Students and staff who visit other colleges and universities frequently encounter challenges accessing safe Wi-Fi networks. Without an integrated system, they may encounter connectivity challenges, different login procedures, or concerns about data security on new networks. These barriers can impede cooperation and productivity, especially in academic and research settings. Eduroam enables users to authenticate using credentials from their home university, resulting in a more comfortable and unified network experience, whether traveling or collaborating between universities.
However, the multi-step authentication procedure poses security risks, especially when user credentials are sent over a wireless network. This is where RadSec, a protocol that encrypts RADIUS transmissions with Transport Layer Security (TLS), comes into action. RadSec establishes a secure tunnel to safeguard authentication data in transit, guaranteeing that unauthorized parties do not intercept or tamper with it.
As the need for safe roaming solutions evolves, many question whether RadSec is the answer to making Eduroam more resilient and secure. Let’s examine its role and demand.
What is Eduroam?
Eduroam is a global Wi-Fi roaming service designed exclusively for higher education and research communities. It enables students, teachers, and staff to connect to secure Wi-Fi networks at their home university and any other visited institution worldwide. Users may join the “Eduroam” network from anywhere with a single set of credentials, eliminating the need for extra login information or manual configuration.
The authentication method is simple yet effective. When users connect to Eduroam from a participating university, their authentication request is securely transmitted to their home institution’s RADIUS server for verification. This decentralized strategy guarantees that the user’s credentials are only recognized by their home institution, resulting in a consistent and secure user experience.
Eduroam has become a pillar of cooperation and mobility in academia, providing ease and security to millions of users worldwide. However, transferring sensitive authentication data via networks raises the question of whether additional security procedures, such as RadSec, are required.
Understanding RadSec
RadSec (RADIUS over TLS) is an advanced protocol that encrypts data while in transit to improve the security of RADIUS transmissions. Unlike standard RADIUS, which uses the less secure UDP protocol, RadSec employs TCP and TLS to build a solid and secure communication channel. The protocol uses certificates on both the client and server sides to provide mutual authentication and data integrity during transmission.
How Does RadSec Work?
RadSec uses TLS to create an encrypted tunnel between the RADIUS server and wireless network infrastructure (such as access points or controllers). This tunnel protects significant authentication data, including credentials or access information, against interception or alteration. Certificates act as trust anchors by utilizing Public Key Infrastructure (PKI), enabling secure communication without requiring pre-shared secrets or static setups.
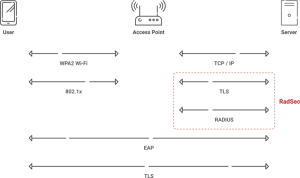
Differences Between RadSec and Traditional RADIUS
Transport Protocol:
- Traditional RADIUS utilizes UDP to deliver data without establishing a dedicated communication channel. While efficient, UDP lacks built-in encryption and is susceptible to packet loss and interception.
- RadSec, on the other hand, employs TCP, which establishes a secure connection and assures that all packets arrive in sequence, increasing security.
Security Layer:
- Traditional RADIUS encrypts just passwords, leaving other aspects of the transmission unencrypted.
- RadSec encrypts every communication using TLS, providing end-to-end security for authentication and accounting data.
Suitable for Roaming:
- UDP-based RADIUS is vulnerable in roaming settings when authentication requests are made across numerous networks. Packet loss or interception in such settings might jeopardize security.
- RadSec, with its encrypted and trustworthy channel, is more suited for roaming situations such as Eduroam, where authentication requests must safely traverse many networks.
Why is RadSec Important in Roaming Contexts?
The risks of data interception or manipulation are increasing in roaming scenarios such as Eduroam, in which users connect to networks other than their home institution. Authentication data, particularly in PEAP-MSCHAPv2 (password-based Wi-Fi) configurations, may travel across many networks before reaching the home institution’s RADIUS server. Attackers might use these handoffs to collect passwords or modify data without appropriate encryption.
RadSec mitigates such risks by encrypting each stage of the authentication procedure. For example, even if a visiting institution’s network is less secure, RadSec’s TLS layer protects authentication data while in transit. Furthermore, RadSec is becoming more significant as roaming solutions like OpenRoaming require its use for secure communication. While not a mandatory Eduroam requirement, RadSec adds an extra degree of security that matches the rising demand for safe and reliable Wi-Fi roaming solutions in academia.
How Eduroam Authentication Works?
Eduroam is a global Wi-Fi roaming solution that streamlines safe internet access for higher education students, teachers, and staff. Users can connect to Eduroam at any partner institution globally using their home institution credentials. Authentication step-by-step:
- Connecting to the Local Eduroam Network
When user devices connect to Eduroam at a host institution, they connect to the local network’s access point. The network recognizes the user as an Eduroam participant but does not validate their credentials.
- Forwarding the Authentication Request
The host institution’s RADIUS server sends the user’s credentials to their home university’s RADIUS server for authentication. A hierarchy of RADIUS servers in the Eduroam federation ensures the request reaches the right place. The home university’s RADIUS server checks the credentials against its identity database (LDAP or Active Directory).
- Authentication Response
The user gains Eduroam network access if the home university’s RADIUS server sends an authentication acceptance message across the chain if their credentials are acceptable. If credentials are invalid, an authentication refusal message is returned.
- Importance of Secure Transmission
Eduroam’s multi-hop authentication mechanism requires safe communication across several servers and networks. When network security requirements differ in roaming settings, each hop creates a risk. Encryption is also required to protect sensitive user credentials during transfers.
- PEAP-MSCHAPv2 vulnerabilities
PEAP-MSCHAPv2-based Eduroam networks are vulnerable during authentication:
- Unencrypted Data at Certain Points: PEAP-MSCHAPv2 encrypts user credentials in the tunnel but not RADIUS communication. Attackers can intercept or alter packets since parts of the data are accessible during transmission.
- Credential Theft: Attackers might utilize false Eduroam networks (e.g., access points) to steal usernames and passwords from devices connecting without server validation.
EAP-TLS and RadSec are recommended for Eduroam administrators to secure and authenticate the RADIUS connection. RadSec encrypts the communication line during authentication and protects passwords and other sensitive data.
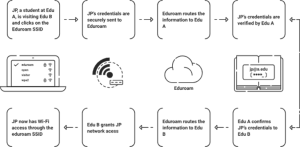
This flowchart shows how Eduroam enables seamless Wi-Fi access across educational institutions. Here’s an explanation:
- Initial Connection: A student (JP) from Edu A goes to Edu B and joins to the Eduroam Wi-Fi network by selecting the Eduroam SSID from their device.
- Credential Transmission: JP’s login information is safely sent to the Eduroam system.
- Routing to Home Institution: Eduroam sends JP’s credentials to their home institution, Edu A, for verification.
- Verification by Home Institution: Edu A checks JP’s credentials to ensure their legitimacy and eligibility.
- Acknowledgment: Edu A returns a confirmation to Eduroam that JP’s credentials are legitimate.
- Forwarding to Host Institution: Eduroam then forwards this confirmation to Edu B (the host institution).
- Granting Access: Edu B offers JP access to its network via the Eduroam service.
- Wi-Fi Access Established: JP is now linked to the Eduroam Wi-Fi at Edu B, allowing for easy and secure internet access.
The Role of RadSec in Enhancing Eduroam Security
RadSec (RADIUS over TLS) helps Eduroam’s security, especially in roaming settings where users connect to new and potentially less secure networks. RadSec encrypts communication to protect sensitive data like authentication credentials.
How RadSec Encrypts the Authentication Process
UDP, used in RADIUS, lacks encryption and can be intercepted or tampered with. RadSec replaces UDP with TCP and encrypts RADIUS communication with TLS for end-to-end security.
When RadSec is implemented:
- Encrypted tunnels carry authentication requests and responses.
- Rogue servers or devices cannot compromise communication since the RADIUS server and client employ mutual trust certificates.
- Despite many network hops in Eduroam’s federation, the encrypted route protects users and passwords.
Addressing Roaming-Related Vulnerabilities
Eduroam roaming generally entails connecting to networks beyond a user’s home institution. RADIUS transmissions may pass through numerous intermediary servers before reaching the user’s institution. Each hop poses a risk. RadSec reduces risks by:
Encrypting data during transmission prevents tampering.
Secure communication between access points, local RADIUS servers, and the home institution’s RADIUS server over public or insecure networks.
RadSec helps PEAP-MSCHAPv2 users. This password-based authentication technique encrypts tunnel credentials but not RADIUS communication. RadSec secures the whole communication chain, preventing credential theft and data modification.
Benefits of RadSec for Organizations Using PEAP-MSCHAPv2
PEAP-MSCHAPv2 is compatible and easy to use; hence, many Eduroam installations employ it. However, this protocol is vulnerable to:
- Man-in-the-middle attacks.
- Exploits via fake Eduroam access points.
Institutions may defend themselves from these risks by encrypting RADIUS communication using RadSec. This is crucial in unmanaged devices, where end users may not validate server certificates.
Is RadSec necessary for Eduroam?
While RadSec is not currently required for Eduroam, it is increasingly seen as a critical upgrade for boosting security in the network’s authentication process. Eduroam’s protocols are safe, but RadSec addresses vulnerabilities common to roaming contexts and emerging cybersecurity issues.
The current status of RadSec in Eduroam
As of now, Eduroam does not compel participants to use RadSec. The majority of universities use existing authentication methods such as PEAP-MSCHAPv2 or EAP-TLS. While these approaches are helpful in many situations, they have room for improvement, particularly in securing RADIUS messages over numerous network hops.
RadSec provides a solution by encrypting these messages, adding an extra layer of protection to reduce possible risks while traveling. Its implementation is crucial for organizations seeking to future-proof their networks against more complex threats.
Alternative Security Protocols: EAP-TLS
For organizations that do not use RadSec, EAP-TLS remains a reliable choice. This certificate-based authentication solution replaces credentials with digital certificates, eliminating the possibility of password theft. However, without RadSec, even certificate-based authentication may expose RADIUS communication to interception or alteration during transmission.
RadSec enhances EAP-TLS by protecting the transport layer and providing end-to-end encryption. RadSec becomes even more critical for institutions employing PEAP-MSCHAPv2 (password-based authentication) to mitigate its known vulnerabilities.
Risks of not using RadSec on roaming networks
Eduroam’s unique structure, which allows users to connect to networks outside of their home institution, presents significant security challenges:
- Interception Risks: RADIUS messages pass through several servers before arriving at their destination. Without RadSec, these signals might be intercepted, revealing sensitive information such as usernames and passwords.
- Rogue Access Points: Attackers can create false Eduroam networks to steal credentials. RadSec mitigates the issue by requiring mutual certificate authentication across RADIUS servers.
- Data Tampering: Without encryption, malicious actors might change or manipulate authentication data in transit, enabling unauthorized access or refusing valid connections.
Institutions can use RadSec to protect themselves against these risks, ensuring a safe and trustworthy authentication procedure even in the most vulnerable roaming settings.
Counterpoint: Practicality vs. Current Security
While RadSec improves Eduroam security, its requirement is dependent on existing infrastructure and threat model:
Cost and Configuration: Implementing RadSec necessitates infrastructure upgrades, certificate management, and administrative control. This might be problematic for universities with limited resources.
Existing Security Measures: Many institutions already employ EAP-TLS with strong server certificate checking, which offers enough security. In such circumstances, the slight security improvement from RadSec may not be worth the effort necessary to execute.
User Behaviour: The efficacy of any security measure depends on adequate device onboarding. Universities that use unmanaged devices must ensure that their users configure them appropriately. Platforms like SecureW2’s JoinNow make onboarding and certificate distribution easier, which is critical regardless of whether RadSec is used.
Balancing Risk with Practicality
Finally, RadSec’s necessity is determined by an institution’s security goals and threat environment. While not required, RadSec offers substantial advantages for safeguarding Eduroam’s authentication procedure, particularly in roaming settings. RadSec is a logical and forward-thinking solution for institutions looking to improve their network security posture and stay updated with emerging trends.
By implementing RadSec, Eduroam participants may address current vulnerabilities, prepare for potential threats, and ensure the trust and security of their user’s data in an interconnected, roaming world.
Benefits of Using RadSec with Eduroam
Implementing RadSec with Eduroam delivers significant security benefits to organizations, offering comprehensive protection for authentication data in transit.
- Improved Encryption: RadSec encrypts RADIUS packets using TLS, protecting sensitive data, including usernames and authentication answers. This encryption ensures that data is safe even in less secure or public networks typically encountered when roaming.
- Improved Security for Password-Based Protocols: Many institutions still use PEAP-MSCHAPv2, a password-based authentication system subject to interception attacks and credential theft. By incorporating RadSec, institutions may safeguard these messages from interception during multi-hop authentication operations.
- Compatibility and Ease of Deployment: Modern RADIUS systems, such as SecureW2’s CloudRADIUS, have RadSec functionality by default, making installation simple. These cloud-based technologies enable institutions to implement RadSec without requiring significant hardware upgrades or onerous configuration processes.
Incorporating RadSec supports Eduroam’s aim of offering secure, seamless connections to people globally. While not required, RadSec significantly improves Eduroam’s security posture by guaranteeing that authentication requests are kept secret and tamper-proof across linked networks. As security threats grow, organizations prioritizing RadSec demonstrate their commitment to safeguarding user data.
Moving from PEAP to EAP-TLS
Transitioning from PEAP-MSCHAPv2 to EAP-TLS is a significant step towards improving Eduroam security. EAP-TLS uses certificates instead of passwords for authentication, which addresses the weaknesses of password-based systems.
- Superior Security: PEAP-MSCHAPv2 is based on passwords, which can be intercepted or abused in man-in-the-middle attacks. In contrast, EAP-TLS employs public key infrastructure (PKI) to securely authenticate devices, guaranteeing that only authorized users may access the network.
- Improved User Experience: With EAP-TLS, end users no longer need to remember complicated passwords or be concerned about compromised credentials. Certificates are device-specific and instantly authenticate users, lowering login friction and increasing overall ease.
- Simplified Transition with PKI Solutions: SecureW2’s PKI platform and JoinNow MultiOS onboarding make the transition to EAP-TLS easier. These technologies automate certificate provisioning, guaranteeing that managed and unmanaged devices get digital certificates within minutes. This automation saves administrative expenses and user error for universities managing different device ecosystems. By minimizing manual intervention, JoinNow MultiOS reduces administrative effort and eliminates user error, both of which are crucial for colleges managing varied device ecosystems.
By integrating JoinNow MultiOS into Eduroam’s authentication process, institutions may install EAP-TLS with ease, assuring outstanding security and an excellent user experience. When paired with RadSec, this method prepares Eduroam for a password-free future, protecting users and data in an evolving threat scenario.
Future-Proofing Eduroam with RadSec
RadSec is not mandatory for Eduroam, although it offers considerable security benefits, especially in safeguarding authentication data during multi-hop transfers. By encrypting RADIUS packets with TLS, RadSec overcomes weaknesses in password-based protocols such as PEAP-MSCHAPv2 and improves roaming security.
RadSec is a proactive step towards future-proofing university networks, ensuring users have safe and smooth Wi-Fi access. SecureW2’s CloudRADIUS and PKI offerings make RadSec implementation simple and cost-effective. These technologies simplify implementation, allowing institutions to improve Eduroam security without complexity.
Contact us now and implement RadSec to protect your campus connectivity.
