Certificate Management has emerged as one of the better alternatives to avoid the vulnerabilities of credentials in modern-day cyberspace. Here’s a recent incident of a high-profile data breach involving credentials compromise, which once again exposed the vulnerability of credentials in a network domain.
OCSP (Online Certificate Standard Protocol) is a protocol described in RFC 6960, generally used to request the revocation status of a digital certificate, and forms an integral component of certificate management. Here we will discuss some major OCSP errors you might encounter and their respective solutions.
Error 1: OCSP SSL certificate error
Sometimes, while using Mozilla Firefox as a web browser, you might encounter the following OCSP error message “The OCSP server has no status for the certificate.”
This mainly occurs when OCSP fails to recognize the status of the secure server certificate. You can solve this error by following the given instructions from Mozilla support. This will ensure that Firefox is configured with the default settings for OCSP connection errors:
- Navigate to the menu and select the Settings
- Select the Edit options and choose the Preference
- Select the Advanced options and navigate to the Advanced panel.
- Select the Encryption option and click it.
- Select the Validation tab and click it.
- Deselect this tab “When an OCSP server connection fails, treat the certificate as invalid.”
- Click OK and close the Window.
- Close the page about: preferences.
You can temporarily stop OCSP certificate validation from getting around the OCSP error by following these given steps:
- Navigate to the menu and select Settings.
- Select the Edit options and choose Preference.
- Select the Advanced options and navigate to the Advanced panel.
- Select the Encryption option and click it.
- Select the Validation tab and click it.
- Deselect this tab “Use the Online Certificate Status Protocol (OCSP) to confirm the validity of certificates.”
- Click OK and close the Window.
- Close the page about: preferences.
SecureW2 allows organizations to efficiently distribute DPI SSL certificates so that organizations can enable their firewalls to decrypt and inspect SSL traffic for threats. Our PKI services allow you to generate your own Root and Intermediate Certificate Authorities, so you can enable your firewall to inspect the traffic it needs.
Error 2: PKIVIEW OCSP Location#1 Error
You might encounter this error while replacing an outdated configuration with a new internal Windows PKI in your organization. Usually, the OCSP location’s status in the pkiview console is “Error.” A certificate appears to be validated when you use certutil (certutil -URL test-certificate.cer or certutil -urlfetch -verify test-certificate.cer) to examine it.
This error is caused by CA extensions that replace the original AIA path with a different one. You can resolve this error by following the steps mentioned.
- Check your Certification Authority (CA).
- Arrange certificates by Certificate Template.
- Determine whether the most recent CA Exchange Certificate has been revoked.
- Run “certutil -cainfo xchg” from an administrative command prompt.
You can also try revoking the XCHG certificate and issuing a new certificate to eliminate this error.
Sometimes this error also vanishes once you refresh the CAExchange certificate and go back to the default IIS setup.
Drawbacks of OCSP
Although we have tried helping you out with the most prominent OCSP errors, there are still some fundamental flaws in OCSP, and that’s why it is not yet ready to replace the existing certificate revocation mechanisms in the industry.
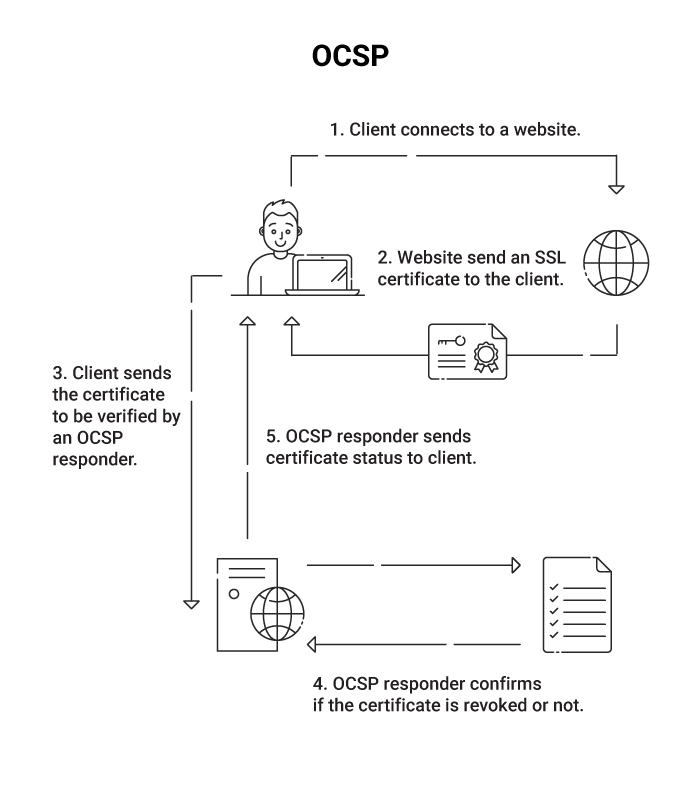
To put it in perspective, the most prominent browsers, such as Google Chrome, Firefox, etc., elect to use the more traditional CRL (Certificate Revocation List) instead of OCSP.
Although OCSP was created to be a more efficient CRL, we think it is a subpar alternative for Wi-Fi security applications in its current form.
CRL: A Better Alternative to OCSP
The PKI cannot determine whether a certificate has been revoked prior to expiration without a CRL. The PKI already maintains a list of authorized users (and the certificates that have been issued to them), but it also requires a list of deauthorized users.
A certificate revocation list, or CRL as it is more commonly known, is a list of digital certificates that have had their authority revoked.
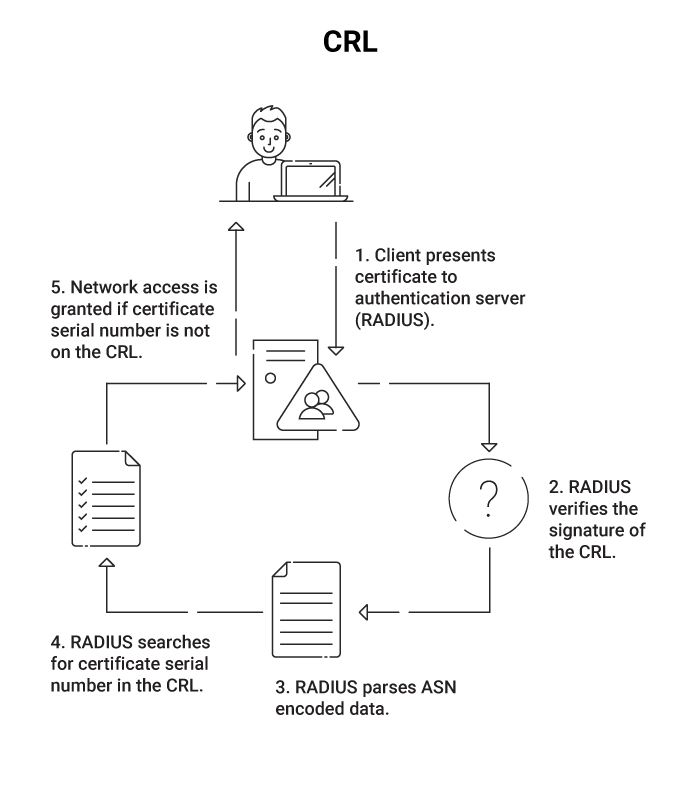
Despite being designed to address this issue, OCSP requests often take longer than CRL requests (and our data shows this effect is exacerbated in globally distributed networks). CRLs are demonstrated to function better across dispersed networks as network latency, not CPU cycles, is ultimately the limiting factor in validating revoked certificates. For this reason, many OCSP architectures use an internal CRL as part of their flow.
Eliminate OCSP Errors with SecureW2
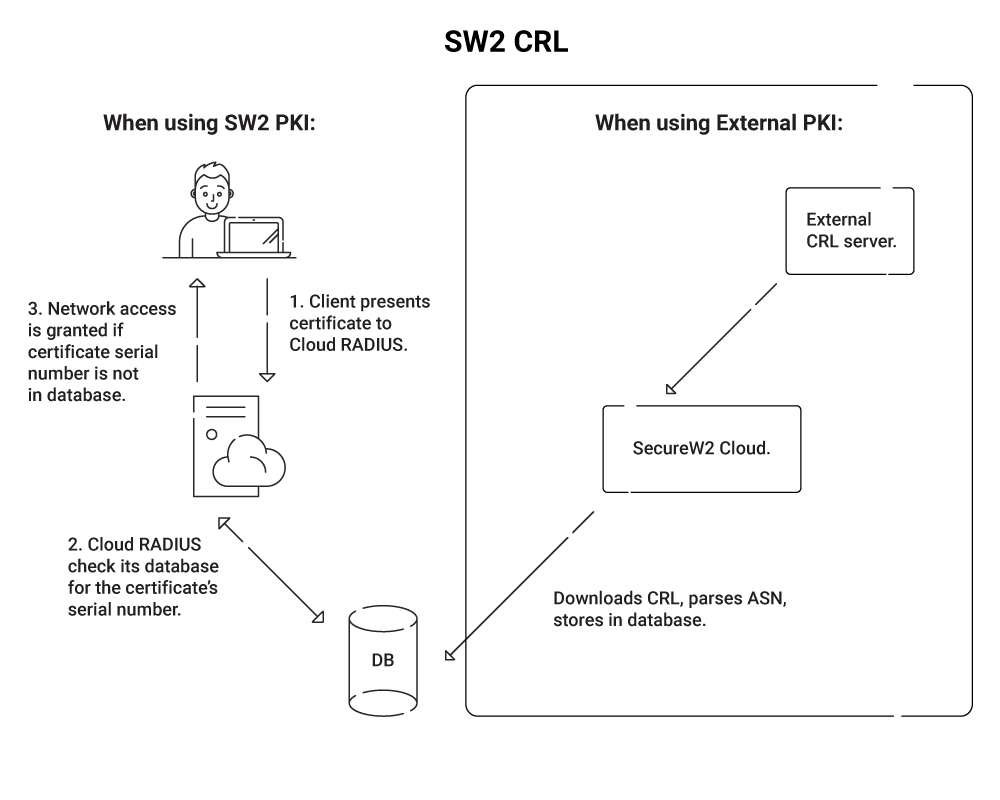
The management suite offered by SecureW2 is user-friendly, powerful, and highly adaptable to the requirements of every enterprise. We offer PKI and CRL solutions at reasonable prices for enterprises of all sizes.
And we are eager to brag about our top-rated support team, which is eager to assist you in every way possible. Please feel free to contact our knowledgeable support experts for additional information regarding certificate management.
