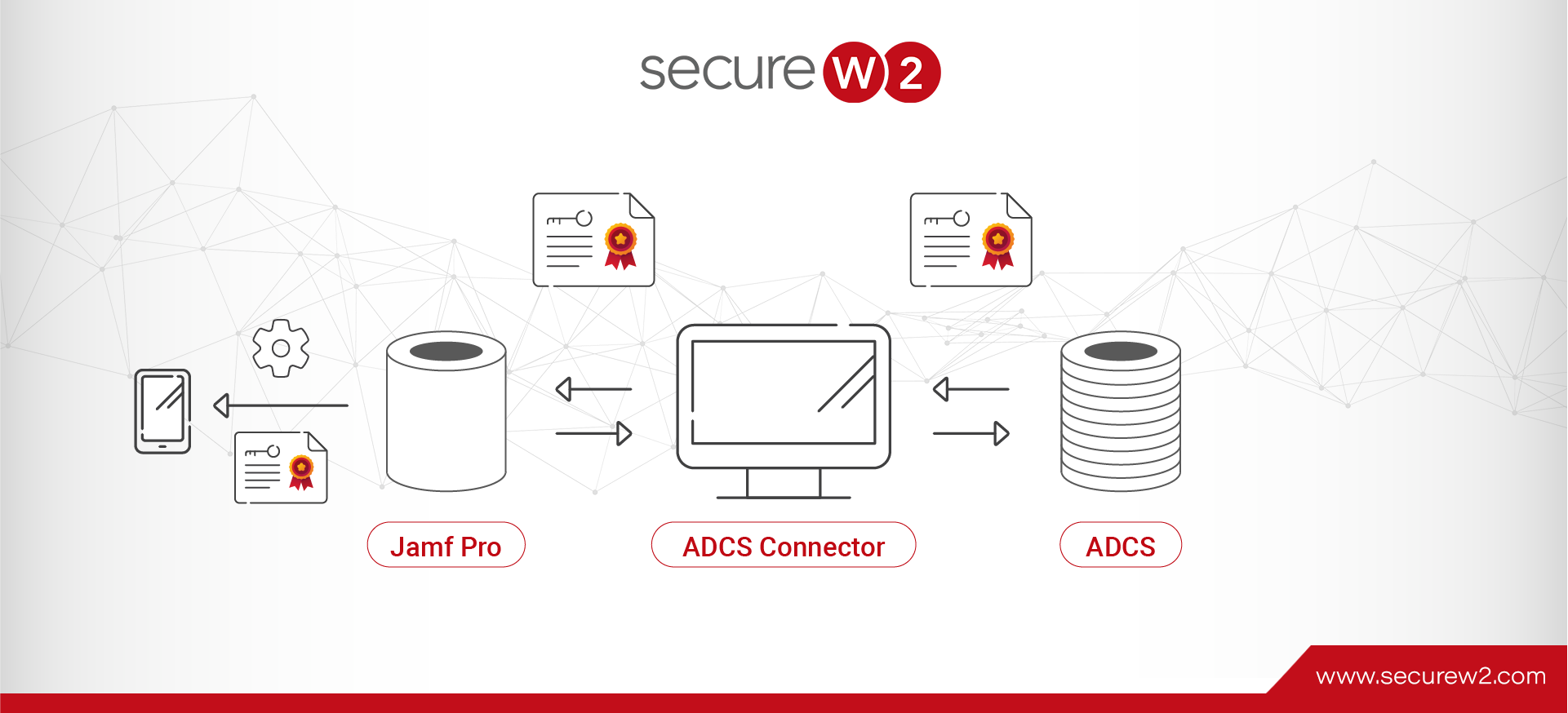
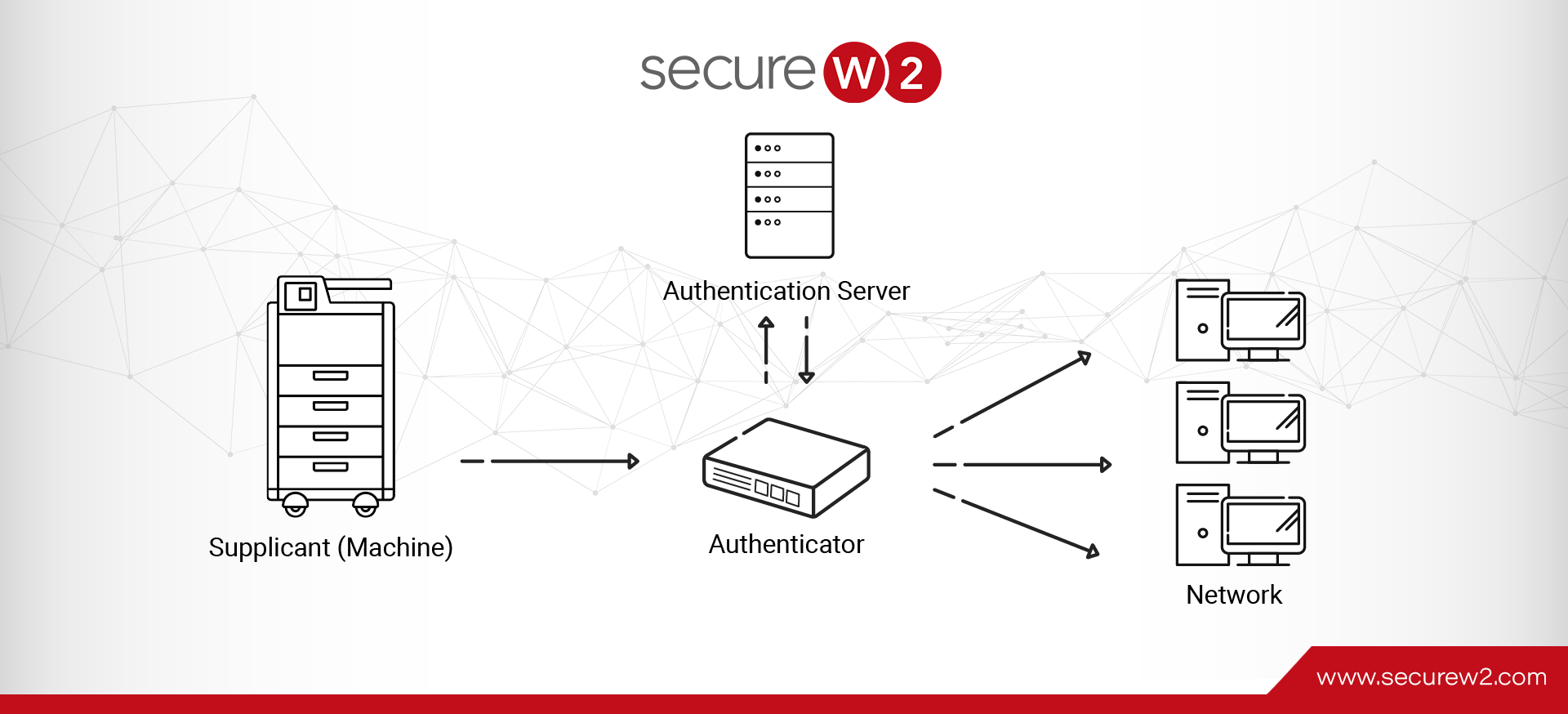
How to Use IEEE 802.1x Authentication for a Wired or a Wireless Network
IEEE 802.1x authentication is a standard for port-based network access control. It essentially requires devices to authenticate themselves before gaining access to network resources. This standard is versatile, working seamlessly with both wired Ethernet networks and wireless networks. Incorporating IEEE ...
Read More