Internal Or External CA- The Best Bet For Your Organization?
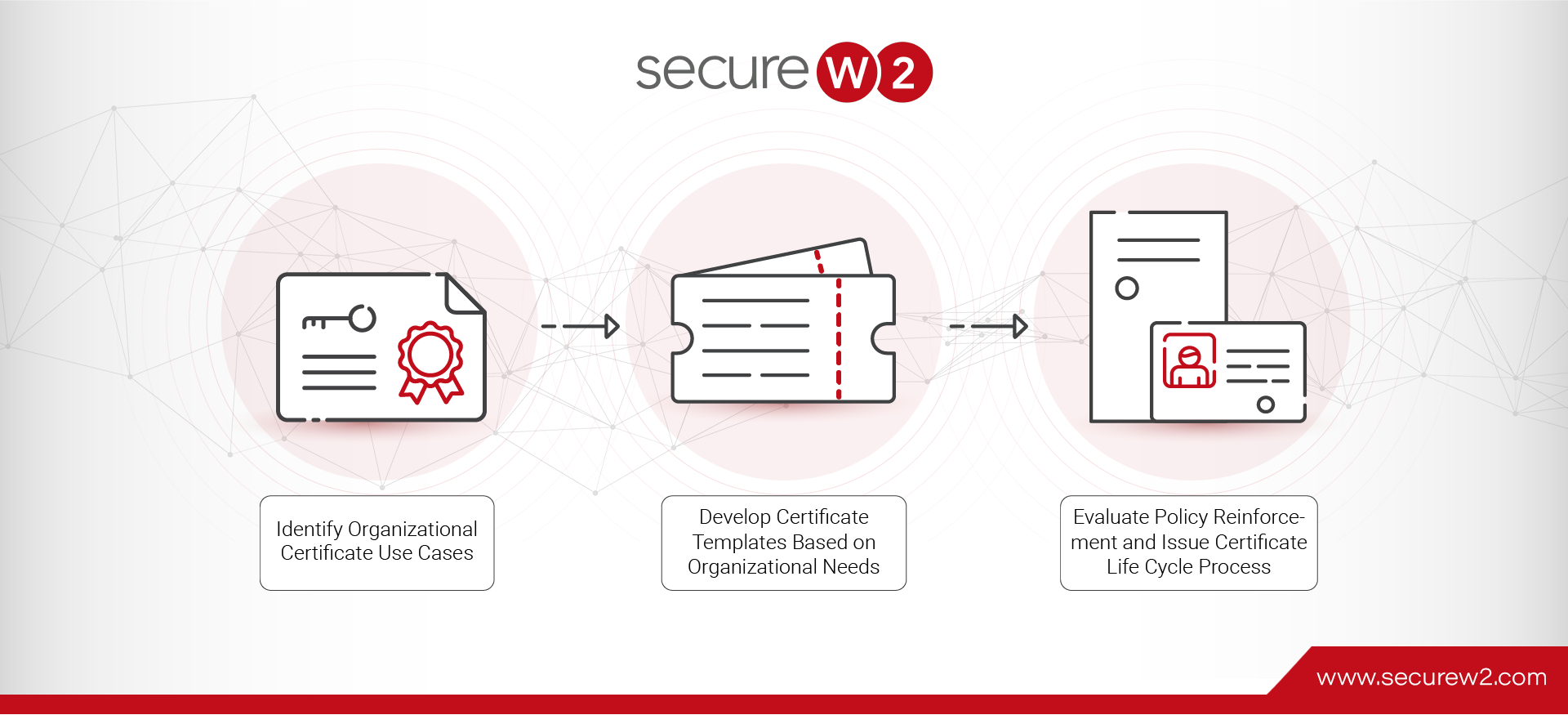
Public Key Infrastructures (PKI) are widely used by organizations because they secure communications among servers and clients with digital certificates and certificate authorities (CA). Certificates are a combination of cryptographic keys which encrypt user information stored within them. For certificates ...
Read More