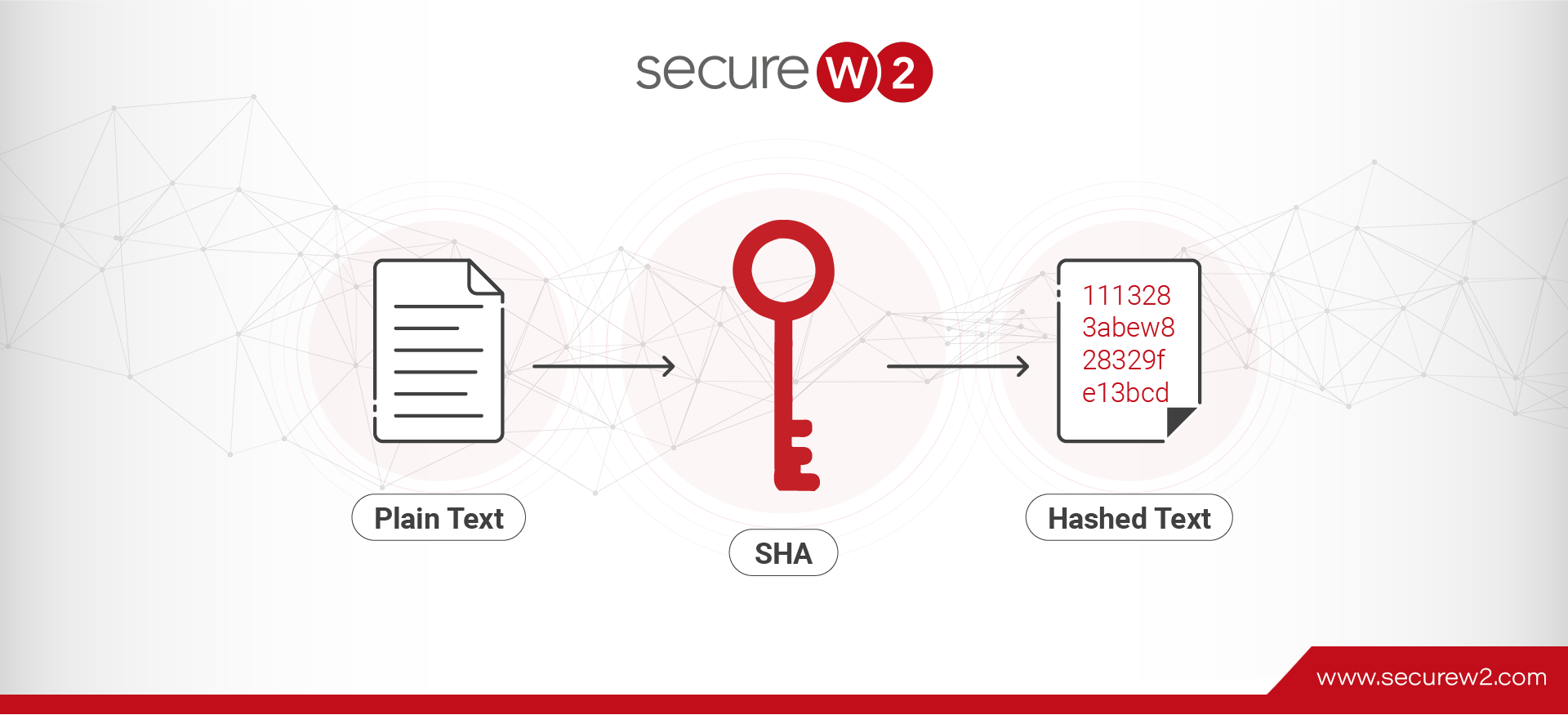
Sending information in clear text over the air is a tremendous risk in today’s complex cybersecurity environment. Hackers constantly evolve attack vectors to target sensitive data in transit, but encryption allows us to prevent this. There are many different encryption ...
Read More
Read this to know more about access control list and its components and the best way to secure your enterprise network.
Read More
Need a solution for your network authentication, authorization, and accounting (AAA) requirements? RADIUS has been around for decades, used by thousands of organizations. Without a RADIUS server, authentication would have to occur at the access point (this would require some ...
Read More
Relying on passwords alone to safeguard access to your resources (including Wi-Fi, applications, and email security) is no longer secure. Cyber attacks designed to harvest credentials become increasingly complex by the day. Stealing a single set of credentials can have ...
Read More
An enterprise needs a safe, secure, and proper network infrastructure implementation to ensure a functional business environment. The Protected Extensible Authentication Protocol (PEAP) is a form of EAP protocol used by organizations to protect their data over-the-air. The PEAP authentication ...
Read More
Everyone uses numerous accounts on the internet these days. Take yourself as an example; you most certainly have a minimum of one social network account, one email address, one for online shopping, and most likely one for online banking. There’s ...
Read More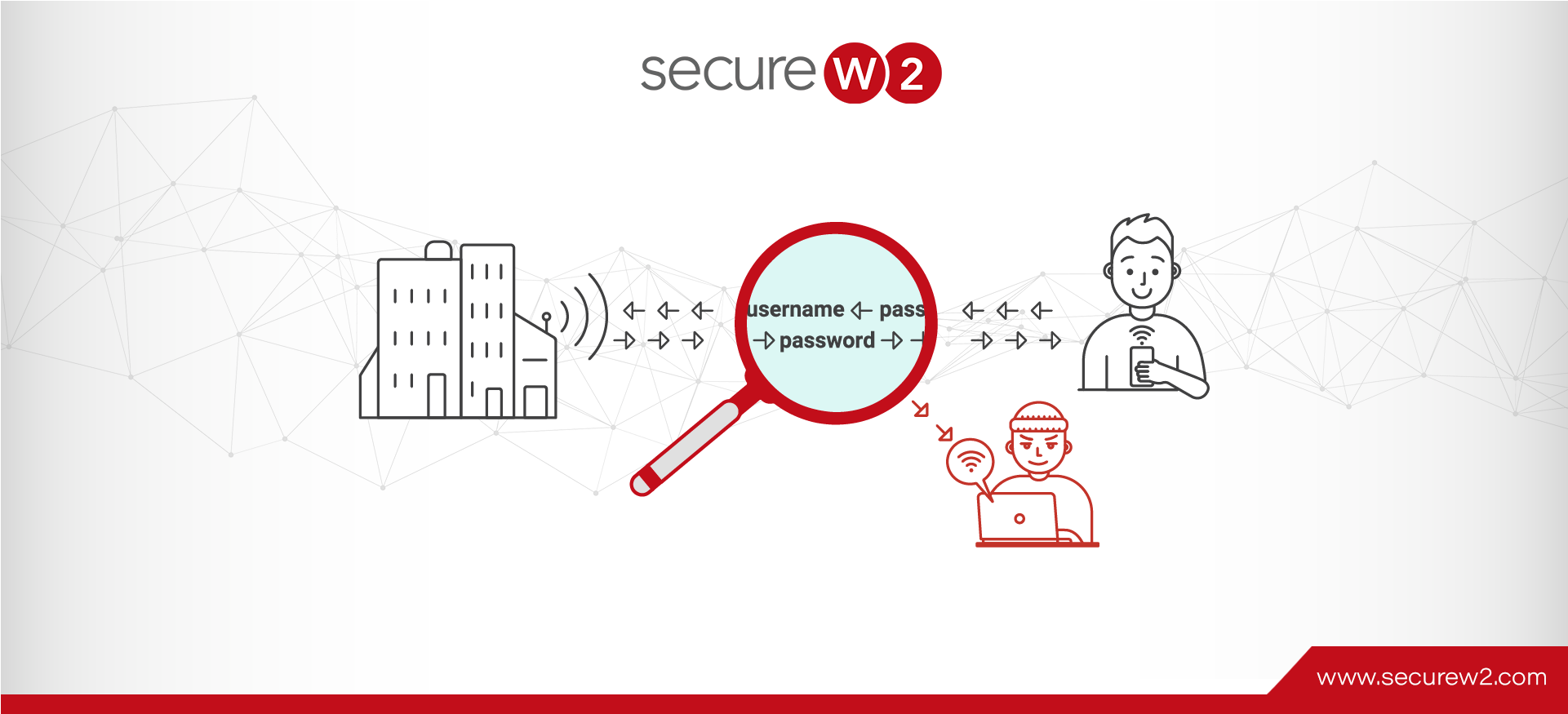
Move away from traditional PSKs to digital certificates and protect your network from Layer 2 attacks. Know more here!
Read More