A major issue that organizations face for authentication is managing different credentials for various web applications. Traditionally, web app authentication requires a unique and complex set of credentials to ensure only those with approved access can log in. However, this can lead to inefficiencies in a company and bottleneck an IT department. Considering that a majority of IT security respondents and individuals (55%) would prefer a method of protecting accounts that don’t involve passwords, it’s safe to say people forgetting their passwords or losing their credentials is a major hassle.
Luckily, Okta enables the use of one set of credentials to access all web applications within a network, this can be taken to another level by configuring users to authenticate with certificates. Digital certificates offer vast improvements to network security, efficiency, and user experience. Read from one of our customers how simple it is to make the switch. SecureW2’s Cloud PKI services work natively with Okta, allowing your users to easily enroll their devices for certificates.
What is PIV?
Personal Identity Verification (PIV) is a security standard detailed in NIST FIPS 201-2 that creates a framework for multi-factor authentication (MFA) on a smartcard.
While it was originally created by the government, PIV has widespread use in commercial applications. Organizations can use customized hardware security keys like YubiKeys with PIV credentials to securely authenticate a broad range of applications like Wi-Fi, VPN, web apps, and more.
PIV-Okta Authentication
Okta is unique in that it’s the only Identity Provider that allows end-users to use PIV Certificate Authentication as the first form of authentication. This significantly prevents organizations from phishing attacks. Organizations that use PIV for authentication distribute a physical smart card configured with identifying information that is used for authentication. A common PIV Smart Card is a YubiKey. Often, the PIV is paired with a PIN number to instill multiple factors of authentication, which is much more secure. Combining SecureW2 with Okta SSO allows you to use certificates without having to struggle with any complicated configuration.
Combining SecureW2 with Okta SSO allows you to use certificates without having to struggle with any complicated configuration.
Okta SSO With Certificates
The process of manually enrolling certificates for SSO is involved and mistake-prone, especially if left for network users to complete. It requires a high level of IT knowledge to understand and presents many opportunities for misconfiguration. To ensure accurate configuration, we recommend you utilize SecureW2’s JoinNow MultiOS onboarding software.
The JoinNow solution allows users to self-configure by completing only a few steps designed to simplify the user experience.
To set up with SecureW2:
- From the SecureW2 management portal, under PKI Management, select Certificate Authorities.
- Download your Root and Intermediate Certificate Authorities
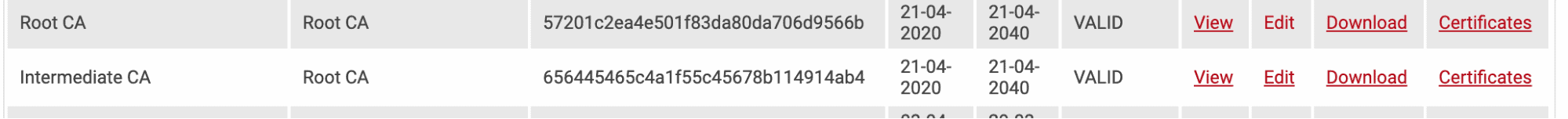
- Combine your Root and Intermediate Certificate Authorities and save as a .pem file.
In Okta:
- Under Users, go to Social and Identity Providers.
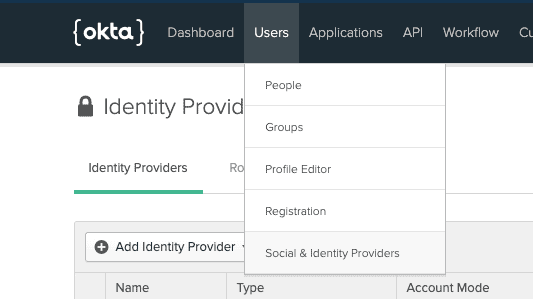
- Go to Add Identity Providers.
-
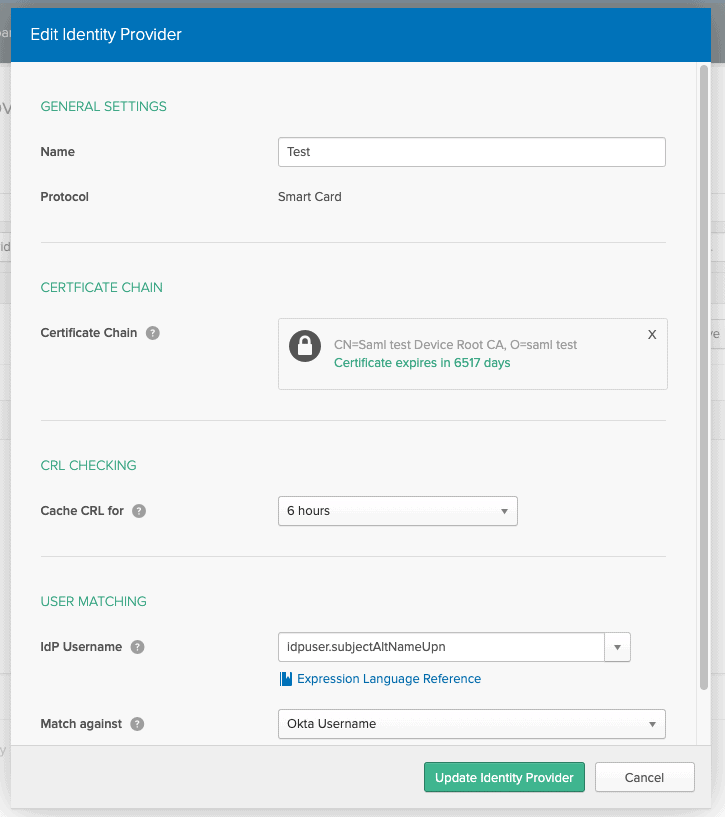
- Upload your combined CA’s to the Certificate Chain.
- Configure IdP username as configured in the screenshot.
- Match against Okta Username.
Congrats! You are now properly configured for certificate SSO authentication. Watch the video below for a complete step-by-step guide.
Make Okta Certificate SSO Easy With SecureW2
By adding certificate capability to Okta SSO, an organization can offer pinpoint security while ameliorating user experience. Certificate-based authentication protects against over-the-air attacks and prevents a user’s identity from being exploited by another. If you’re interested in learning more about SecureW2’s #1 rated service, check out our Okta solutions page here.
