Key Points
- Pre-shared keys (PSKs) relies on passwords or a single key, leaving networks vulnerable to certain attacks and potential mismanagement.
- EAP-TLS - or certificate-based authentication for Wi-Fi - provides increased security by removing shared passwords and limiting access to confirmed identities.
- SecureW2’s managed PKI service makes it simple for organizations to issue and manage certificates for passwordless Wi-Fi authentication.
Wi-Fi security is designed to safeguard data as it traverses the airwaves in wireless networks. Wi-Fi Protected Access (WPA) emerged as a response to the glaring deficiencies of its predecessor, Wired Equivalent Privacy (WEP).
Pre-Shared Key (PSK) security protocols have also significantly evolved, with their journey starting from WPA to the much more sophisticated WPA2 and WPA3 standards. Each iteration brought with it enhanced security features, though the conceptual base—using a shared key for authentication—remained the same.
WPA PSK is designed to offer users a simpler method of securing their wireless networks using the shared key. In this article, we explore what a Wi-Fi Protected Access pre-shared key is, how it works, why pre-shared keys are a security issue, and finally, why certificate-based authentication offers better security to a wireless network.
What is a Pre-Shared Key?
In WPA protocol, a Pre-Shared Key (PSK) serves as a foundational element, facilitating a symmetric encryption methodology to secure wireless networks. A PSK is a complex string of characters utilized by participants within a network to authenticate each other before a connection is established. This form of authentication leverages a shared secret known to the network’s access point and its any potential wireless client, underpinning the security protocol that safeguards the communication channel against unauthorized access.
What about Wi-Fi Protected Access Pre Shared Key (WPA PSK)?
Specifically, in WPA and WPA2 environments, the pre shared key is employed to generate a series of encryption keys which are instrumental in the encryption and decryption process of the data packets traversing the network. The intrinsic security of a PSK-based system is heavily contingent upon the confidentiality and complexity of the key itself. Given that the key is shared among users of the network, it introduces potential vulnerabilities, especially when keys are poorly managed or inadequately complex, thereby rendering the network susceptible to a spectrum of cyber attacks. This underscores the criticality of robust key management practices within pre-shared key implementations to uphold the integrity and privacy of the wireless communications.
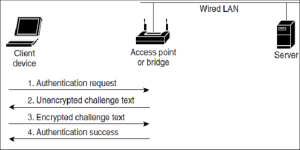
Sequence of Shared Key Authentication Source: ResearchGate
How a Pre-Shared Key Works
In facilitating a secure, encrypted communication channel within wireless networks, PSKs work as follows:
- Initial Setup: During the setup phase, a PSK is generated and configured on both the network’s access point and the devices intending to connect to the network.
- Authentication Phase: When a device attempts to connect, the PSK is used as a shared secret for authentication. The device and the access point must both possess the correct PSK to proceed.
- Key Derivation: Upon successful authentication, the PSK aids in the derivation of dynamic encryption keys. This process involves the use of the PSK along with nonces (random numbers used once) exchanged during the authentication handshake.
- Data Encryption: The derived keys encrypt and decrypt data transmitted between the authenticated device and the access point, ensuring the confidentiality and integrity of the data exchange.
The Difference Between WPA, WPA2, and WPA3 Pre-Shared Keys
PSKs have evolved across the iterations of WPA to address emerging security challenges. The progression from WPA to WPA2, and ultimately WPA3, marks significant enhancements in security protocols, encryption methodologies, and authentication mechanisms.
WPA PSK introduced TKIP (Temporal Key Integrity Protocol) for encryption, offering improved security over WEP but eventually found to be vulnerable to certain attacks. WPA2 PSK then shifted to the more secure Advanced Encryption Standard (AES encryption), significantly enhancing wireless network security by addressing the vulnerabilities of TKIP. WPA3 PSK introduces even stronger encryption methods, individualized data encryption, and protection against brute-force attacks, setting a new benchmark for Wi-Fi security.
Enhanced Security Features in WPA2 PSK
WPA2 PSK made a monumental leap in wireless security by implementing AES encryption. This marked a transition to a more secure encryption method, capable of withstanding more sophisticated cyber-attacks. AES operates on a block cipher, offering a higher degree of security and making WPA2 PSK the standard for secure Wi-Fi networks.
WPA3 PSK: A Leap Forward
WPA3 PSK enhances Wi-Fi security through features like Simultaneous Authentication of Equals (SAE), which provides better protection against password guessing by third parties. It introduces forward secrecy, ensuring that captured data cannot be decrypted even if the attacker later obtains the PSK, significantly mitigating the potential impact of security breaches.
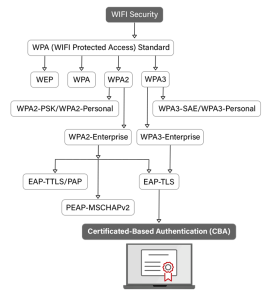
Why Pre-Shared Keys Pose Security Risks
Pre-Shared Keys, despite being central to WPA security protocols, introduce inherent security risks due primarily to their shared nature and the reliance on password strength. The static and unchanging nature of PSKs makes them susceptible to a variety of attack vectors, from brute force to sophisticated decryption techniques. As the complexity and power of cyber-attacks evolve, the static PSK becomes a glaring liability in the security posture of wireless networks.
The Vulnerabilities of Wireless PSK
Wireless PSKs face vulnerabilities stemming from their widespread and uniform use across a network. An intercepted PSK grants attackers access to the network, bypassing further security measures. This uniform application, without distinctions between users or sessions, means that once a PSK is compromised, the security of the entire network is jeopardized, making it a single point of failure in WPA and WPA2 PSK settings.
Weaknesses in WPA2 PSK Authentication
The primary weakness in WPA2 PSK authentication lies in its reliance on the complexity of the pre-shared key. In cases where the PSK is weak or has been shared broadly, it becomes an easy target for brute force attacks. These methods, especially when combined with modern computational power, can decipher weak PSKs, thus rendering the WPA2 PSK network vulnerable to unauthorized access and data breaches.
Temporal Key Integrity Protocol and Its Limitations
While TKIP was introduced as an enhancement in the realm of WPA PSK to improve security, it has notable limitations. Designed as a stopgap measure to retrofit additional security on older hardware, TKIP is susceptible to several types of sophisticated attacks such as key recovery attacks. These vulnerabilities make TKIP a less reliable protocol within the WPA2 PSK framework, underlining the necessity for moving towards more advanced encryption standards like the advanced encryption standard (AES).
How Hackers Target Pre-Shared Keys
Attackers employ a range of tactics to crack WPA2 PSKs. These include dictionary attacks, where common passwords are tried systematically, and more complex methods like capturing a four-way handshake (the process by which a device authenticates with a Wi-Fi network using WPA2 PSK) and then using that to guess the PSK.
Brute Force Attacks: A Persistent Threat to WPA2 PSK
Brute force attacks are particularly effective against weak WPA2 PSKs. Given enough time and processing power, an attacker can eventually crack even moderately complex passwords, exposing the entire wireless network to unauthorized access.
The Role of Social Engineering in WPA2 PSK Compromise
Hackers often turn to social engineering tactics to acquire WPA2 PSKs. They might trick individuals into revealing the WPA2 PSK through phishing attacks or by masquerading as IT personnel. Once in possession of the WPA2 PSK, they gain unfettered access to the network and its resources.
Beyond WPA2 PSK: Certificate-based Authentication
In light of the vulnerabilities associated with PSKs, it’s evident that relying solely on them for Wi-Fi security is increasingly untenable. The introduction of WPA3-PSK with its improved security measures represents a step in the right direction, but the adoption rate is still low, and many networks continue to operate on outdated security standards due to compatibility issues with older devices or simply because of lack of awareness.
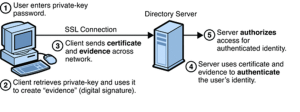
Certificate-based authentication in action
The battle against cyber threats necessitates a more dynamic and multifaceted approach to wireless security, one that moves beyond the limitations of PSKs. Certificate-based authentication is one formidable and more secure method for Wi-Fi authentication. Unlike PSKs that rely on a shared secret, certificate-based authentication utilizes digital certificates to validate the identity of devices and users, offering a higher level of security and ease of management. Here’s a closer look at how it works and the role of Public Key Infrastructure (PKI) and RADIUS servers in enabling this advanced authentication method:
- Digital Certificates: In certificate-based systems, a digital certificate acts as an electronic “passport” for devices, authenticating them on the network. These certificates contain a public key and the identity of the certificate owner.
- Public Key Infrastructure (PKI): PKI is the backbone of certificate-based authentication, providing the framework to create, manage, distribute, use, store, and revoke digital certificates. A PKI enables the issuance of certificates to legitimate network users and devices, ensuring that only authorized entities can access the network.
- Authentication Process: A device or user presents their certificate to the network. The network’s enterprise authentication server (often a RADIUS server) evaluates the certificate against its list of valid certificates. If the certificate is valid and the user/device is authorized, access is granted. Otherwise, access is denied.
SecureW2 offers a comprehensive managed PKI solution designed to simplify the deployment and management of digital certificates. This, coupled with SecureW2’s RADIUS platform, offers a robust framework for passwordless authentication. By verifying each network access request against the most current network policies and utilizing identity lookup from your SAML Identity Provider (IDP), SecureW2 ensures a high-security standard and a seamless user experience.
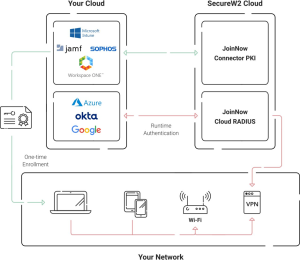
Certificate-based authentication not only eliminates the risks associated with PSKs but also automates the process of network access control, reducing administrative overhead and enhancing network security. Its reliance on digital certificates and a robust PKI, supported by SecureW2’s solutions, marks a significant advancement in Wi-Fi authentication technologies, paving the way for a more secure, efficient, and user-friendly wireless network environment. For more information, click here to see our pricing.