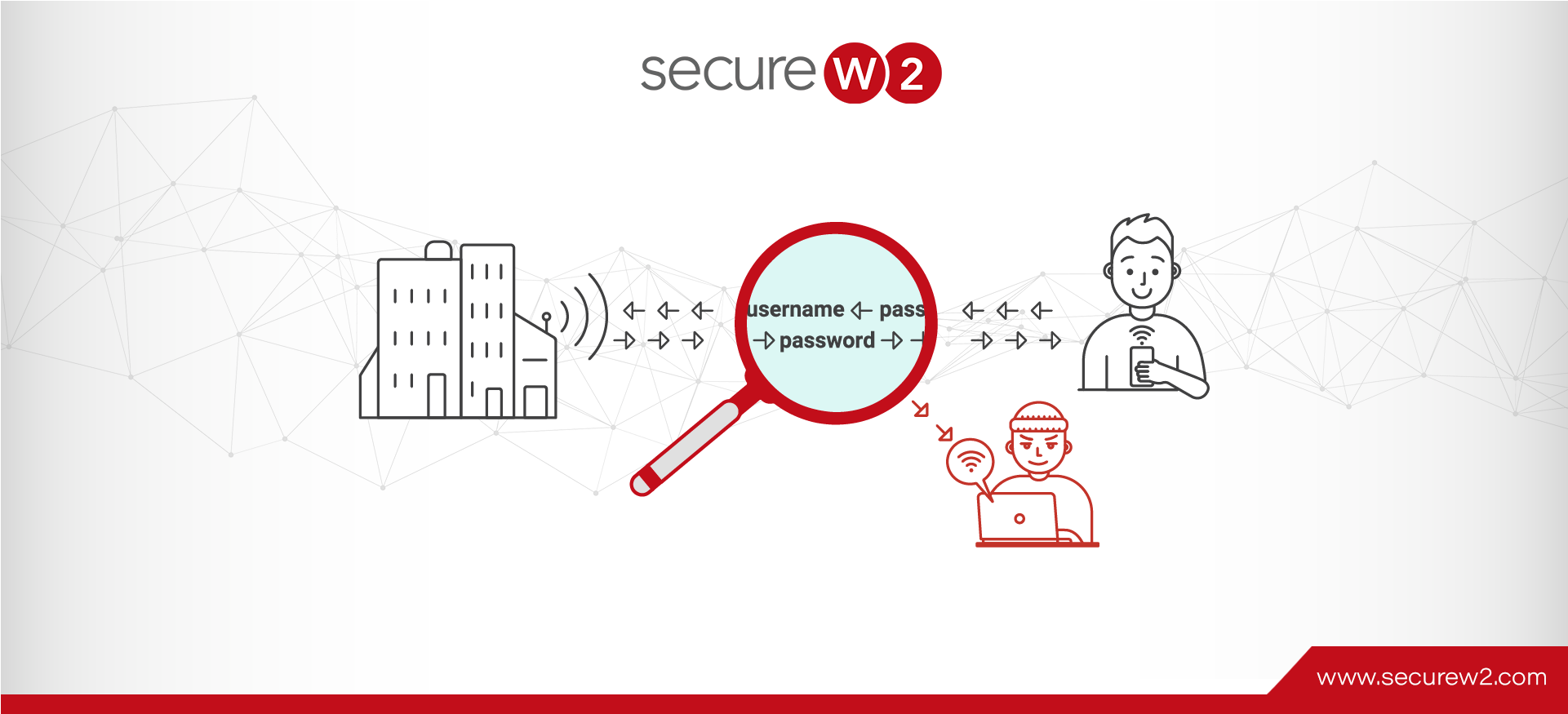
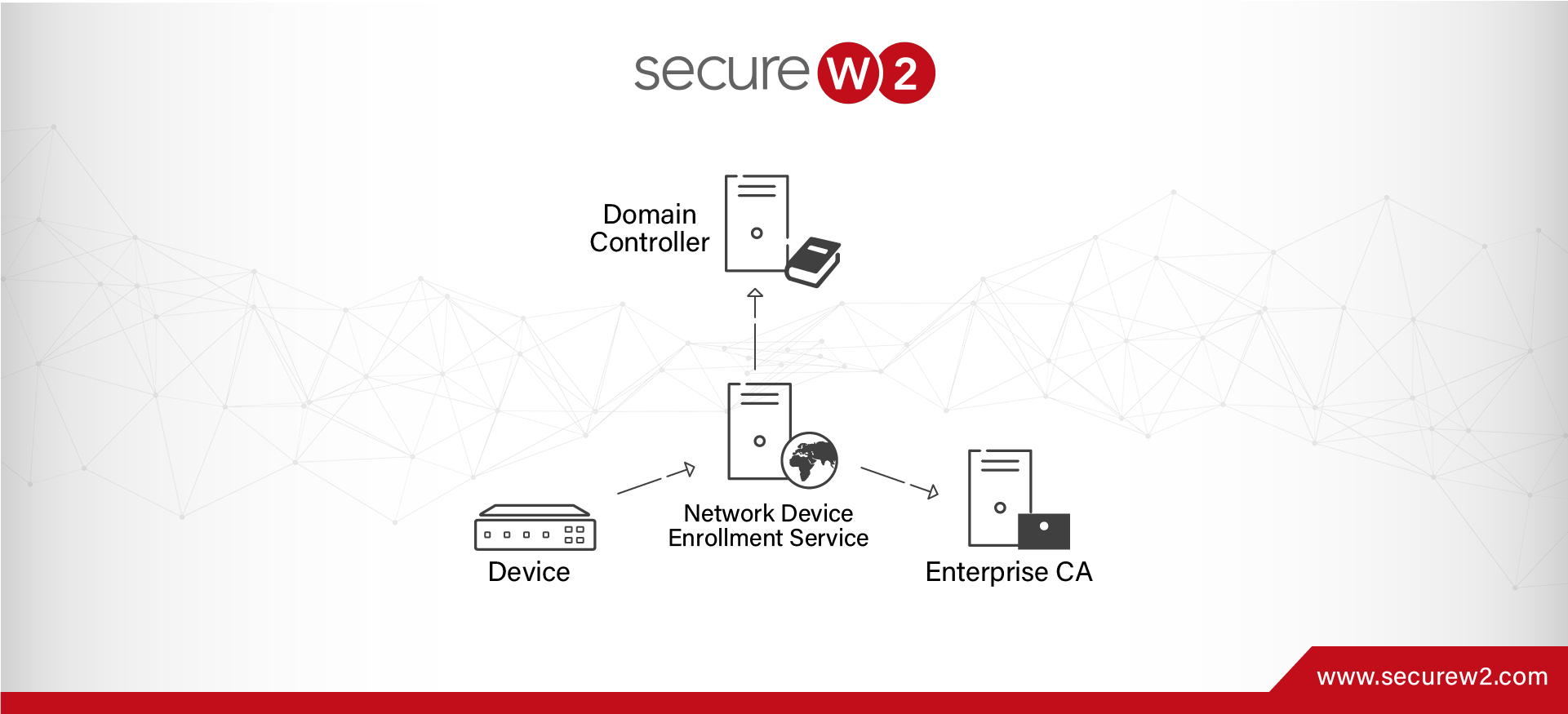
802.1X Port Security Simplified
Did you know that the cost of data breaches reached a whopping $4.35 million in 2022? Data breaches cost organizations a lot in penalties and lost business opportunities. Almost 68% of organizations that had suffered a breach had to increase ...
Read More