Key Points
- Microsoft's AD CS with Jamf for passwordless authentication is complex, error-prone, and struggles with delayed deployments and compatibility issues, especially with newer macOS versions.
- A managed PKI eliminates the need for building a PKI from scratch, automates certificate lifecycle and provides an easier to manage cloud-based solution.
- SecureW2s Managed PKI solution is vendor-neutral, automates enrollment and revocation, and reduces the risk of misconfiguration occuring due to the manual setup required for AD CS.
As credential-based authentication becomes increasingly insecure, many organizations see the benefit of moving to passwordless security methods such as digital certificates. Implementing certificates, however, requires the implementation of a Public Key Infrastructure (PKI) for the management of those certificates.
When set up properly, a PKI can integrate with an organization’s infrastructure, including the organization’s Mobile Device Management (MDM) systems. Jamf Pro is a particularly popular MDM for Apple devices. In this article, we’ll explore how administrators can use Microsoft’s Active Directory Certificate Services (AD CS) to integrate with Jamf for issuing certificates to managed devices.
We’ll also discuss alternatives to AD CS and common problems administrators may face during this kind of integration.
Overview of Using an AD CS Certificate Authority with Jamf
It’s possible to add Active Directory Certificate Services (AD CS) as a PKI provider in Jamf Pro, but you’ll need to use the Jamf AD CS Connector. The AD CS Connector is an SSL-secured web application that receives client certificate requests from Jamf Pro and passes on these requests to the AD CS server, which then generates a certificate request number. This certificate request number is sent back to Jamf. From then on, the number is used to verify the certificate’s completion status with the AD CS Server. As soon as certificates are ready, Jamf Pro distributes them to its endpoints.
In essence, the Active Directory Certificate Services Connector serves as a middleman for all communication between the AD CS server and Jamf. It’s worth noting that this does require good network bandwidth to function properly. Once this is set up, however, AD CS can be used as a certificate authority (CA) and issue certificates to endpoints such as laptops and smartphones, thus enabling certificate-based authentication for Jamf-managed devices.
AD CS PKI and Jamf Integration Steps
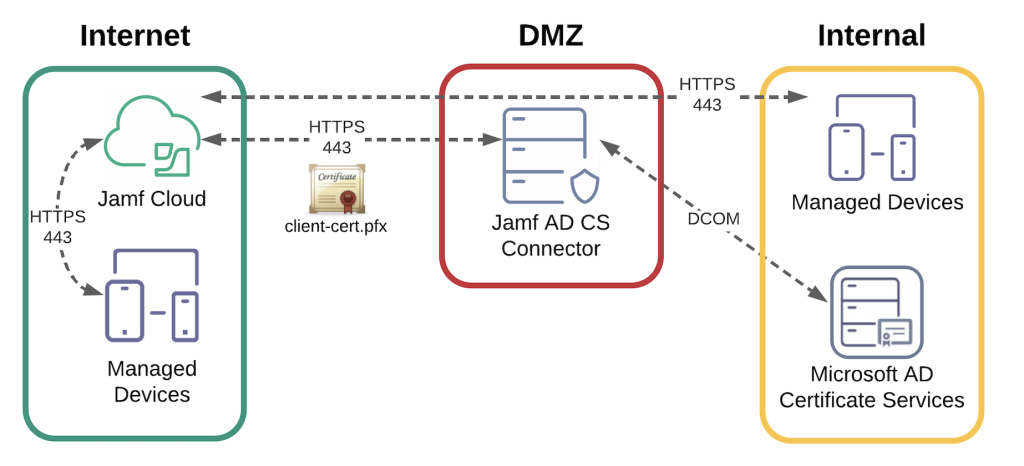
Configuration Overview:
There are three broad steps you’ll need to complete to integrate Jamf with AD CS:
- Installing the Jamf Active Directory Certificate Services Connector on a Windows server
- Adding the Jamf AD CS Connector as a PKI Provider in Jamf Pro Server
- Certificate deployment through Configuration Profile
Pre-requisites:
- Windows 2016 server or later joined to a domain that has a trust relationship with the Certificate Authority
- .NET Framework 4.8 or later
- PowerShell 5.1 (for the installation script)
- Open TCP ports
- 135, 49152-65535 for DCOM – Active Directory Certificate Services communication
- 443 HTTPS for Jamf Pro and Jamf AD CS to connect
- Ideally Jamf Pro Server 10.40 or later
Installing the Jamf Active Directory Certificate Services Connector on a Windows server
To integrate Jamf Pro with Active Directory Certificate Services, Jamf AD CS Connector needs to be installed on a Windows server.
- Log in to your Jamf Account.
- Navigate to Products > Other Products > Jamf AD CS Connector and click Download for Windows.
- Log in to your Jamf AD CS Connector server with administrator privileges.
- Locate the adcs.zip file within the AD CS Connector.zip archive downloaded from the Jamf Account, and extract its contents to your IIS app folder (e.g., C:\inetpub\wwwroot\adcsproxy).
- Open a PowerShell console as administrator, and then run the installer commands
The Jamf AD CS Connector is installed and the server and client certificates are generated. Now you can also configure settings in Jamf Pro to enable communication between Jamf Cloud and the Jamf AD CS Connector.
Adding the Jamf AD CS Connector as a PKI Provider in Jamf Pro
This involves configuring settings in Jamf Pro to define Active Directory Certificate Services (AD CS) as a certificate provider and its life cycle manager and adding client and server certificates to permit authentication between Jamf Cloud and the AD CS connector.
- In settings, go to PKI certificates and configure a New Certificate Authority.
- Select Active Directory Certificate Services (certificate services AD CS) and configure the integration settings by entering the domain name of the server that hosts AD CS in the Fully Qualified Domain Name field and the name of the certificate authority in the CA Name field
- Configure the Jamf Pro certificate services AD CS Connector settings by entering the URL for the location of Jamf Connector and then uploading the server and client certificate
AD CS will appear as a listed CA on the Certificates Authority page as shown below. You can then use Jamf Pro to distribute certificates to devices using configuration profiles with Active Directory Certificate Services as the CA.
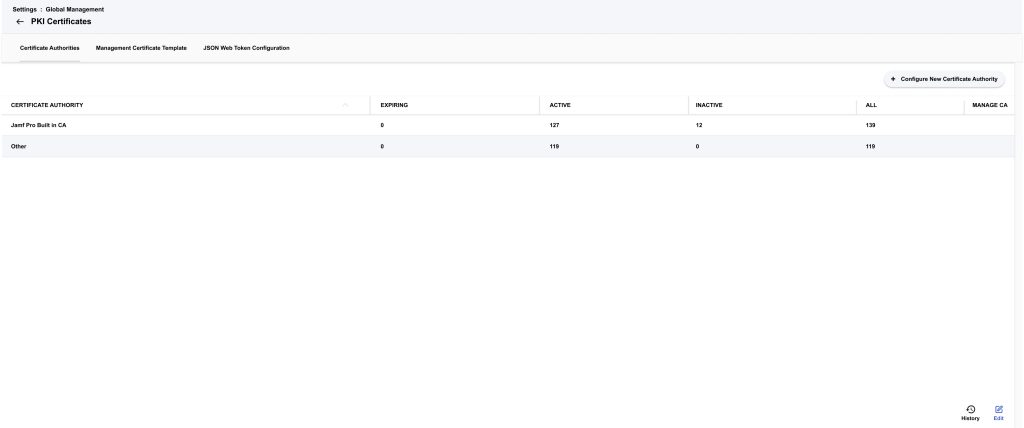
After Active Directory Certificate Services (AD CS) is added as a PKI Provider in Jamf Pro, you can use the PKI Certificates settings to view and edit information about the CA.
Distributing a Certificate Using a Configuration Profile
After the connection between Jamf Pro and Active Directory Certificate Services (AD CS) has been established, you can use Jamf Pro to distribute certificates with AD CS as the new certificate authority (CA) to computers and mobile devices in your environment using configuration profiles. Each certificate will have a certificate subject name and certificate serial number.
One important note is certificates won’t be deployed immediately to the device.
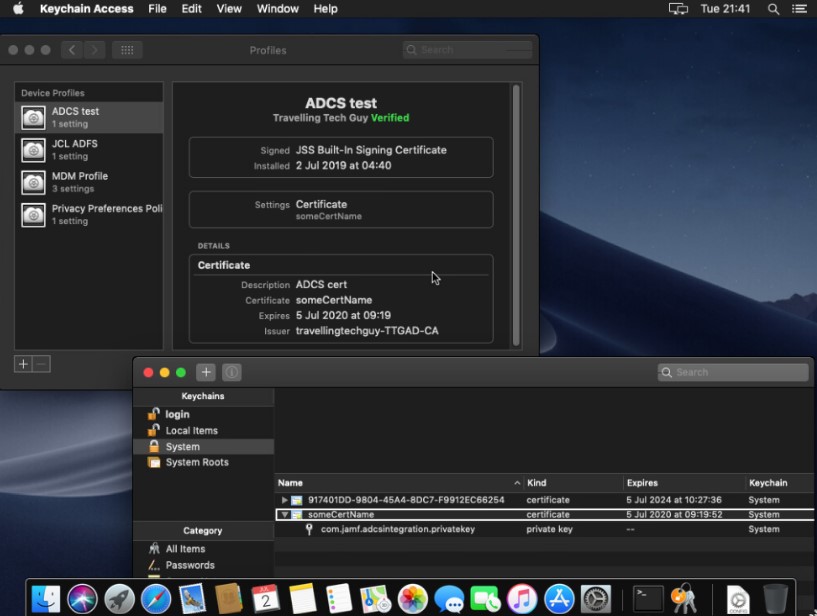
The Drawbacks of AD CS as a PKI with Jamf Pro
Complex Configuration and Management
AD CS requires a high degree of expertise to set up correctly. And if you don’t set it up correctly, you can expose your network to a range of exploitations and vulnerabilities, including certificate theft.
Misconfiguration is a very real risk. For example, organizations using Jamf Pro 10.40.0 or later have to ensure each web application in clustered environments can communicated with the Jamf AD CS Connector – a process which takes time.
- AD CS is complex to install and manage. We have found a whole bouquet of issues compiled here.
- The chances of misconfiguration and minor errors are high. For example, while using Jamf Pro 10.40.0 or later, one needs to ensure all web applications in clustered environments are able to communicate with the configured Jamf AD CS Connector.
Delayed Certificate Deployment
Certificate-based authentication enhances security by reducing the use of vulnerable credentials. Deploying them as quickly as possible is paramount.
When using AD CS with Jamf, however, there’s a delay in certificate deployment. Once the Jamf Pro configuration file is run on devices, the profiles need to queue up the AD CS server for the certificates to be fetched.
Certificates cannot be deployed immediately as soon the Jamf Pro configuration profile is run on devices as these profiles need to queue to ADCS server for fetching a certificate
Difficult Troubleshooting
AD CS, once connected with Jamf, requires a lot of manual troubleshooting when issues arise. As an example, you might receive an error message that says something like the following:
“Problem requesting a certificate from AD CS.”
There might be several different reasons for such an error, and the message doesn’t provide you with a lot of context. You’ll have to go through multiple checks to determine the cause, eliminating issues like these:
- SSL certificate error – Jamf AD CS Connector server certificate in IIS and the Jamf Pro PKI settings or the one present in load balancer/reverse proxy
- Template issue – check the template or variables
- Invalid parameter – check if the right CA name is placed in the AD CS PKI Jamf settings
- CA unreachable – check the CA’s Fully Qualified Domain Name in the PKI Certificate settings in Jamf Pro or firewall
- DNS issue – check the Fully Qualified Domain Name of the Jamf AD CS Connector
- Firewall issue
- Client certificate issue – check the client certificate
- Wrong trusted root CA – check the trusted root CA
Issues Setting up the DMZ
Oftentimes, it’s difficult to set Jamf AD CS connector in a DMZ and have it pass certificates from the internal CA to the Jamf Pro cloud. This happens despite allowing all inbound/outbound IPs on the firewall (not a security best practice but tried with the intent of troubleshooting) while using the correct FQDN for AD CS CA and a properly working DNS.
On further analysis of the captured traffic on the server that houses the connector and the firewall, one can see Jamf Pro Cloud hit the connector in the DMZ,but the connection gets reset, and never reaches the internal CA. If you are looking to put your Jamf Active Directory Certificate Services connector in DMZ, chances are that you might not succeed at all.
Inflexible Infrastructure /Binding Jamf to Active Directory causes long-term headaches
AD CS requires one to have AD to store all the user identities. From what our customers have experienced, AD server doesn’t sync well with Jamf Pro. While discussion on the reasons is beyond the scope of this blog we have witnessed MacOS and AD behaving differently with different OS versions. For example, AD binding works well with the older versions of the MacOS like Sierra while the latest ones such as Monterey have a tougher time.
Costliness of AD CS Setup
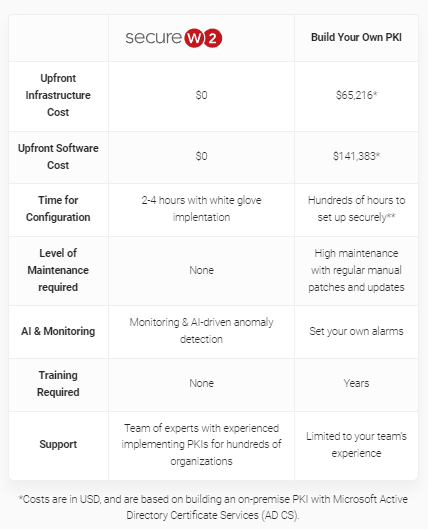
Ultimately, all the drawbacks we discussed previously cause an increase in cost. Any time your administrators need to spend an abundance of time on configuration, it inflates the expenses of your PKI. AD CS is not a managed service; it is a CA server you must manually configure and maintain with regular updates once you integrate it with Jamf Pro.
Alternatively, a managed PKI, such as SecureW2’s, can save you the hassle of troubleshooting and building your own PKI from scratch. Unlike AD CS, our PKI was also designed for the cloud and for vendor-neutrality, allowing it to integrate with all of your infrastructure, including popular MDMs like Jamf Pro. Using the Simple Certificate Enrollment Protocol (SCEP), our PKI can automatically enroll your endpoints for certificates, as well as automatically revoke certificates based on the groups in Jamf.
Why go for a PKI, especially on the Cloud?
AD CS isn’t technically a PKI but a CA server, it provides a platform to build and implement a PKI. AD CS is linked to Active Directory, a Windows server that acts as a user database. As we have seen above there are enormous issues with AD CS and AD. AD CS gives you the ability to build a PKI to deploy certificates to devices on the network. Certificate lifecycle management needs to be done manually.
SecureW2 offers JoinNow MultiOS for faster device onboarding, making setup easier for MacOS devices. This speeds up the certificate distribution process. This approach reduces the possibility of misconfigurations while ensuring cross-platform compatibility and user self-service options. Deploying and managing a PKI is much simpler on the cloud because you can access it from anywhere and automate menial tasks. Contact us today.