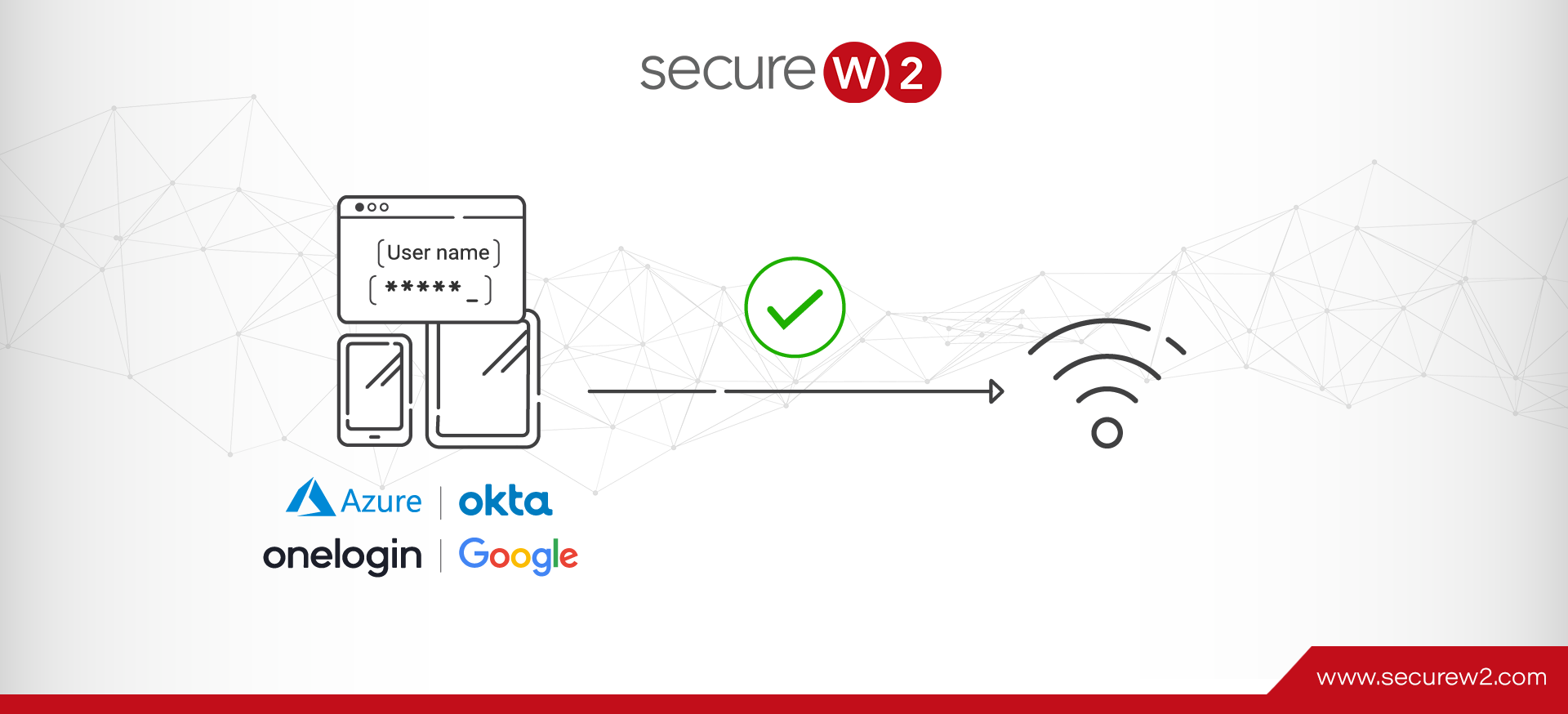
Introducing WebAuth Wi-Fi with Cloud IDPs
It’s no secret that open Wi-Fi networks are infamously insecure, and Pre-Shared Key (PSK) networks aren’t much better. If you tie your organization’s Wi-Fi to a single password and more than a handful of people know it, it’s only a ...
Read More