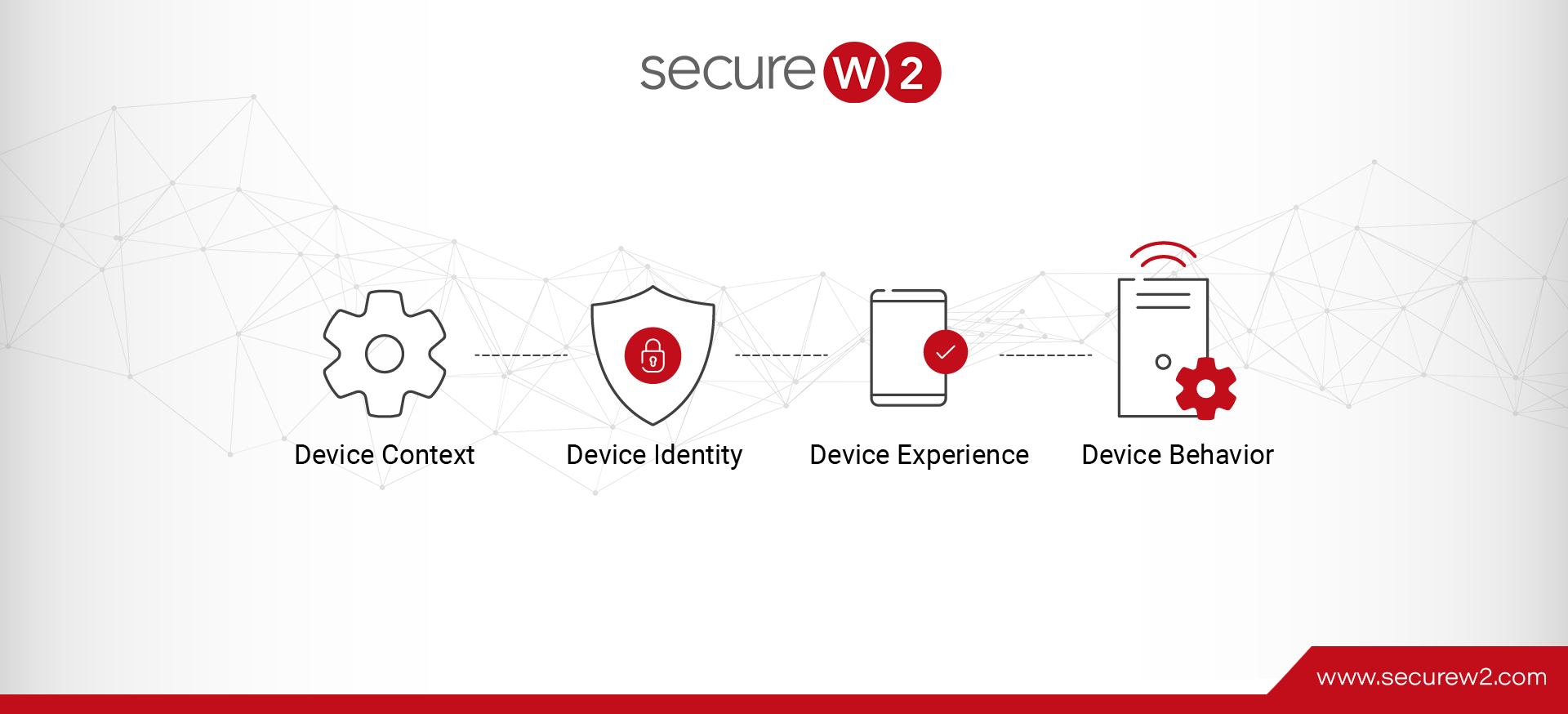
How to Improve Device Identity Context for Network Security
Protect your network from security breach by getting more visibility over your unmanaged and BYOD devices. Device Identity Context can help you improve network security. Continue reading to know more.
Read More