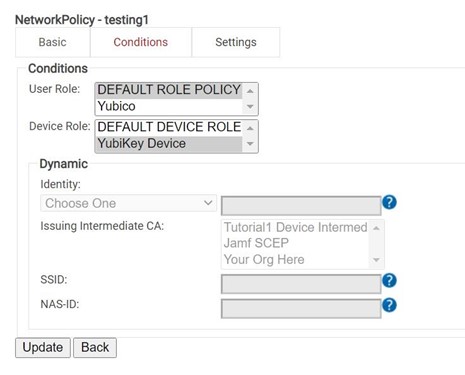
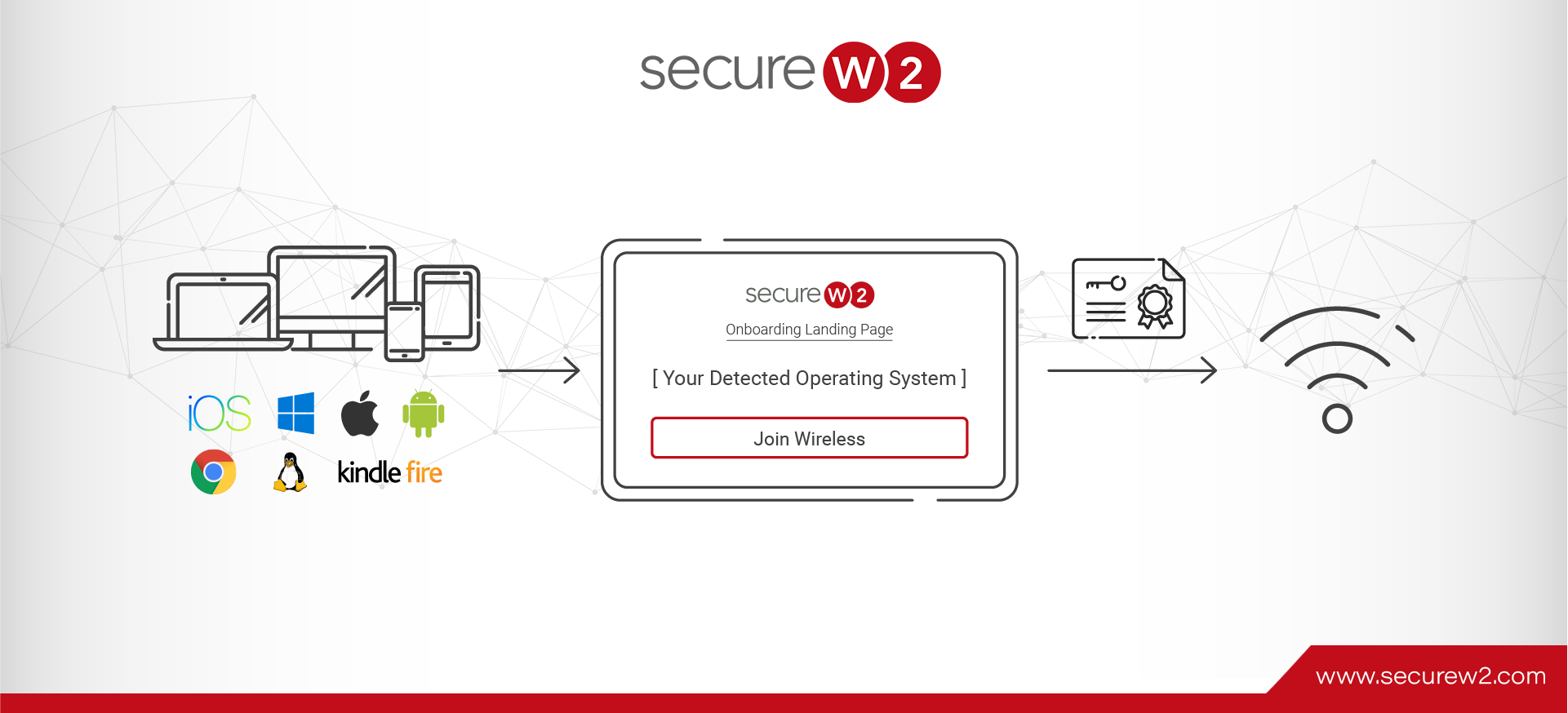
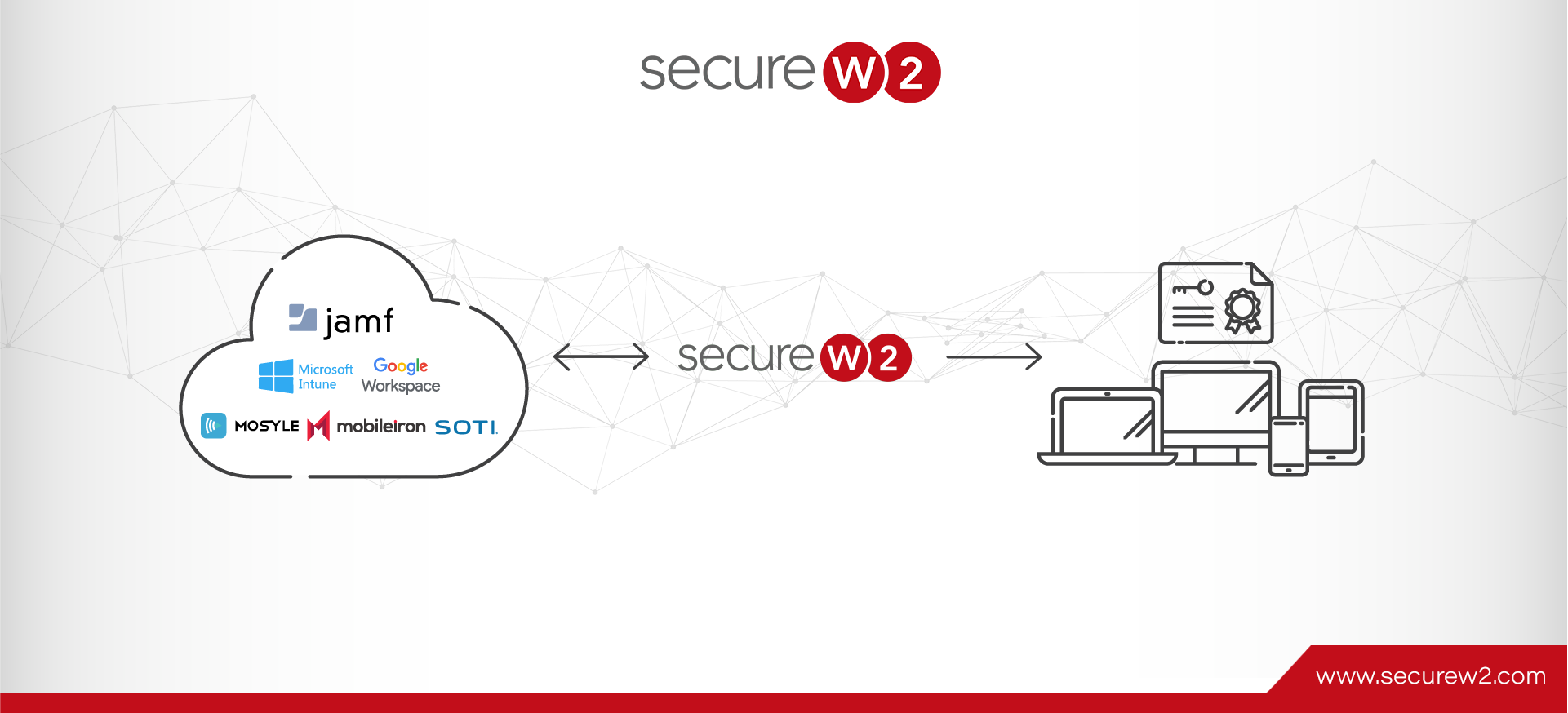
EAP-TLS vs. EAP-TTLS/PAP
Choosing the right authentication protocol is more than a matter of security. Authentication is the critical check ensuring only rightful users can access certain data or networks. The decision between implementing EAP-TLS or EAP-TTLS/PAP is more than a technical dilemma—it’s ...
Read More