Network Access Control Service
Designed for Your Cloud
Enforce network access control (NAC) for trusted identities with SecureW2's agentless 802.1x platform.
Leverage policies from Okta, Entra ID, Jamf, CrowdStrike, and more to ensure only trusted, compliant users/devices access the network.
Certificates are Critical for Network Access Control
Our Certificate Lifecycle Management solution was designed to seamlessly extend your cloud identity environment. Create as many certificates as needed based on your identity infrastructure's user and device groups. Our managed cloud PKI solution allows you to create certificates for:
- Network Authentication (Wi-Fi and VPN)
- Application Access
- Code Signing
- Smart Cards/Yubikeys
- Desktop Login
Network Access Control
For All Your Devices
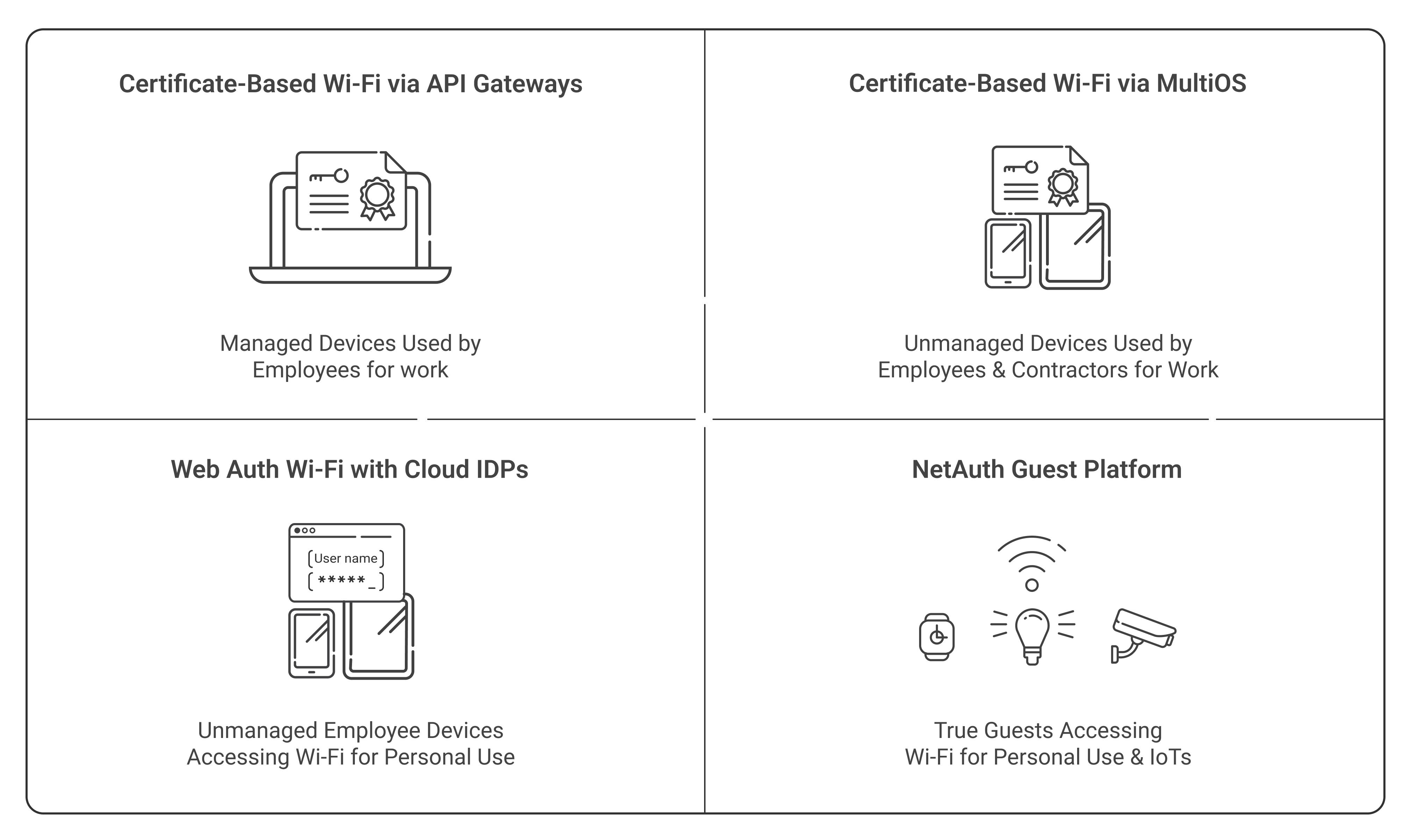
Certificate-based authentication may be the highest level of Network Access security, but it’s not always feasible for all your devices. Guests or employees using personal devices on the enterprise network can’t adhere to the same security posture as other users. Fortunately, our NAC solution can provide unique security controls for every type of user you might have.
- Certificate-Based Network Access: Easily issue certificates to all endpoint devices for managed and unmanaged systems used for work
- WebAuth Wi-Fi with Cloud IDPs: Secure Captive Portal for network access. Great for tying BYODs to Azure AD, Okta, Google, or OneLogin credentials.
- NetAuth Guest Platform: Allow guest users and IoTs access with our self-service login functionality or through access sponsored by your employees.
What Real Customers Have to Say About SecureW2
At SecureW2, we have a laser focus on making products and services that customers love. But don’t take our word for it, check out what some of our customers are saying:

5-Star Support Experience - Thorough assistance for planning, testing and implementation -Fantastic functionality - Thorough Integration Support


The implementation was seemless and easy. It worked immediately, and the individuals working with us were able to tell us exactly what to do.


With SecureW2, we are finally able to stop using user name an passwords for Wi-Fi authentication and strictly use machine based certificates. This has alleviated several pain points with our users.

Very little time was spent configuring the product. SecureW2 was able to help walk my team through all necessary configurations to create our PKI environment and automate certificate deployment. Since then everything has simply just worked and is integrated perfectly with out device lifecycle.

The White Glove Service made it easy to implement and connect to our services The team has been very knowledgeable, And implementation into the network was very simple.
Network Access Security Designed for Your Cloud
Leverage passwordless authentication through digital certificates for a more secure connection to any user and device connecting to your network. Digital certificates enhance network access control as they are non-exportable, providing a unique identity context and making network segmentation easier.
Enforce Network Access Control Policies in Real-Time
Passwordless security for your RADIUS requires a robust framework to authenticate devices, networks, and apps strongly. Eliminate frustrating password complexity and reset employee policies on corporate networks and devices while significantly improving authentication security for Wi-Fi, VPN, Single-Sign-On, and more.
- Tie user/device identity to every connection for detailed tracking and segmentation.
- Avoid unauthorized users/devices from accessing the network.
- Divide your network into smaller VLAN segments to prevent attacks on the system surface.
- Lookup user/device status in all significant Cloud Identity Providers to authenticate them in real time; auto-revoke certificates when lookups fail.
Certificate Lifecycle Management Designed for Your Cloud Environment
With SecureW2, using digital certificates for network access control is easier than ever. Our Certificate Lifecycle Management solution extends your cloud environment, automating the certificate lifecycle based on real-time data from your Cloud Identity. Now, you can use all your Azure, Okta, Jamf, or Intune policies to automate certificate management.
- Search for users/devices and easily view all their digital certificate lifecycles and authentication events in one place for easy troubleshooting and management.
- Simple and secure. Offers protection for Private Keys using FIPS140-2 Level 3+ standard HSM's.
- Integrate with ease to nearly every device management system or with BYODs/unmanaged devices.
- Automate certificate enrollment and revocation to all your managed devices through our APIs.
- Total cost of ownership (TCO) is less than a third of comparable on-premise PKI solution.
Auto-Enroll Certificates to Managed Devices
Certificate distribution and management for all your managed devices with no need for complex infrastructure changes.
- Zero-touch certificate distribution and renewal via extensive APIs including SCEP, JSON, WSTEP, EST, and more
- Auto-revoke certificates through your MDM when a user/device leaves the organization.
- Proven integration with all major MDMs including Jamf, Workspace One, Soti, Mosyle, MobileIron, Meraki, and many more
All it takes is two easy steps:
- Step 1: Configure your MDM platform with our PKI services.
- Step 2: Send out configuration profiles directing managed devices to auto-enroll for a certificate and self-service for 802.1X.
Onboard BYODs to Your Network Easily
BYODs and unmanaged devices don’t have to be complex or time-consuming to configure for secure network access.- Provides passwordless enrollment for robust authentication.
- Prevents unauthorized users and devices from accessing confidential/unauthorized data.
- Stop Over-the-Air Cyber Attacks from Intercepting Sensitive Information.
- Integrates natively with every major Identity Provider. Entra ID, Okta, Google..etc.
See for yourself how user-friendly the Network Access process can be!
Network Access Control FAQS
How Does a PKI and RADIUS Enable Network Access Control?
What Network Access Control Policies Can Be Configured in SecureW2?
How Does a Public Key Infrastructure (PKI) Enable More Robust Network Security Policies?
- User Attributes
- User Groups
- Device Serial Number
- User Email
- Operating System
- Whether the device is managed or unmanaged
- Issuing Certificate Authority
- Model Number
- MAC Address
- Certificate Validity
Why Should I Consider Transitioning Away from Password-Based Network Authentication?
How Do Your PKI and RADIUS Integrate with Our Infrastructure?
Can I Use the Security Policies from My Cloud Identity Provider on Your Platform?
Can I Leverage My Security Policies from my MDM with Your Platform?
Does Your Platform Offer Network Access Control Solutions for IoT Devices that Can’t Support Certificate-Based Authentication?
How Can We Allow Guest Network Access without Compromising Network Security?
Cloud RADIUS offers an easy-to-use Web Authentication captive portal as one option. It works by presenting a captive portal when users join the network. After their credentials are validated, they are authorized to access the network. The MAC Address is saved for subsequent authentications and for admins to understand and track the users and devices using the network.
JoinNow NetAuth is another product by SecureW2 that allows secure guest network access without compromising network security. Your guests can now access your network through self-registration or sponsored access. The JoinNow NetAuth also allows you to automate access policies where you can determine the level of access that can be provided to a guest on your network. Your guests can access an encrypted network combined with SecureW2's JoinNow MultiOS.