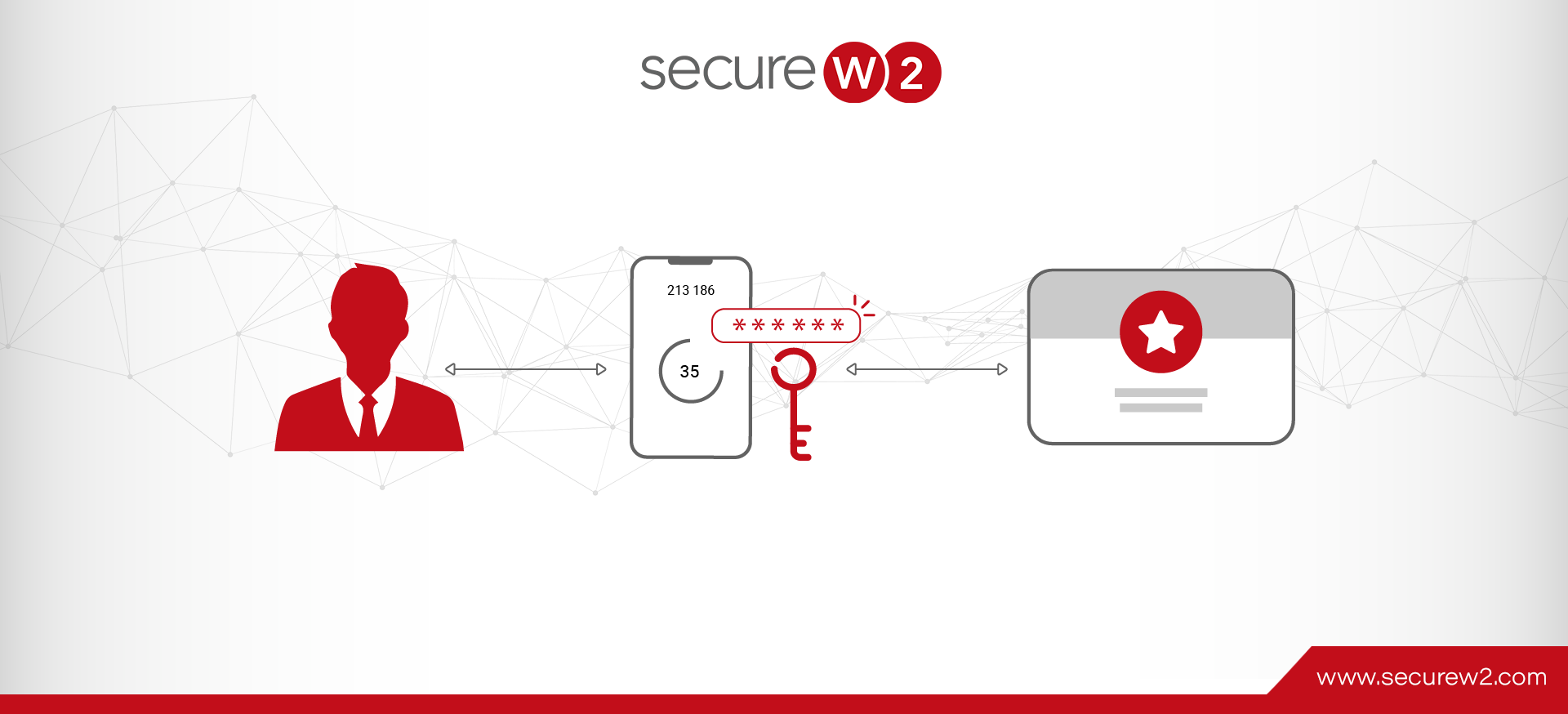
Personal Identity Verification (PIV) is a security standard detailed in NIST FIPS 201-2 that creates a framework for multi-factor authentication (MFA) on a smartcard.
While PIV was originally designed for the US government, it has seen widespread use in commercial applications. Its high assurance identity proofing and the ability to implement MFA to secure physical and network resources has made the standard very attractive.
This article is meant to provide context on the Personal Identity Verification standard as well as suggest a turnkey PIV solution for enterprise.
Origin of PIV
In 2004, the United States federal government commissioned the creation of a standardized identity credential in order to enhance both physical and cyber security. The stated goals were to prevent identity fraud, improve privacy, and facilitate cross-agency cooperation.
The result was Federal Information Processing Standard (FIPS) 201: Personal Identity Verification (PIV) for Federal Employees and Contractors. In 2014, the National Institute for Standards and Technology (NIST) released the updated FIPS 202-2.
What Personal Information is Stored in PIV?
Despite being able to provide a high level of identity assurance, the actual data stored in a PIV credential is pretty minimal. Most of the identity proofing occurs before the credential is even issued, typically by human resources.
In the case of US federal PIV cards, the credentials include:
- Digital photograph
- Biometric scan (fingerprints)
- Cryptographic keys
Enterprises that deploy PIV may not utilize every data field – it’s not uncommon to have systems without biometric capabilities. At its core, PIV is reliant on “cryptographic keys” in the form of X.509 digital certificates – the strongest form of authentication security.
PIV Use Cases
While PIV was developed for internal use within the US federal government, its solid cryptographical foundation and focus on interoperability has made it popular in commercial applications as well.
Non-governmental organizations around the world frequently use the FIPS 201 standard to deploy smartcards with “PIV-compatible features”. This behavior has led to the use of a more colloquial PIV meaning that has little to do with its origins in the US government. Instead, it refers to secure cryptoprocessors (such as a smartcard) that have the capacity to meet the stringent requirements of the PIV standard.
Commercially, PIV is usually used in a similar manner to the US government’s implementation: it serves to identify individuals and control physical and network access. Whereas the government uses standardized PIV badges with photographs (as well as Common Access Cards, or CAC), private industries can place PIV credentials on a variety of compliant devices.
That said, PIV credentials are still usually deployed on smartcards embedded in ID cards to be used with card readers positioned at security doors or desktop workstations. A more recent trend has organizations using customized hardware security keys like the YubiKey with PIV credentials to securely authenticate a broad range of applications: desktop, Wi-Fi, VPN, web apps, and more.
How to use PIV for MFA

One of the most popular PIV-compliant smartcard devices is the YubiKey. Several models of the key are manufactured specifically for PIV-compliance and are used by governments and enterprises alike because of their strong, versatile MFA options (including biometrics) and ease-of-use.
As a Yubico Partner, SecureW2 has developed a Yubico Credential Management System that allows you to automatically configure and manage YubiKeys at enterprise scale, including configuring YubiKeys for PIV-compliance. Want to know more about our YubiKey-PIV solution? Talk to our experts today!
But picking out the device is the easy part – managing the PIV credential lifecycle is another beast entirely. PIV uses X.509 digital certificates to achieve the highest level of identity assurance. Certificates need to be issued and managed by a PKI, which can be a hefty time and resource investment for an IT team that doesn’t have PKI management experience.
PIV Alternatives
Two additional standards have been created using the foundation established by PIV, though neither have seen widespread adoption.
PIV-I (Personal Identity Verification – Interoperability) is a variant of PIV with much of the same requirements. It was created in response to a need of the US federal government to be able to manage the identities and access of guest users (like contractors). It is compatible with the same architecture as PIV, but doesn’t necessarily have the same rigor because it does not mandate the same requirements.
CIV (Commercial Identity Verification) is an alternate protocol based on the PIV framework -, the primary difference being less stringent standards. The lower standards were meant to reduce the barrier to entry and encourage commercial adoption.
In practice, however, CIV has yet to see widespread use. Instead, most enterprises simply use the regular PIV standard as a framework to set up their own internal authentication security with better security than CIV offers.
Manage PIV Credential Lifecycles with SecureW2
PIV is one of the best methods to implement MFA that can protect both physical and virtual assets.
However, the continued effectiveness of PIV security relies on efficient management in the backend. SecureW2’s PIV solution covers the entire lifecycle of a PIV credential:
- Identity proofing
- Certificate provisioning
- Authentication and authorization event logging
- Retirement/revocation/reissuance
Don’t be intimidated by the need for a public key infrastructure. SecureW2’s Managed Cloud PKI supports the PIV standard, and our expert support engineers are on standby to help you configure and deploy your upgraded network. SecureW2’s Managed Cloud PKI supports the PIV standard, and our expert support engineers are on standby to help you configure and deploy your upgraded network. Automating certificate management for Wi-Fi, VPN, and other systems streamlines and secures workplace environments while providing a smooth, password-free authentication experience.
We have affordable options for organizations of all sizes. Click here to see our pricing.