For small and medium-sized enterprises, coordinating employees’ iPhone, iPad, and Mac devices may distract you from your primary responsibilities. Jamf assists businesses in addressing this issue. The affordable cloud-based solution streamlines the administration of mobile devices, allowing you to concentrate on your daily duties.
Here, we’ll explore Jamf, a robust device management platform developed exclusively for Apple products, including Macs, iPhones, and iPads. As an IT administrator, protecting the security and effectiveness of your organization’s fleet of Apple devices is critical, which is where Jamf comes in.
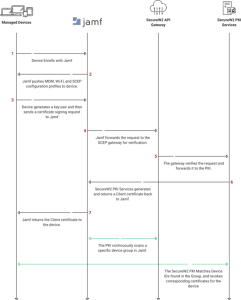
At the heart of a good Jamf setup is a well-configured RADIUS server. The RADIUS server is a central authentication and authorization center, allowing for secure user access to network resources. When hosting and configuring the Jamf RADIUS server in this context, it is imperative to employ the correct procedures. Learn how SecureW2 helped a hospital IT staff in healing their insecure network.
Whether you’re new to Jamf or looking to optimize your RADIUS server configuration, let’s dive into the realm of Jamf RADIUS server best practices to maximize your Apple device administration experience.
1. Selecting a Reliable Platform for Hosting the Jamf Server
Choosing an effective platform is the first and most crucial step in hosting your Jamf server. The hosting platform you choose can substantially impact the performance and overall efficacy of your Jamf server, making this a crucial decision for your device management operations.
The Significance of Choosing a Reliable Hosting Platform
The foundation of any successful device management system is reliability. A dependable and robust hosting platform ensures that your Jamf server is available and accessible at all times without interruptions or delays. This level of dependability directly increases the productivity and efficiency of your organization.
In addition, a dependable platform reduces the risk of data loss or security vulnerabilities, giving you peace of mind that your sensitive data and configurations are secure.
The Benefits of Handling Configuration Complexities
Configuring a Jamf server can be complex, especially when administering a large fleet of Apple devices with diverse settings and profiles. A competent hosting platform reduces this complexity by providing user-friendly tools and resources to expedite the configuration process.
An effective platform will help simplify onboarding complexities such as certificate management, Wi-Fi profile configuration, and security configuration. This saves time and decreases the likelihood of errors resulting in network vulnerabilities.
Onboarding Solutions for a Smooth Setup Process
Setting up a Jamf server from start to finish can be challenging, particularly for those unfamiliar with the platform. A reputable hosting provider recognizes this difficulty and typically provides exhaustive onboarding solutions.
These induction solutions may include step-by-step instructions, video demonstrations, and individualized support to ensure a seamless start-up. The objective is to ensure that you rapidly comprehend the essential features and can utilize the maximum capabilities of your Jamf server without encountering any unnecessary obstacles.
By providing a straightforward enrollment procedure, the hosting platform puts you on the path to effective device management from day one. Explore SecureW2’s solutions for the optimal onboarding experience and to ensure a seamless setup process. We provide exhaustive onboarding support and user-friendly resources that make setting up your Jamf server easier.
Understanding Secure Authentication Protocols
To keep private information secure and prevent unauthorized access, RADIUS servers must have solid security in place. Protecting against outside interference is essential, and a secure authentication system plays a significant part.
The Importance of a Secure Authentication Protocol for RADIUS Servers
A RADIUS server controls who may access a network by authenticating and authorizing their requests. Malicious actors might exploit weaknesses and obtain unauthorized access to your network if you don’t have a secure authentication procedure.
A reliable defense may be set up by using a secure authentication protocol to validate the identities of people and devices requesting access to a network. This verification procedure safeguards against data breaches and cyberattacks and prevents unauthorized entry.
Advantages of EAP-TLS
Extensible Authentication Protocol-Transport Layer Security (EAP-TLS) is an excellent example of a secure authentication protocol. The security provided by EAP-TLS in RADIUS contexts is well-known and frequently used.
Using digital certificates for authentication, the EAP-TLS protocol ensures that only authorized devices can connect to the network. This certificate-based method improves security by eliminating the weaknesses of traditional password authentication.
EAP-TLS also allows for mutual authentication, in which the server and the client verify the other’s identity. This mutual authentication method guarantees a safe and stable link between your devices and the RADIUS server.
While EAP-TLS provides great security, other authentication methods, such as PEAP (Protected Extensible Authentication Protocol), may have some flaws. Although PEAP is a widely used authentication technology, EAP-TLS offers higher security.
Their methodologies for certificate validation represent the primary distinction. PEAP only uses server-side certificates for authentication, but EAP-TLS verifies both client- and server-side certificates to provide better security. Because PEAP doesn’t have mutual identification, it could be vulnerable to some man-in-the-middle threats because it doesn’t protect against security risks.
Linking back to EAP-TLS, it’s clear that the mutual authentication feature makes it a safer choice. This feature ensures that the client and the server verify each other’s identities, creating a strong and trusted link.
2. Creating Jamf Configuration Profiles in a Sequential Manner
To make sure Jamf setup settings work well, you must follow a certain order:
A. SCEP Payload
Start by setting up the content for the SCEP (Simple Certificate Enrollment Protocol). This step makes it easy to register digital certificates so that devices can talk to each other securely.
B. Certificate Payload
The certificate payload can be sent after the SCEP payload is in place. This ensures the devices have the certificates to access network services safely.
C. Network or Wi-Fi Payload
Finally, pay attention to the network payload or Wi-Fi payload. This step includes setting up network settings like Wi-Fi access points so that you can join easily and safely.
Avoid Eliminating Production Profiles
When handling setup profiles, you must be very careful. Keep production profiles because doing so could prevent users from losing their certificates. Instead, use the right methods for managing user profiles to keep things running smoothly for users and keep the network safe.
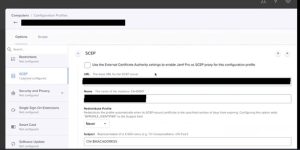
3. SCEP Proxy vs. SCEP Payload
Regarding Jamf, the Simple Certificate Enrollment Protocol (SCEP) has two essential parts: the SCEP Proxy and the SCEP Payload.
Difference Between SCEP Proxy and SCEP Payload
SCEP Proxy
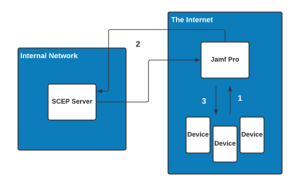
The SCEP Proxy is suggested if you want to improve the security and control of device registration. It sits between the device and the SCEP server and helps them communicate.
When a device wants a certificate, it talks to the SCEP Proxy. The SCEP Proxy then sends the request to the SCEP server. This arrangement makes the registration process safer and stops people from misusing certificates or getting them without permission.
SCEP Payload
The SCEP Payload, on the other hand, tells the device to talk to the SCEP server to get the certificate. This way works, but it doesn’t have the extra layer of security that the SCEP Proxy does.
Why Choose the SCEP Proxy?
Because network security is so important, using the SCEP Proxy is highly suggested. By using the SCEP Proxy, organizations get better control over the certificate registration process. This makes it less likely that people who shouldn’t be able to access network resources will be able to do so.
Using the SCEP Proxy, managers can ensure that authentication and certificate issuance are safer and more reliable. This improves the security of the device control system as a whole.
SecureW2’s API Gateway adds more protection to Jamf-managed devices than a standard SCEP Implementation. The API keeps an eye on certain Computer or Device groups for new devices and quickly takes away certificates for any new devices that are found.
This changing process lets admins set their own conditions, like when a certificate was used or Device Compliance, to determine if it is still current. So, organizations can make sure that only legal and authorized devices can use network resources. This improves network security and makes device control more efficient as a whole.
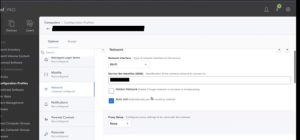
4. Configuring Secure Wi-Fi Profiles in Jamf
Creating Wi-Fi settings in Jamf is an important part of managing devices. Here’s a quick look at the process and the most important things to be mindful about:
Configuring Wi-Fi Profiles
In Jamf, you can make Wi-Fi settings that let devices join easily and securely. These profiles have network options, like Wi-Fi access points and login information, so devices can easily join the network.
SCEP as a Proxy or Payload
When setting up Wi-Fi profiles, you can use SCEP (Simple Certificate Enrollment Protocol) as a server or payload for certificate issues. The SCEP Proxy works as a middleman between devices and the SCEP server, giving certificate registration an extra layer of security. On the other hand, the SCEP Payload tells devices directly to talk to the SCEP server so that certificates can be issued.
5. Network Security Settings
In Jamf, network security optimization is vital. Here are some essential things to keep in mind to improve security:
Configure WPA2 Enterprise
Implementing WPA2 Enterprise ensures that Wi-Fi networks have strong security and identification. This advanced security measure keeps people from getting in without permission and keeps private info safe.
Quality of Service
Set up Quality of Service (QoS) choices to prioritize voice and video data. This ensures that contact is easy and video streams smoothly, improving the user experience.
TLS Version
To keep data transfer safe, choose TLS versions with security in mind. Using the most recent TLS versions strengthens security and guards against possible flaws.
RADIUS Server Name
The RADIUS server name can change the connecting process. Choosing a clear and easy-to-remember server name improves network performance and makes device registration easier.
6. Using Certificate Auto-Revocation
Certificate auto-revocation is a useful tool that gives network settings an extra layer of security. The Certificate Authority (CA) controls this feature, which lets digital certificates be automatically revoked when necessary.
When a CA supervisor decides that a certificate should no longer be accepted, they can log into the CA and start the cancellation process. Then, this information is shared by putting out a Certificate Revocation List (CRL) with the serial numbers of the certificates that have been canceled before their expiration date.
Streamlining Auto-Revocation with SecureW2’s JoinNow
SecureW2’s JoinNow includes the certificate auto-revocation capability for major MDMs like Intune and Jamf, making handling revoked certificates simpler and more efficient. Organizations can choose a particular CA or accept the organization’s Certificate Authority as its default option. Additionally, administrators can tick the box for certificate auto-revocation, which comes in handy when revocation of certificates is required often or on a big scale.
Organizations may quickly react to security concerns by deploying certificate auto-revocation using SecureW2’s JoinNow, and risks can be reduced. By limiting access to network resources to only trusted devices with current certificates, this feature improves the overall network security posture. With this innovative feature, businesses can avoid possible security threats and reliably safeguard their network and data.
Organizations can also benefit from the seamless integration of certificate auto-revocation with Jamf by auto-enrolling certificates in Jamf. For Jamf-managed devices, combining certificate auto-enrollment and auto-revocation enables a simple and safe certificate management procedure.
Businesses may proactively reduce security risks and successfully protect their network and data thanks to our JoinNow cutting-edge capabilities. SecureW2 equips businesses with a potent tool to maintain a safe and reliable network environment by making the certificate auto-revocation procedure easier.
Streamline Device Management and Network Security with Cloud RADIUS
Implementing a safe and efficient Jamf RADIUS server setup is critical for effective device management and network security, especially when using macOS and iOS devices. Organizations can develop a strong and secure device management environment by following best practices such as choosing a dependable hosting platform, using secure authentication methods such as EAP-TLS, and carefully defining Wi-Fi profiles using PEAP.
SecureW2 provides cutting-edge network security and device management solutions that enable businesses to fortify their network infrastructure and safeguard critical data. With our role-based access policy and dynamic RADIUS, you can manage user access and ensure that only authorized users and devices can connect to your network. Our solutions simplify Wi-Fi authentication, making it more secure and user-friendly for workers and visitors.
The native integration of our Cloud RADIUS with several MDM solutions, including Jamf, enables seamless device registration and certificate management, resulting in a smooth user experience while ensuring network security. The addition of SecureW2’s auto-revocation policy improves certificate management by guaranteeing that expired or compromised certificates are revoked as soon as possible to avoid any security problems.
Contact us to learn more about our industry-leading products and how you can confidently safeguard your organization’s network.