Key Points
- Pre-Shared Key (PSK) networks are vulnerable to a range of layer 2 attacks.
- In PSK networks, one compromised key gives attackers access to the entire network, enabling exploits like ARP spoofing, DHCP starvation, or MAC flooding etc.
- SecureW2 enables 802.1X and EAP-TLS, where each device gets a unique, non-exportable certificate. This enables per-device revocation, hardware-backed integrity checks, and resistance to Layer 2 attacks.
WPA2-PSK is a standard wireless security protocol used in many networks worldwide, but we know that pre-shared keys (PSK) or passwords are pretty insecure. A PSK is a weak link that could lead to numerous Layer 2 attacks on your network.
Most organizations readily deploy measures to protect physical assets but overlook LAN security. It is a common assumption that if all your data is securely stored on cloud servers like Google Drive or Office 365, then there’s no need to secure your local network.
Even if all your organizational resources are stored in the cloud, they’re still vulnerable. A Layer 2 attack could easily compromise the network’s security, revealing other passwords to the attacker or interrupting your access to the cloud. This article will describe the Layer 2 attacks targeting networks protected only with a preshared key.
What is a Layer 2 Attack?
The Open Systems Interconnection (OSI) model comprises layers communicating with each other. Layer 2 transfers data between nodes across the physical layer of a network. It is known as the host’s physical address. Layer 2 processes raw data transmission from the physical layer and transmits it to the network layer.
The following are some Layer 2 attacks that can occur on your network:
Address Resolution Protocol (ARP) Attacks
Hackers use ARP attacks to gain access to user data. A hacker conducts an ARP attack by imitating a device and routing messages to himself instead of the original recipient. Every device has an IP address and MAC address. The hosts present on a network must know each other’s addresses to send or receive messages.
The hacker gains access to the network by pretending to be Host B. He sends a message to Host A to trick him into believing he is Host B. So, Host A will now send messages to the attacker initially intended for Host B. The hacker is now a Man-in-the-middle and the first point of communication whenever Host A tries to communicate with Host B. They are typically used for spying and elaborate cyber attacks.
Content Addressable Memory (CAM) Table Overflows

In a CAM Overflow Attack, a hacker connects to single or multiple switch ports to run a program that mimics thousands of MAC addresses on the ports. This switch accesses the CAM table and fills it to overflowing. Eventually, it cannot add more MAC addresses, so it fails open, thus flooding the traffic from new hosts through the ports on this switch.
A CAM attack converts a switch into a hub enabling the attacker to facilitate MITM attacks and eavesdrop on mutual conversations.
Spanning Tree Protocol (STP) Attacks
A Spanning Tree Protocol (STP) prevents bridging loops in a switched network, thus stopping broadcast traffic from becoming a storm. An STP network has a root switch on the top and is chosen based on the lowest configured priority. It identifies other switches and selects the root bridge when it boots up. Once the root bridge is set, the network anatomy is built based on its connectivity.
An STP attack happens when the hackers or attacker spoofs the root bridge of the anatomy. They broadcast an STP configuration change to force the STP to recalculate. An STP recalculation can cause disruption every time a root bridge is manipulated.
Media Access Control (MAC) Spoofing

MAC spoofing uses flaws in the MAC authentication bypass mechanism to orchestrate attacks on a network. It’s often considered one of the oldest attacks in the history of spoofs. MAC spoofing is easy to pull off as a device’s MAC address is simply a (sometimes temporary) serial number identifying a machine, which can be faked or changed without much hassle. MAC spoofing results in configuring unauthorized access points or simulating an access point to capture user credentials.
If a device unwittingly shares its network with a hacker, the rest of the network can also be compromised. You can prevent these attacks by disabling unnecessary ports, deploying firewalls, and using more robust authentication methods like MFA and digital certificates.
Switch Spoofing
Similar to a home router, a switch is typically available and awaiting connections from authorized users or devices. A hacker configures a system to spoof itself as a switch in a switch spoofing attack. The attack mimics the Inter Link switch (ISL) or the 802.1Q simultaneously with the Dynamic Trunking Protocol (DTP) to establish a trunk connection to the switch.
A switch spoofing attack can occur when the interfaces negotiate with a trunk. Another way to conduct a switch spoof attack is to connect a rogue switch to a switch port. Thus, to avoid switch spoofing attacks, you should disable trunking on ports that are idle and disable DTP on truck ports.
Double Tagging
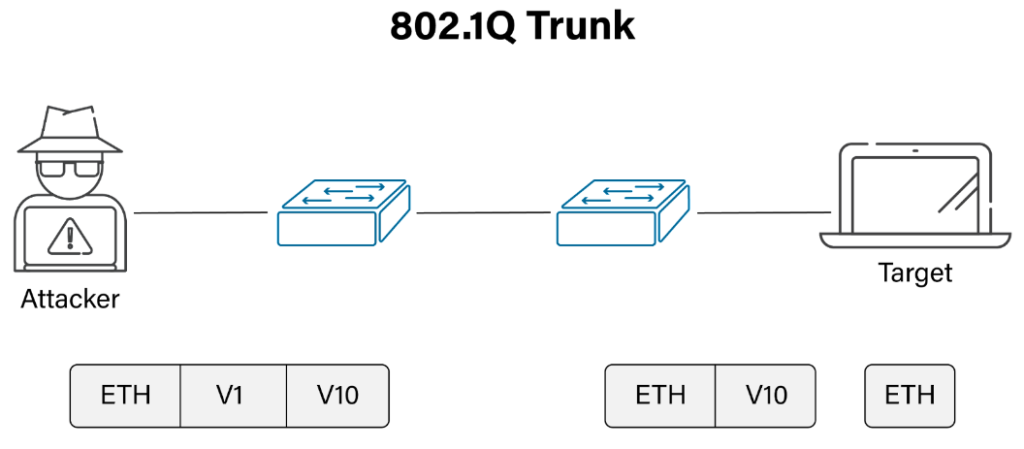
A double-tagging VLAN attack is another kind of VLAN hopping attack and is successful when the attacker connects to a native VLAN of the trunk port. A Double tagging attack is mostly unidirectional and takes advantage of the 802.1Q tagging and tag removal on many switches.
A hacker changes the initial frame and adds additional VLAN tags to the original structure. The outer tag is his original VLAN, and the inner tag is the victim’s VLAN. A hacker’s system must belong to the original VLAN of the trunk link. A double tagging attack can only happen on switch ports configured to use native VLANs.
Cisco Discovery Protocol (CDP) Reconnaissance
Cisco Discovery Protocol (CDP) is a proprietary protocol that CISCO devices can use to discover other CISCO devices and auto-configure to a network. Auto configuration simplifies the process of onboarding. However, attackers can easily sniff information from devices that CDP is broadcasting across its network.
A CDP is unauthenticated, which allows an attacker to devise bogus CDP packets and send them to the receiver through his connected CDP device. Suppose the hacker manages to gain access to your router through Telnet or SNMP, they can misuse the CDP data to discover the topology of an organization’s network at Layers 2 and 3.
The best way to avoid a CDP attack is to disable CDP on any device that may not need it.
Dynamic Host Configuration Protocol (DHCP) Spoofing
In Dynamic Host Configuration Protocol (DHCP) spoofing, a hacker acts as another person ( a DHCP server here). DHCP is a widely used protocol that provides information and other data to users, so any loss of DHCP control could threaten the whole network.
A hacker orchestrates a DHCP spoofing attack by placing a rogue DHCP server onto a network. The fastest DHCP server receives the first request when a client accesses the network and requests an address. If the rogue server responds to a user first, it can easily assign an address and control the device it chooses to use as a gateway.
WPA2-Enterprise and Securing Your Network with Digital Certificates
Using a single password to gate your network access is a serious vulnerability. It provides a single point of failure that, when broken, gives hackers free rein to penetrate your network even further, leading to outcomes such as:
- Attack surface expansion
- Lateral movement
- Privilege escalation
The alternative is to transition to a WPA2-Enterprise network, which gives individual users their own unique credentials as opposed to sharing one password. However, even using multiple passwords for network access can leave you vulnerable to attack given the numerous methods for stealing them.
WPA2-Enterprise and 802.1X are significantly more secure when digital certificates are used as the authentication mechanism instead of passwords. They offer a host of benefits, including the following:
- Greater Security
- Better End-User Experience
- Faster Authentication
Greater Security
Certificates use public-private key encryption to encrypt any information sent over-the-air. This means there aren’t any passwords being transmitted that could be potentially stolen.
Additionally, certificates grant administrators significantly more granular control and visibility over the network. That’s due to the fact that they have detailed templates that contain more information, such as the user’s operating system, email address, MAC address, device serial number, organizational department, and much more.
Better End-User Experience
Security has often come at the cost of convenience – or vice versa. As an example, consider all the measures end users have to take to ensure greater security with their passwords, such as using complex passwords, resetting them regularly, or never using the same one twice.
With certificates, you get the best of both worlds: convenience and security. Using certificates to access your network means your users no longer have to deal with disconnects when they reset their password, frustrating password complexity requirements or needing to manually enter passwords time and time again.
Faster Authentication
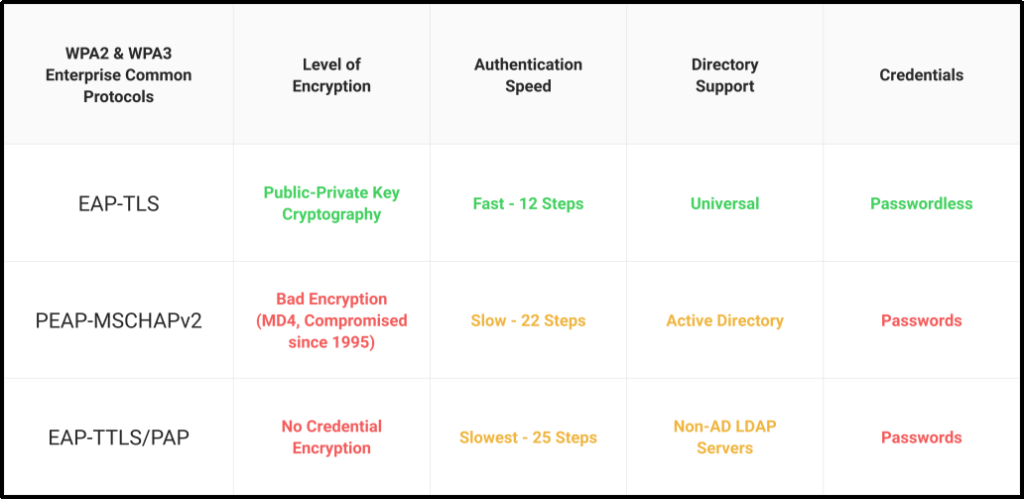
Fewer packets are transmitted when certificate-based EAP-TLS is used for authentication. As a result, end users are able to connect to your network even faster.
Initially, this may seem like a small benefit, but the time can really add up and ensure more time is spent being productive rather than setting up.
Leave Pre-Shared Keys Behind and Go Passwordless with SecureW2
In the past, doing 802.1X with EAP-TLS in the cloud securely has been tedious for administrators. Building and maintaining both a RADIUS and PKI demands technical knowledge and time. Now, however, there are modern cloud-based passwordless platforms like that provided by SecureW2 which make the transition quick, simple, and most importantly, secure.
Our platform helps organizations leave PSK behind with a turnkey managed PKI and RADIUS service that are designed to integrate with any network access infrastructure. We even streamline certificate issuance through a top-rated self-service onboarding technology for unmanaged devices or gateway APIs for managed ones.
Talk to our team of experts today to discover how our solutions can help you go passwordless.