[vc_row padding_top=”0px” padding_bottom=”0px”][vc_column fade_animation_offset=”45px” width=”1/1″][vc_column_text]
What is a Certificate Authority?
A certificate authority (CA) is an entity that distributes digital certificates to devices. They assist in validating the identities of websites, individuals, and devices before administering digital certificates to them.
In a PKI system, the client generates a public-private key pair. The public key and the end user’s information are sent to the CA. The CA then creates a digital certificate consisting of the user’s public key and certificate attributes verifying that the information is correct. The certificate is signed by the CA with its private key, solidifying the legitimacy of the certificate.
Certificate authorities are undoubtedly an integral part of a PKI, which can boost security tremendously. SecureW2 Cloud PKI service allows you to create CAs and distribute certificates with ease. It’s also cheaper than on-premise alternatives as maintaining a cloud PKI costs ⅓ of the price of an on-prem PKI, see how we helped one of our customers here.
In this article, we are going to explain what a Microsoft CA is and how to best take advantage of one.
What Is A Private Certificate Authority?
Private CAs are locally hosted certificate authorities usually meant for internal use only. A private CA is only trusted by users within the organization where it was created, usually a large company or university. The potential benefit of this is that with fewer links in the chain of trust there is less potential for a breach of information, which makes them perfect for high-security internal applications.
While it’s possible to generate your own private certificate authorities, the process is not very straightforward. Luckily, companies have created software that can allow you to take advantage of certificates without building a PKI from the ground up. These solutions can be critical since a misconfigured or an expired private CA can leave your network vulnerable and at risk.
Microsoft’s Certificate Authority With AD CS
One solution is Microsoft’s Azure AD Domain Services (AD DS), which provides customizable resources for issuing and managing digital certificates used in software security systems that employ public key technologies. Microsoft offers their own CAs so Microsoft-based environments can implement a Public Key Infrastructure (PKI) with AD CS.
Organizations running on Microsoft environments can use a Microsoft CA to leverage Active Directory and Microsoft certificate services to distribute certificates to all your domain-connected devices through group policies. Microsoft CA services are also free (technically, although human resources required to run them actually make them one of the most expensive PKI solutions) because they’re included in the Windows server.
It’s not an easy task deploying and managing a Microsoft CA. You will need a dedicated team with PKI experience in order for the implementation to go smoothly. After the setup, your team needs to stay up to date with the best PKI practices to maintain uptime and reliability. That involves a lot of meetings and decisions to be made.
Microsoft CA’s come with hidden costs of hardware, hiring a team of experts, and annual maintenance by that team of experts. Those expenses can add up, making the claim of “free” virtually meaningless.
Private CA Management Software With SecureW2
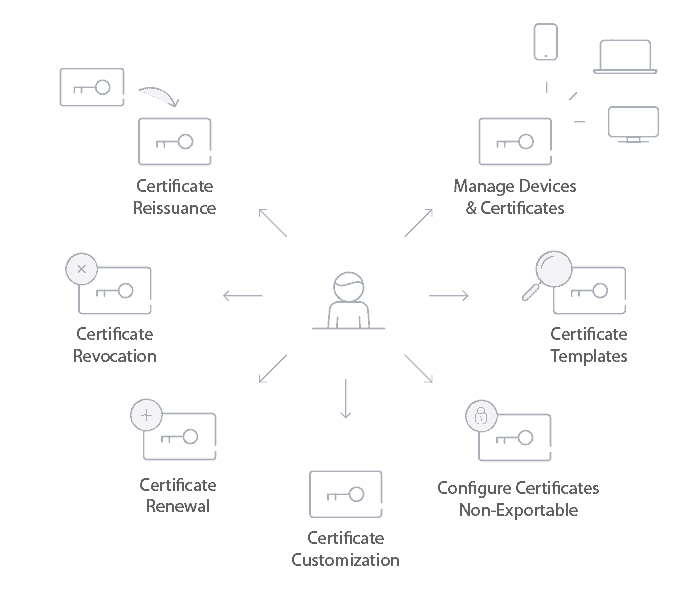
You can skip the configuration and hassle by using SecureW2’s advanced PKI. Our state-of-the-art management tool allows you to benefit from having a private CA without the associated inconveniences that come with them. You can create both root and intermediate private CAs in minutes, and manage and customize your CA ensuring all your security needs are met. It comes with a suite of certificate authority management features so you can customize certificate expiration based on a user’s status, and ensure no certificate expires without notice with our awesome notification features.
SecureW2 also allows you to integrate any SAML/LDAP Identity Provider with your Private CA, which makes it simple to issue certificates, create robust policies, and create custom certificate templates based on user groups that already exist in your directory. Our Cloud RADIUS can even perform Identity Lookup on any cloud directory, providing another security measure to your network.
Managing Certificates on Azure AD
Below, we’ve listed a few features that SecureW2 can provide when combined with a Microsoft CA and how they simplify network management.
Certificate Templates for Azure AD
Certificate templates are easier to configure and manage with SecureW2 because our GUI is more intuitive than AD CS. There’s no need to duplicate default certificates and fewer steps are involved. Admins can increase security by creating network groups based on access level permissions to configure a template for each respective group.
Azure AD CRL
RADIUS servers can view all the revoked certificates with a certificate revocation list (CRL) so it knows which certificates are still valid. This list is downloaded periodically so the RADIUS server stays up to date. SecureW2 gives admins the ability to adjust update intervals to ensure the CRL is always up to date.
SecureW2 uses industry-first technology to allow our Dynamic RADIUS to talk to your IDP and enforce policies for your users depending on your needs without having to revoke or reissue certificates, increasing overall security for your network. This takes care of any potential security lapses that may occur in between download intervals.
Managed Device Gateways
SecureW2 gives admins the ability to build a SCEP gateway for certificate enrollment and policy configurations. Instead of wasting time manually configuring every single device or leaving it up to the end-user, admins can configure a SCEP gateway to push out payloads that enable managed devices to configure themselves for certificate enrollment.
If your Azure environment contains Microsoft Intune, check out our guide on integrating SCEP to enroll certificates on Intune.
Integrating a Microsoft CA with SecureW2
The added cost of running an on-premise PKI without a lot of useful certificate management features is hard to justify. Not to mention that manually configuring every device with a certificate is tedious and simply not an option for larger organizations. Your IT department is busy enough without the extra workload. Instead of all the headaches, use SecureW2’s software to simplify device onboarding for your devices.
[/vc_column_text][/vc_column][/vc_row]