3 Security Advantages of a Cloud RADIUS Server
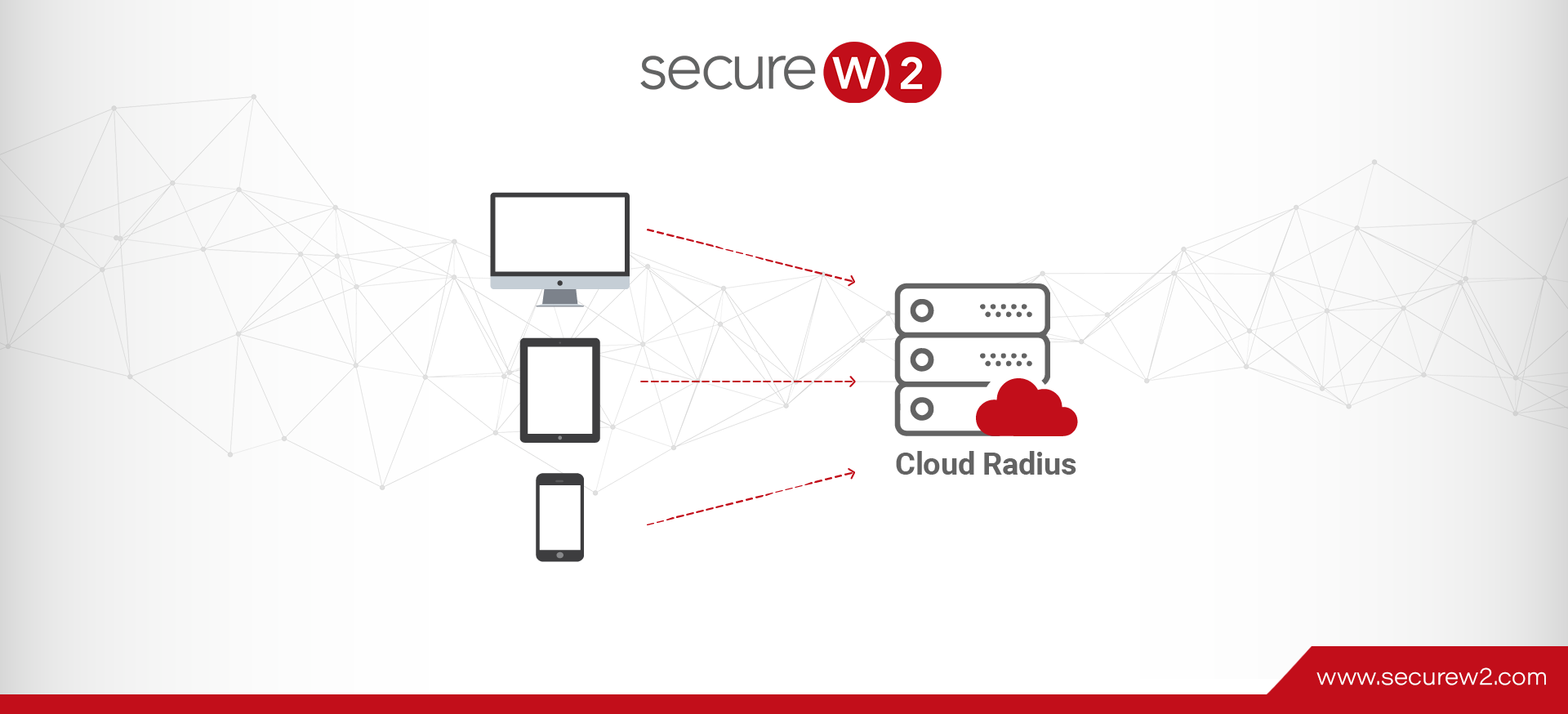
In order to successfully configure a WPA2-Enterprise network you must have a RADIUS server. The RADIUS authorizes and authenticates users signing into the network and eliminates any speculation into who is using your network. A properly configured Cloud RADIUS can ...
Read More