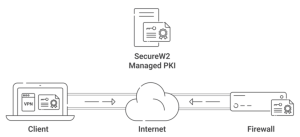
IT administrators must decide on network security: should they install Active Directory Certificate Services (AD CS) on a Domain Controller (DC)? Microsoft PKI (Public Key Infrastructure) solutions are the cornerstone for managing and distributing the digital certificates which is essential for protecting communication channels inside enterprises. But then a conundrum appears: is it better to implement AD CS directly on a DC, or are there other options that take advantage of Microsoft Cloud PKI?
AD CS provides the foundation for a strong Microsoft PKI, providing the digital certificate management and authentication features necessary for safe communication. In the middle of this, Microsoft Cloud PKI’s introduction offers a strong alternative that promises increased security, scalability, and accessibility. However, AD CS can be tricky, and many IT admins make mistakes during the configuration process. One such mistake is installing AD CS CAs on a Domain Controller (DC) instead of another server.
This article explores the nuances of this choice-making process, highlighting the differences between using Microsoft Cloud PKI’s capabilities to strengthen network security architecture and installing AD CS on a DC.
Understanding Microsoft PKI (Public Key Infrastructure)
As the foundation for securing communications inside corporate networks, Microsoft PKI offers the resources to manage digital certificates and Certificate Authorities (CAs). At its foundation, Microsoft PKI relies on public key cryptography to build confidence and support safe authentication and encryption operations. Digital certificates issued by reputable CAs function as digital identities, allowing for safe network communication. The integrity, validity, and secrecy of transmitted data are guaranteed by the public keys, private keys, and information included in these certificates.
One of the main elements of Microsoft PKI is Active Directory Certificate Services (AD CS), which provides a range of features designed to facilitate safe encryption and authentication on corporate networks. By making it easier to issue, validate, and revoke digital certificates, AD CS protects the integrity of data and identities across a range of network endpoints. Organizations may use AD CS to protect critical communications and transactions using strong security protocols like Secure Sockets Layer (SSL) and Transport Layer Security (TLS). Additionally, AD CS easily interfaces with Microsoft Active Directory, allowing for the centralized administration of authentication policies and certificates. This improves overall network security posture and streamlines administrative operations.
Don’t Install AD CS on Domain Controllers
While it’s possible to install an AD CS CA on the same server as a DC, doing so will create several problems for admins in the future. For starters, DCs eventually have to be decommissioned, which becomes more complicated if that DC contains AD CS. Admins would have to move AD CS off that DC before decommissioning the DC.
To upgrade an AD CS CA in a DC, admins must upgrade the DC’s OS. That requires the DC to be decommissioned and AD CS removed from the DC, as we’ve just stated. One of the worst problems is that if the DC were to fail, admins would face the grueling task of restoring the DC and CA. The CA being down means that certificate validation and authentication are affected.
Installing AD CS on a DC is a bad security practice because installing any additional role on a DC increases its attack surface. Unfortunately, several gaps in security with AD CS can compromise the DC if it is installed on the same server.
Configure a Managed PKI with AD CS
While AD CS allows admins to build a PKI, there’s a major disadvantage to not using a third-party PKI solution. AD CS is an on-prem service requiring admins to keep legacy systems on-prem.
On-premise PKIs are incredibly expensive to set up because there are so many components to include, each with its own price tag. Enterprises need to pay for hardware and software implementation, maintenance fees, software licensing, secure hardware storage, data backup, disaster recovery, and much more. These expenses often come as hidden costs, meaning enterprises aren’t aware of them until it’s too late.
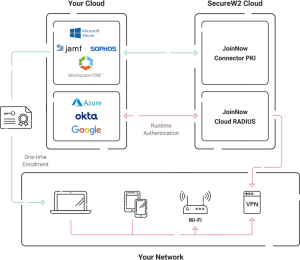
Instead, Microsoft admins can integrate their AD CS setup with a Managed Cloud PKI solution, which removes the implementation and management workload from admins and provides full cloud capabilities.
Configure SecureW2’s Cloud PKI and Cloud RADIUS with AD CS
SecureW2’s Cloud PKI and CloudRADIUS products integrate seamlessly with Active Directory Certificate Services (AD CS), giving organizations greater protection and flexibility. In contrast with traditional AD CS installations, which are inextricably linked to Active Directory, SecureW2’s cloud-based methodology provides increased flexibility in modern network settings. Organizations may centralize operations related to certificate administration, such as issuance, renewal, and revocation. At the same time, still using their current Active Directory infrastructure for user and device management by utilizing SecureW2’s Cloud PKI in conjunction with AD CS. This connection automates device registration processes and enforces strong authentication requirements using CloudRADIUS, simplifying the management of digital certificates and improving security. Additionally, administrators may search for certificates using numerous criteria and do remote troubleshooting with ease thanks to SecureW2’s Cloud PKI, which gives them complete control over certificate administration. Organisations can obtain unmatched authentication security and network scalability with this cloud-friendly design, which also makes traditional PKI implementations less complicated.
A whole range of cloud-based solutions from SecureW2 are available to transform your network security setup. SecureW2’s Cloud PKI streamlines certificate issuing and maintenance, doing away with the time-consuming chores of setting up traditional PKIs. Administrators now have extensive control over certificate management, including the ability to search for certificates based on multiple criteria, easing remote troubleshooting and ensuring seamless operations.
In addition, SecureW2’s Cloud PKI comes with JoinNow onboarding software, making enrolling certificates for BYOD devices on any platform simple. Administrators may safely automate device enrollment procedures while guaranteeing that the highest security requirements are fulfilled using advanced API gateways. Organizations may achieve unmatched authentication security using certificate-based EAP-TLS authentication combined with SecureW2’s CloudRADIUS solution, reducing the risks of credential theft and unauthorized access. Leverage the potential of cloud computing by utilizing SecureW2’s scalable, round-the-clock CloudRADIUS to improve the user10 us experience and strengthen security throughout your network.
Secure Your Network Today with SecureW2’s Cloud PKI and CloudRADIUS
Installing Active Directory Certificate Services (AD CS) on a Domain Controller involves several operational and security risks. Enterprises may reduce these risks and expedite certificate administration and authentication procedures using SecureW2’s Cloud PKI and CloudRADIUS technologies. These cloud-based solutions automate time-consuming operations, guaranteeing an ideal security posture and scalability to accommodate changing company requirements.
Partnering with SecureW2 can help you advance your network security infrastructure. With SecureW2’s Cloud PKI and CloudRADIUS solutions, you may benefit from strong authentication security, easier certificate administration, and cloud scalability. Contact us to schedule a consultation and protect your network from online risks.