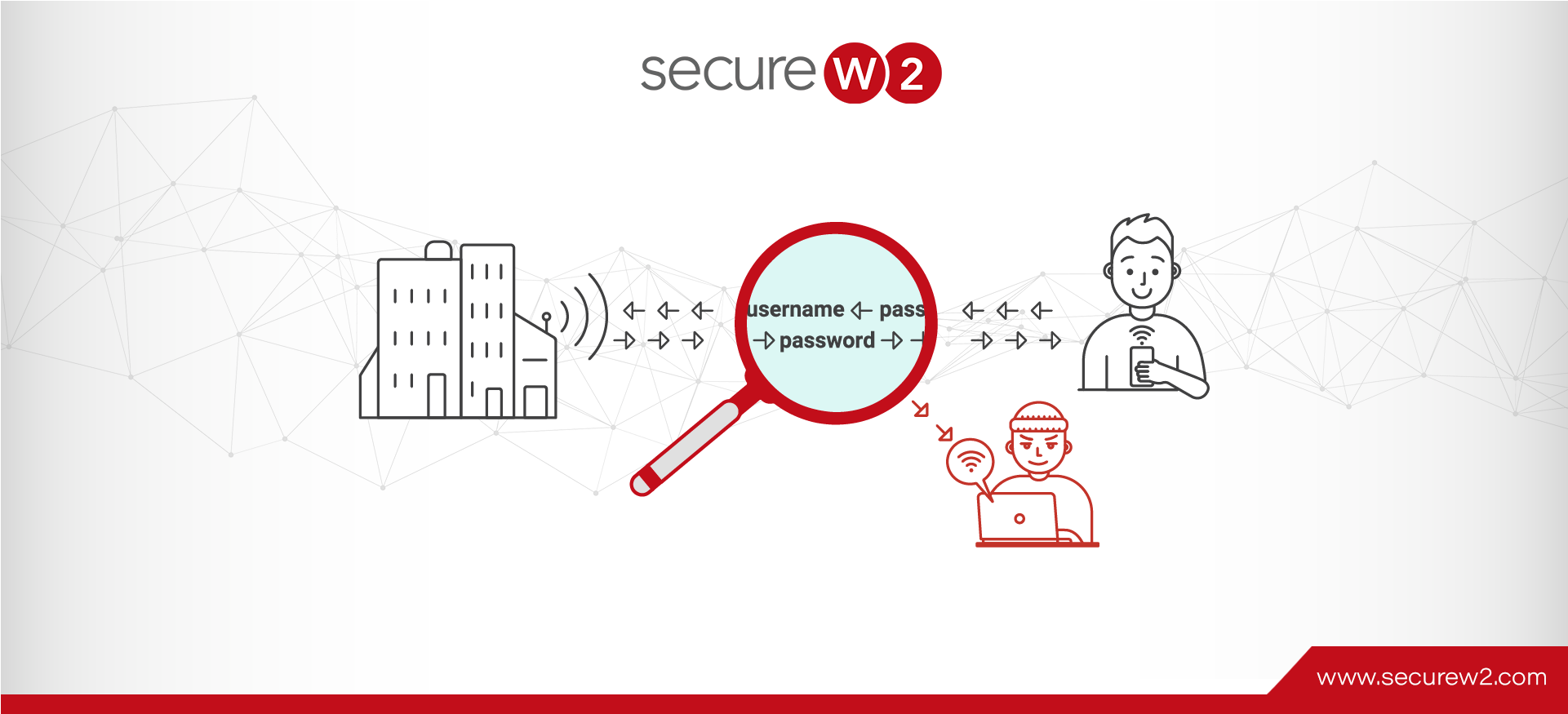
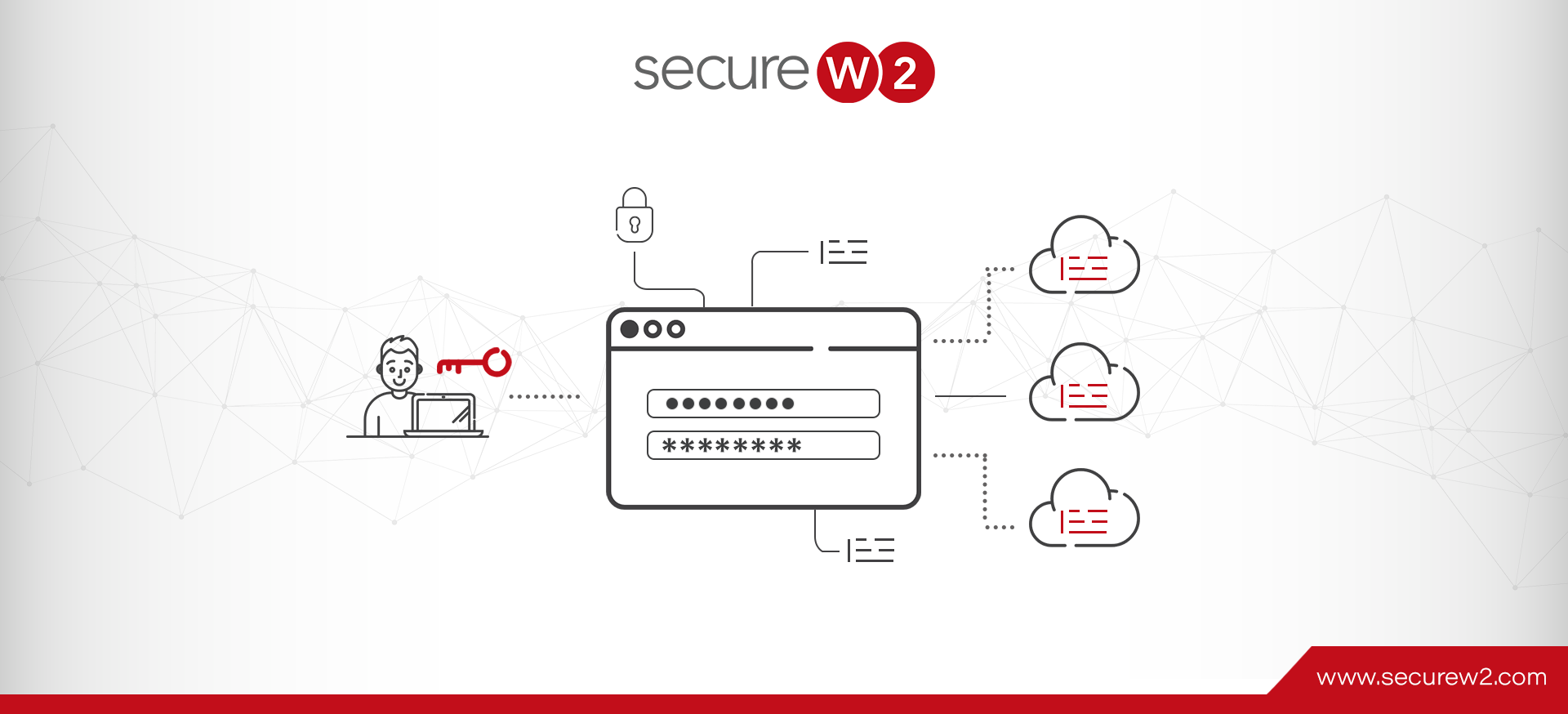
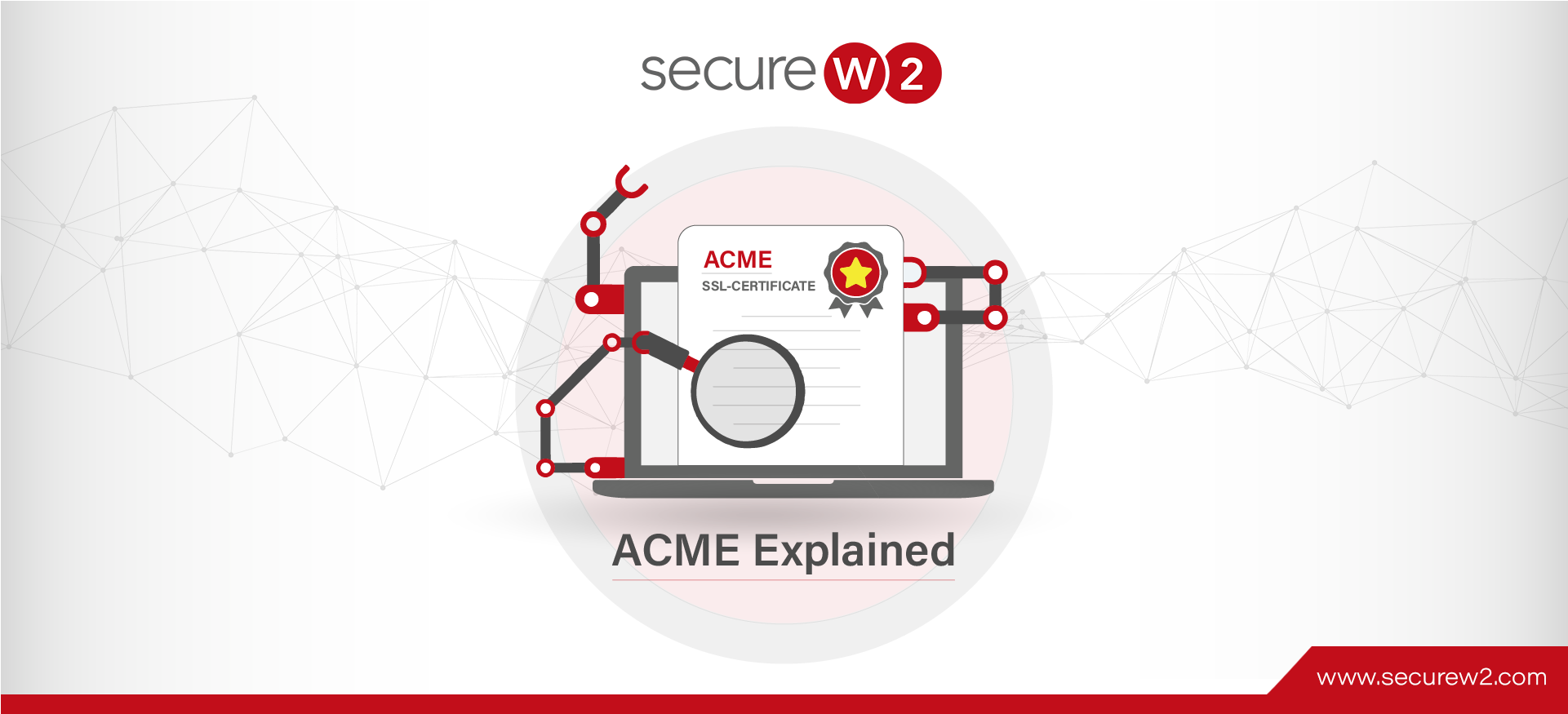
What is Secure Sockets Layer (SSL)?
Security over the internet has drastically improved in the few decades that the internet has been widely available. The average user doesn’t realize how much goes on behind the scenes to ensure the integrity of their data and browsing experience ... Read More