In the current digital environment, the proper management and security of devices within organizations are of the utmost importance. Mobile Device Management (MDM) solutions enable organizations to manage “managed devices” in this regard effectively.
To achieve optimal security and safeguard against potential threats, it is imperative to adhere to the recommended best practices for MDM security. In this article, we’ll outline best practices for administering devices with MDMs, emphasizing SecureW2’s role in assisting organizations in adhering to these best practices.
Click here for a case study on how our client successfully transformed their network with our 802.1X deployment solution.
1. Implementing Secure Authentication Protocol
Avoid relying on passwords
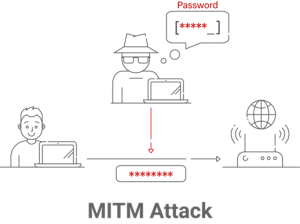
Relying entirely on passwords for MDM authentication creates serious security vulnerabilities, particularly when MDMs such as Intune and Jamf employ protocols such as PEAP (Protected Extensible Authentication Protocol). PEAP depends on passwords for authentication, leaving it susceptible to man-in-the-middle (MITM) attacks. In MITM attacks, hackers intercept communication between a user’s device and the MDM server, obtaining unauthorized access to sensitive data and possibly compromising the whole device fleet.
Strong login processes like multifactor authentication (MFA) should be used to strengthen MDM security and avoid such dangers. MFA demands that users present multiple proofs to validate their identity, making unauthorized access much more difficult. Organizations can strengthen their security posture and safeguard their managed devices and data from possible attacks by introducing MFA into MDM authentication procedures, resulting in a more secure and resilient MDM environment.
Utilize secure authentication protocols like EAP-TLS
EAP-TLS is better than PEAP with passwords for MDMs. EAP-TLS uses digital certificates and is a safe and strong authentication technique. This technique is more secure than password-based methods since it eliminates password guessing, brute-force attacks, and reuse.
EAP-TLS authentication begins with a TLS handshake between the MDM device and the server. This device shows its unique, secure digital certificate during this handshake. The MDM server checks the device’s certificate for forgery or compromise. After verifying the device’s identification, the MDM server and device create a secure, encrypted connection.
EAP-TLS uses digital certificates to authenticate the device and MDM server mutually, adding security. This minimizes man-in-the-middle attacks when unauthorized parties intercept and modify device-server communication. EAP-TLS also protects MDM data transport. TLS encryption protects sensitive device-to-MDM server data from eavesdropping and unauthorized access.
SecureW2 is a reputable solution provider specializing in installing and managing digital certificates, delivering a safe and smooth login experience across devices and platforms. Our solutions integrate effortlessly with popular MDMs such as Intune and Jamf, providing organizations with better security through strong authentication techniques like EAP-TLS, which depends on digital certificates for secure device and user authentication. This simplified method enhances the overall user experience and device security, making login procedures safer and more trustworthy for organizations.
2. Enforcing Device Encryption
Enable device-level encryption to protect sensitive data
Organizations must activate device-level encryption to safeguard sensitive data stored on managed devices. Device encryption employs powerful cryptographic algorithms to convert data into an unreadable format, ensuring that the data stays safe even if the device falls into the wrong hands. Organizations may protect their data from possible breaches and unauthorized access by making encryption the default option on all controlled devices and appropriately managing encryption keys.
The benefits and importance of encryption
Encryption provides substantial advantages and value to businesses. First, it protects crucial information from unauthorized access in case of device loss, theft, or data breaches. Encryption, by encoding sensitive data, guarantees that even if someone has physical access to the device, the data remains unreadable and secure.
Second, encryption assists organizations in meeting industry legislation and data security requirements, proving their commitment to protecting sensitive data. Furthermore, encryption improves an organization’s overall security posture by reducing the effect of security events. Organizations may guarantee secure device administration and communication by employing public key encryption and digital certificates, such as those supplied by SecureW2, preserving their data and promoting trust among customers and partners.
SecureW2’s involvement in public key encryption
SecureW2’s JoinNow Connector PKI is critical in providing public key encryption, which serves as the cryptographic underpinning for digital certificates used in MDM security. It protects sensitive data on managed devices from unauthorized access using public key encryption. Organizations can effortlessly enforce device protection across their fleet by combining SecureW2’s solutions with MDMs like Intune and Jamf, enhancing data security and satisfying regulatory requirements.
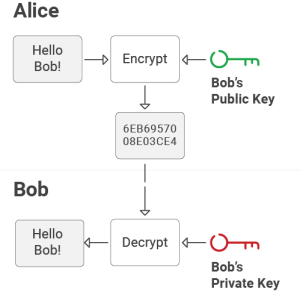
SecureW2 relies on public key encryption to provide secure device authentication and communication. Our digital certificates contain public and private key pairs, where the public key encrypts data and the private key decrypts it. This guarantees that authorized recipients may only access and decrypt sensitive data with the corresponding private key. Organizations can confidently adopt robust authentication mechanisms and safeguard their controlled devices and data with SecureW2’s experience in public key encryption and digital certificate management.
Set up strict access control policies for device enrollment
Organizations should create rigorous access control rules for device enrollment to guarantee safe management. This involves creating policies to validate user identities in the Identity Providers before giving access to enroll devices in the MDM system. Organizations may prevent unauthorized devices from accessing critical resources and guarantee that only authorized staff can register devices by implementing relevant policies.
Define user roles and permissions within the MDM solution
Establishing a safe and well-organized device management environment relies heavily on clearly defining user roles and permissions inside the MDM system. Organizations may restrict access to unnecessary features and data for employees to do their duties when roles are assigned based on their responsibilities and access needs.
SecureW2’s policy engine makes defining user roles and permissions in the MDM system easier. The policy engine allows businesses to establish role-based security with fine-grained access restrictions and custom permissions. This makes unauthorized parties less likely to access sensitive information and increases the system’s security.
3. Implementing Secure Configuration
Regularly update and patch MDM software
Maintaining a safe environment requires updating MDM software with the latest security patches and upgrades. Regular updates and patches fix known vulnerabilities and increase the MDM solution’s overall security. Organizations should implement a strategy for frequent upgrades to ensure that MDM software is up-to-date and protected against new risks.
Securely configure MDM servers and endpoints
MDM servers and clients must be set up securely to prevent security risks and ensure a safe device control environment. Follow best practices like setting safe communication methods, requiring strong authentication, and limiting access to only authorized users.
Update and fix software regularly set up role-based rights, and monitor users’ behavior to spot any strange behavior. By following these best practices and using SecureW2’s expert guidance, organizations can set up a strong and secure MDM system that keeps their controlled devices and data safe from possible security risks.
4. Conducting Regular Audits and Monitoring
Perform periodic MDM settings and configurations audits
Regular audits of MDM settings and configurations are required to uncover possible risks and verify policy adherence. Organizations should undertake frequent audits to check the efficacy of security measures, detect misconfigurations or holes, and take corrective action. Audits aid in the maintenance of a secure and well-managed MDM system.
Monitor devices for compliance and potential security risks
Continuous device monitoring is critical for ensuring compliance with security rules and quickly detecting possible security concerns. Organizations should implement monitoring systems to watch device behavior, spot abnormalities or non-compliant equipment, and handle security issues proactively. Monitoring contributes to the integrity and security of managed devices and the broader MDM architecture.
5. Educating Users and Promoting Security Awareness
Conduct employee training on MDM security best practices
Organizations should prioritize employee training to ensure all users understand and implement MDM security best practices. Secure device enrollment, password hygiene, preventing phishing attacks, and recognizing possible security concerns should all be included in training sessions. Organizations can empower their staff to actively contribute to the overall security of the MDM environment by training them.
Promote the importance of maintaining device security
To foster a security-conscious culture inside the organization, it is critical to emphasize the need to maintain device security. Employees should be informed about the risks of device compromise, such as data breaches or unauthorized access. Promoting frequent updates, strong passwords, and safe device use encourages employees to approach device security proactively.
6. Backing Up and Restoring Data
Implement regular data backups to prevent data loss
Regular data backups prevent irreversible data loss in device failure, theft, or other unforeseen circumstances. Establishing a backup strategy that includes device data transfer data will ensure that vital data is protected and can be restored.
Have a reliable data restoration process in place
In addition to implementing data backups, organizations should implement a dependable data restoration procedure. This procedure ensures that backed-up data can be restored efficiently and effectively, minimizing delays and mitigating the effects of data loss incidents.
7. Continuous Improvement and Updates
Stay updated with the latest MDM security practices
Organizations must remain updated on the latest MDM security best practices to maintain a secure MDM environment. This requires monitoring industry trends regularly, staying current on emerging threats and vulnerabilities, and actively searching out new security measures and best practices. Organizations can adapt their security strategies to counter evolving threats if they remain informed.
Regularly review and enhance security measures
Implementing security measures is not a one-time task; it necessitates periodic review and improvement. Organizations should perform regular security assessments and audits to identify MDM security vulnerabilities or deficiencies. By routinely evaluating security measures, organizations can identify areas for improvement and implement the required enhancements to maintain a robust and current security posture.
Integrated MDM Solutions for Enhanced Security
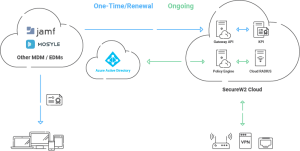
SecureW2 integrates seamlessly with almost all MDMs, which includes many prominent ones such as Jamf and Intune, providing organizations with a comprehensive solution for enhanced MDM security. Our integration simplifies the implementation of security measures, allowing them to maximize the potential of their MDM platforms. With SecureW2’s integration, organizations can manage their devices with greater security and efficiency.
SecureW2 has recently introduced an auto-revocation policy explicitly designed for Jamf and Intune. This policy automates revoking digital certificates, ensuring that compromised or unauthorized certificates are promptly rendered invalid. By implementing the auto-revocation policy, organizations can substantially reduce the risk of external infiltration and maintain a more secure MDM environment.
Many organizations employ our JoinNow PKI and Cloud RADIUS solutions. JoinNow PKI facilitates the entire lifecycle administration of digital certificates, allowing organizations to issue, renew, and revoke certificates more efficiently. Cloud RADIUS offers a scalable and secure infrastructure for authentication, enabling seamless integration between devices, MDMs, IDPs, and other network endpoints. SecureW2 enables organizations to strengthen their MDM security measures and defend their managed devices and data with these solutions.
Take control of your MDM security with SecureW2. Explore our integrated solutions and streamline your device management today.